Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Learn how to use more English phrasal verbs with this instructional English language lesson. get...over with

If you're going to build a coyote trap, you want to make absolutely sure you get it right. After all, the last thing you need to deal with is a furious coyote getting loose after you've trapped him! In this video you'll learn how to make a cheap and effective coyote trap.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Conflict is a part of life but how you deal with that conflict is up to you. You may find yourself in an argument and instead of making it a shouting match, employ some techniques that will be sure to keep this conversation civil.
With the TSA's full-body scanners occupying a great deal of airports nationwide, the debate remains as to whether air travelers should continue to be subject to immoral security techniques and possible health risks due to the x-ray scanning devices. The "advanced imaging technology" may help keep obvious weapons out of major airports, but scanning naked bodies seems more voyeuristic than crucial to national security. But while the argument continues, one woman is taking a stand… well, not rea...

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

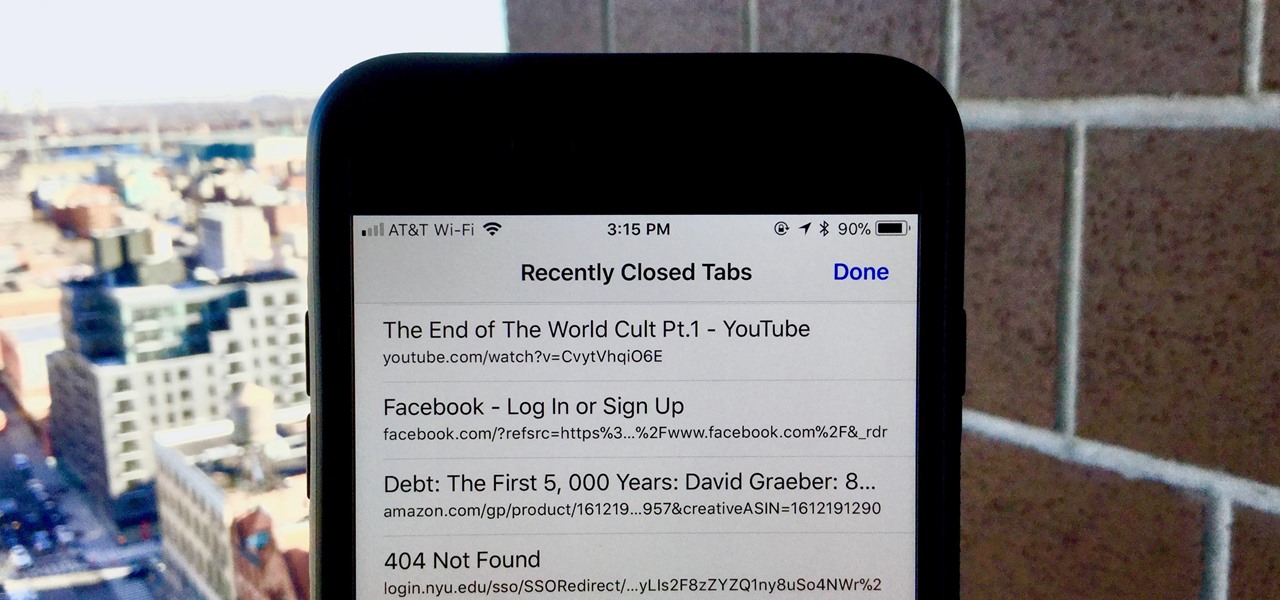
Almost certainly, you've closed out of a webpage that you didn't want to at some point in your iPhone-owning life. Whether you accidentally swiped the tab away or closed it only to need it moments later, tab-regret is just a part of our internet culture. Luckily, Safari on iOS includes an easy way to open recently closed tabs.

