As with most OEMs, HTC would like you to think that you can do virtually anything with your new HTC One M8, but as a softModder, you know that isn't true. To actually unleash the full potential of that device, you need access to the whole system, not just the parts that HTC deems okay for you to mess with.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.
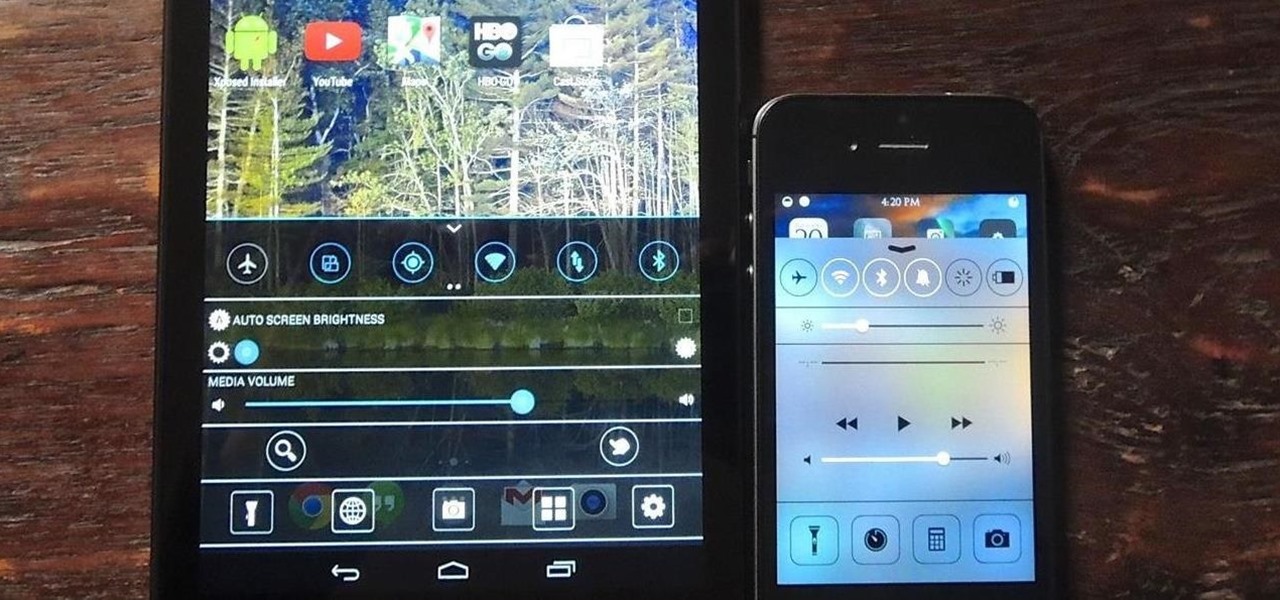
There are two types of tablet users in the world—those who like their quick settings up top, and those who want them on the bottom. I fall into the latter category, and there are a couple of reasons for it.

In order to unleash the full potential of your Samsung Galaxy Note 3, you've got to root it. These days, it's easier than ever, and can be done by just plugging your device into a Windows computer and pressing one button. It's so easy, your grandmother could do it, so what's stopping you?

Yesterday, the Free Software Foundation published an article written by Paul Kocialkowski. A software developer for the the Android fork system Replicant, Paul stated that his organization discovered, and later patched, a "backdoor" vulnerability that existed in older Samsung Galaxy devices, including our beloved Galaxy S3s. Only problem is, it's kind of bullshit—but we'll get to that later.

Slide to left, slide to the right, one hop this time. Okay, so maybe those are some of the dance instructions for the "Cha Cha Slide", but sliding and swiping on your Samsung Galaxy S3 can become so much more than just a simple gesture.

With the emergence of rumors that Amazon, Google, and Samsung are all making their foray into the gaming console market, it's a possibility that our Android-powered mobile devices might become tools that play a central role.

The Academy Awards, commonly referred to as The Oscars, are airing this weekend. If you're a movie buff or just want to watch the dimes walking on the red carpet, The Oscars is not to be missed.

