
How To: 50-50 grind with a skateboard
Learn how to 50-50 grind with a skateboard. After you've mastered some skateboarding fundamentals, try moving on to the 50-50 grind.


Learn how to 50-50 grind with a skateboard. After you've mastered some skateboarding fundamentals, try moving on to the 50-50 grind.

Golf and baseball have a lot of similarities to one another. The swing, stance and basic fundamentals of both sports can help golfers produce a more effective golf game. Learn some tips about using baseball to improve your golf game from our golfing expert in this free video series.

Learn how to model the infamous drive-by shooter, the Mac 10, in MAXON Cinema 4D. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, including complete instructions, watch this 3D modeler's guide.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Kicking in rugby is a fundamental skill most players will master. Learn how to play rugby, including rules and skills, in this video rugby lesson.

This is an instructional video on how to thread a circular knitting machine. For the demonstration, the circular knitting machine by Innovations serves as our example. Tips are provided based on the experience of a seasoned machine knitter accustomed to using this machine.

This instructional video provides basic tips on proper baseball hitting fundamentals. Specifically, in this tutorial you'll learn how to hit line drives to the pull side by using the tee. Whether you are a parent who is excited about getting your youngster or youngsters started out in t-ball, a teenager trying to improve your skills or even a college or professional player, these hitting basics hold true regardless of what skill level you are at.

This instructional video provides basic tips on proper baseball hitting fundamentals. Whether you are a parent who is excited about getting your youngster or youngsters started out in t-ball, a teenager trying to improve your skills or even a college or professional player, these hitting basics hold true regardless of what skill level you are at.

Creating drum beats is a crucial part of making a great song. Learn how to use Logic Pro 8 Ultrabeat drum machine feature to create and mix your recordings in this free music production tool tutorial from a professional audio engineer.

Check out this video to learn the fundamentals of woodsball, a mission or scenario oriented type of paint ball. Positions are meticulously explained to help in deciding which player type best suits an individual.

Tennis footwork drill for adults and kids using a fundamental plyometric exercise designed to develop explosive lateral movement on the court.

This informative video from howtodj.com is a basic lesson that teaches the fundamental technique of how to match beats, and pitches while DJing. Speed up or slow down the record with your finger and move the pitch control to adjust the pitch. You can also set your thumb on the platter to slow down the album. Good luck!

This video is a demonstration of the most fundamental DJ technique, beat matching, by DJ Magic Wong. A demonstration of how to count and identify a phrase, how to match beats and crossfade.

Data analytics is crucial to the operations of any modern business these days. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics.

This year, over 2.7 billion gamers will spend nearly $160 billion dollars. That number is predicted to increase to over $200 billion in just three years. If ever an industry had growth potential, this is it.
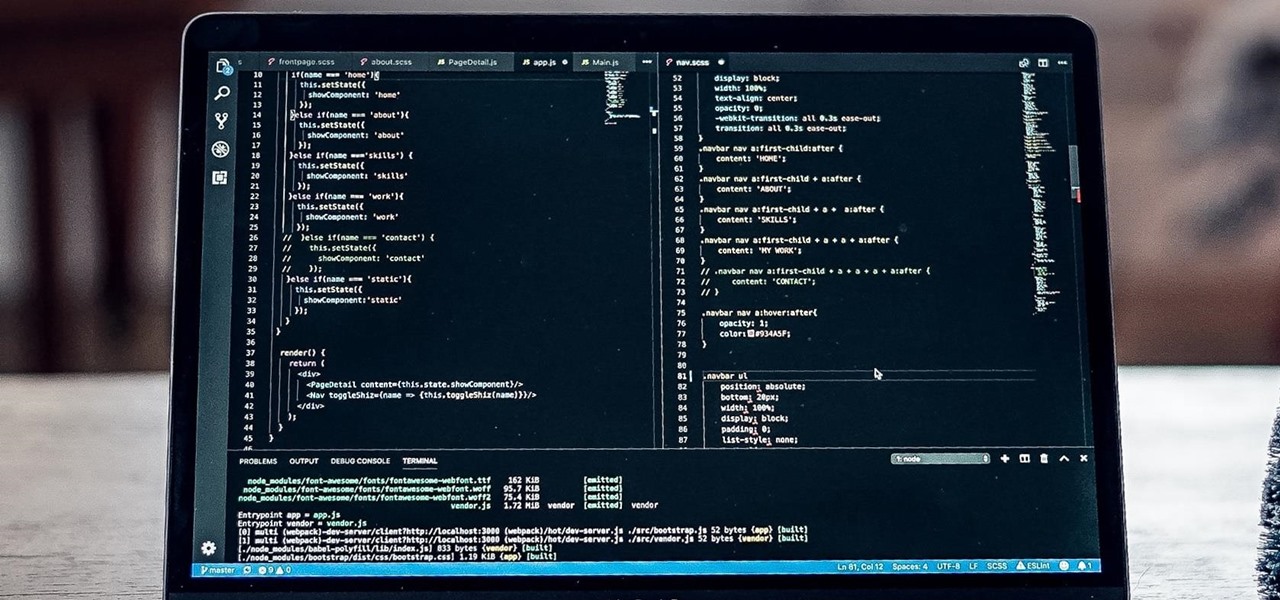
If you're a frequent Null Byte reader, chances are you're already up to speed with at least one or two programming languages or development platforms. But in a world that's becoming increasingly reliant on high-powered apps and responsive websites, knowing the fundamentals of just a few go-to programming languages isn't going to cut it if you want to be competitive and successful.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

