See how you can quickly, easily, and consistently you can make uniform lampwork spacers using the Electric Mandrel Spinner. An electric mandrel spinner is a tool that grips materials to be spun or machined. Watch this instructional lampworking video to see how molten glass may be shaped with a mandrel spinner. Mandrels are commonly used to shape beads of glass into a desired size and shape for jewelry manufacturing. This video shows you how to make glass spacer beads using a lampwork torch an...

Here is a tutorial on getting a perfect 1/4" seam allowance for quilt piecing. The sewing machine foot will sometimes have a groove to allow you to make a perfect quarter inch seam automatically. If you don't have one of these, there are a few ways to make your own quarter inch seam guide.

This video animation tutorial demonstrates a technique for creating a fabric-like effect out of clay for stop motion figures, or armatures. Instead of smooth clay, try to give a more authentic finish to clay that will be used to create clothing. This technique will also create patterned fabrics. You'll need to chop the clay up first in a food processor, and then put it through a pasta machine. Watch this instructional video and learn how to make clay look like fabric for claymation armature c...

Check out this tutorial that teaches you how to make a cotton reusable grocery bag out of bandanna. All you need is 2 bandanas, sewing thread, a sewing machine, scissors, and marking pens. This is a great, fashionable way to go shopping and cut down on plastic bags. Watch this how to video and you can save the earth in style with reusable grocery bags.

This video will show you the proper technique for getting your snowmobile out of the snow after it falls and gets stuck in a snowdrift. Snowmobile safety is important and this video will show you just how you can keep your machine out of the snow.

Whether you're heading to a frat party, out for Halloween or just looking for a cool way to tie your towel at the beach - this video is here to help! Learn how to tie a toga, the ancient Greek way of dressing, and be ready for whatever costume situation may arise with a quick and cheap outfit!

Summer is just around the corner and those jeans that seemed perfect for winter aren't looking so hot. Put those jeans to use, and make your very own jean skirt. Grab a pair of scissors and a sewing machine and get started.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

In this video series you will not only learn many of the basics for Jazz dancing but how to put them all together. Our expert covers everything from the type of shoes that are best for training to how to isolate your head when performing a move. These hands on videos will walk you step by step through the fundamentals and show you how anyone can be a dancer, even you!!

It's Black Friday time, and in 2020, that means a lot of online deals to make up for more stores closing on Thanksgiving, as well as everyone avoiding in-person shopping because of the coronavirus. But while you may wish to grab a better 65-inch 4K TV, the new PlayStation 5, or some hacker hardware on sale, Black Friday is also the best time to invest in your programming and cybersecurity education.

Amazon Web Services (AWS) is the premier on-demand cloud computing platform. Offering a wide range of APIs to companies, governments, and individuals on a pay-as-you-go basis, this Amazon subsidiary pulled in over $35 billion in revenue in 2019 alone.

It feels like every few months, some new feature is discovered in the Pixel's Camera app. By taking advantage of machine learning and the high-quality camera, Google continues to add hidden functions that improve your life even if they're a little niche.

In a world that's becoming increasingly dependent on a variety of AI and machine learning applications, Big Data reigns supreme. As the primary forces behind everything from self-driving cars and surgical robots to home automation systems and even space exploration, Big Data and AI stand at the heart of today's most important innovations.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

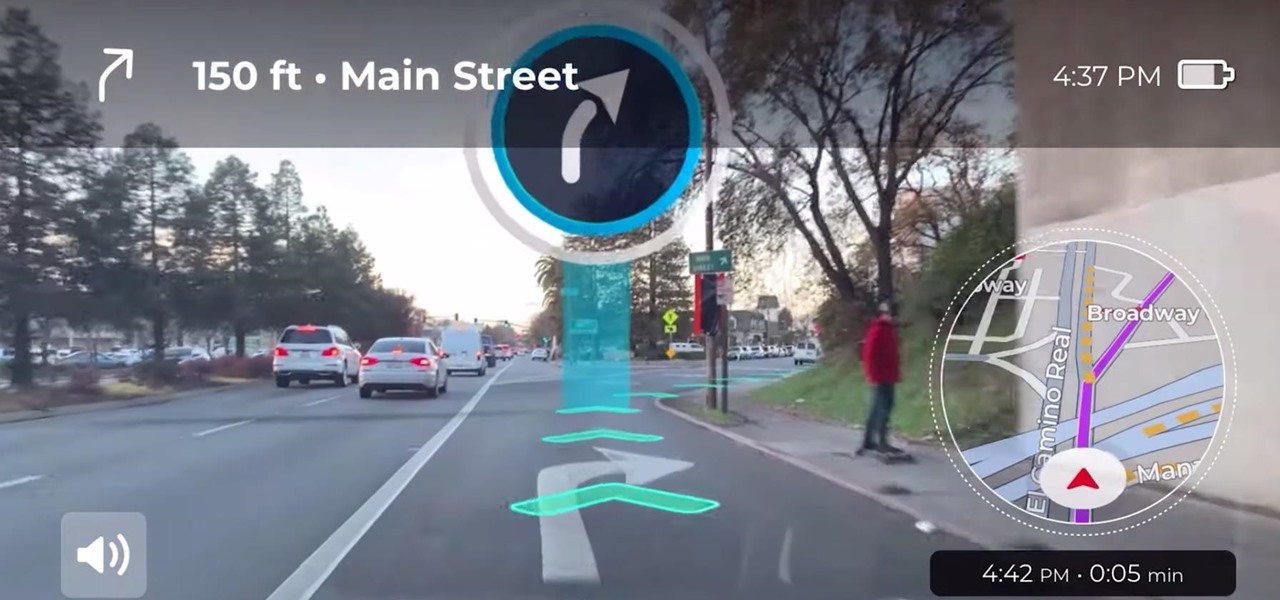
Google pushed a new kind of augmented reality walking navigation to the mainstream last year, and now startup Phiar is hoping users will use its AR app in the same way for driving navigation.

