
How To: Send Ghost Mail
Watch this video to learn how to send ghost mail. Send a secret message in email or catch someone who forwards your work off as their own. Watch this video tutorial and learn how to send email with hidden writing.


Watch this video to learn how to send ghost mail. Send a secret message in email or catch someone who forwards your work off as their own. Watch this video tutorial and learn how to send email with hidden writing.
If you're a heavy gmail user here's a handy way to sort your incoming emails from spam with a little known trick from Tekzilla.

This tutorial guides you through setting up a default email account using cPanel. This video is provided to you by Scandicsoft.

This is a short tutorial on how to add or delete email accounts using cPanel. This video is provided by Scandicsoft.

In this screencast, we show you how to quickly and easily set up an email filter in GMail.
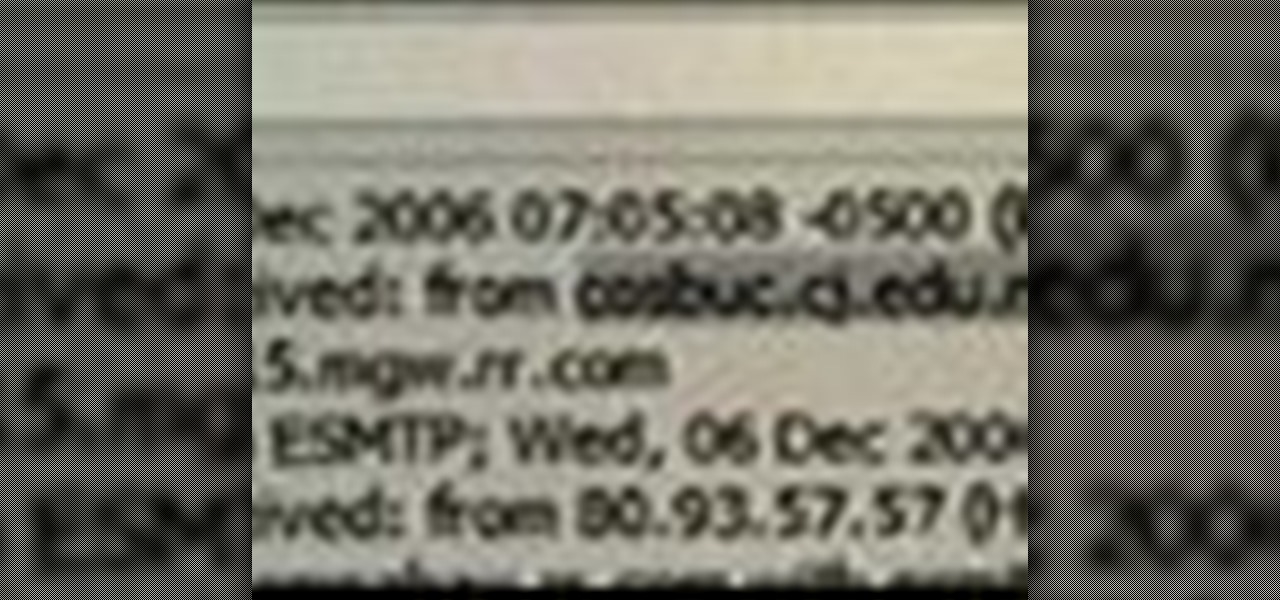
Kipkay explains how to trace any email and then see a map of where it came from. Go to your mail service, click on options, look for received from, and copy what is listed.

Need some IBM Lotus Notes help? Well, check out this video tutorial to learn how to have Lotus Notes remember the sorting of emails. This is a very quick and easy way of getting Lotus Notes to remember the sorting of emails. Easy to follow.
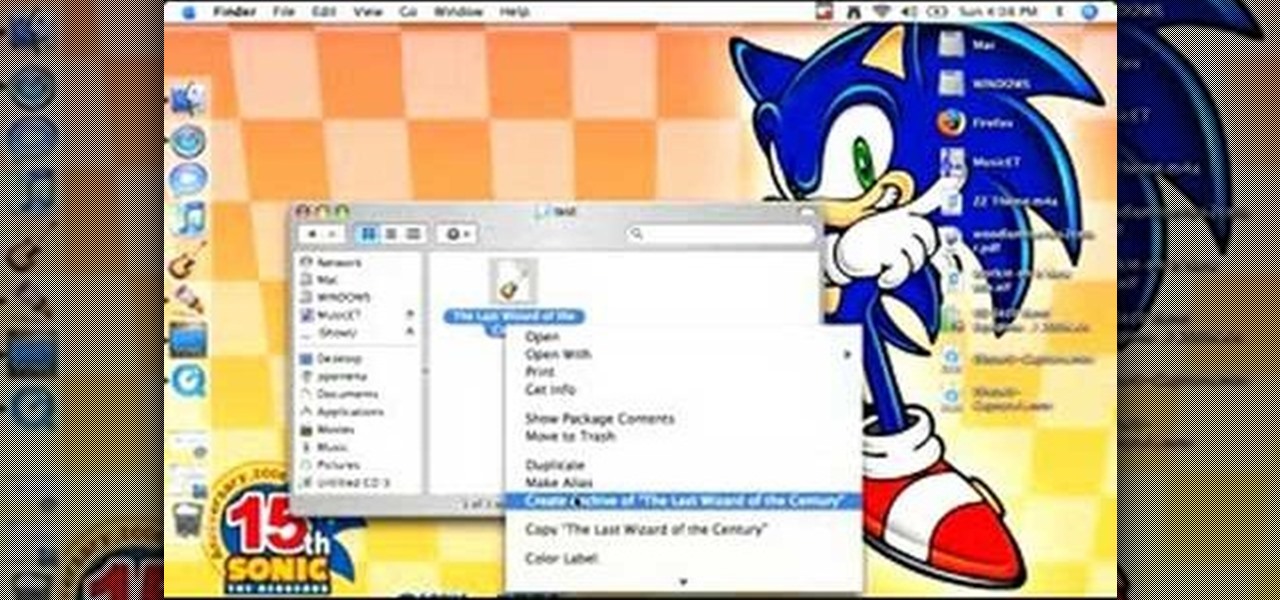
This software tutorial will show you how to email GarageBand files. Learn how to zip the GarageBand file and create an archive so you can email your GarageBand music files.

