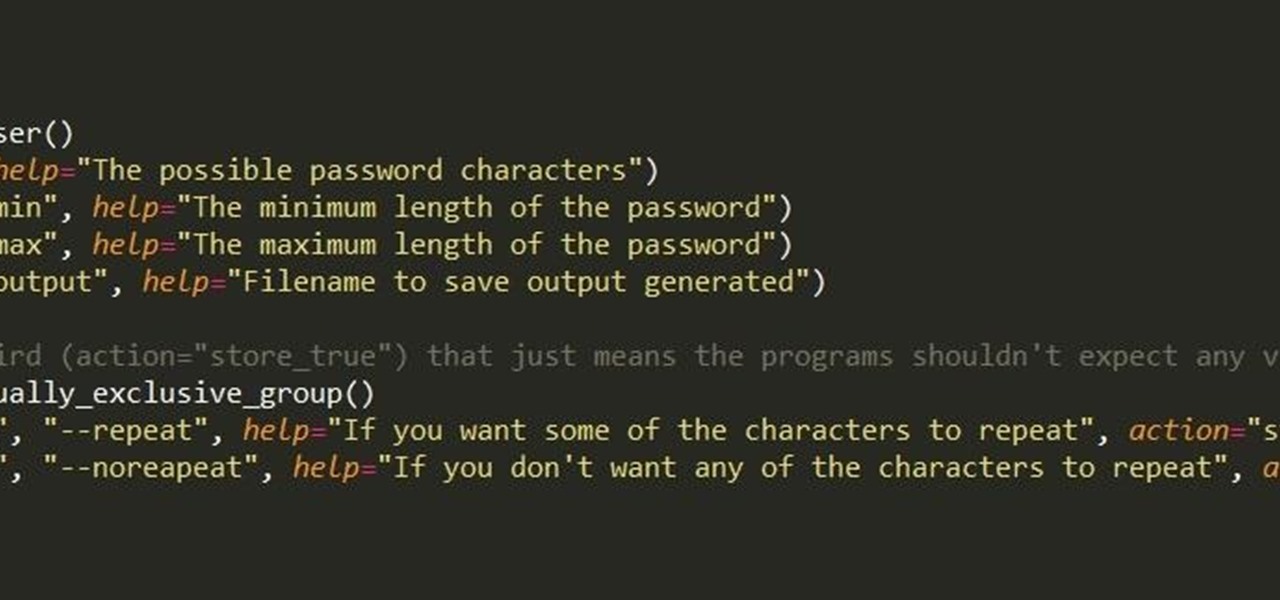
First of all, I hope the title makes sense. :D Well, this is basically creating a program that can help with dictionary attacks. Generate possible passwords. It pretty much lies in you knowing the person you want to hack.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...
This brief video outlines how to keep the paragraphs of your IELTS argument essay linked.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

This video is about showing you how to use feng shui in repairing your dysfunctional family and getting rid of the bad vibes that may be in your home, re-energizing the foundation of love. The family center is located on the left center of your home. The element for the family is wood and you wouldn't want to have dead or plants with sharp leaves because they start arguments. Too much red is considered the fire element and can also lead to your family having arguments. If you have metal in yo...

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Hello everyone. I've recently made the annoucement of the Null Byte suite of tools, and we've covered how to download and install it. Now it's time we cover how to submit a tool for inclusion into the suite. It's relatively simple, but we need to get a few ground rules out of the way.

