This flower arrangement tutorial shows you how to make a candle centerpiece using a pick machine. A pick machine attaches steel picks to the stems of your silk flowers. This makes arranging your flowers in floral foam much easier. Watch this how to video and you will be making this beautiful candle flower arrangement in no time.
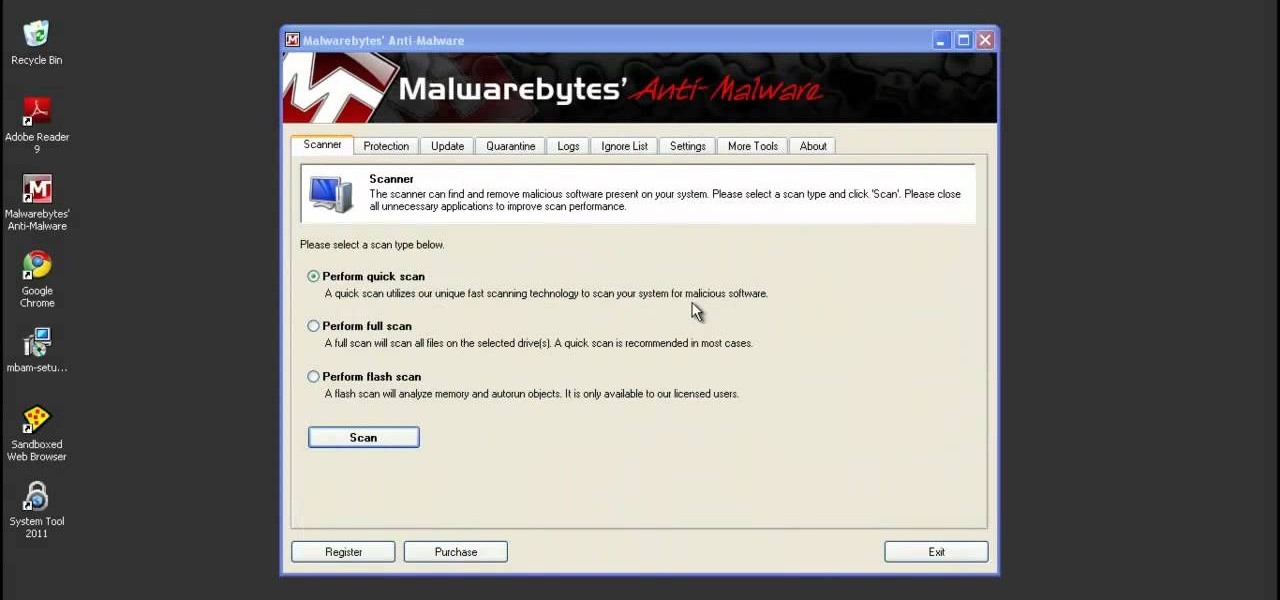
System Tool and System Tool 2011 are the most widespread fake-antivirus rogues on the internet today, infecting countless machines. This video will teach you how to uninstall both warez completely, returning your computer to blessed normalcy.

