While scrunchies might not be that common a hair accessory anymore, you can make one of your own by following the steps in this how-to video. You will need two satin fabric pieces of 50cm, a sewing machine, sewing thread, a pair of scissors, marking pins, as well as brown and black satin fabrics. It's so easy to make, even a cat can do it. Check out this video sewing tutorial and learn how to make a frilly hair scrunchie.

In this five-part video tutorial series, you'll learn the fundamentals of working with electronics. To follow along, you'll need a 28-280 Electronics kit from RadioShack.
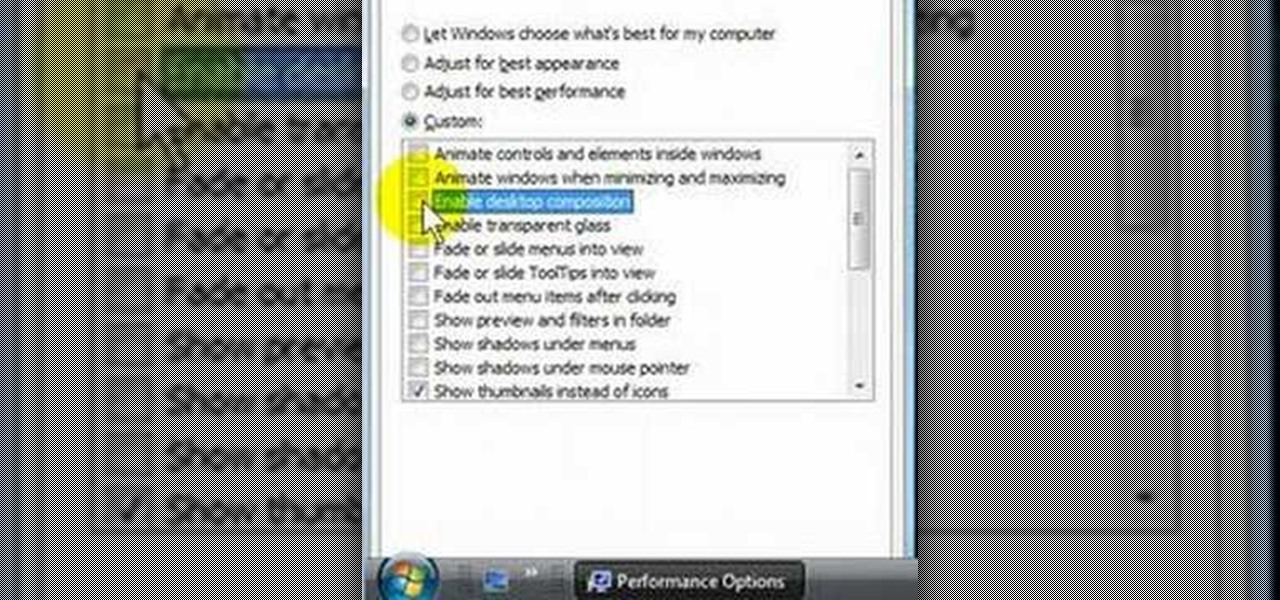
Are you disappointed with the sluggishness of Microsoft Windows Vista? In this Windows video tutorial, you'll learn how to use the Performance tool in Windows Vista to disable senseless features you don't need and to make Vista run more quickly in the process. For more, or to get started speeding up your own Windows Vista machine, take a look!
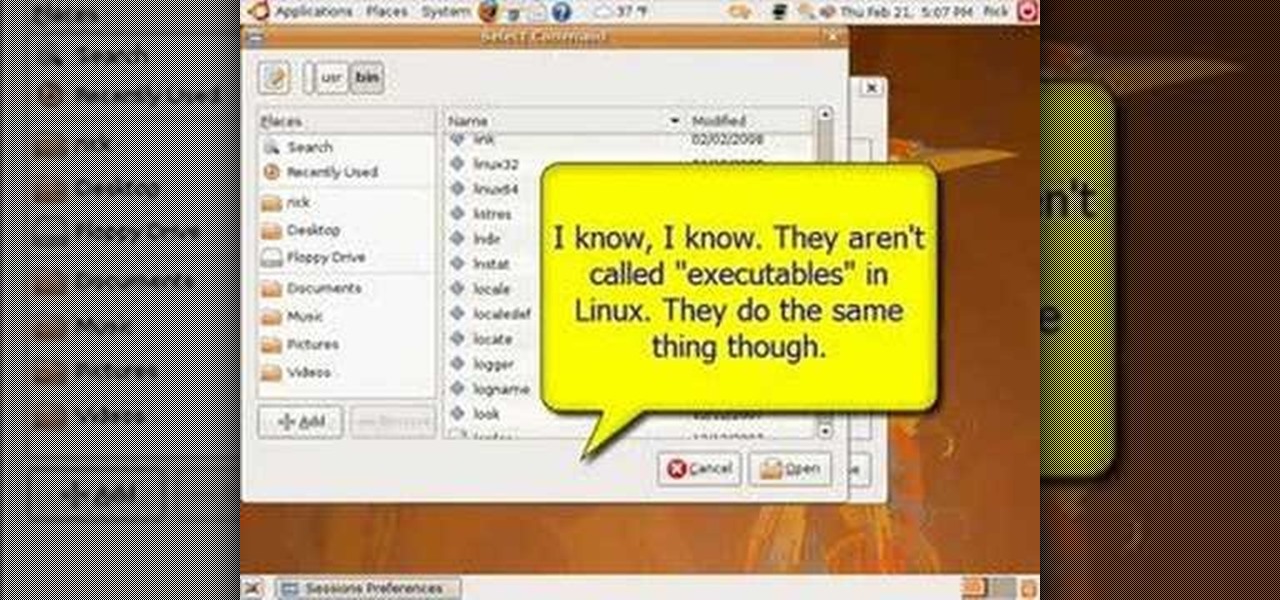
New to the Ubuntu Linux distribution (or one of its derivatives) and looking for a way to start programs automatically when you boot up your machine? Take heart: This video tutorial will show you how to accomplish just that using your system preferences. Take a look!

