
Today's Top News: Elon Musk Warns of Zombie Driverless Fleets
Tesla founder and CEO Elon Musk offered some insight into how hackers might seek to turn driverless cars into zombie fleets, but remained upbeat about what can be done about it.


Tesla founder and CEO Elon Musk offered some insight into how hackers might seek to turn driverless cars into zombie fleets, but remained upbeat about what can be done about it.

So it's 2017 and there are no flying cars and teleportation devices around, but there might be holographic smartphones sometime soon. As cool as that sounds, should we trust a holographic smartphone from a company that has never made smartphones before?

A few years ago, the Hilton hotel group unrolled the Digital Key, a feature of the Hilton Honors app that allows you to unlock your hotel room with your smartphone.

China's Baidu, the Chinese equivalent of Google, live streamed a video yesterday of CEO Robin Li riding a self-drive vehicle along the streets and highways of Beijing.

Volvo Cars' claims it will offer Level 4 models by 2021 means the premium carmaker will likely have to finalize the driverless design to meet the aggressive timeline by next year at the latest.
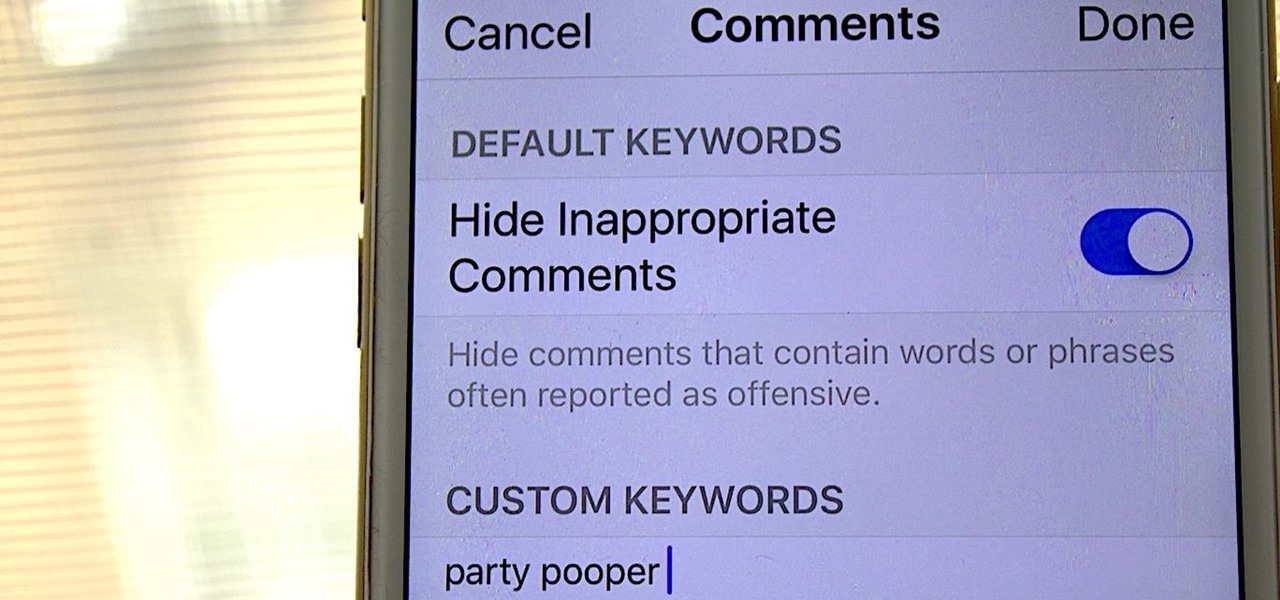
One of my favorite things about Instagram, and the reason why it's still my go-to app, is the fact that it's not like Facebook or YouTube. After our last presidential election, well, I think we've all been scarred from going anywhere near Facebook. And YouTube, I'm not sure why comments on that platform are some of the worst, but they are.

Who would have thought back in 1991 that you'd eventually be able to play Sonic the Hedgehog whenever and wherever you wanted? Not a crappy Game Gear version, either. I'm talking the full Sega Genesis version of Sonic, available to you on a bus, a plane, or in a rest-stop bathroom. Now imagine how those people would react if you told them the game would also be free. They would think you were crazy.

A new Google Search update lets job-seekers streamline their search process. Searches like 'jobs near me' are now designed to show relevant opportunities from multiple sites.

Much work needs to be done before laws and regulations no longer block driverless' rollout in the US, Rob Csongor, vice president and general manager of Nvidia's automotive division, said today during a US Senate committee hearing.

Waymo revealed more clues about its future business model after it said yesterday it plans to kill its Firefly pod-like car project and focus more closely on offering driverless systems for commercially available car and truck models.

During the opening keynote of their Worldwide Developers Conference today in San Jose, Apple introduced the ARKit for the new iOS 11 that will bring augmented reality apps to millions of compatible iPhones and iPads.
Over the past week, we are seeing more companies capitalizing on services leveraging augmented reality. One company secured funding to expand their service, while two other companies grow its own services through acquisition.

Our canine best friends could spread our bacterial worst nightmare, according to a recent study. The problem with drug-resistant bacteria is well known. Overused, poorly used, and naturally adaptive bacteria clearly have us outnumbered. As science drives hard to find alternative drugs, therapies, and options to treat increasingly resistant infections, humans are treading water, hoping our drugs of last resort work until we figure out better strategies.

According to Electrek, Tesla CEO Elon Musk, in a covert conference call with a select few investors, commented in detail about his plan to have Tesla's Model 3 driving on the road earlier than we all expected.

