
News: Resolution Games Scores $7.5M in Funding Round Backed by Google, Unity Founder, & Others
Fresh off shipping an augmented reality game for Magic Leap, Resolution Games has farmed another $7.5 million in funding through a Series B round.


Fresh off shipping an augmented reality game for Magic Leap, Resolution Games has farmed another $7.5 million in funding through a Series B round.

At its annual MAX event kicking off on Monday in Los Angeles, Adobe gave the audience a new preview of its forthcoming Project Aero augmented reality authoring tool during the keynote presentation.

Earlier this year, Samsung released the Galaxy J3 and J7 to select markets. These two devices are the latest in the J series, Samsung's super-budget series that tries to rewrite what it means to be a budget phone. Now, starting September 14th, you will be able to get them GSM unlocked.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

As it prepares to ship its first product by the end of the summer, Magic Leap has managed to impress yet another high-profile investor in telecommunications giant AT&T.

When you receive a photo or video from a contact in WhatsApp, after you load it, it's automatically saved to your phone's local storage. That means all received content from WhatsApp is visible to anyone who gains access to your default photo gallery. Luckily, there's a new feature available for the Android version of the app that can prevent this from happening.

Last month was a whirlwind for the augmented reality industry, with the Augmented World Expo, Apple's Worldwide Developers Conference, and an exciting Magic Leap Twitch livestream all wrapping up before the ides of June. Now that we've had a chance to fully digest it all, we have a real sense of where the augmented reality industry is heading.

The Power Rangers universe is massive, spanning numerous shows and movies that feature different heroes — from the original dinosaur-themed Mighty Morphin Power Rangers, to Power Rangers Samurai, and so on. To tie it all in, Nexon has soft launched Power Rangers: All Stars in select countries ahead of a worldwide release. But you can try the game out right now thanks to a simple hack.

Last week's Augmented World Expo felt like a distant memory by this Monday, as Apple unveiled ARKit 2.0 at its annual Worldwide Developers Conference. Certainly, this news would overshadow anything augmented reality this week as it nearly eclipsed AWE when early reports leaked of the toolkit's new superpowers.