Exotic sports cars are the province of the ridiculously wealthy but, thanks to augmented reality, you can now get closer than ever to a Bugatti Chiron.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

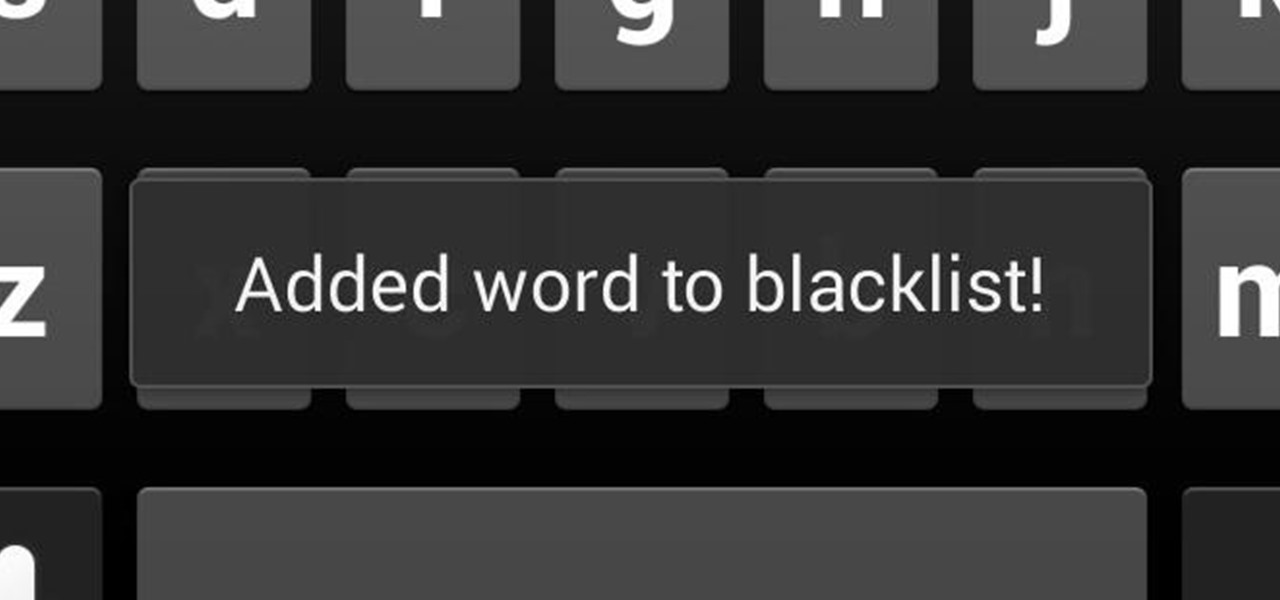
In the midst of furious finger typing on a small non-tactile screen, you're sure to make mistakes—so the majority of keyboards have autocorrect. Generally it works pretty well and is a welcomed feature.

Believe it or not, capturing a beautiful shot of a vehicle is more difficult than you think. Sure, you can just snap a photo, but capturing the design, detail, and essence of the car is a whole other story. Lighting, location, settings, and angles are play into how well the photographic representation turns out.

If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so inclined to take over your computer. How the Exploit Works

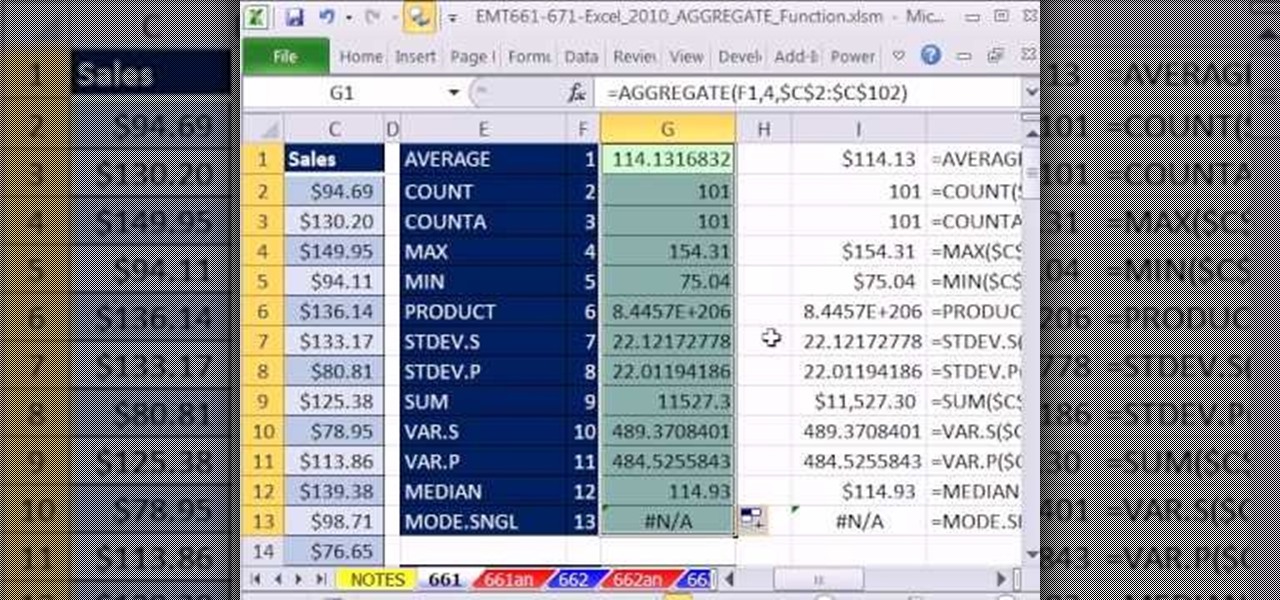
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 664th installment in their series of digital spreadsheet magic tricks, you'll learn how about how the new Excel 2010 AGGREGATE function that can calculate these 19 different functions depending on what number you put into the 1st argument of the AGGREGATE function. This is an improvement over the SUBTOTAL function wh...

