The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

The iPhone X is Apple at its most classic — they take away a key feature that seems odd at first, but usually, the change pans out in the end. So is the case for the long-lived Home button, whose last appearance may be on the iPhone 8 and 8 Plus. That begs the question — how do you use an iPhone without a Home button?

The iPhone X is almost within reach. In fact, you can preorder right now. We know you've been itching to get your hands on Apple's newest iPhone, but before you give up over $1,000 of your hard-earned money, make sure your iPhone X knowledge is up-to-snuff.

At the Augmented World Expo Europe press conference in Munich today, RE'FLEKT will unveil the addition of remote video calling to their RE'FLEKT One enterprise augmented reality platform, in addition to ARKit and ARCore apps that demonstrate the platform's capabilities.

Today, anyone with a compatible PC can download the Windows 10 Fall Creators Update and experience Windows Mixed Reality.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

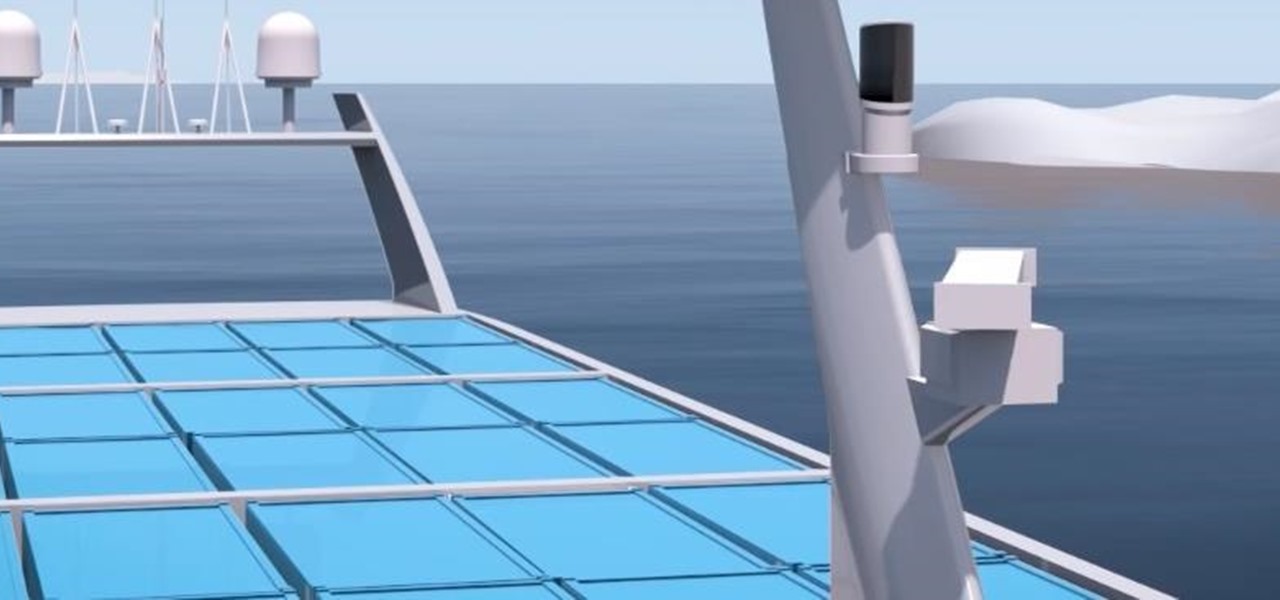
A Norwegian carrier's launch of a pilotless container ship next year could lead the way to a new era in sea transportation and shipping if successful.

Research group OpenAI, a research institute co-founded by Tesla CEO Elon Musk, says it is possible to trick driverless cars' neural networks into mistaking images for something else.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

If you don't know Clay, you're probably going to want to. According to their website, Clay VR's goal was to not only expose users to the world of AR/VR, but fully immerse them in it. Clay does this by allowing users to feel like they were touching the objects in virtual worlds in order to make the virtual worlds feel more natural and real.

The National Transportation Safety Board (NTSB) said it is still investigating the circumstances of a fatal Tesla crash last year to determine if the car or Tesla's Autopilot driverless system was at fault, but revealed more details about the circumstances of the crash.

Former Google employee Tristan Harris claims there's an easy way to combat phone addiction without installing any new software. By enabling grayscale on your phone, checking your apps and notifications will be less appealing and thus stop you from obsessively checking your phone.