If you're new to Ubuntu Linux and, for whatever reason, not so very keen on Ubuntu's default email client, Evolution, then you might like to try Mozilla Thunderbird. In this tutorial, you'll how learn how to go about setting up an email account in Thunderbird. Take a look.
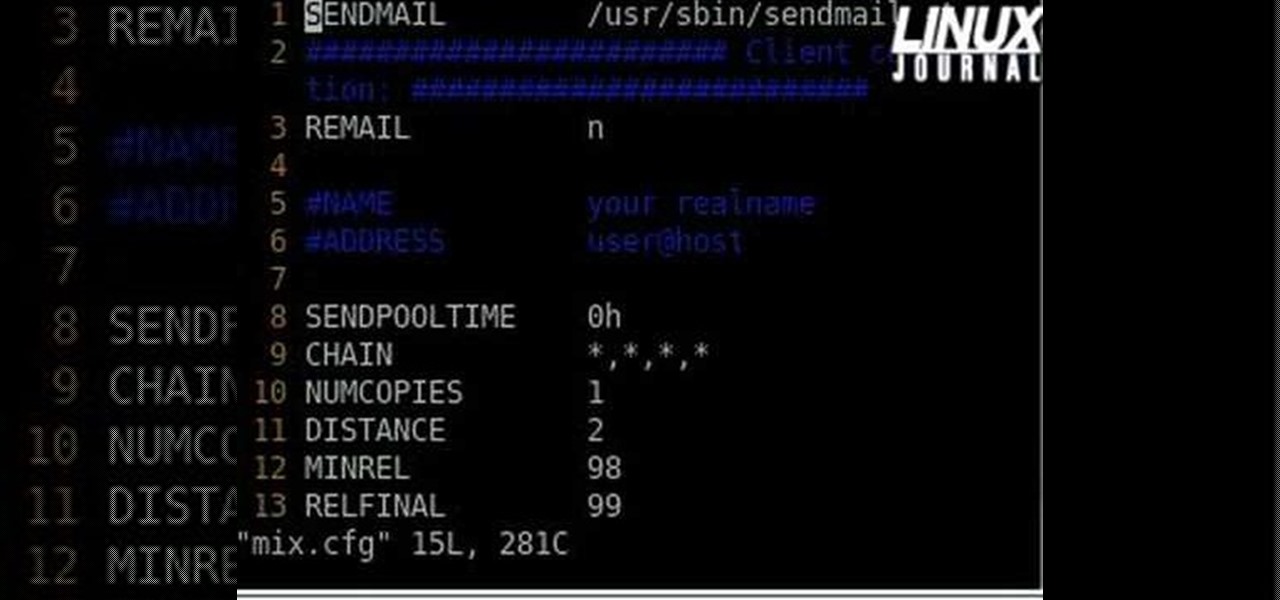
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.

If you're new to the Mac OS X operating system, one of the first things you might like to do is set up an email client. In this how-to, Gary Rosenzweig looks at how to set up the Apple Mail application to receive and send email from a standard ISP email account.
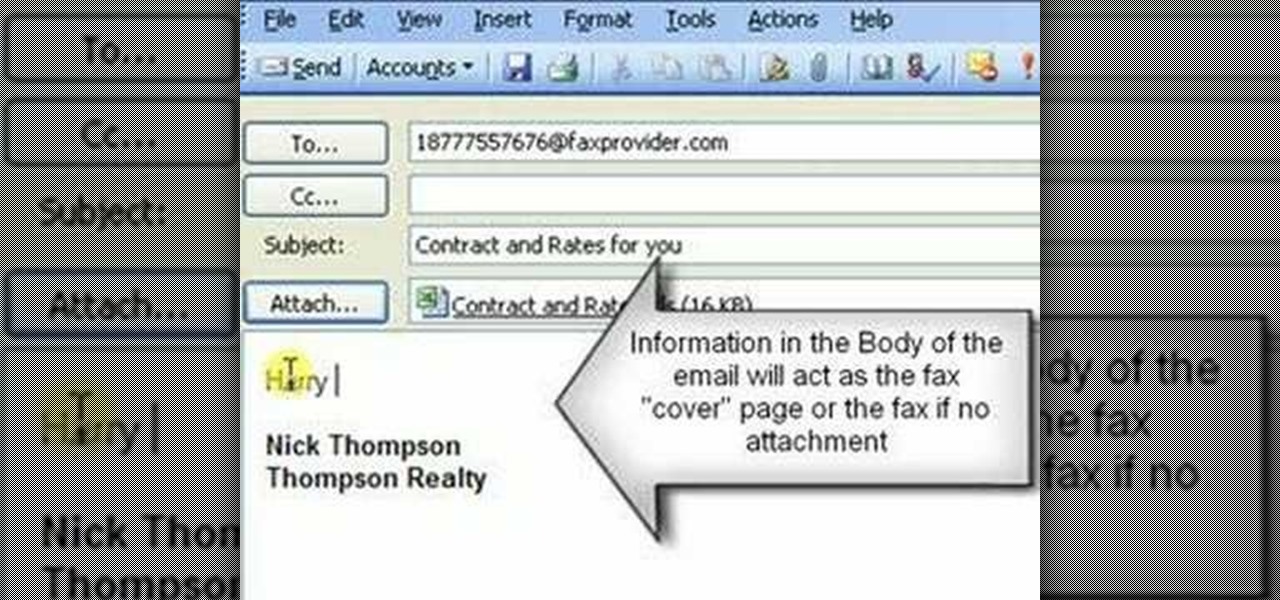
Check out this video tutorial on how to send a fax with email using Internet Fax. You'll need an Internet fax provider, and a phone number, so don't think it's easy as one, two, three.