Consumers are chomping at the bit for augmented reality smartglasses from Cupertino's finest, but one market analyst is saying not so fast, Apple fans. Meanwhile, automotive AR is gaining speed, with the latest milestone coming courtesy of a major investment in waveguides by Continental. And although mobile AR apps have already arrived, retailer Target is taking a different approach. So why is Target tinkering with web-based AR? Answers below...
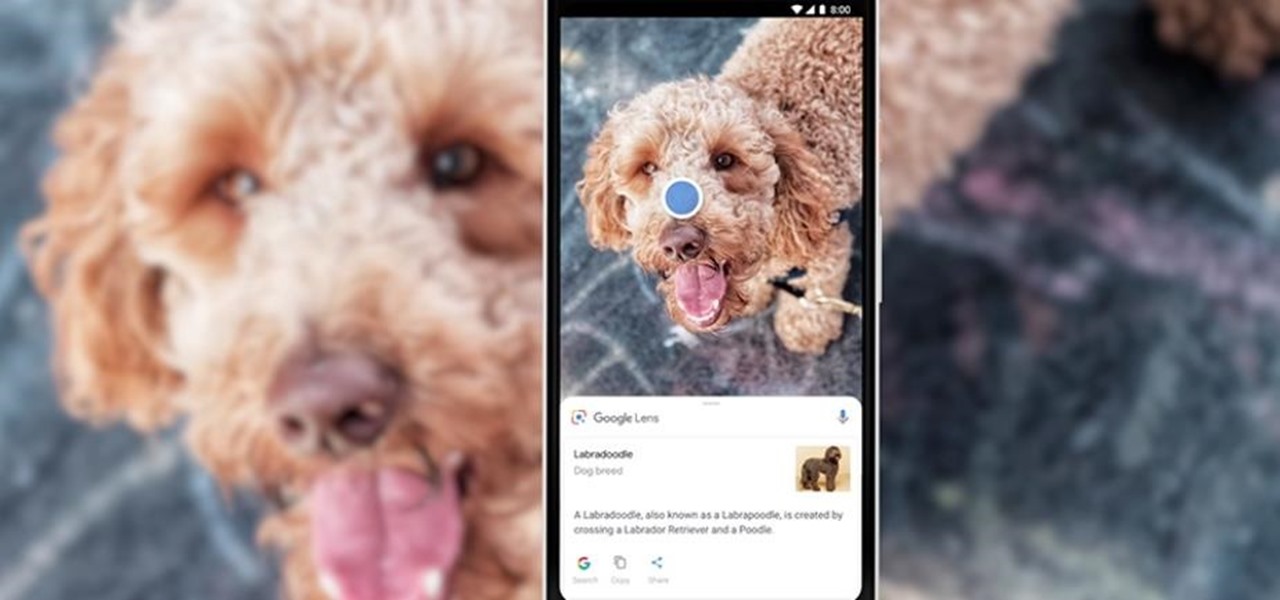
During Tuesday's keynote at the I/O developer conference, Google unveiled new capabilities for its Lens visual search engine and expanded the availability of the platform in smartphone camera apps.
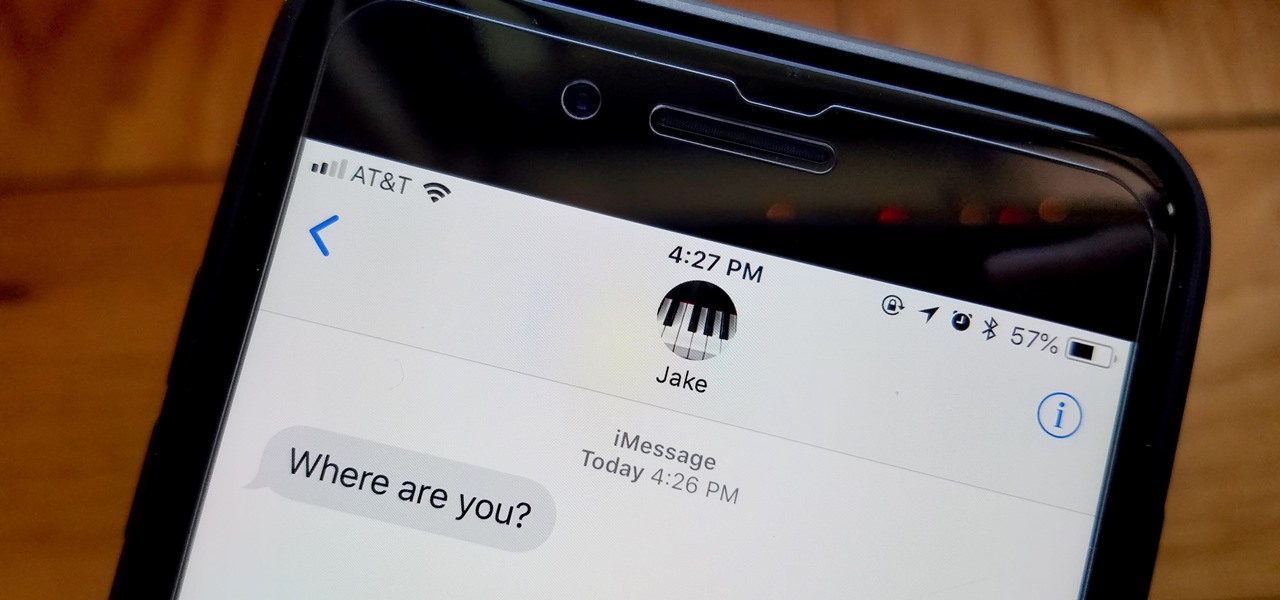
You're at the bar, but your friend can't find you. You could call them, but that wouldn't feel very 2018. Instead, let your iPhone do the talking. Right