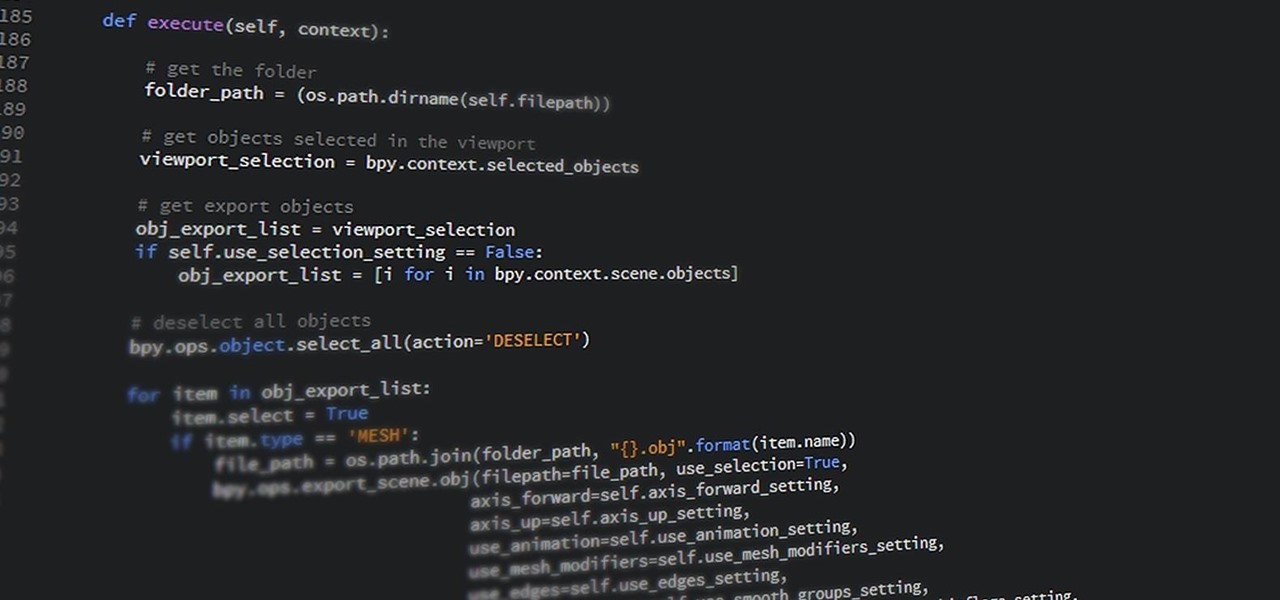
There is plenty of evidence to suggest that learning to program is becoming a highly lucrative and useful skill. Monster.com called coding "the skill you need today" if you want a job in some of the highest-paying fields out there. If the last year has proven anything, working online requires a strong digital infrastructure that someone has to help build. That someone can, and should, be you.

Want to land an exciting new job, get that promotion, or simply become more productive in 2021? Project and quality management are invaluable, transferable skills that will improve your efficiency in almost any industry. Right now, "The Premium 2021 Project & Quality Management Certification Bundle" is on sale with an amazing 98% off the regular price of $4,400, for just $45.99.

Want to take your productivity to the next level in the new year? Whatever industry you're in, The Complete Google Master Class Bundle will teach you the tips and tricks to become more efficient and highly skilled in its most popular apps. Right now, the entire bundle is on sale for just $39.99 — that's an amazing 97% discount off the regular price of $1,990.

Ready to take the next step in your career and become an Amazon Web Services certified cloud practitioner in 2021? The complete AWS Certified Cloud Practitioner All In One Bundle is the easiest option to help you kill the exam — and right now, the entire bundle of courses is on sale with 91% off, for just $24.99 (regular price $300).

Microsoft has plenty of products that you're likely familiar with, especially if you work or dream of working in IT. One of the most important now and in the future will be Azure, the company's cloud computing service. You might not know it, but a significant portion of the internet runs on Azure, and that share of the web is projected to keep growing in the coming years.