If you're putting your email address online on your own website, or sites like facebook or myspace, you may want to be a bit clever about it. Check out this tutorial and see how to protect your email address from spam.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.
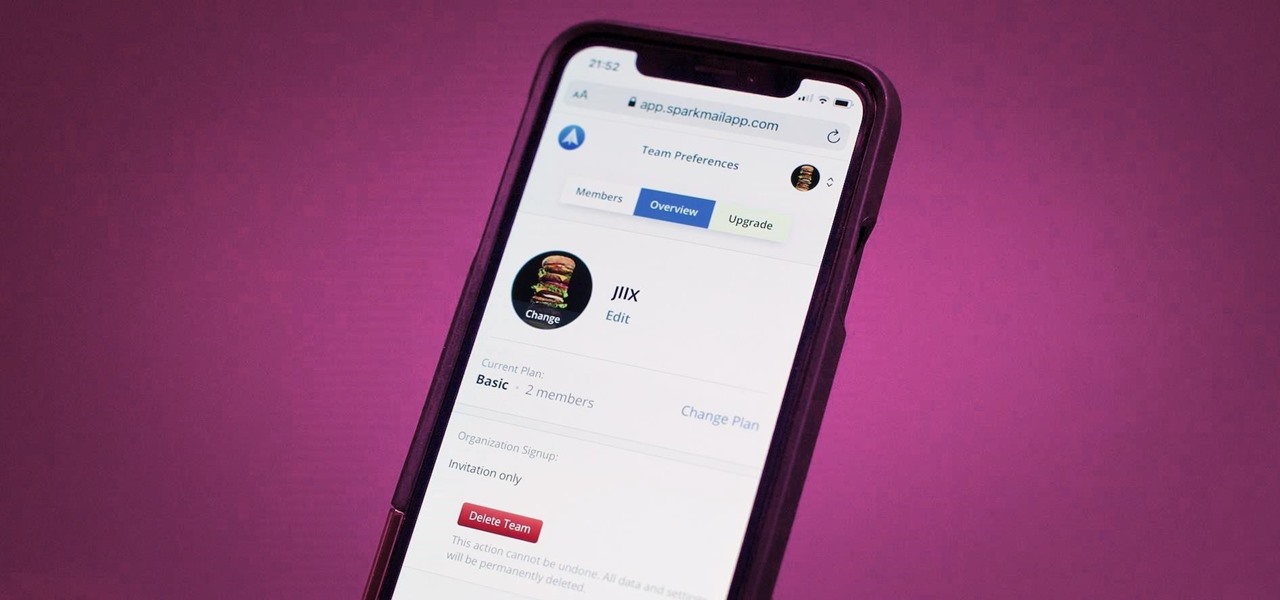
Last year, Readdle released a major update to their popular intelligent email client Spark, which brought a number of new features and improvements, including the ability for team members to collaborate on emails. You can draft new emails and privately discuss existing ones with your team, invite team members into email threads, and create and share links to specific emails.