in the Messages app, you can easily send your friend your current location — all without interrupting the friends you're hanging out with.
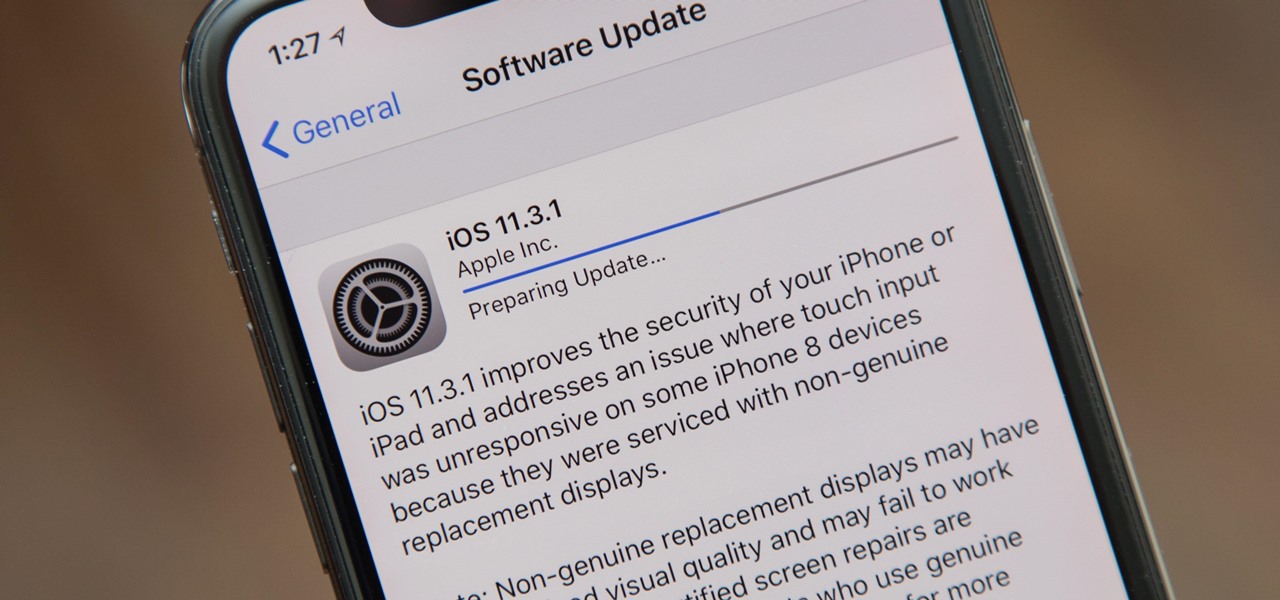
Apple released the iOS 11.3.1 update for iPhones on Tuesday, April 24, 26 days after the official release of iOS 11.3 and eight days after the iOS 11.4 beta 2 update. It is the first minor update to iOS 11.3, and the biggest thing in it is a fix that lets displays fixed by third parties work again.
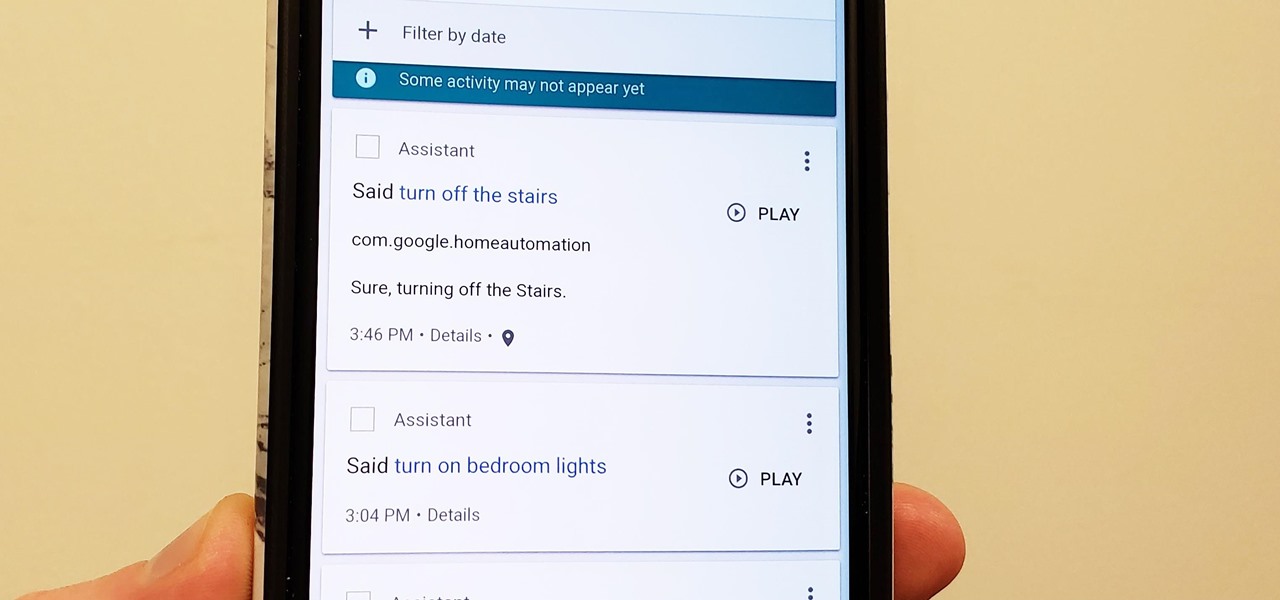
Privacy is a hot topic. In the wake of Facebook's data scandal, many want to safeguard their personal info. On the other hand, we all gain a certain amount of convenience by using services administered by huge companies like Google, Facebook, and Twitter. Google Assistant collects plenty of data, but you can easily check what is stored and delete items at will.