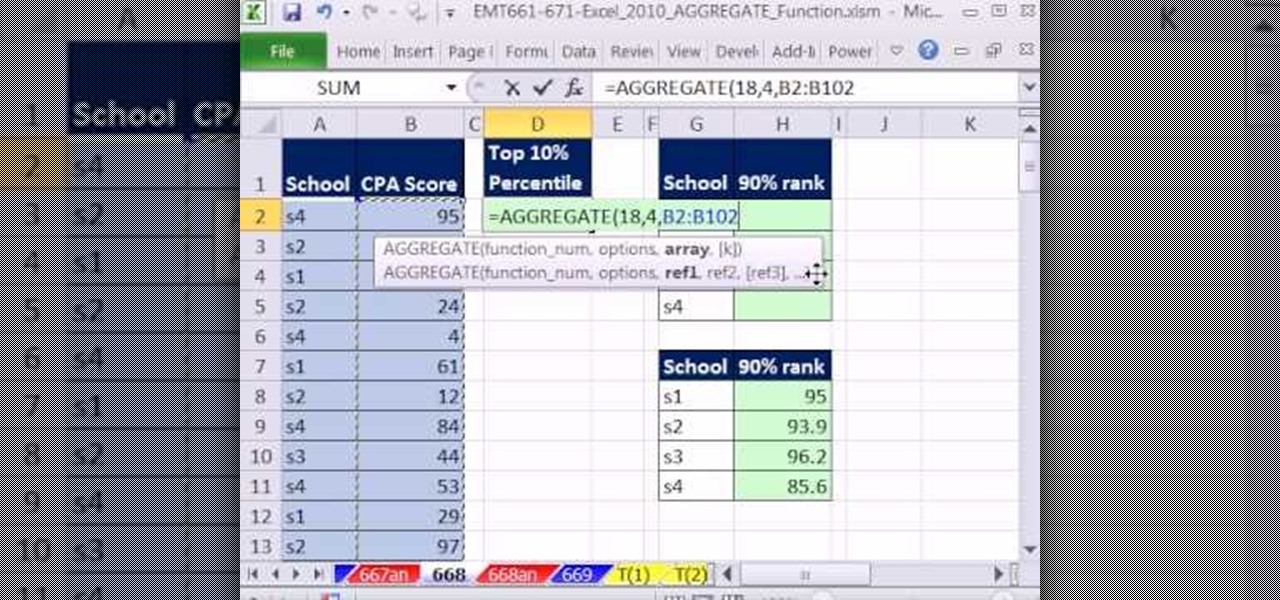
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 669th installment in their series of digital spreadsheet magic tricks, you'll learn how to use the AGGREGATE function in Microsoft Excel 2010 and later. This new function is better than SUBTOTAL function because 1) the options argument set to 18 will calculate Percentile and 2) AGGREGATE can handle arrays. See how th...

In this clip, learn how to make the right phone calls and press the right buttons to "trick" your phone company into giving you a free phone upgrade before you are due. You will also learn how to save money on you phone bill by using a few choice words on the telephone. This trick works for Sprint, Verizon, T-Mobile and AT&T, so not matter who your carrier is you will be golden. This clip is hosted by an ex-employee from a cell phone company, so it is full of insider tips.

Onion rings or French fries? The debate for which American-food side dish is superior will rage on until the end of cooking. This video makes a very convincing argument for the supremacy of the onion ring, presenting a recipe for them using unconventional ingredients to create what the chef in the video insists are the most delicious onion rings on Earth.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, but the location is "beyond the Caucasus mountains," which could imply Russia?) desperately want their hands on this system.