Create a card with an embossing machine and chalk. Any embossed image can be colored in easily with a little big of chalk for a soft effect. Watch this video card-making tutorial and learn how to use embossed paper and chalk to make a card.

Racquetball is not only a fun sport but also a great workout. Learn some important beginning fundamentals of racquetball in this free video clip series.

Watch this video tutorial to learn how to bypass the cumbersome process of making squaring backings for your quilts. This is an attempt to show you how and why you may never want to make a perfect square backing for your longarm sewing machine again.

Learn how to use the couching technique to create depth and dimension to your quilts. Add borders and trim to intricate quilted patterns. You'll need a large eye needle and various couching material, such as yarn, ribbon and scraps of fabric. Couching adds texture and finish to quilted fabrics.

This video card making tutorial shows how to make a name placard, great for social functions. Also demonstrated are how to use a Cuttlebug embossing machine and how to replicate the stamp kissing technique. Watch this instructional video and learn how to make a name card placard.

Often we neglect simple tools because the big fancy machine tools are so attractive. But often these basic tools are the best for the jobs. This how to video is a quick review of some basic hand tool techniques with Kaleo Kala.

This how to video sewing tutorial demonstrates how to sew a whip stitch by hand, just in case you don't have a sewing machine. The straight stitch is excellent for simple hems, decorative stitching and gathering fabric.

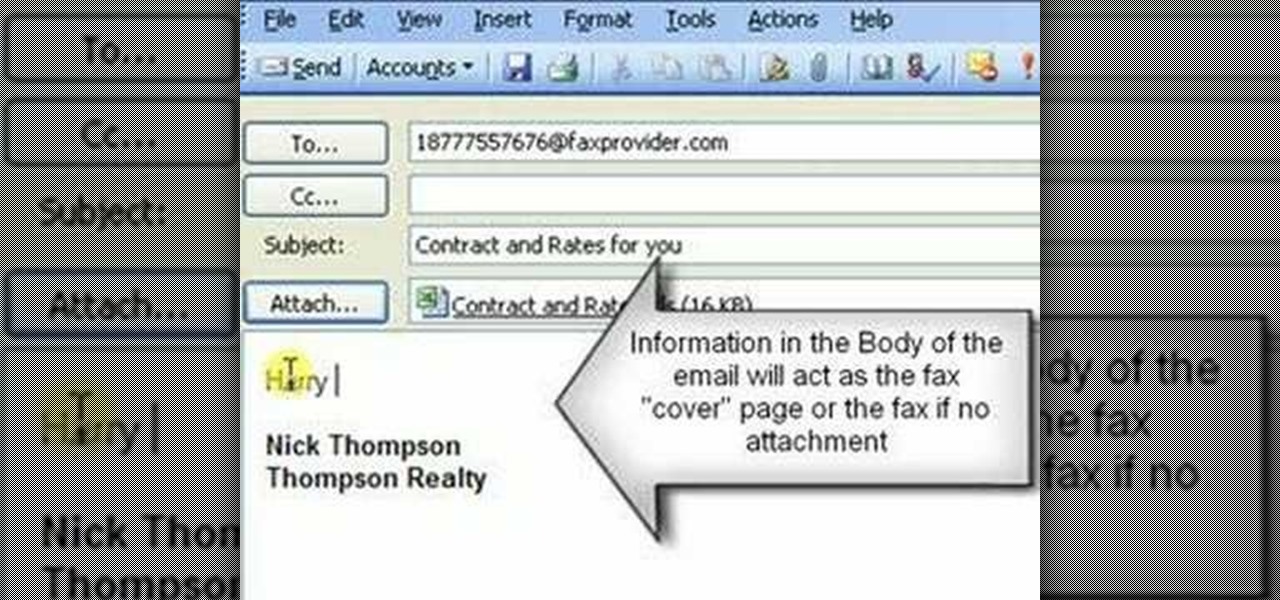
Check out this video tutorial on how to send a fax with email using Internet Fax. You'll need an Internet fax provider, and a phone number, so don't think it's easy as one, two, three.