Circle or infinity scarves became really popular this year, and this little how-to shows you how to knit one up yourself. Knit 1, perl two. You can do it! Follow the steps and fight that cold neck feeling!
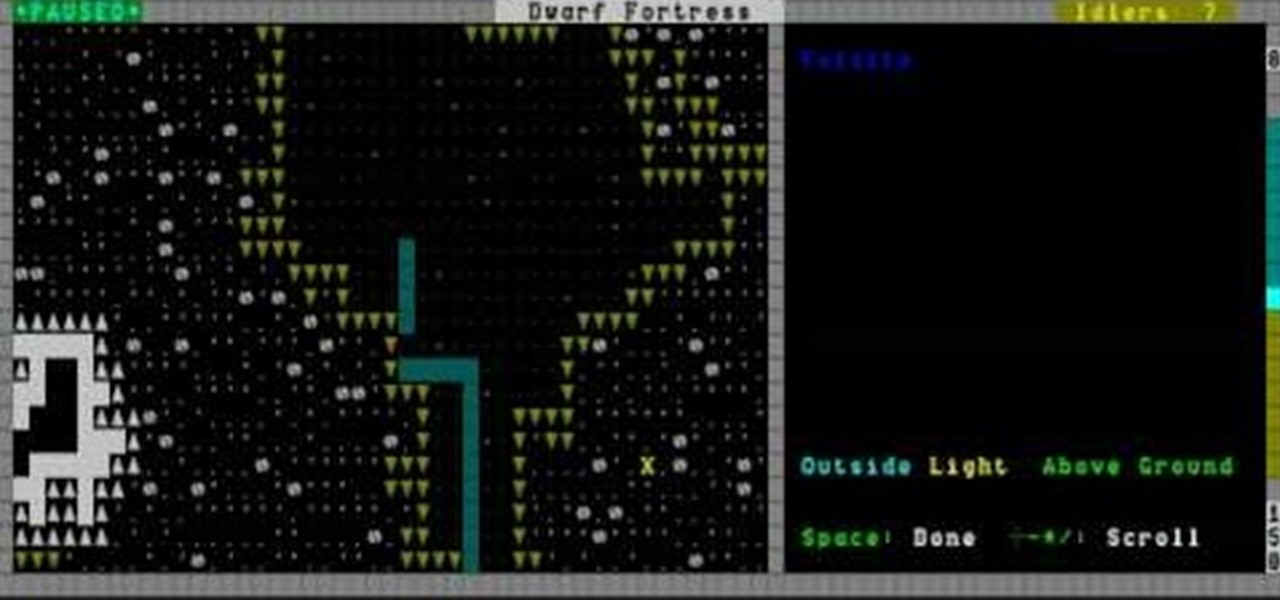
Late in the Dwarf Fortress game building machinery can allow you to pump water around the map and power mill stones to make more advanced food. This video will show you how to build and use machines safely, without destroying your fortress and the lives of your dwarves.
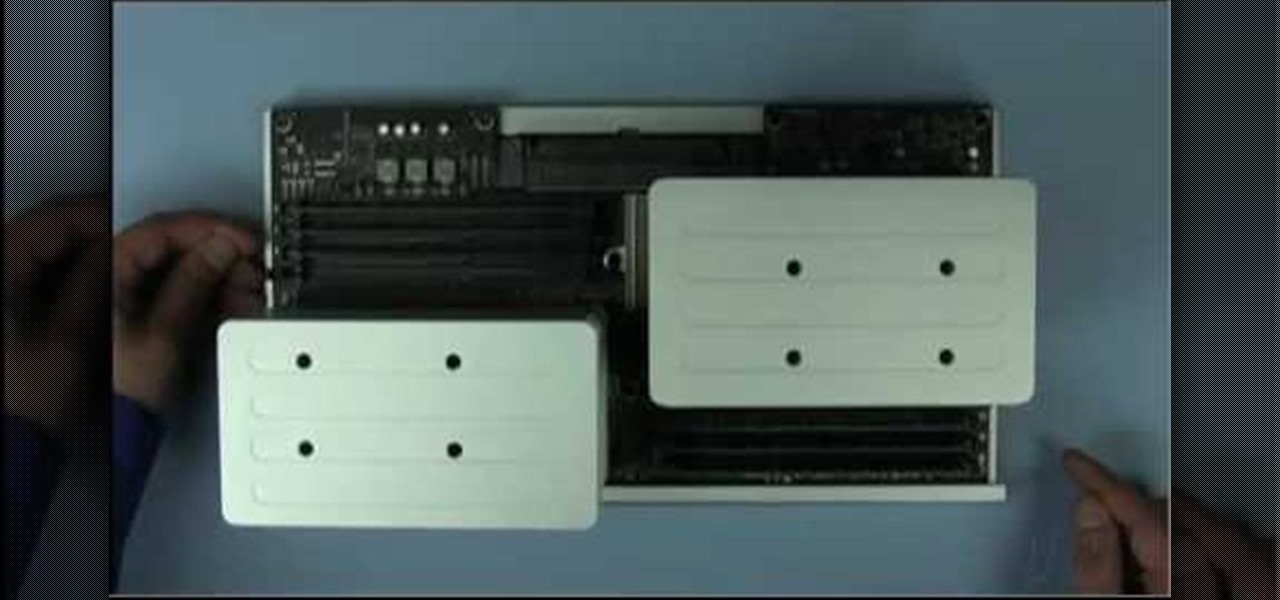
MacOSG demonstrates how to install memory in a 2009 Mac Pro. When performing this upgrade, be sure to take precautions for static by discharging static electricity before beginning. Shut down, unplug and place the Mac Pro on a static-free surface. To access the memory, you need to open the side access door by lifting the latch located on the rear of the Mac until it locks in the open position. You can then the door forward and then remove from the body. The memory is attached to the processor...