While we've seen Snapchat apply sky segmentation to AR content, the makers of the Blue Sky Paint app have applied similar capabilities to create and share airborne art.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.
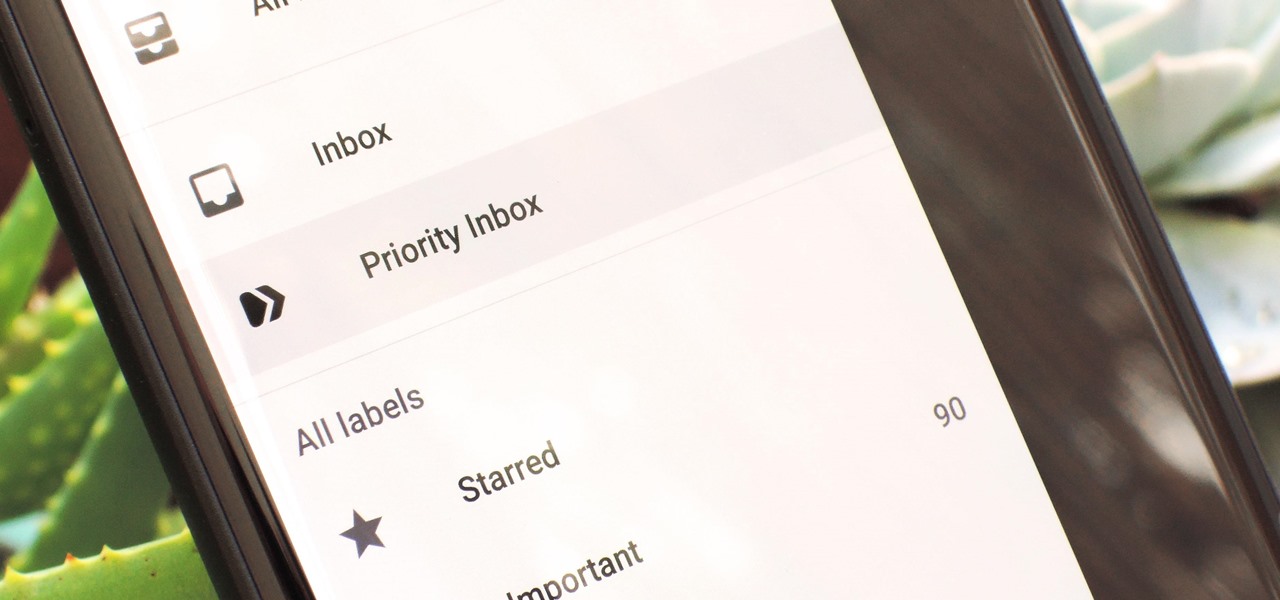
For many of us, getting to inbox zero is the highlight of our day. But if you used your email address to sign up for various sites and services, your inbox is probably cluttered with all sorts of spam, news letters, and unimportant emails. Thankfully, Gmail has a feature that can solve this by using machine learning.

To the best of my recollection, Fruit Ninja was one of the first touchscreen games that appeared to really take advantage of the new paradigm of user input, turning the player's finger into a produce-slicing katana.

A development duo has concocted an iPhone app that displays related tweets based on objects recognized by the device's camera.