Did you know there's a way to make animating your own cartoons that's way easier than it looks — and that you can learn all the skills you need from home? Whether you want to pick up a fun, creative hobby over the holiday season or learn the skills to start working in animation, The Ultimate Cartoon Animator 4 Pro Mac Bundle will have you quickly making your own cartoons. Right now, it's on sale for 74% off, at just $49.99 (regular price $196).

Whether you want to build your own website for your business, start your new lucrative career in web development, or gain a wealth of projects to add to your portfolio, this course will help you do it. And right now, "The Complete Web Developer Course" is on sale for just $14.99 — a staggering 92% discount off the regular price of $199.

If you have information technology or computer science aspirations — even white hat hacking — then Python is a programming language you absolutely have to be familiar with. According to a recent survey of industry experts, Python is the fastest-growing language in the developer field. It's also one of the most sought-after skill sets among employers and is responsible for some of the best hacking tools.

Coders are accustomed to working remotely. The beauty of coding is that all you need is a laptop and a WiFi connection, which makes working anywhere a fairly simple transition. If you're looking for a career change, now might be the perfect time to give coding a try.

Java is one of the world's leading programming languages thanks to its virtually endless array of applications. Since Java's initial release in 1998, this Open Source platform has become beloved by coders for its speed, flexibility, and dependability.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

There's something seriously wrong with Apple's new Shortcuts app, and it's severely limiting the number of shortcuts users can install on their iPhones.

While numerous startups are competing to convert the AR Cloud from a pie-in-the-sky to a reality, Wikitude is thinking smaller with the latest edition of its augmented reality SDK.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Mobile World Congress is a four-day event that is both a showcase and conference starring prominent figures in the mobile industry. Oftentimes, OEMs will use this event to announce new products for the upcoming year — and this year shouldn't be any different. Here are all the phones we expect to be announced.

While it's easy enough to make yourself invisible on Snap Map, nothing is quite as private as not having a Snapchat account at all. Whether you're concerned about your privacy or you simply never signed up for the social media platform, Snapchat's web-based map is an easy way to check in on what's happening in your area and beyond.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

When Apple announced their ARKit platform in June, they immediately staked the claim to the largest augmented reality hardware platform, with millions of iPhones and iPads compatible with iOS 11 becoming AR devices this fall.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.

A group of researchers from Stanford University and Princeton University has put together the largest RGB-D video dataset to date with over 1,500 scans of over 700 different locations across the world, for a total of 2.5 million views.

In the past, to see a pre-constructed state of the house that you would one day live in, you had to be able to read blueprints or hire an artist to sketch it out. Later came the ability to have a 3D rendering of that house on a screen, but you'd still have to work hard to envision it in real life.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.

Students have been passing notes in class for decades, so what's the big deal about sending a quick text message? Everybody does it, even your teacher was surely guilty of covertly communicating with his or her peers back when they were in high school.

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

I like to think of myself as a pretty calm and even-keeled person. I rarely get angry or annoyed, and I don't even get peeved very frequently.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Just what are probiotics and why are they so good for you? Probiotics are "viable microorganisms" that can confer lots and lots of health benefits if they reach your intestine while they're alive. You may have heard them described as "friendly bacteria."

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

See how fast and precisely you can transfer glass onto the mandrel using our electric mandrel spinner. An electric mandrel spinner is a tool that grips materials to be spun or machined. Watch this instructional lampworking video to see how molten glass may be shaped with a mandrel spinner. Mandrels are commonly used to shape beads of glass into a desired size and shape for jewelry manufacturing. This video shows you how to build transfer glass from the cane using a lampwork torch and an ele...

This video shows the features of the Deluxe electric mandrel spinner. An electric mandrel spinner is a tool that grips materials to be spun or machined. Watch this instructional lampworking video to see how molten glass may be shaped with a mandrel spinner. Mandrels are commonly used to shape beads of glass into a desired size and shape for jewelry manufacturing. This video shows you how to use all of the features of an electric mandrel spinner.