What's better than one prank? Five pranks! This video from the notorious Kipkay provides five fantastic, funny, and facile pranks to pull off on your friends and family… maybe even your enemies.

In this video Sarah Magid shows how to make dark chocolate cupcakes with espresso butter cream along with sugar flowers as follows:

The new Pyro FX in Houdini 10 are very impressive with improved workflow. The Pyro FX are great for creating 3D fire and smoke effects. And in this video tutorial series, you will learn the Pyro FX workflow in-depth and the parameters used to create fire and smoke effects. You will also see how volumetric data is created and recorded, and how to visualize it.

Release your inner wild thing with a costume based on the classic children's book. You Will Need

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build a firewall from a junk PC to protect networks.

Watch this video tutorial from the Polish Guy to see how to polish a stainless steel roller using Autosol. In this polishing tip we polish a stainless steel roller using Autosol Metal Polish. The tutorial includes detailed work instructions and best practices.

Do you want to know some quick tricks for improving tech processes at your company? How about equipping yourself with skills that will land you a new job or promotion this year? Becoming a cloud computing expert will make it happen, and right now, The 2021 Cloud Computing Architect Certification Bundle is on sale for just $29.99. That's an amazing 98% off the regular price of $1,800.

Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Watch this instructional knitting video to hang a knitted hem. Add weights the inside of a hem to keep your knitted piece straight. If you knit with a knitting machine, this is an essential trick for getting started with larger projects.

Use the Martelli Stitch in the Ditch Binding Foot for top stitching and with a double needle to get a professional finish to your quilting and sewing projects. Watch this video sewing tutorial and learn how to top stitch with a double need on a sewing machine.

This Mig Welding Video Demo shows how simple and easy it is to use a MIG welding machine. Mig Welding Machines are use throughout the world. They are the suited for many welding applications. This video demonstration demonstrates Mig welding by welding two pieces of sheet metal together. Watch this video welding tutorial and learn how to fuse two pieces of sheet metal together with a Mig welder.

Watch this video from the Concrete Network to learn how use a buffing machine and its accessories.

This tutorial for Sony Vegas teaches you the complete fundamentals for building a simple and short, yet catchy intro. Also explains what metronome is and what it does. This tutorial is for more advanced Vegas users.

This video demonstrates how to hook up a washing machine. This can save the high price of hiring a handyman.

No pain no gain, ladies and gents. If you want a fabulous body, trying to take the easy way out by trying those hokey "As Seen On TV" exercise machines or just by starving yourself is going to get you nowhere fast. Neither serve to encourage long term weight loss results, and while you may lose weight, most of that weight is going to be loss of muscle mass because you're not exercising.

It's amazing what you can create with a few, everyday household and office supplies. Most of these items are already sitting in your junk drawers, so there's no need to spend money! Kipkay shows you 4 awesome hacks you can make in this "household hack pack" video.

In this how-to video, you will learn how to create your own tube top dress with lace and tulle. This will be useful if you need a unique dress for prom. You will need a sewing machine, scissors, pins, ruler, measuring tape, thread, a half yard of gray knit, tulle, and a yard of lace. First, cut out a rectangular piece that can fold in half. The lower half is a trapezoidal piece. This will be the jersey skit. The smaller end should fit around your waist. Lay the rectangle first and then put th...