If bezel-less was the goal of OEMs in 2017, 2018 seems to be the year of the notch. Thanks in no small part to Apple's iPhone X, more and more smartphone manufacturers are designing their displays with this polarizing cutout. While many are frustrated with the trend, it's worth taking the time to consider what each phone gains with the unique design.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.
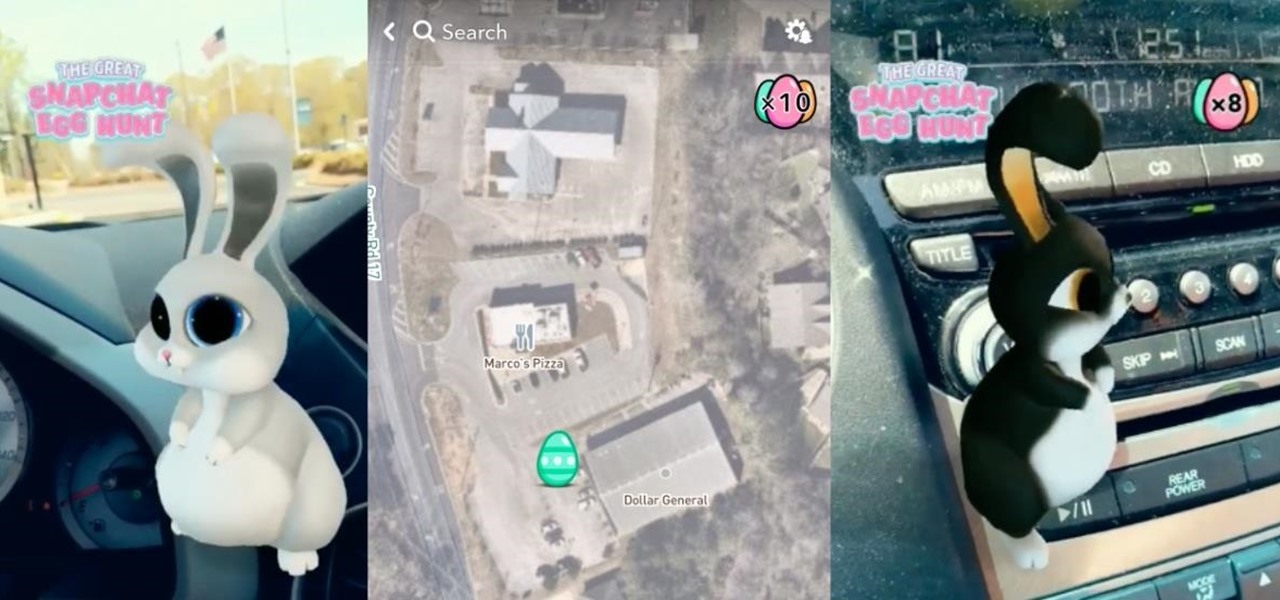
Alongside the usual collection of holiday-themed Lenses, Snapchatters received an extra-special treat from Snapchat over the weekend—a world-spanning Easter egg hunt.
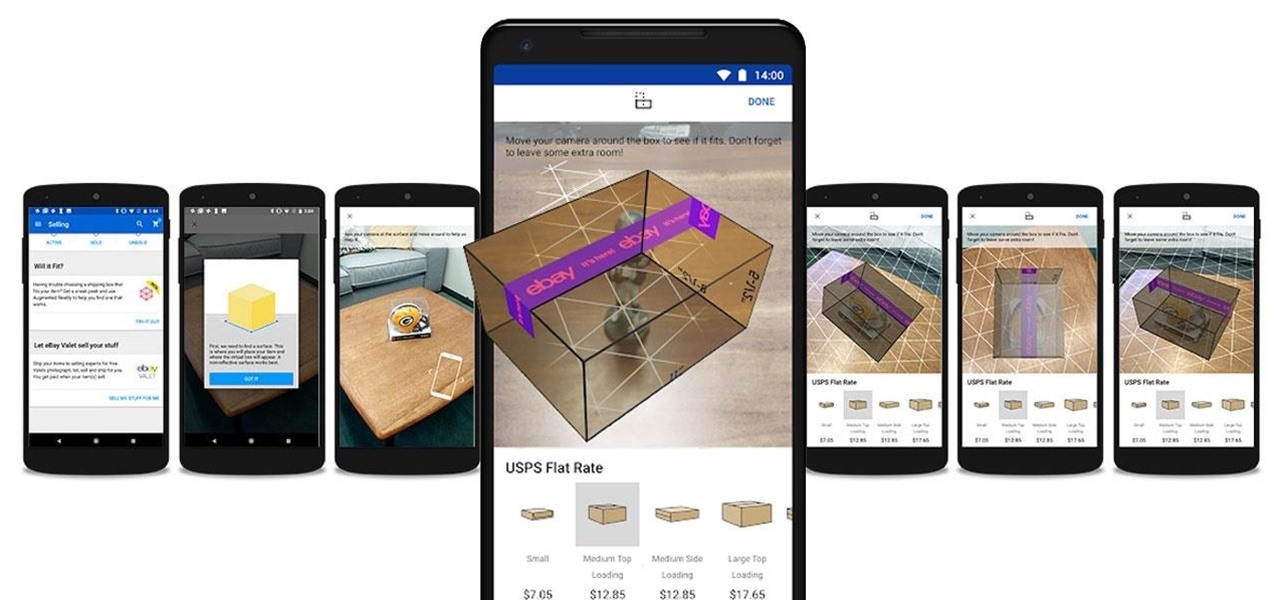
In the weeks following Google's AR toolkit launch last month, the availability of quality ARCore apps has been somewhat limited. That changed on Tuesday, as a flurry of new and updated apps arrived on the Play Store, including some AR experiences available exclusively on Android.