Shopping wasn't always this easy. Now, in a matter of minutes, you can order your groceries for the week, send your cracked phone in for repairs, get your holiday shopping done, and have everything delivered to your front door in just a few days — without ever having to leave your home. Online shopping is convenient, comfortable, and a blessing ... right? Well, it can also be a headache.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.
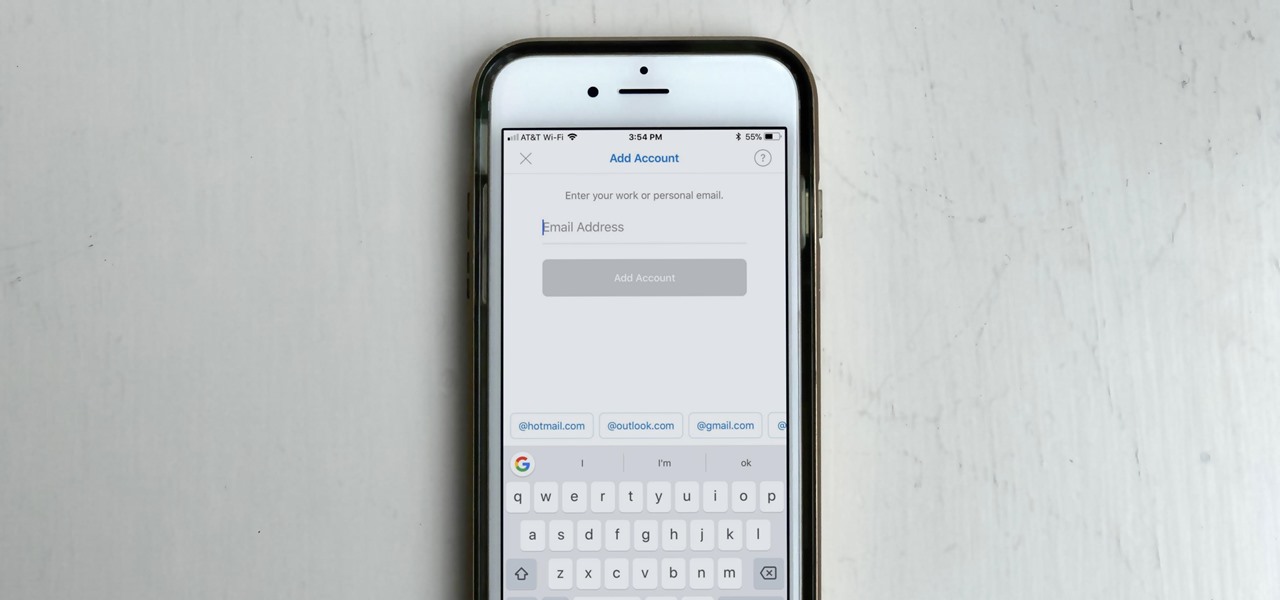
If you work with multiple email addresses, you need an app that can organize and declutter your day-to-day messages. Outlook is a great choice, but if you only have one account attached, it somewhat defeats the purpose. Lucky for you, adding additional email accounts is both quick and simple.
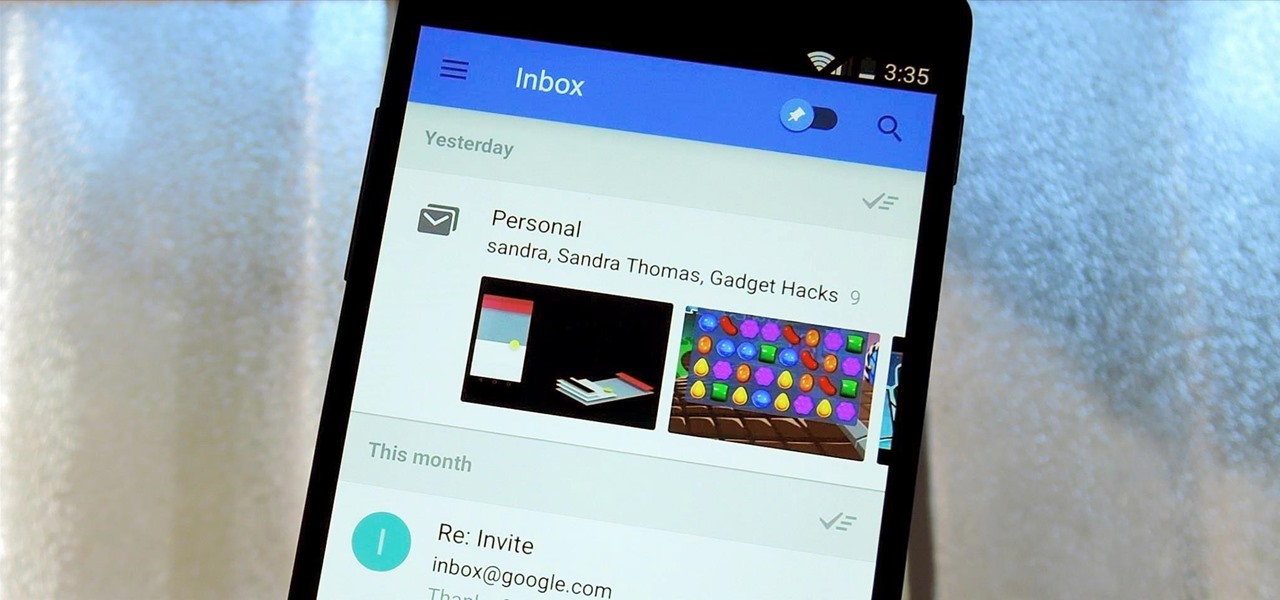
Google's new Inbox by Gmail service wants to fundamentally change the way you handle email, so a bit of a learning curve is to be expected when you're first using the utility. As of right now, the service is invite-only, but if you were lucky enough to get in on the ground floor, you're probably wondering, "How the heck do I use this thing?"
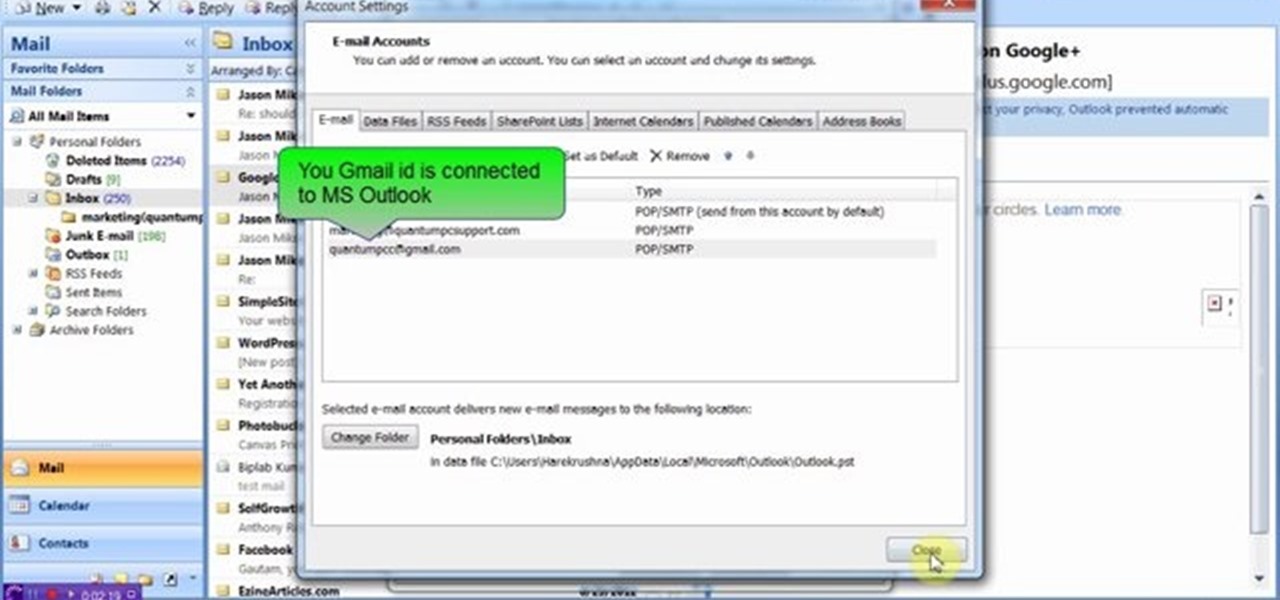
This video will show you how to connect ms outlook with Gmail to access and backup all email in outlook express. Google mail will be connected to MS outlook and copy of your each email in Google mail will be send to MS outlook. This way outlook will be a backup of your each Gmail. You could open your all emails from outlook offline. Watch the video and employ the technique in your PC.