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

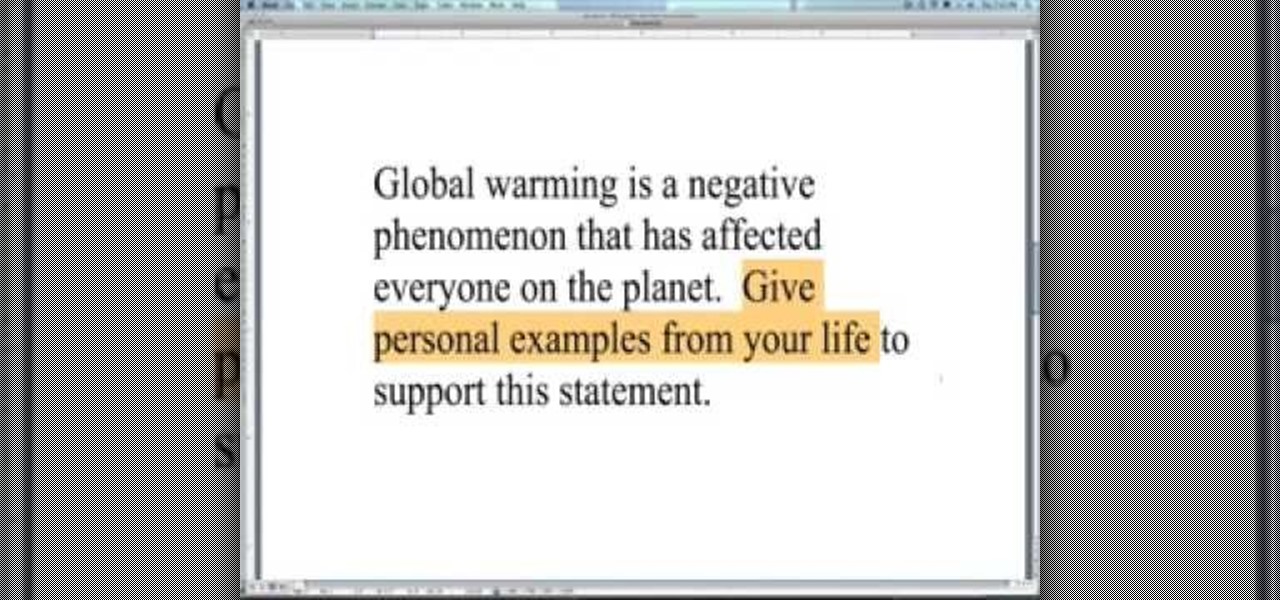
In this video, we learn how to write a good argumentative essay introduction. This is a persuasive essay that is just an argument. What makes this an essay is that it has an introductory section, main body, and concluding section. Many high schools and universities will require you to write an argumentative essay. You will first need to understand the process of writing the paper and then look at good and bad examples so you can get ideas of how the paper should look. Remember that you should...

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 684th installment in their series of digital spreadsheet magic tricks, you'll learn how to do single-condition lookup adding for both the VLOOKUP and HLOOKUP functions. You'll also learn how to use an array constant in the row/column num argument for the HLOOKUP and VLOOKUP functions.

Jessica shows you how to relieve some anger and stress by turning your ex-boyfriend's favorite pair of jeans into new low-rider, distressed, destroyed vintage shorts in this fun tutorial. First step: fray them on the pockets and seams by using an X-acto knife. Just scrape the knife along the edges of the pockets/seams, which will take around five minutes per 2-inch section. Step 2: distress them by taking a pair of scissors and making a cut in the both knees. Then take a seam ripper (availabl...