Augmented reality headsets with larger eye boxes than any device currently available could make their way to market by the end of next year if current timelines hold true.

Directive Games received the enviable honor of unveiling their ARKit game, The Machines, on stage as part of Apple's iPhone launch presentation.

Ride-sharing firm Lyft says it will continue to rely on drivers in the near and long term even as it replaces them with driverless cars, Taggart Matthiesen, Lyft's director of product, said during a Podcast with Recode.

Tesla has confirmed the EV carmaker has begun to upload videos from models equipped with its latest flavor of Autopilot, as Tesla seeks to "fleet source" data to help improve its cars' machine learning capabilities.

Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.
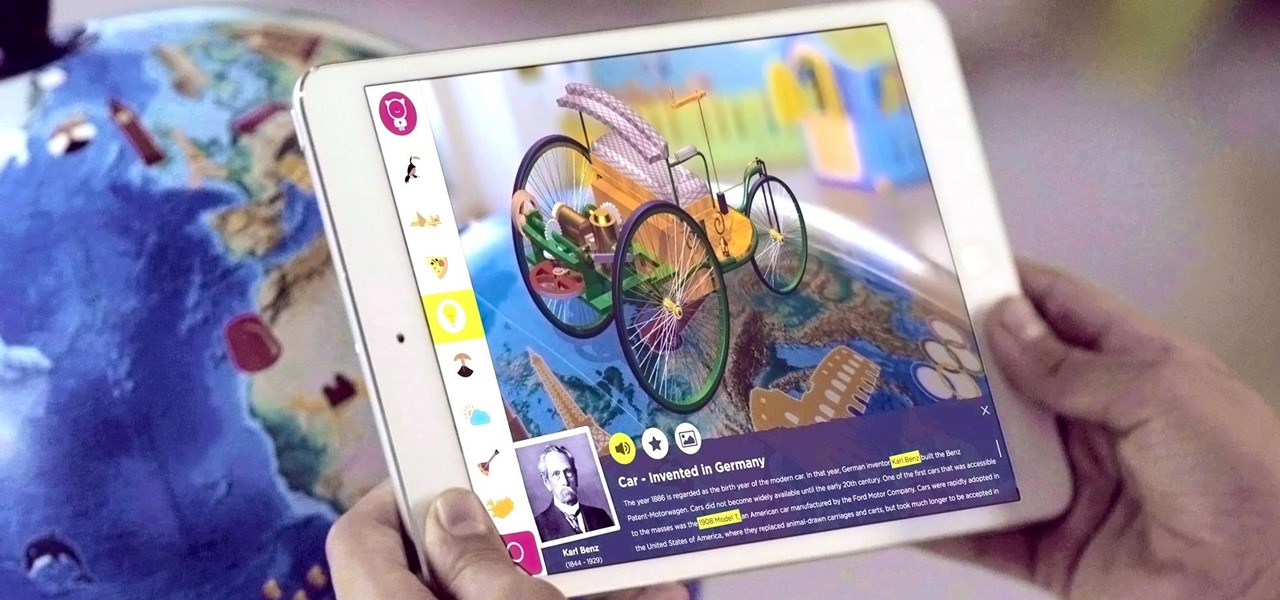
Globes used to be standard in households, usurped in many ways by modern mobile and desktop applications. But one company believes they can upgrade the globe for the 21st century.

Every Friday, Next Reality reviews the latest headlines from the financial side of augmented and mixed reality. This Market Reality column covers funding announcements, mergers and acquisitions, market analysis, and the like. This week's column is led by two companies cashing in on visual inputs.

The Snapdragon 820 and 821 were met with praise last year, receiving almost no complaints compared to their overheating predecessor, the Snapdragon 810. But now, all eyes are on Qualcomm to see what goodies they have in store for us this year, as their new SoC, the Snapdragon 835, will be revealed this week at CES 2017.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

As an avid coffee drinker, I used to be a big fan of single-serve coffee machines. One day, the machine decided to stop working—which does happen from time to time—so I decided to go old school and use my automatic drip. Then, I realized that all I had were pods of single-serve coffee grinds, and I was all out of regular coffee filters!

Like a strong-tasting cup of joe, but want more caffeine out of it? Start double brewing your coffee. To paraphrase a big fan of the double brew process on Reddit, it'll make you feel like you can throw an orange at 60 percent the speed of light. It's that strong. Really.

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.