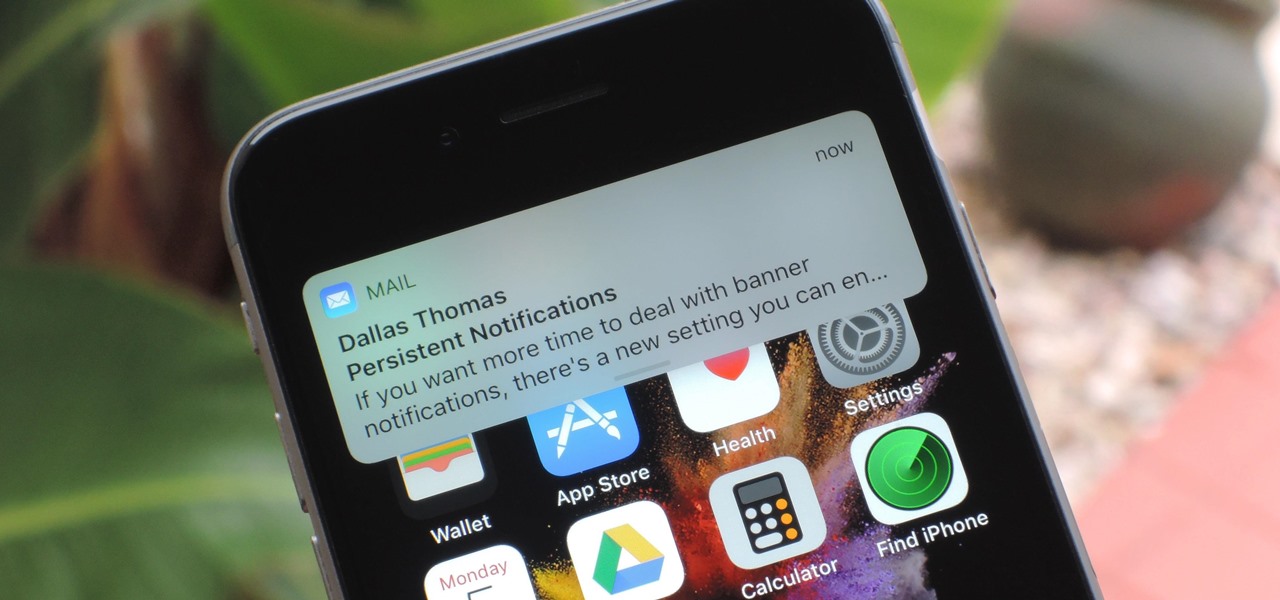
You're working on your iPhone or playing an awesome game when you receive a notification. You take too long to look up from your activity, so before you get a chance to see what's up, the notification is gone. Persistent notifications won't disappear on you like the default disappearing ones in iOS 11 and iOS 12, giving you as long as you need to check them. Here's how to set them up.

Google, the company that rules the internet, is now testing a method to leverage its machine learning with its ubiquitous presence on mobile devices. The new model they're employing is called Federated Learning, and it hopes to apply artificial intelligence to Google's services on Android without compromising user privacy.

360world, a Hungary-based tech company involved in motion control and augmented reality, released information today about their latest products, the CLAIRITY HoloTower and CLAIRITY SmartBinocular. These tools are designed to bring augmented reality into the hands of air traffic controllers, via Windows Mixed Reality, to greatly improve their workflow over tools already in use.

User interfaces for computers have evolved over the years, from the introduction of the keyboard and mouse on the personal computer, to touchscreens on mobile devices, to natural voice recognition. However, the same cannot be said for robots or drones—until now.

In an early morning blog post, Microsoft announced the expansion of the Microsoft HoloLens Agency Readiness Partner Program. This announcement comes on the tail of an expanded HoloLens release over the last few months to many countries outside the initial US and Canada.