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Steganography is the art of hiding information in plain sight, and in this tutorial, I'll show you how to use Steghide — a very simple command line tool to do just that. In addition, I'll go over a bit of conceptual background to help you understand what's going on behind the scenes. This is a tool that's simple, configurable, and only takes a few seconds to hide information in many file types.

Ever been in an argument, only to have the other person cop out by saying "I never said that," when you know full well they did? Or how about one of those times when you're sitting in the lecture hall, half dozing off to your professor's monotone ramblings, when your ears perk up because they somehow know you missed something important that was just said?

Welcome back! In our last training session, we covered some advanced list topics. We'll be going deeper into the advanced list rabbit hole today with lambda and lambda operators! (And I'm not talking about Gordan Freeman)

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

Welcome back! Sorry for being so quiet, I've been rather busy with this project lately! Anyways, in the last iteration of how to train your python, we covered lists. Today we'll be introducing iteration and the two loops python has to offer, for and while. Also, we'll be covering a couple general use functions. So, let's get started!

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

On-screen navigation buttons offer many distinct advantages over physical buttons—they can change orientation along with your device, they're capable of visually morphing to indicate secondary functionality, and the user experience is more consistent when buttons and app elements require the same amount of force to press. Add to that the fact that they're far less likely to fail and can be themed or even switched out altogether, and it's hard to come up with an argument in favor of physical b...

Check it out: you save more dough (ba dum bump) when you order a large pizza than with any other size. Why is this true? NPR reporter Quoctrung Bui's engineer friend pointed out that a medium pizza was twice as big as a small one, yet only cost slightly more.

People like Ralphige and The Jerky Boys have elevated prank phone calls to an art. Here’s how you can get in on the fun.

He's not exactly demanding sexual favors, but his flirting is getting really gross. What's a girl who likes her job to do? You will need diplomacy and documentation. Assess his behavior. Now, don’t be offended, but we have to ask: Is he really coming on to you, or is he just a sociable, flirtatious kind of guy? If it’s the latter, just ignore it. Do your part to keep the relationship professional. Don't chat about how your last two boyfriends cheated on you and then expect him to know that di...

Don't sign any termination papers until you're sure you've made the best deal you can. You Will Need

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

Use the Excel Vlookup function in Microsoft Excel 2007 to look up data in a table. This tutorial looks up the level and value of a product from a stock list using the Vlookup function in Excel.

Did you forget to get a Christmas gift for that niece or nephew who you see once a year? If you're lucky, the Walmart near you may have a Merge Cube in stock. When paired with the 57° North game for the Merge Cube, the mysterious-looking cube offers the possibility of extended sessions of virtual adventure in the palm of your hand. Available for $2.99 through the App Store or Google Play, 57° North is a choose-your-own-adventure game that takes place in augmented reality.

It appears a privacy lawsuit that began five years ago is about to come to an end, and you might get some money out of it.

Like most people, you probably use hand gestures when you talk, whether you wave your hands excitedly when discussing the latest episode of Game of Thrones or smack the back of your hand as you rattle off points during an argument. As your speech teacher probably told you, gesturing while talking is a great reinforcement tool—when used appropriately, of course.