This video will provide an idea how to block an email address in Yahoo and Gmail. This video will show in two steps. Watch the video and follow all the steps to block email ids in Yahoo and Gmail account.
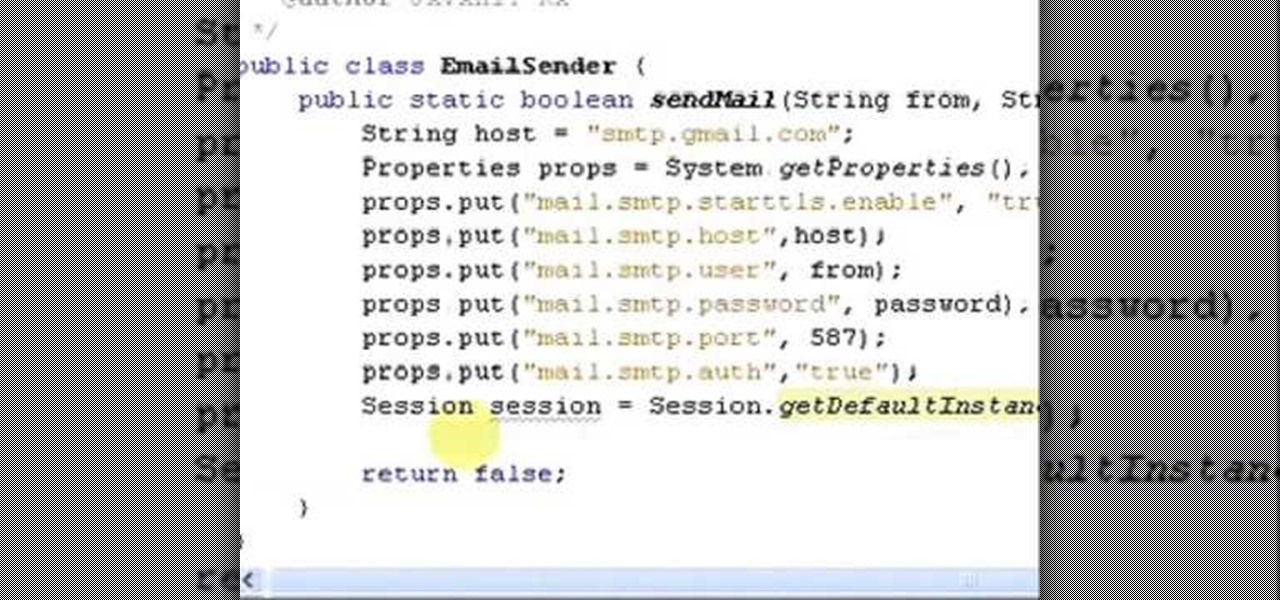
It uses JavaMail API, NetBeans IDE 7.0.1 First download the JavaMail API as shown in beginning of the video then follow the video to send email dynamically from your Gmail account. No need to open your inbox.

I know it's a very first-world problem, but I really can't stand it. Email was invented to speed up communications between people across the world, even just across the office, yet when I'm on my super awesome iPhone running iOS 7, I have to go back and forth between my gallery and my email to send more than five photos at one time.

Send an email prematurely? Forgot to attach a file? Accidentally addressed it to the wrong person? It happens to the best of us. But what can you do to get it back? Hack into the other person's email account and delete the email before they get a chance to see it? Unless you're a hacker extraordinaire, that option is unlikely. So, what can you do? If the email has already been sent, you're probably out of luck. Even if they didn't read it yet, your chances of retrieving it are slim. But some ...
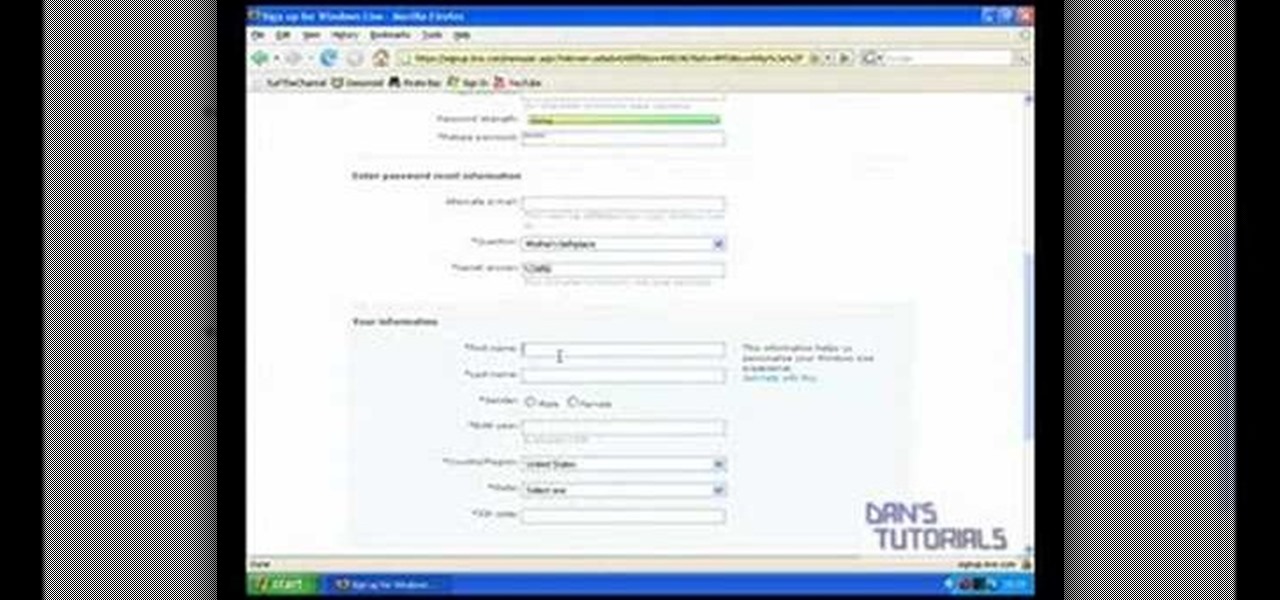
This tutorial shows how to create an email account in Windows Live. Use Google search to find the Windows Live Hotmail page. When you get to that page, click on the button that says, "Get it Free". On the next page, you can choose your email address, ending with either @live.com or @hotmail.com. If the email address is already in use, pick something else or add some numbers. Next, choose a password. There is a bar that shows how strong your password is. You can set a security question that ca...