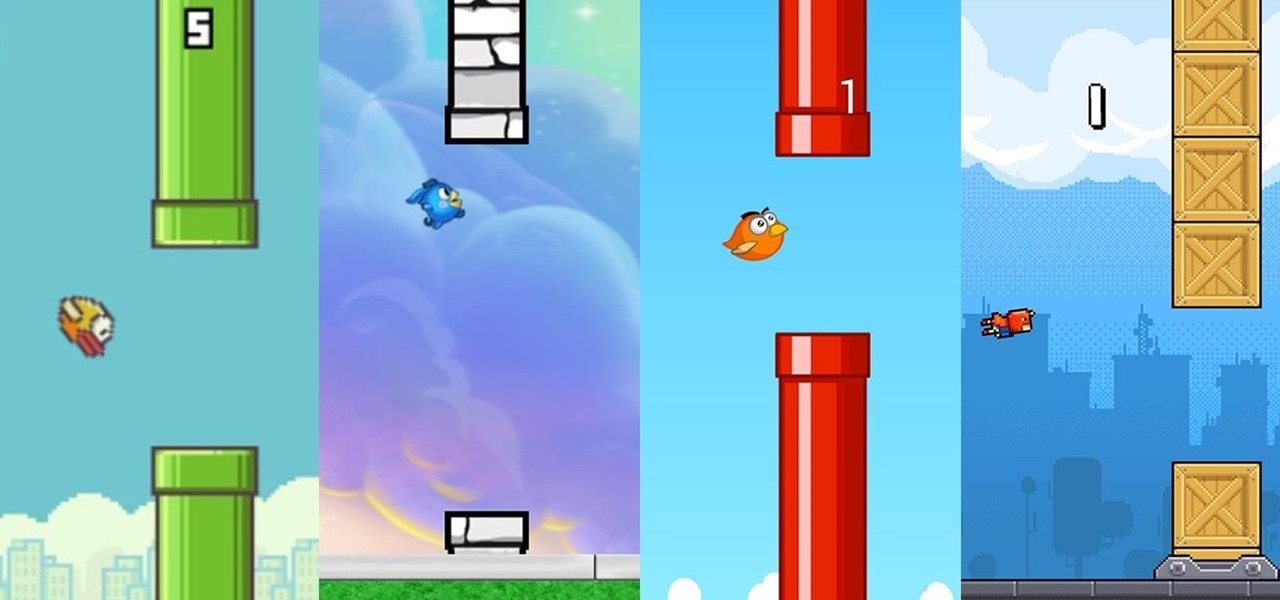
In a much-hated move, Flappy Bird developer Dong Nguyen removed his incredibly popular, yet extremely frustrating app from both Google Play and the iOS App Store. The jury is still out on the exact reason behind the move, though we can rule out pressure from Nintendo, but one thing is for sure—Flappy Bird has fallen for good.

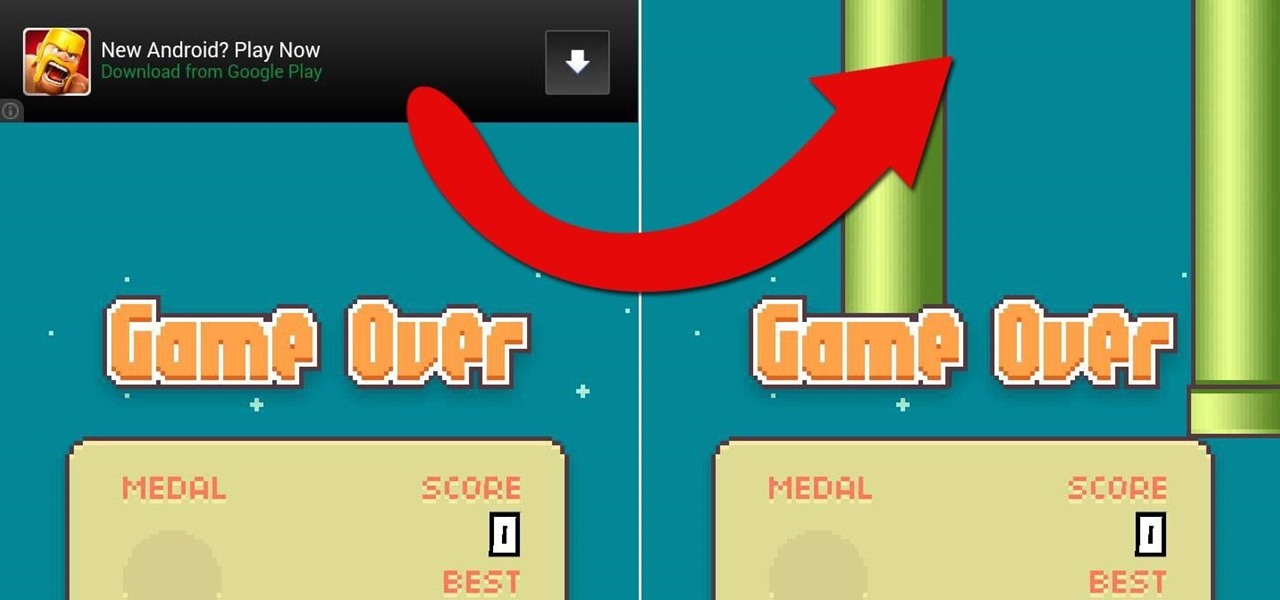
One thing we can probably all agree on is that ads suck. In particular, ad-supported mobile apps are both a gift and a curse. Most are free, but supplement that non-existent price tag with non-stop banner or video ads. Sometimes, those ads can ruin the entire app, especially if it's a game that requires your undivided attention.