Not content to just be a provider of rugged smartglasses for enterprise users, DAQRI has made the jump into the AR software side of the industry with its new Worksense productivity suite.
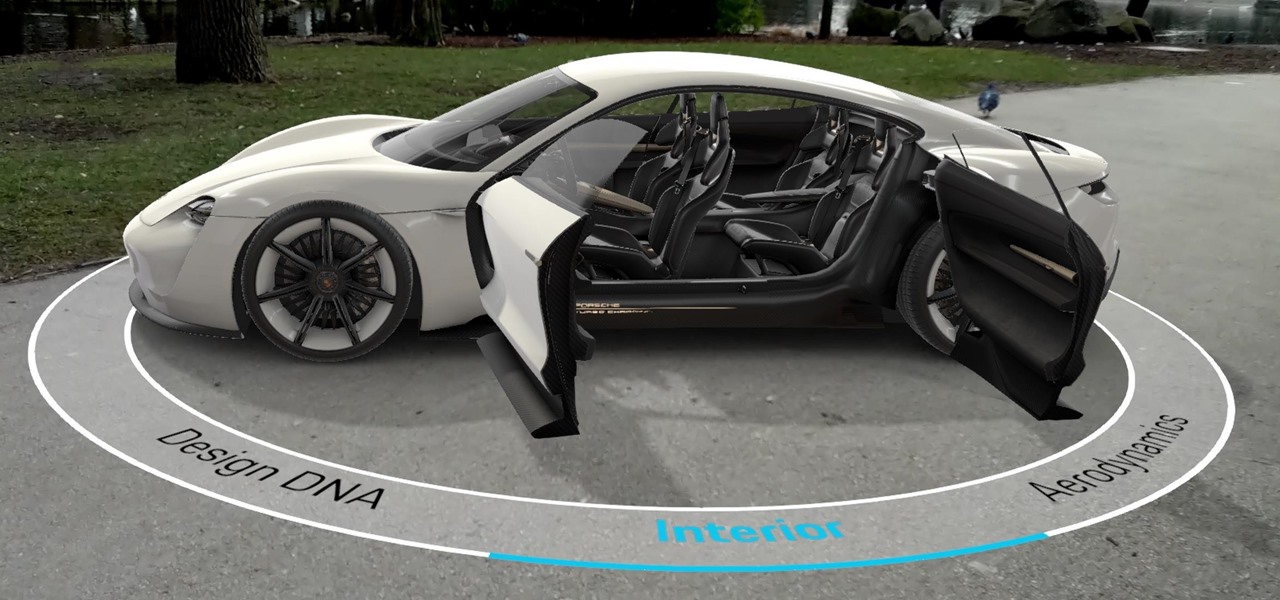
In one of the worst-kept secrets of the upcoming Mobile World Congress, Google has officially released ARCore on the Play Store for owners of the latest flagship Android smartphones.