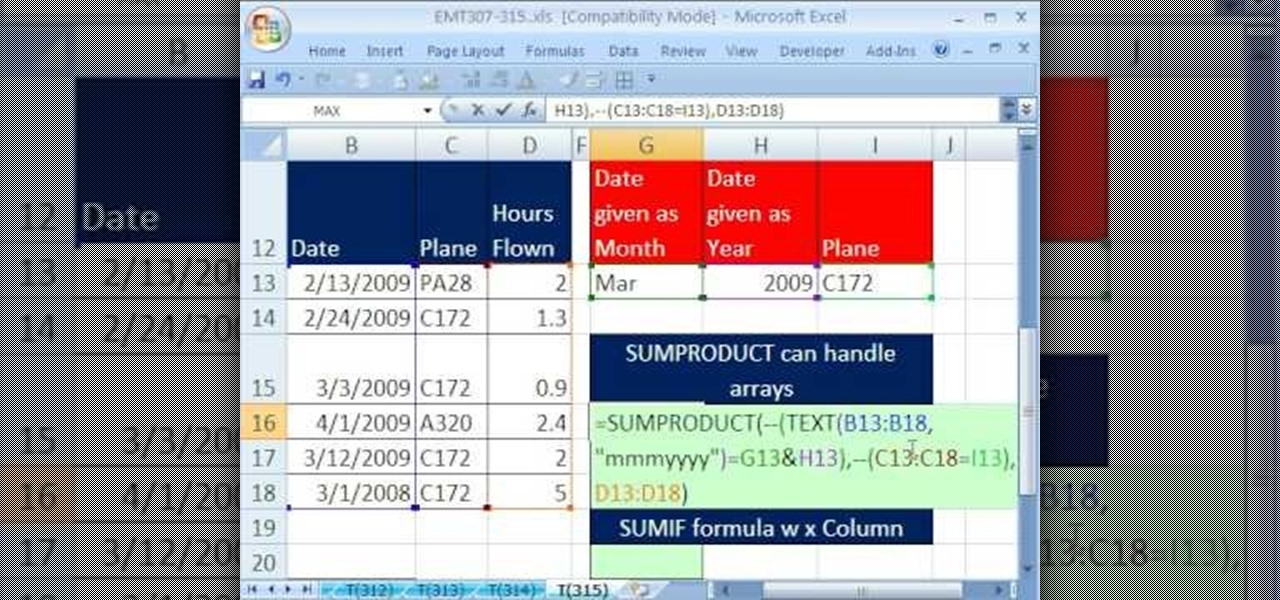
New to Excel? Looking for a tip? How about a tip so mind-blowingly advanced as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 315th installment in their series of digital spreadsheet magic tricks, you'll learn how (and when) to use the SUMIF & SUMPRODUCT functions.

How you work out your abs determines how they'll appear in the long run. Not only are the type of ab exercises you do important, but also the frequency with which you do them.

In this tutorial, we learn how to teach children to be gentle. If children are in a setting with other kids, arguments will arise. If a child happens to try to harm another, you will need to tell that child that it hurts the other one if you harm them. Tell them that it's not nice and that they need to say they are sorry for not being gentle. Tell them that it is a nice thing to be gentle with other people and they will make friends by doing this. This will help your child be gentle and make ...

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun and Mr. Excel, the 52nd installment in their joint series of digital spreadsheet magic tricks, you'll learn how to use the INDEX function to turn a Ctrl + Shift + Enter array formula into just an Enter array formula. Avoid Ctrl + Shift + Enter by using the INDEX function and a blank as the row argument.

In this video, we learn how to use personal pronouns in an IELTS essay. Pronouns are: we, I, me, you, and us. These are words we use to describe ourselves and should generally be avoided in an essay. There are times when it's difficult to avoid personal pronouns in essay, but only use these when you're being asked to or are supporting an argument. An example of how to avoid using personal pronouns is: "I believe that" could be changed to "it is believed that". Once you learn how to replace pe...

If you've been waiting for the college football season to arrive or need to get your hands on some football, then NCAA Football 11 may be what you need. This video game has made some changes since the last installment and is even being considered better than the Madden series. Whatever the argument may be, this game is perfect for any football fan.

There are always two sides to every argument. Usually when it comes to furniture, one side is for throwing it out or selling it to buy a newer more enjoyable looking piece, while the other side may want to keep it. Is there a way to compromise? You bet there is! When it comes to old looking or antique furniture, you can easily refinish it to make it look brand new and fit the style of your room. This tutorial will show you how to easily refinish antique furniture in a snap! Enjoy!

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 527th installment in their series of digital spreadsheet magic tricks, you'll learn how to enter VLOOKUPs 3rd Argument in four different ways: Number, COLUMN function, COLUMNS function, or MATCH function. col_index_num or Column Number for VLOOKUP

Elizabeth Chamberlain, with Space Lift, demonstrates how to make room for love with feng shui at home. First, find your focus room with your energy map by laying the energy map on top of your floor plan. The love area is the far right corner from the front door, facing in. If the love area turns to be an outside area like a patio, clean it up. Remove the cacti and pointy plants to reduce arguments in the relationship. Clear out any unfinished materials and projects. Next, complete the area by...