1. Open the web browser and type www.facebook.com and press enter. 2. In order to be a member you will have to first sign up as a facebook member.
In this video, we learn how to delete an SMS or email message on an iPhone. Not only is this quick and easy, it can be done for multiple messages that you don't want to keep in your inbox. First, turn your iPhone on and go to your inbox (email or SMS). Next, slide your finger left to right on the message you don't want to keep and then click on the red "delete" button. This will then delete your message! Click anywhere other than the red delete button and this will cancel out the deletion of ...
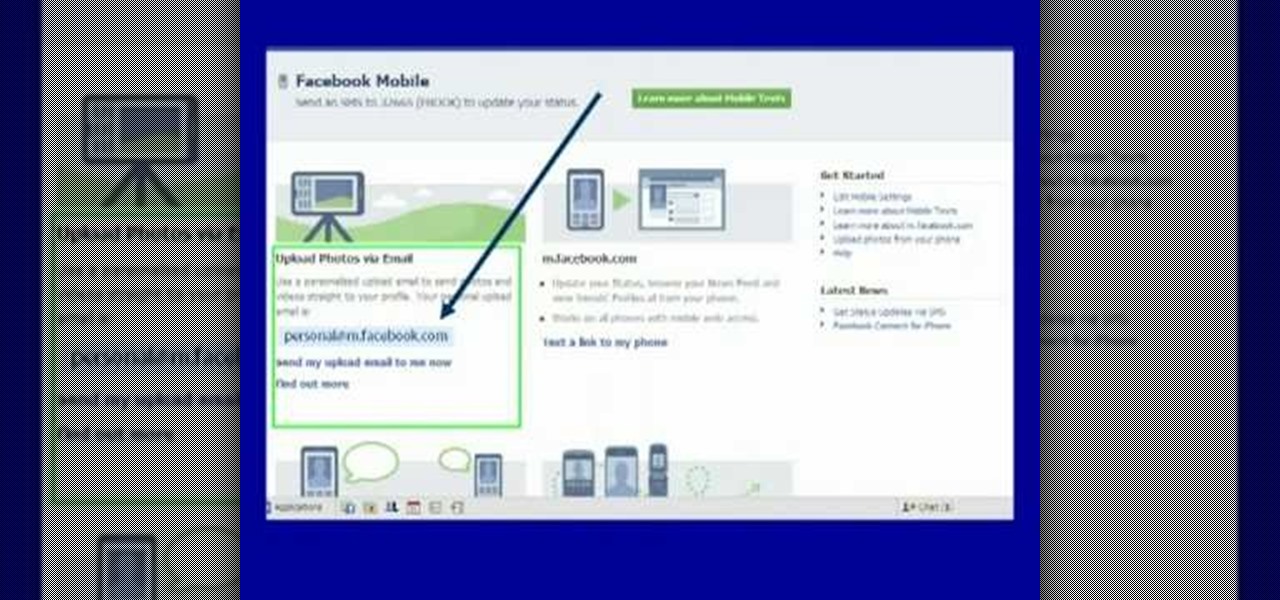
Moniquewade will show you how to upload photos and videos to Facebook by using email. The user has seven steps for you to follow in order to upload photos and videos to Facebook using email services very fast and easy. The first step starts out by telling you to go to Facebook.com. By following each of the seven steps that are provided, you should be able to send different types of photos and videos to your Facebook account just by using email.

There are many tips and tricks on the best way to use your Gmail. In order to use the tips provided you will need to have the newest version of Firefox or Google Chrome for them to work. There are three tips that can help you maximize your Gmail funtionalities and help you save time.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

In order to increase the security and harden the integrity of an email account and its content, you'll want to use PGP on your Windows, macOS, or Linux computer. This is usually the first thing security analysts do to protect communications with encryption, and everyone else should consider it too, especially since there's an easy way to incorporate PGP that anyone can follow.
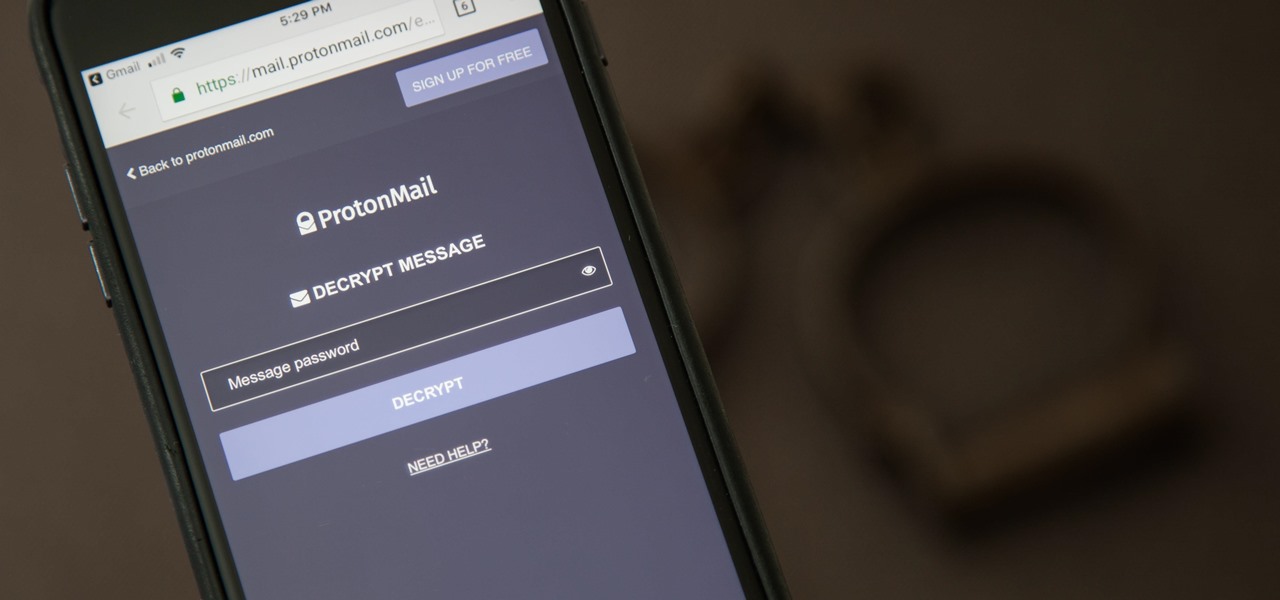
It can be hard to get all of your friends, family, coworkers, and acquaintances to jump on board with the more-secure email system ProtonMail, but that doesn't mean you can't still send them encrypted emails. Best of all, they won't even have to install any other apps or extensions to read or reply to the messages.