HBO's Westworld has touched down on iOS as a mobile game, giving players the chance to manage their very own futuristic theme park set in the wild west. Unfortunately, the game is currently only available in select countries as a soft launch until its fully developed. But if you'd like to try out this game right now, there's a simple workaround to get Westworld on your iPhone.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

The latest cosmetics brand to launch its own augmented reality try-on tool is Cover Girl, which introduced its browser-based experience this week.

Super Bowl LII will bring millions of football and non-football fans together to watch the big game on the big screen. But without a cable subscription, this process can be a little daunting. Luckily, the Google Play Store and the iOS App Store offer a few ways to accomplish this — no cable contract required.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

A few months ago, we gave you a small peek at a new entrant in the race to deliver augmented reality smartglasses to the masses, and now the device is finally ready for the public. ThirdEye Gen is now accepting preorders for its X1 Smart Glasses, which will also provide users with an AR-centric app store.
When most people first become aware of Kodi (formerly known as XBMC), they hear about its ability to stream illegal content. But the real Kodi community knows that it's much more than just a haven for pirated material — it's an all-in-one media player that addresses the majority of home theater needs, particularly for those that decided to cut the cord.

Sports gaming company ePlay Digital, Inc. is looking to capitalize on the fall launch of iOS 11 and ARKit with an augmented reality fantasy sports app.

When you have an infection, a doctor prescribes antibiotics to make the bacteria that causes it disappear. Sounds like a good idea, but the disappearance of microorganisms that have inhabited humans for millennia could be driving rising numbers of serious illness and debilitating conditions.