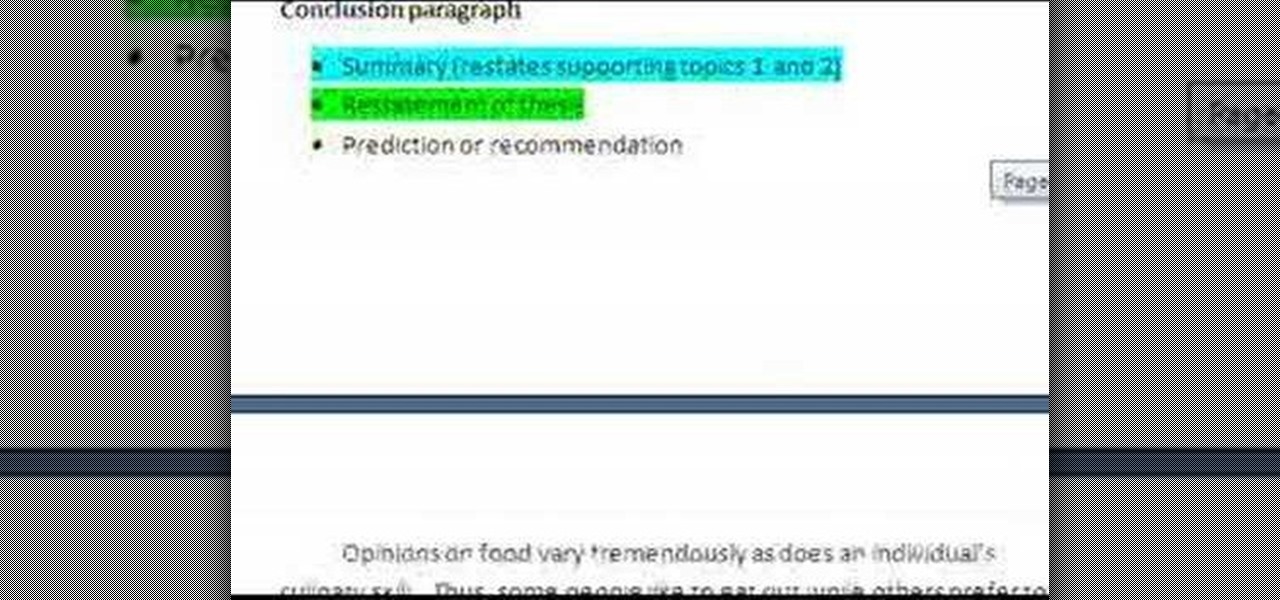
This video takes the viewer through a simple, step-by-step process for writing a compelling introduction to an argumentative essay. According to the author, an ideal introduction should begin with detailing the subject matter of the essay, and should provide the background information on the issue being discussed in the essay. The introduction should be very clear about the conclusion that the author of the essay is alluding at. One of the major problems with student essays is that their intr...

Well I've converted one of these rc bikes into a snarling (ha ha) nitro powered machine. I'm now going to convert my other stock model into a brushless monster. This particular bike had a rather bumpy crossing from the USA when I bought it from ebay. It got damaged in it's box and was returned to the sender. He, very nicely, found a new set of front forks, fitted them and posted it back to me, for no extra charge! Top Man! It's a bit sluggish, stock, so I think sticking a MAMBA MAX 7700kv mot...

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

In the last iteration of how to train your python, we covered if/else and conditional statements. We're going to diverge a little today and cover lists. Lists are simply that, lists. It is a set of values located under one variable. Now that we know the definition of a list, let's learn about them! List Basics

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

When the Nintendo 3DS XL came out, I traded in my regular sized Nintendo 3DS for one — but I ended up hating it. The XL just felt big and unwieldy, and because the screens were larger (with the same resolution), it ended up looking blurrier than the regular 3DS. This, to a less severe extent, is the argument for the Galaxy S9 against the Note 8.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.