Faraday Future's all-electric super sports car concept attracted a lot of attention at CES earlier this year, but now it is struggling to replace key driverless engineers and program directors who left the company amid its recent financial troubles.
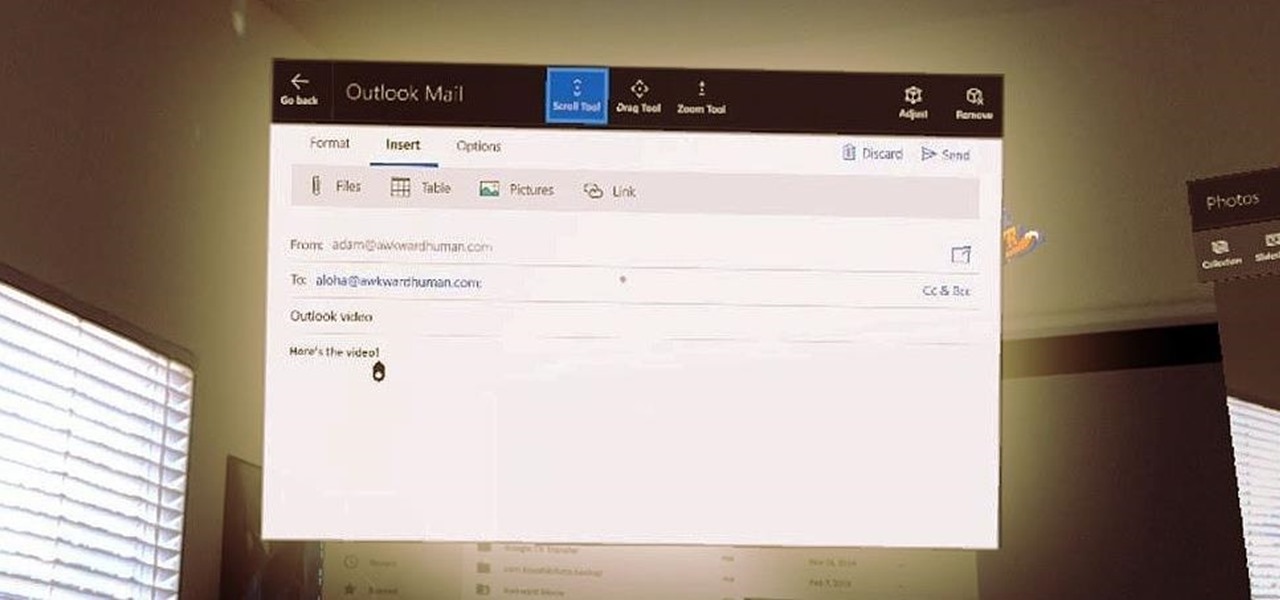
One of the more surprising omissions from the HoloLens' original app selection was email. You could write a word document or make a spreadsheet but only email through the browser. While not a major encumbrance, Microsoft's addition of Outlook makes the whole office experience feel complete.
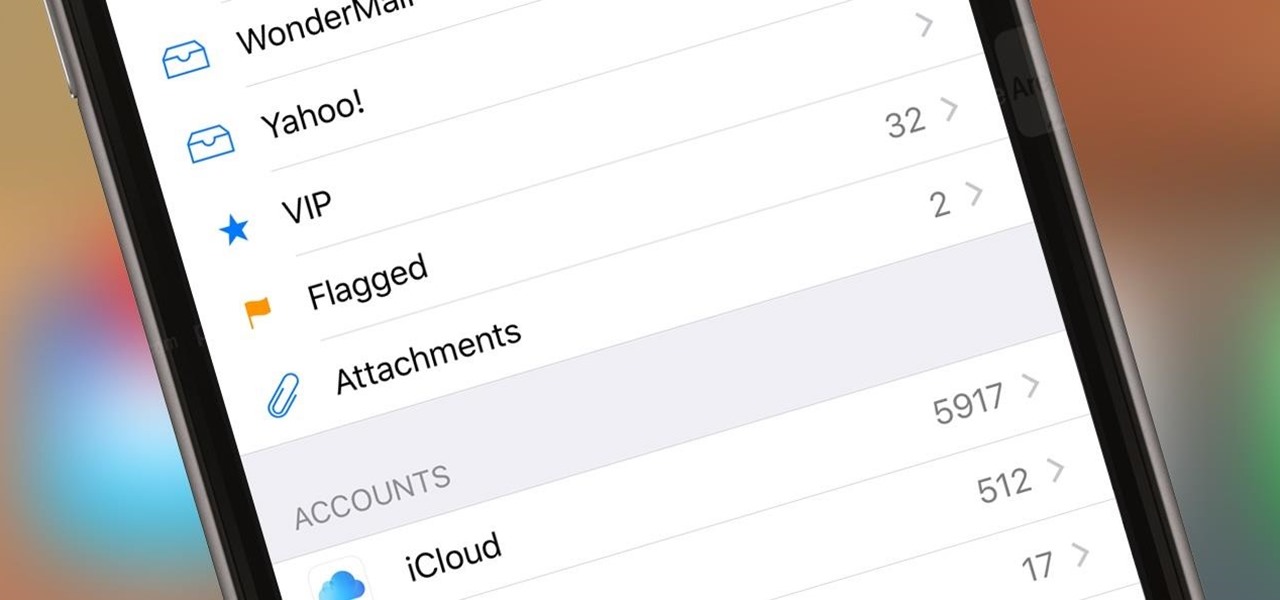
If you get a ton of emails each day, your mailbox probably has thousands of unread messages, and that annoying badge icon will keep reminding you of it. Fortunately, iOS comes with some tools to help you bring some sense of order to that chaotic mailbox of yours.