Keeping unwanted clowns off on my Samsung Galaxy S3 is priority number one. I've shown you how to snag a picture of people opening your apps and how to lock your screen for whenever you hand off your phone, allowing them to access only the page you left open.

We're only years away from a complete Robot Revolution and Google Inc. will surely be leading the charge.

If you've been using Google's hidden App Ops to lock down and prevent some of your Android applications from exposing your privacy, then think twice before updating to the new Android 4.4.2 software.

Twitter's video-sharing app, Vine, had some very stiff competition once Instagram added video sharing to its repertoire. Recent figures show Instagram at 130 million followers compared to Vine's 40 million. Many think that Vine is on its way out, but on the contrary, I think it's here to stay.

The sound I get when receiving a new text message is the camel from that Geico commercial yelling "Hump Day!" Sure, I could find a less obnoxious notification sound, but it makes me laugh every time, and that's important.

Ubuntu isn't just a cool sounding name, but pegs itself as the world's favorite free operating system. It gained its popularity for being lightweight, fast, and visually appealing, and now that great look and speed can be placed right on the lock screen of your Samsung Galaxy S3.

I remember how fast my Nexus 7 was the first time I turned it on. Boy, do I miss it. Now my tablet is pretty buggy and crashes happen frequently, and I'm sure that goes for many of your Nexus 7s as well. Even if you upgrade to the new Nexus 7 next week, it will eventually develop similar issues.

Your HTC EVO 4G LTE has been lying to you. It will tell you when you're connected to a 4G network, but it will say 3G even if you're connected on 1X, which is a 2G CDMA network!

Nearly two years ago, Peter Chou, CEO of HTC, confirmed that the company would no longer be locking bootloaders. Whether or not they've actually lived up to this claim is debatable. Any phone bought from a wireless carrier comes locked. Only the new HTC One Developer Edition ships with an unlocked bootloader, and it does not have any carrier add-on software installed.

Of the hundreds of uses for our devices, the one that I cherish most is the ability to kill time just about whenever and wherever I need to. Whether it's reading news, checking social media, or watching videos, we have a ton of ways to pass the time in that two-hour DMV line or dentist's waiting room.

Skype is a great way to stay in contact with friends and family over the internet, and people tend to share a lot in their chats, so why not try and find a way to hack it! Once a Skype account is hacked, you can view all conversations within the last three months, see how long each video call was, and even access files that were shared through chat.

Clearing the cache on your computer is (usually) a quick and easy way to help speed it up. Deleting those temporary files frees up space, helping you computer run smoother, especially if you have not cleared the cache for a extended period. However, finding the different caches in Windows 8 is a little trickier than in previous Windows systems.