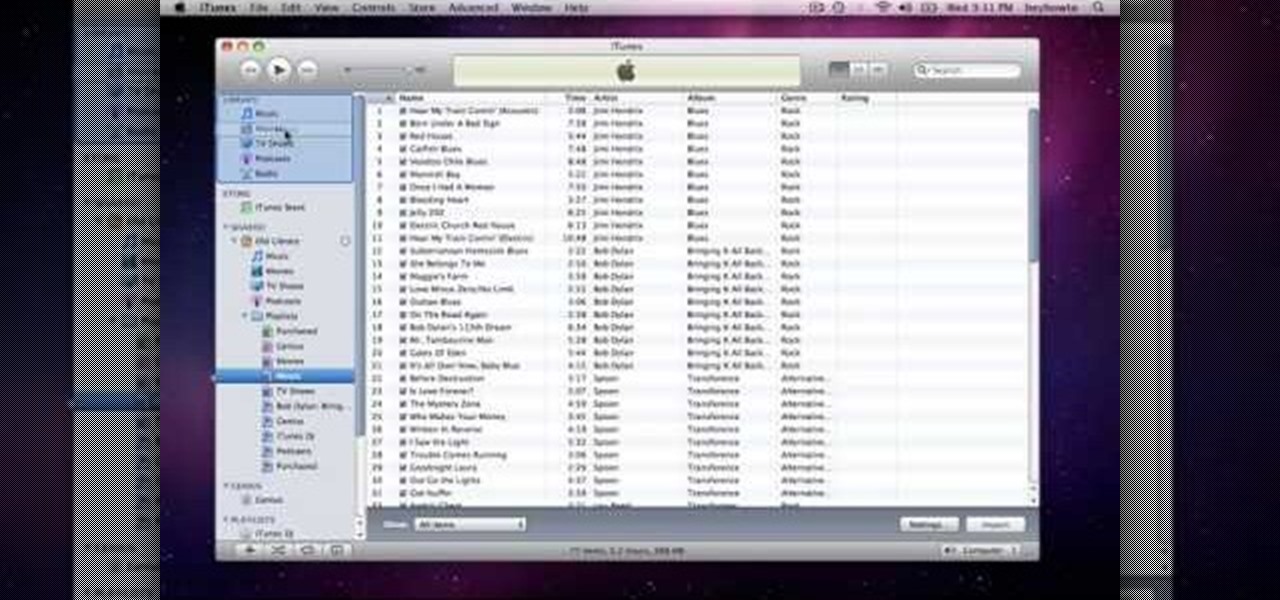
How to use Home Sharing in iTunes 9 to transfer music files to another computer. First make sure both computers have iTunes version 9 installed. To check this go to the iTunes 9 menu next to file in upper left and select the about item. On windows machines this will be in the help menu. In the computer with the music files we need to make sure the iTunes library is nicely organized. Again go to iTunes menu, this time open the preferences menu, and advanced icon. Check mark both sections "Keep...

You can add USB ports to your PS3 at home. Put two new ports onto the back of your PS3 for a total of six ports to get even more out of your machine. You will need a basic knowledge of circuitry and some electrician equipment to do this the right way. This video will show you how to add USB ports to your PS3. Keep in mind that this video does not show you how to reassemble it so be sure to keep track of your work.

Southwest Yard and Garden teaches viewers how to prepare garden soil for planting. You can use compost to work this into your soil. You can make your own compost and you can also buy compost. First, you can use a flat bladed spade or a sharp shooter spade to double dig your garden soil. First, you should dig double deep into the soil and turn the soil to the side. What you want to do is dig a trench. Go back to the beginning of the trench and dig a second depth. You will want to get below the...

This video on typhoon preparedness comes from Andersen Air Force Base in Guam, where typhoons are common. The key to surviving a typhoon or other disaster is preparation. Stock up on enough food and supplies to last your family for about a week. Routinely check expiration dates on food, water and batteries and rotate your stock. Be sure window screens are in place and in good condition in the event the power is off for several days.

Master Gardener Rosamarie Maddox asks John White, Doña Ana County Extension Agent, about problems facing her pecans, grapevines, and native shrubs. An unidentified insect found on her pecan tree is identified by John White as a Twice Stabbed Ladybug. This ladybug is a useful insect that often over-winters on the tree and helps takes care of the aphid problems faced by pecans. Pink fuzzy coating on pecan nuts is also brought up. The coating is normal for pecan and contains bitter tannin. Too m...