A new study shows the Zika virus is present in saliva — but it may not be enough to make you sick. The Centers for Disease Control and Prevention notes there is "no evidence that Zika can be transmitted through saliva during deep kissing." Given the results of research published in the journal, Nature Communications," the agency may need to revise its guidance.
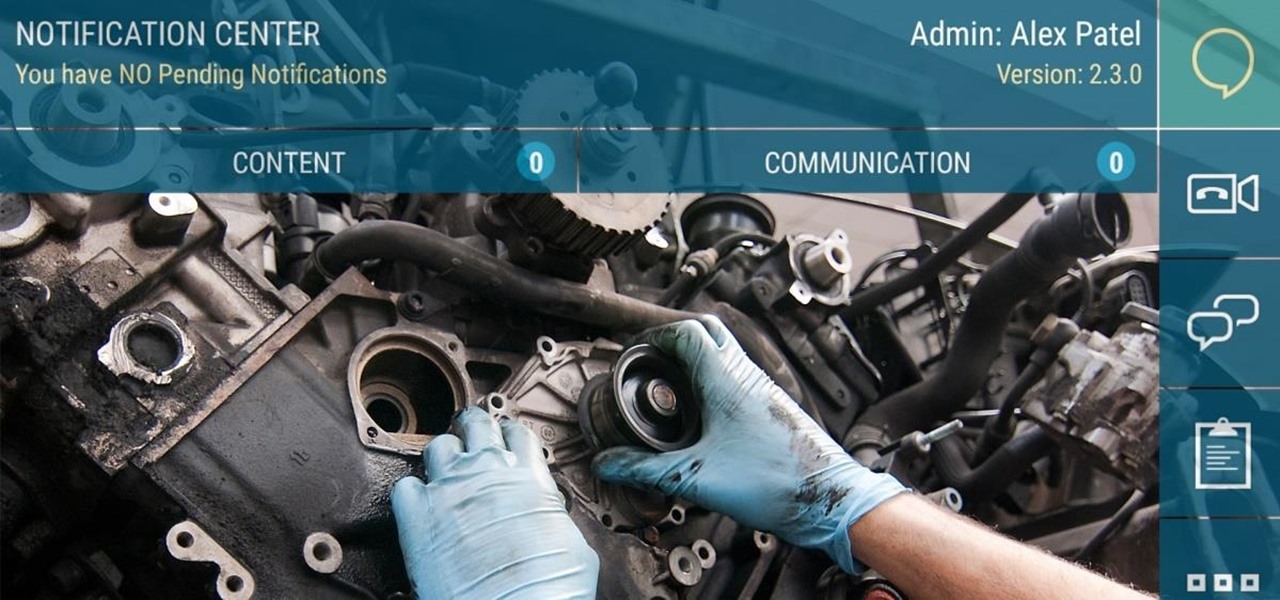
The augmented reality productivity app market for is a crowded space, so differentiation can be an advantage. Atheer is doing just that this week with their AiR Enterprise application.
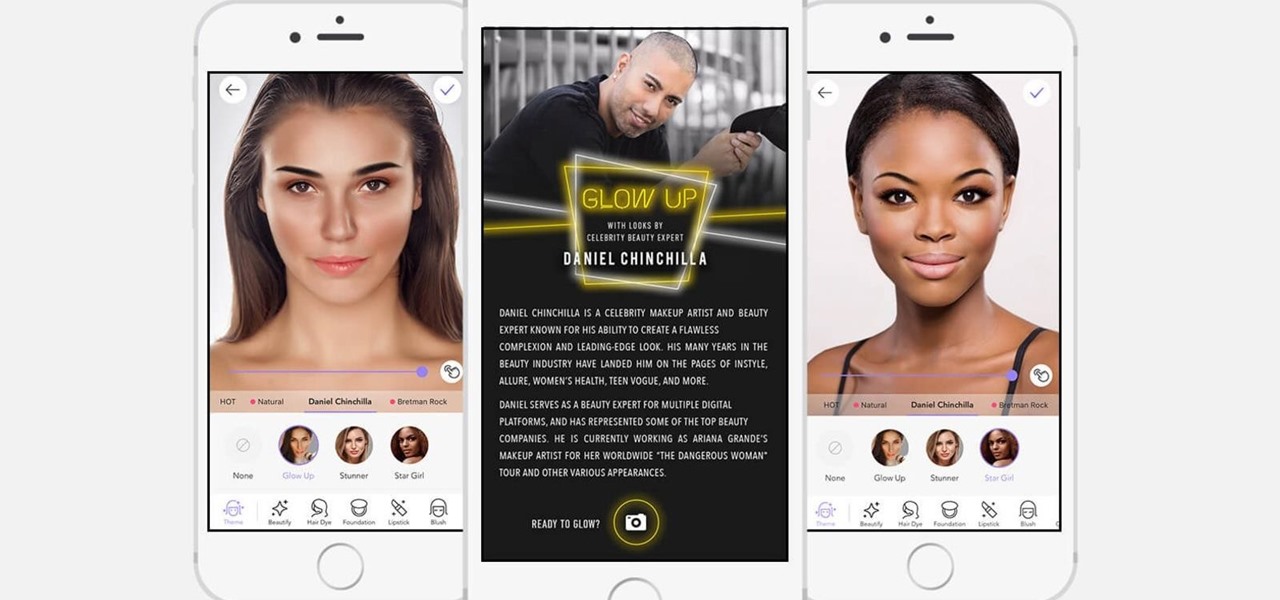
If it's not official by now, it really should be: if you're going to sell cosmetics, you need an augmented reality app. Of course, that's not all augmented reality is good for. It can be used to animate medical models and engage sports fans. Read on below…
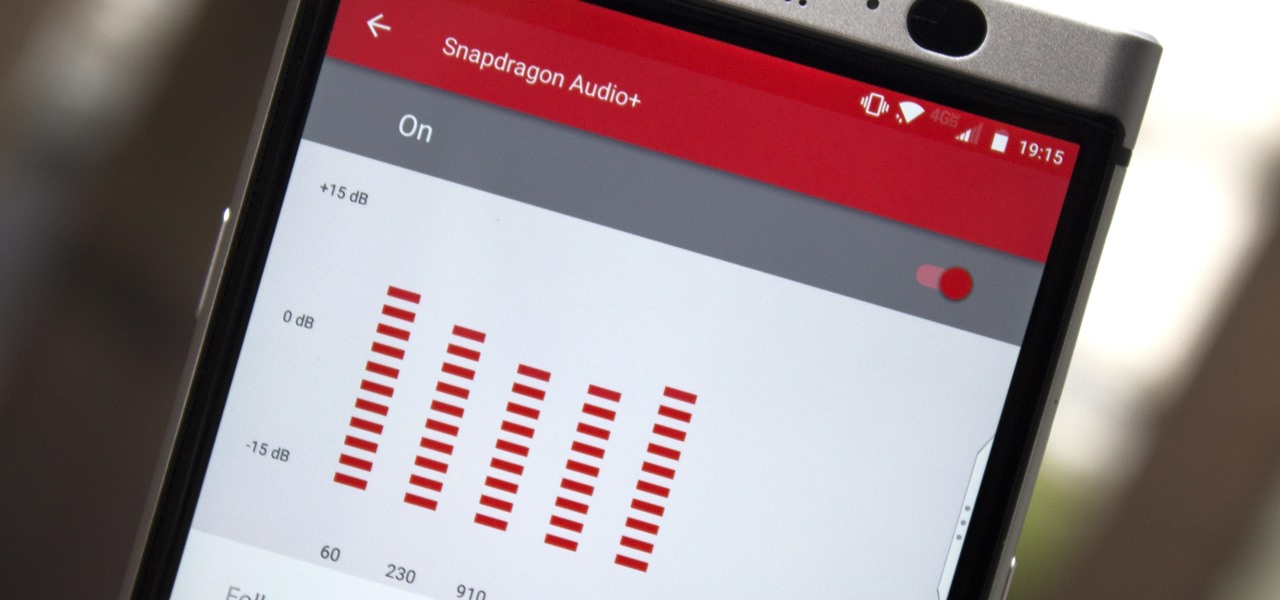
You may not know this, but the Spotify app will let you add a bit of personal touch to all the music you stream. Unlike many other music streaming services, Spotify actually has fantastic equalizer support on both iOS and Android.