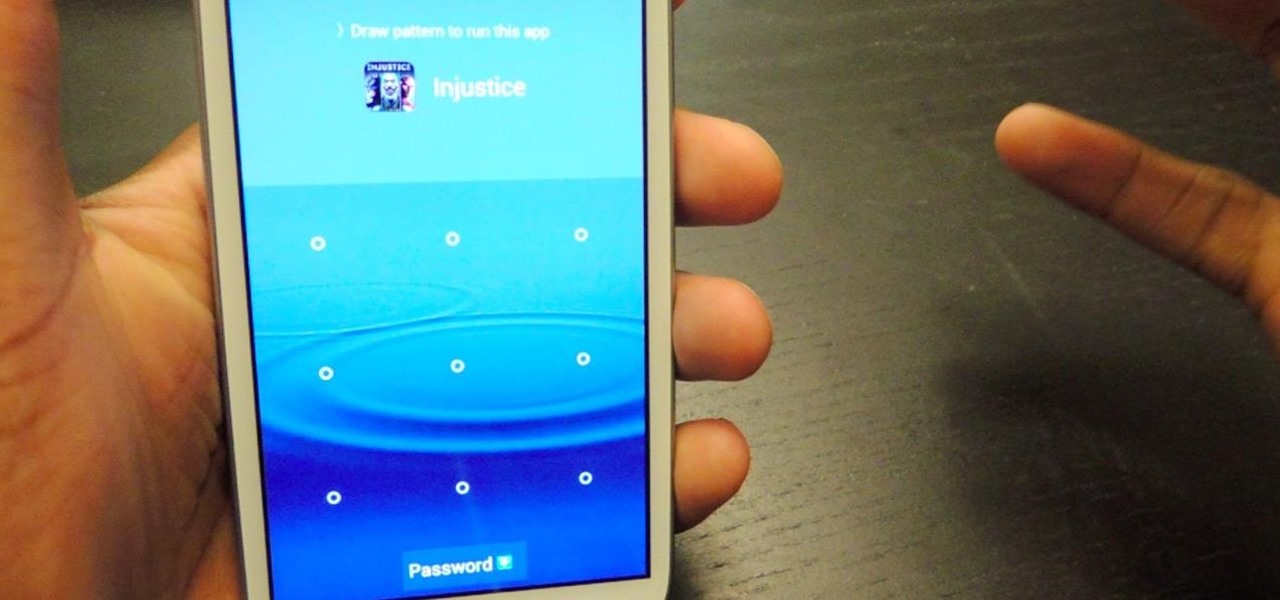
Back in 2010, iOS developer Daniel Amitay developed a camera security app for iPhones that used an unlock screen almost identical to that of the iPhone.

Hello and welcome to my post. I would like to share a few things I have picked up along the way - while feeding my two dwarf rabbits. In this tutorial I would like to answer the question - How to choose the best food for your rabbit?

Redbox recently announced a partnership with Verizon to bring a new streaming video service called Redbox Instant to an already crowded table. No prices have been released yet for the service, but with Netflix, Hulu, Amazon, YouTube, iTunes, and many others all attempting to get a hold of your dollars, what are currently your best options? Subscriptions Services

OSAGYEFO DR. KWAME NKRUMAH (1909-72) Founder and Father of the Nation Osagyefo Dr. Kwame Nkrumah, the first Prime Minister and President of Ghana, stands out not only among the Big Six but also among the greatest statesmen of history. It was he who canalized the discontent of the people of the Gold Coast Colony into the highly organized movement of protest against British rule, and within a relatively short period won political independence for Ghana on March 6, 1957. With Ghana independent, ...

You can gain lots of victories, but absolutely no glory from using these methods of cheating to win at arm wrestling.

What if I told you that you could read minds? You'd most likely think I was crazy, and you'd be right. But what I really meant is that you could make people think that you could read minds, something that's not the least bit crazy.

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.

The so-called 'photo button trick' can help you get the exposure right, when you film in low light situations / total darkness. The tutorial was made for the Canon HV20 but works for the HG10 as well (they share menu / software).

Belly dancing is a great way to improve fitness, gain self-confidence and enjoy music. Find out about belly-dancing costumes, such as making bras, skirts and jewelry, and learn some simple belly-dancing exercises with this free video series from a belly-dancing instructor.

Despite the fact that over 600,000 Snap Lens filters have been created since Lens Studio debuted in 2017, and Facebook is reporting that more than a billion users have interacted with its Spark AR filters across Facebook properties, social augmented reality filters get a bad rap in the AR industry.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

The headphone jack is becoming outdated technology in smartphones — that's what many manufacturers would have you believe. For the convenience of the audiophiles out there, we recently published our list of all phones that have removed the 3.5 mm jack. But what did each company gain inside their flagship phones by removing this supposedly antiquated port?

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.