This weekend, take some time to escape from the business and stress of your daily grind. Make a hammock and lay around in it. Fit for a city and you can make it even without much knowledge of sewing machines.

Learn how to do Gravitron speed wide grip pull ups. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do Gravitron wide grip drop set pull ups. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do wide grip pull ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do speed tricep dips on a Gravitron. Presented by Real Jock Gay Fitness Health & Life. enefits

Learn how to do power press single leg presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do cable bar pull down triceps. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do single arm rope press downs. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do a single cable scissor squat and row. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do single cable squats and rows. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do speed single cable reverse flys. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do tube rows. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do alternating T push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Make an Eddie Earthworm doll. Yes, you will need cloth and pins. A sewing machine is helpful. Part 1 of 3 - How to Make an Eddie Earthworm doll.

Watch this video from the Concrete Network for tips on using the Mongoose concrete cutting machine to cut intricate designs in concrete surfaces before coloring.

Ever wish you could bring your tabs with you from computer to computer? Now you can! Watch Tekzilla to find out all the details.

This video shows you how to adjust headlights. Unfortunately it uses a precision machine so you won't be able to do this at home.

The Patch Kit by Designs in Machine Embroidery makes it easy and profitable to embroider patches. Watch how simple it is to use this time and money saving product.

The Magna-Hoop Pro, the latest innovation from Designs in Machine Embroidery makes it easy to embroider an afghan.

This week on Threadheads, the ladies of Compai are helpin' us out with a very special viewer request, plus we hang out and take a look into their popular DIY book series 99 ways. So sit back, relax, grab your sewing machine and get comfy.

Django is a Python web framework used for rapid application development in any environment. In under 10 minutes, you can go from a bare Linux (Ubuntu) installation to a fully functional Django server.

This is a simple recipe that just uses regular AP flour. You can, of course, use a mixture of semolina flour like many pasta recipes suggest. But, this recipe is very user friendly, and if you’ve never made your own pasta before, this would be a good place to start. By the way, those pasta machines are surprisingly affordable at your local mega-store

This video demonstrates how to work your hamstrings by doing leg curls. The video walks you through setting up the seated leg curler machine and performing the exercises correctly.

This video demonstrates how to use a leg press to work out your quads and glutes. The video walks you through setting up the machine to your body type and performing the exercises correctly to avoid injuries.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

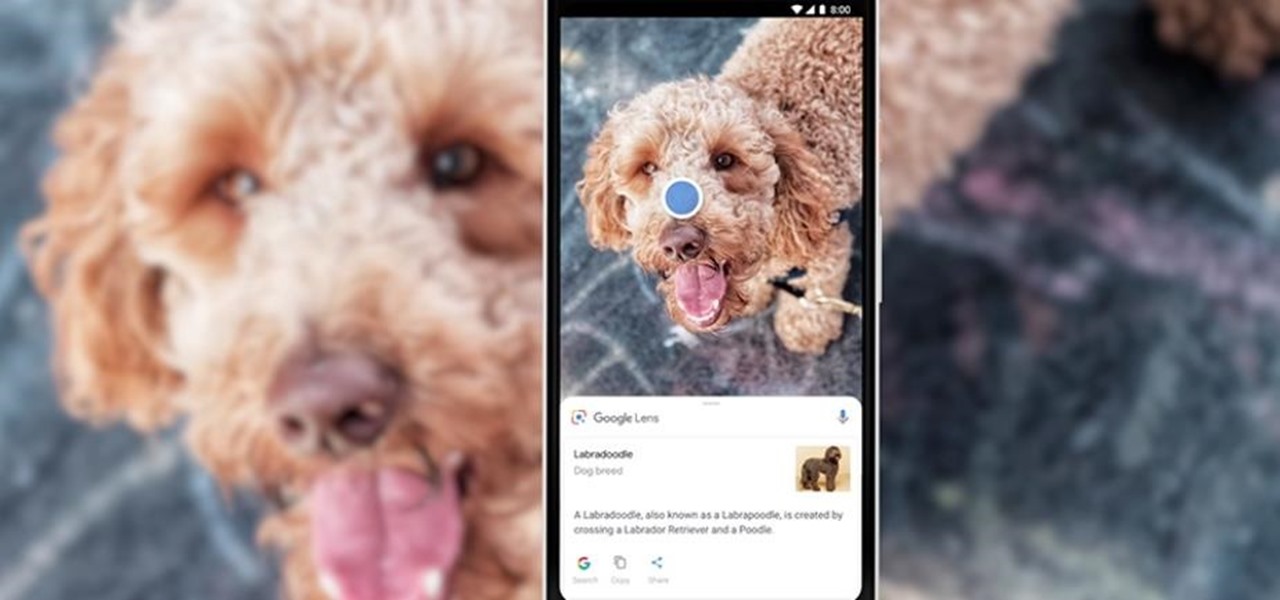
During Tuesday's keynote at the I/O developer conference, Google unveiled new capabilities for its Lens visual search engine and expanded the availability of the platform in smartphone camera apps.