Norovirus outbreaks occur all year long, but peak in the winter months, which means we are in the middle of norovirus season. But there's still time to protect yourself from the highly infectious bug.

Don't let the lack of owning a HoloLens stop you from joining in on the fun of creating software in this exciting new space. The HoloLens Emulator offers a solution for everyone that wants to explore Windows Holographic development.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

Copying files from a computer to your Android device has always been pretty straightforward—just connect the two devices with a USB cable, open your desktop file explorer, then move the files over. But what if you didn't need any wires at all?

Before we dive any further into getting your Mac ready for hacking, I wanted to continue on with the concept of encryption. In the last part, we talked about full disk encryption on your Mac, but now I want to quickly cover the encryption of disk images before we dive into managing passwords, terminal emulators, etc.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.
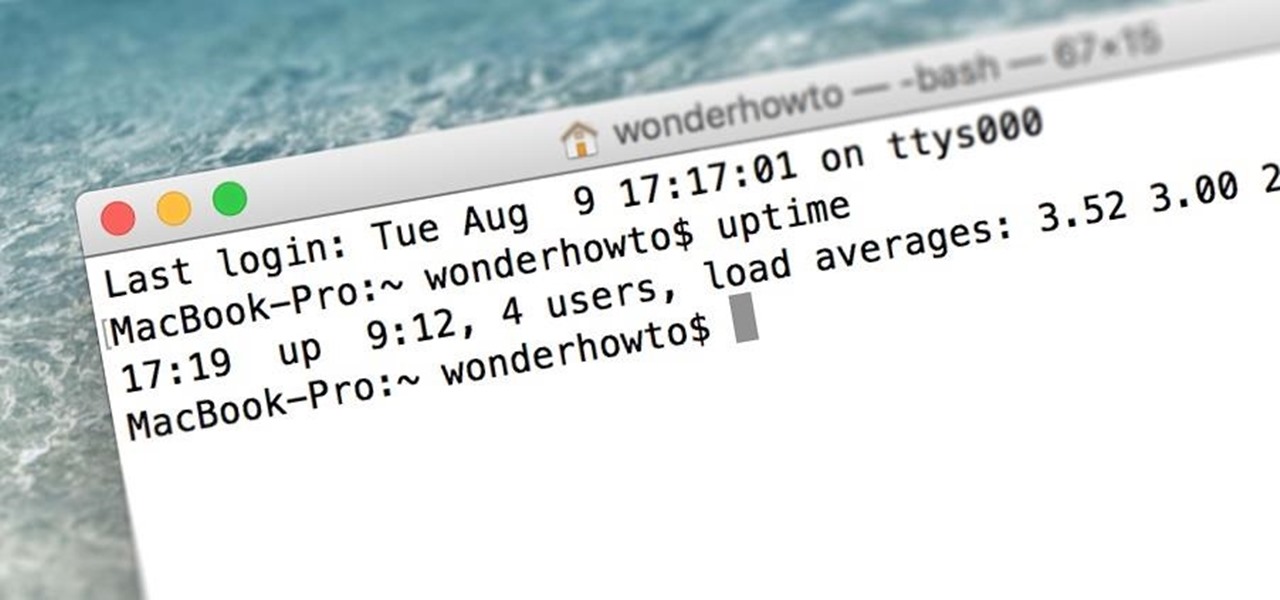
When was the last time you restarted or shutdown your Mac? In the post-iPhone era, most devices are now powered on almost constantly. For better or for worse, the computing landscape has accommodated this "always on" trend, but you still need to periodically restart your devices—especially your Mac.

If you spend weekend mornings sadly turning your omelet attempts into scrambled eggs rather than enjoying a perfectly flipped omelet, reach for a resealable plastic bag. Using a ziplock bag to make an omelet is not only foolproof, it's the perfect solution to cooking for a crowd, where you can make everyone's customized omelets at the same time. How cool is that?!

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

Whenever I go to Jamba Juice, I usually gravitate towards either the Matcha Green Tea or Caribbean Passion smoothies. But when I learned about their secret menu a few years ago, I felt like a little kid all over again—especially with flavors like Pink Gummy Bear and Orange Dream Machine.

Over the course of the past century or so, media consumption has gone from a few readers enjoying their local print publication to billions of users viewing countless hours of video across the globe each day. This was a gradual evolution at first, but recent advancements in mobile connectivity have sent us into a climb the likes of which we have never seen before.

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Stock is a crucial ingredient for so many recipes: soups, gravies, and risottos depend on stock; quinoa and rice are both more flavorful when cooked with it, too. So, chances are that broth is a staple on your weekly shopping list.

Welcome back, my greenhorn hackers!

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkernel.org/2015/12/11/embed-metasploit-payload-in-apk-easily/
Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget you ever used Windows Vista... almost.

Greetings null-bytians. Firstly, I would like to apologize for the no images thing. I guess I can't upload them.
Greetings null-bytians. Say you have been able to penetrate your neighbour's AP, and of course you had spoofed your MAC address. Now you go on and test to see with excitement if the password really works and the MAC is still spoofed. You login successfully and you browse the web forgetting to check what your current MAC is. Well, if you may do an ifconfig command, you will see that your permanent MAC is being used. Oh!! and guess what, ... your real MAC has been logged. Even though there is t...

The standard way to make pasta requires a lot of water, and it takes a long time for that big pot of water to actually start boiling. For these reasons, as well as my hatred for washing large pots, I don't cook pasta at home very often—at least not the traditional way.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...