Mirror, mirror on the wall, who's the smartest of them all? Since Max Braun's Medium post went viral back in January of 2016, smart mirrors have been appearing on tech blogs in all shapes and sizes. Some are technically sound, some incredibly easy, but all are visually compelling. However, we've never seen one with a fully functional operating system and gesture support—until now.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

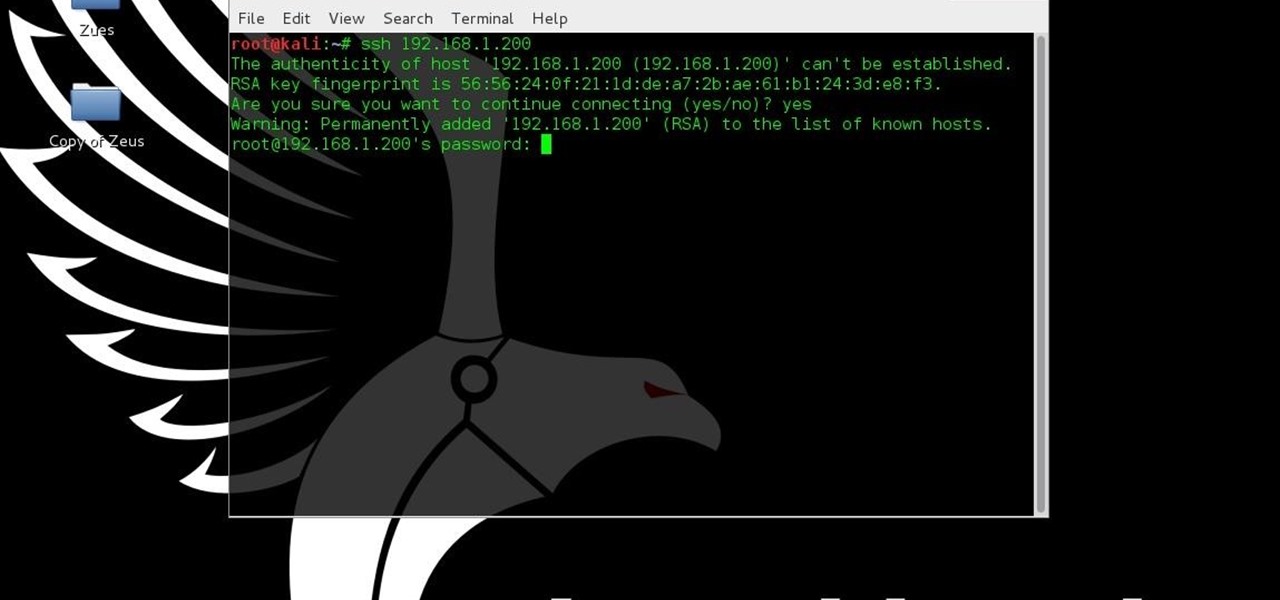
With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

When it comes time to buy a new smartphone, the sheer amount of options on the market can make you feel overwhelmed. There are Android devices of all shapes and sizes with different functionalities and price points, and now, even Apple has three unique iPhone models to fit various budgets.

I was on our new #nullbyte IRC channel when someone told me how tedious it is to install an OSX Virtual Machine on Virtual Box (I think it was wawa). We all know Linux rocks (gets acknowledgement from the crowd), but there are morons out there, multiplying at a never before seen rate, who use OSX. We at nullbyte should be prepared for anything and everything. So, in this guide I take you step by step to creating your OSX Yogemite VM.

On Wednesday, Microsoft launched a chatbot on social media that learns from conversation, and trolls quickly taught it how to be a shameless, Nazi-loving bigot. Oh Internet, an opportunity for a Hitler joke never slips past you, does it? This Is Why We Can't Have Nice Things

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

As you're probably well aware by now, the Apple Watch isn't just for sending text messages and checking Instagram—you can also use it as your wallet. With Apple Pay compatibility, you can use your Watch to make purchases at any retailer that accepts the payment service.

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

If you're like most people, you've stretched before a workout or playing sports. Doing so should help you get your muscles ready to work. While stretching is good for your muscles, you're wasting your time if it's the first thing you do. I talked to Dr. Brian Parr, professor at the Dept. of Exercise and Sports Science at the University of South Carolina Aiken, who explained this misconception and what you can do about it:

Unless your work clothes require dry cleaning, you probably only go to the cleaner a few times a year. And for those few items in your closet for which you do, you have to then find the time and extra budget to make a trip all the way to the cleaners and back again. In the end, it can be quite the hassle.

Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time they want—without triggering the "camera on" light. Yeah, that means those Justin Bieber lip sync videos you recorded weren't just for your private collection.