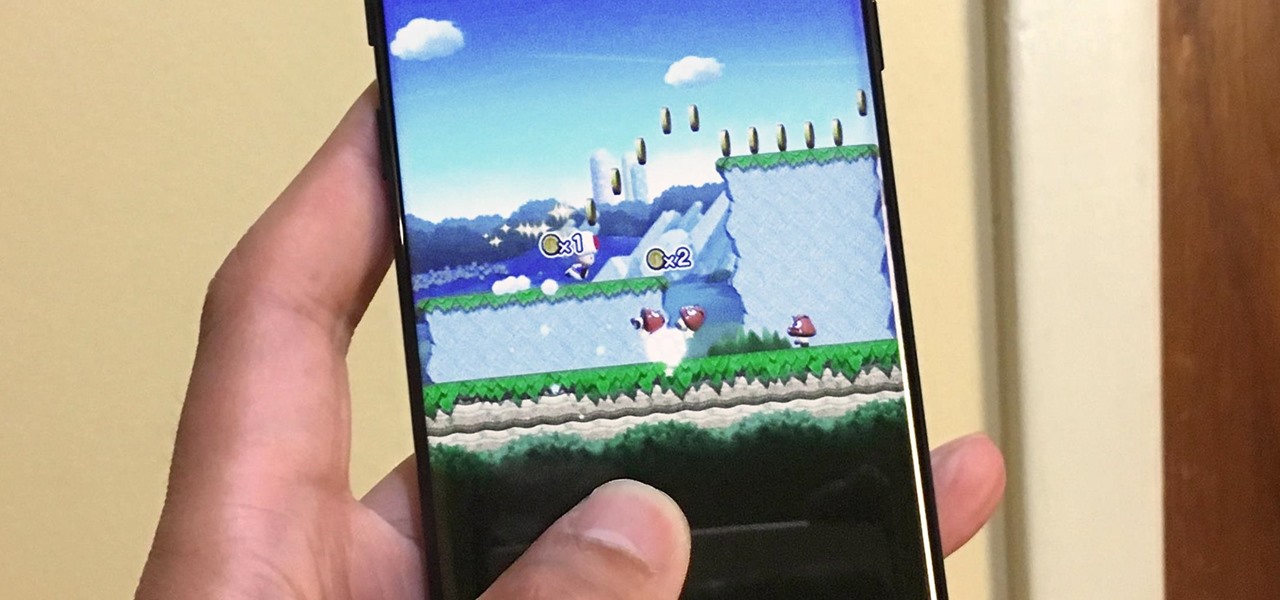
Though not quite as agile as the world famous plump plumber Mario, Toad, the lovable fungus, is still one of the most fun characters to use while playing Super Mario Run. Thankfully, he is also by far the easiest character to unlock in the game, requiring no special tasks to complete.

When you first set up an iPhone, you'll be prompted to create a six-digit passcode to unlock your screen and access certain system settings. If you skip this step, you can always go back and create one, which we highly recommend. Without a passcode, everything on your iPhone is accessible by anyone who gets their hands on it — nosey friends, hackers, thieves, local law enforcement, the FBI — and you don't want that, do you?

We continue to field stories underscoring the strong trends of Investment in augmented reality in various sectors. This week, one company strengthens their offerings to the enterprise sector, while two other companies capitalize on the promise presented by augmented reality to consumers – specifically, in gaming.

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.