When Google introduced the Call Screen feature with the Pixel 3, I had never been more excited to get a Pixel device. This AI feature provided real protection against rising spam and robocalls, which billions of people deal with each year. After a recent update to the feature, you can reduce robocalls and other spam calls to nearly zero.

After opening up its Spark AR platform on Instagram for all creators, Facebook is already expanding the platform's capabilities on its Snapchat killer.

As the demand for realistic volumetric video for AR experiences begins to grow (along with the available facilities and services for capturing it), researchers at Google have figured out how to improve upon the format.

With the imminent arrival of the HoloLens 2 expected any day now, Microsoft is preparing new users to take advantage of its software from day one.

Facebook and its Oculus subsidiary have been open about their intentions to bring AR wearables into the mainstream for some time now.

Roughly six months after emerging from stealth, AR cloud company 6D.ai is now ready for public consumption, and it has a big name partner to help it kick off its platform.

So you've been using iOS 13 for a little while and noticed your iPhone is pretty slow to charge. Using the 5-watt power adapter out of the box, in the time it used to take your iPhone to charge its battery to 100 percent, your iPhone is stuck at 80% or below instead. That's because Apple introduced a new feature in iOS 13 that slows down charging — but for a good reason.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

I'm here at the annual AWE event in Santa Clara, California, and the venue is just as packed, if not more so, than last year.

Because of its ability to place digital content into the real world, augmented reality lends itself well to artists and creatives.

After applying augmented reality as a solution for the sale and marketing of sneakers, Nike is taking the next step in its adoption of AR to improve the customer experience.

After announcing at Google I/O 2019 that augmented reality content would come to Search, Google revealed how it would make that happen with the latest round of updates to ARCore.

The Pixel is the phone to beat when it comes to cameras, and it's largely due to software. While its hardware is solid, Google's machine learning prowess and general coding wizardry are the biggest reasons the Pixel is so good with taking photos and recording video. What this means is that if you can get the Pixel's camera software, you can replicate the Pixel camera experience on other phones.

We've seen a variety of AR experiences related to athletic footwear over the years, but Puma is betting sneakerheads will buy into a version of interactive design where sneakers are the augmented reality experience

The long guarded veil of mystery surrounding Magic Leap for years was finally lifted last year when the company revealed its Magic Leap One device.

While Google isn't ready to commit to a wide release of the AR walking navigation mode for Google Maps, the company has begun testing the feature with members of its Local Guides crowdsourcing community.

The HoloLens has made enough of an impact on the healthcare industry for Microsoft technology partner Medivis to convince investors to pledge $2.3 million in funding for its surgical platform.

With Magic Leap One approaching six months since launch, Magic Leap is fully focused on building a content ecosystem and developer community.

Move over, cosmetics companies. The athletic footwear industry wants to be able to give their customers the opportunity to try on products in augmented reality as well.

The release of Avatar Chat for Magic Leap One and Spatial for HoloLens during the fourth quarter of 2018 appeared to revolutionize video calling via augmented reality.

While the technology companies continue to drive forward with autonomous vehicles, Nissan's vision of the future of self-driving automobiles lies in a cooperative experience between human and machine, facilitated by augmented reality.

The iPhone X introduced the world to Face ID in 2017, and now, every new iPhone uses Apple's biometric security system instead of the old Touch ID. It's more secure than fingerprint scanners and it's even more user-friendly. True, it's not without its faults, but at least one of the biggest problems can be fixed.

Hollywood has already proven that it's on board with augmented reality, with examples ranging from Avengers: Infinity War to Ralph Breaks the Internet. But one startup wants to make the augmented reality content that's being used to promote TV and film entertainment smarter.

Augmented reality content makers often position the technology as a new storytelling medium. And who loves stories more than children?