There are a ton of cool things you can do with your iPhone's camera in iOS 7, from taking burst photos to bouncing the camera open and taking nice parallax-friendly wallpapers. However, nothing tops the camera's super secret hidden feature—turning you into a spy photographer.

Texting is a godsend to mobile devices, but it also has its caveats. Sending a text to someone requires visual, manual, and cognitive attention—looking at what you're typing, holding the phone steady, and thinking about what you're trying to say. So, texting while doing pretty much anything else is not a wise move.

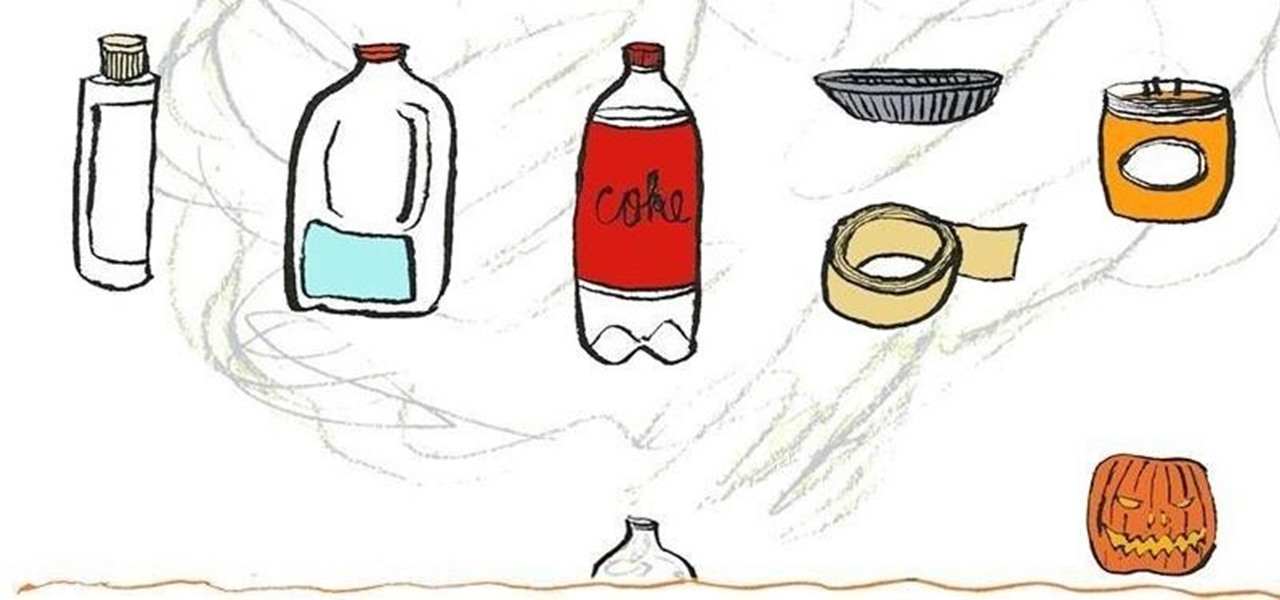
Need to add some spooky ambient fog to your super-scary Halloween party? Rather than shelling out money for a fog machine you'll probably only use once a year, make a trip to the nearest drug store and pick up a bottle of glycerin, a gallon of distilled water, a 2-liter bottle of cola, a disposable mini-pie tin, and a big candle in a jar.

Sometimes you just want to grill. It doesn't matter where you are, what you have, or whom you're with—you just want a delicious burger and you don't care what it takes.

Watch this instructional knitting video to bond a vinyl hem with a knitting machine. Hang an elastic or ravel cord and push it against the bed. Fold the hem over the ravel cord. If you knit with a knitting machine, this is an essential trick for getting started with larger projects.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to decrease the size of your knit piece. Use a single prong tool to unhook and tie off a single stitch on either side of the piece before completing each row to gradually decrease the width of the knit work. You may want to reference written instructions in addition to watching this knitting video.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to weave a cast on. This is a cast on that many people find difficulty with. You may want to reference written instructions in addition to watching this knitting video.

This is the final step of learning how to sew on a vintage Kenmore sewing machine. Watch this how to video to learn how to sew a straight stitch on a this type of sewing machine. Run the motor as you press the reverse button, this locks up the thread.

Using a sewing machine entails knowing how to fill a bobbin with thread properly. This sewing how to video will show you how to fill a bobbin on a vintage Kenmore sewing machine. Happy sewing!