Blue corn is a special variety of corn which can be differentiated by the majority of the corn species by looking at the unusual top growth of the corn. It is a hybrid and grows very uniformly throughout. Now take a corn from the field and peel it off. You shall notice that it has a blue color corns. Blue color corns are hard from outside but they are very soft and tender in the middle. You can use these blue corns in making commercial products like blue corn chips, tortillas, and atole ’,‘ c...

This video tutorial demonstrates tips for how to organize your home office when you are visually impaired. Here a rehabilitation specialist is helping a visually impaired person. The person who is visually impaired should know what is visually important to him/her. Mostly these people obviously need to know where every thing is because they don’t have their eyes to depend anymore. Here visually impaired person is 66 year old Deanne Jackson. She has wet macular degeneration. In order to set up...

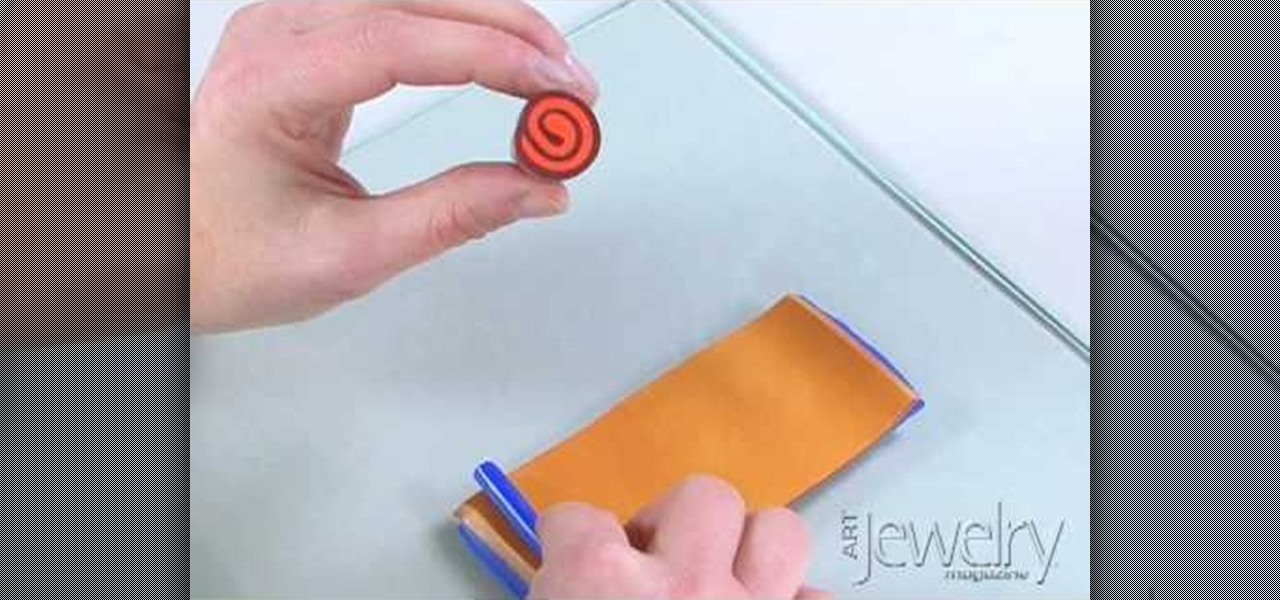
Jill Erickson from Art Jewelry Magazine demonstrates how to make a Jellyroll cane with polymer clay. Condition two different colors of clay by running them through a pasta machine set on medium. Then, trim off any rough edges. Stack the clay on top of each other and place a little bit of pressure on it to confirm the two layers. Using a blade slightly bevel the edges. Slide the blade underneath the two layers of clay for easier handling. Place a think snake of clay in the contrasting color on...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Twelve years ago Google launched its Cloud Platform, and the world has never been the same. This suite of cloud computing services has changed how modern businesses operate. Whether you use it for data storage, management tools, computing, or machine learning, the Google Cloud Platform is essential.

More information is available to us now than ever before. We simply cannot make sense of so much data on our own. Thankfully, we have programs to do the heavy lifting for us.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.