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.
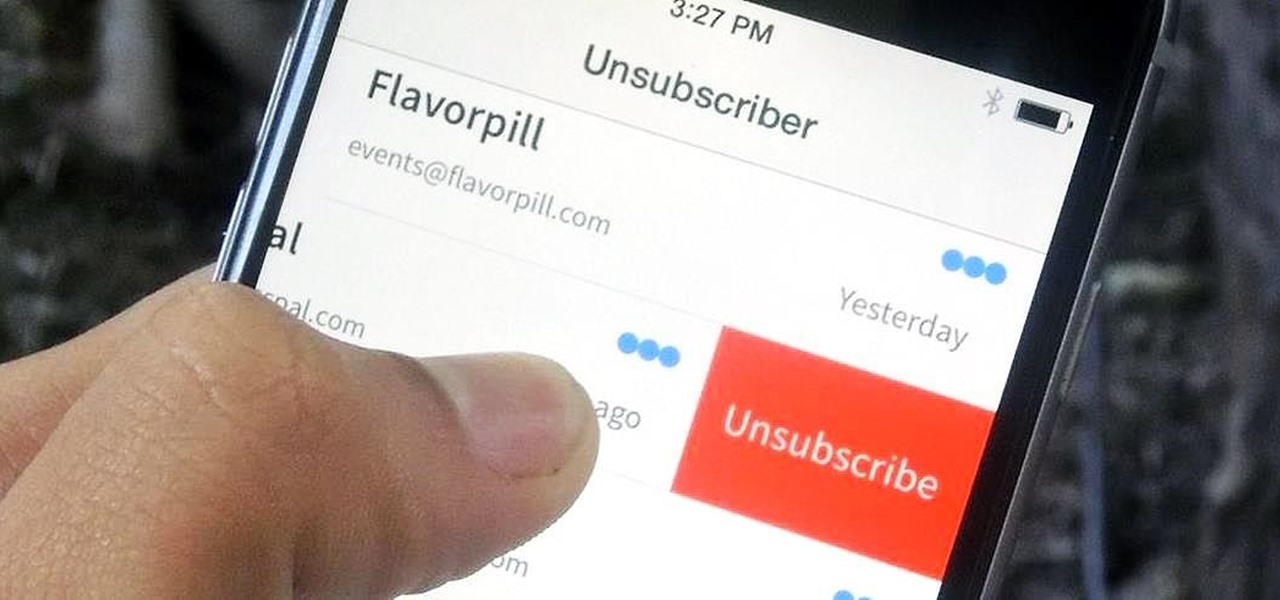
You've undoubtedly used your email address to sign up for a chance to win something online or to purchase something on sale. Often, these offers are too enticing to pass up, and you reason that you'll live with the consequences of handing out your information for the chance at making out big.
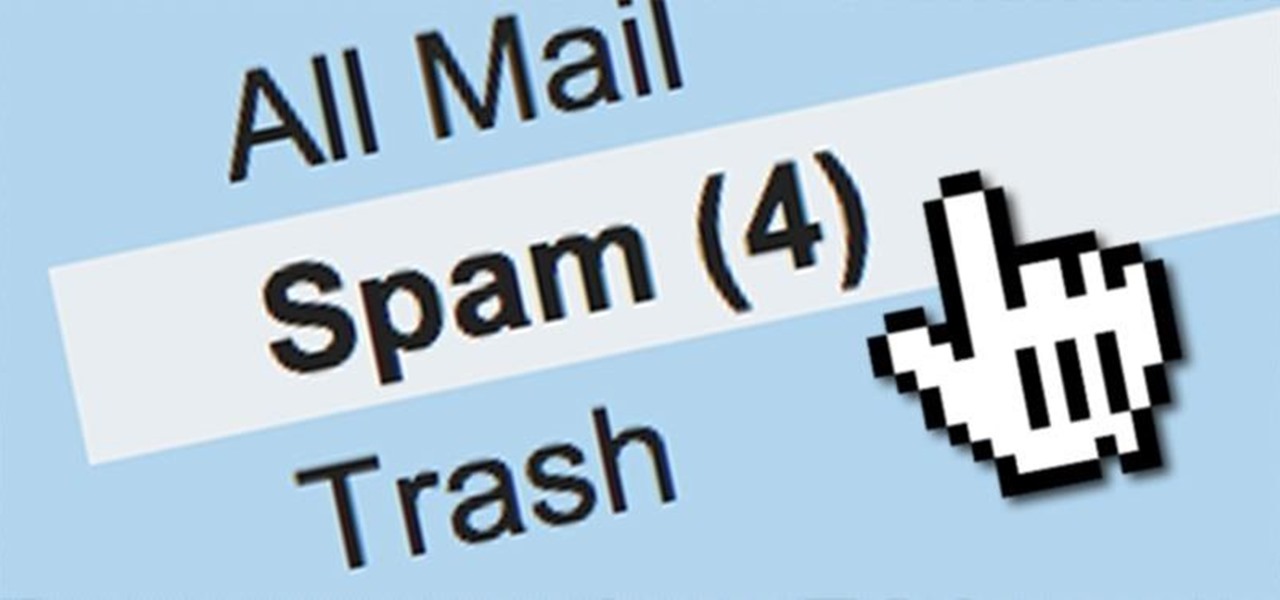
I rarely receive spam mail, but every now and then I’ll get an email from Cat Fancy Magazine. I’ve never read an issue of Cat Fancy Magazine or been to their website. Actually, I’m allergic to cats. So how did they manage to get my information?