As augmented reality gains popularity, the demand for delivering related services and generating content increases. This is demonstrated by a pair of investments from the past week, one in the expansion of a technology lab and another in the form of seed funding for a content studio.

One of the more meme-able characters from the animated series Rick & Morty will be able to beckon iPhone owners to "show them me what you got" thanks to ARKit.
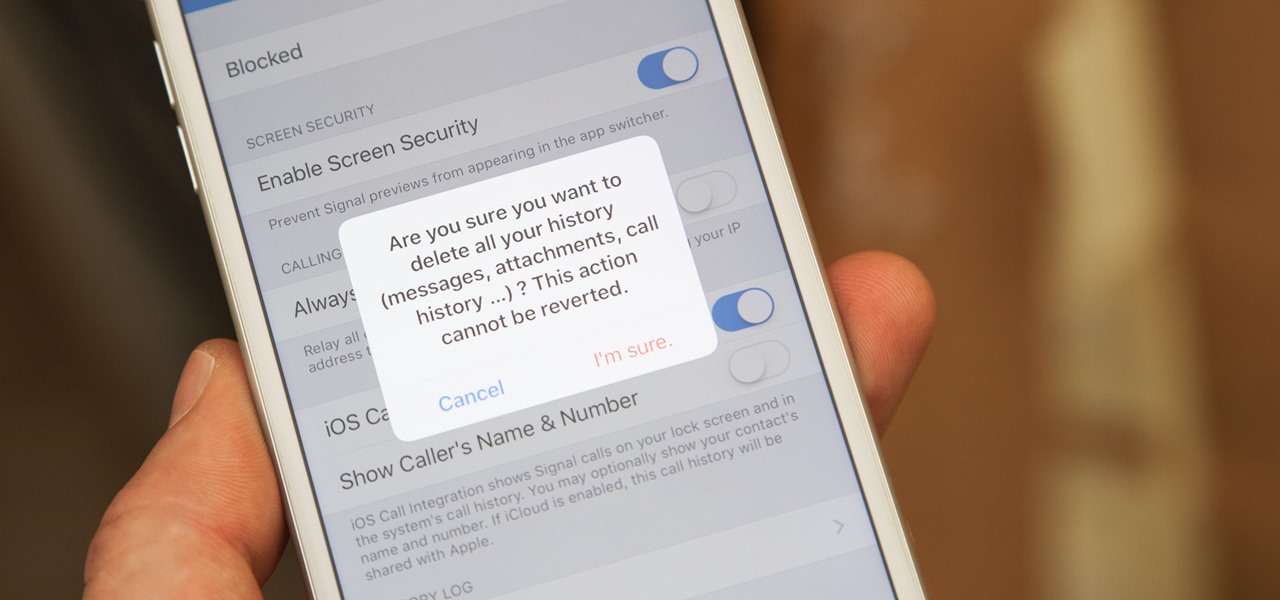
If thieves, hackers, law enforcement, or other would-be enemies should ever gain entry to your smartphone, they could also access conversations you've had in Signal Private Messenger. To better secure your encrypted communications, you can password-protect the whole app and its contents — but only on Android. Even then, it's necessary to perform data deletion on a periodic basis, if not immediately.

Intel's driverless division will be managed by Israel-based Mobileye, as the chip giant emerges from relative obscurity in the driverless space to become a major supplier after completing its $15.3-billion purchase of Mobileye this week.
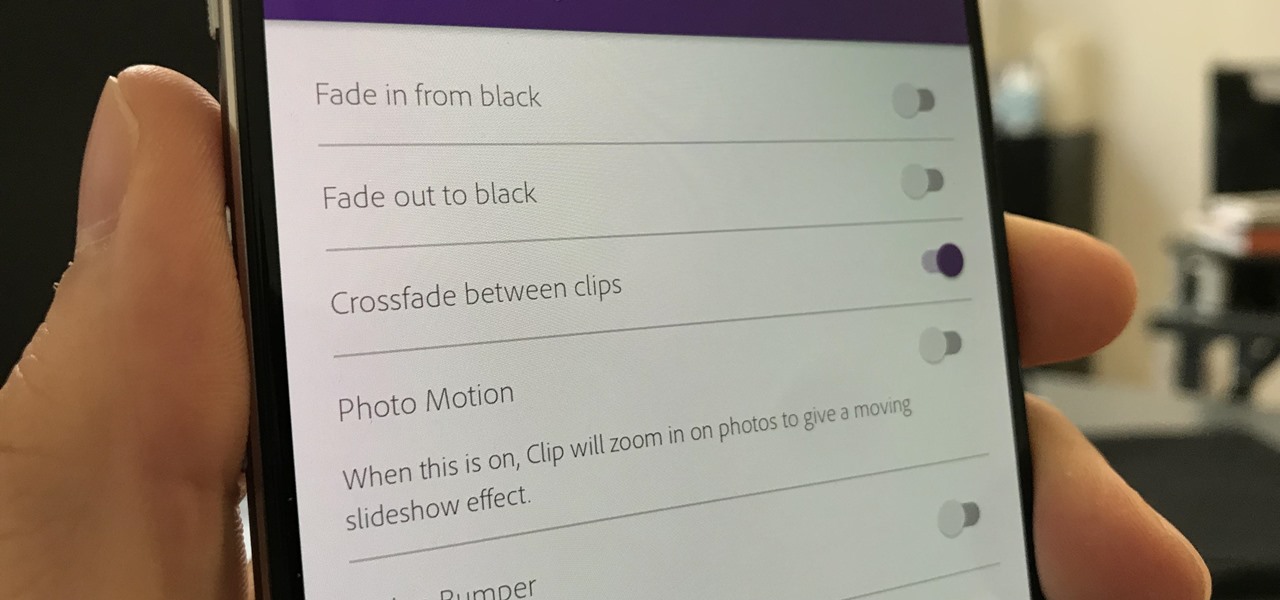
Crossfades are a great way to get from one scene to another. They bridge the gap between two video clips in a fresh, fun way. But can you even use this transition in a smartphone editor? You bet you can, and it's extremely easy.

Drones are a fairly new craze to hit the nation. While they are accessible to the general population, good drones still typically cost a ton of money and despite all the fun they are, it's sometimes not worth it to actually buy one. If you're one of those people who would love to play around with drones — but don't want to have to buy one — Arcane Reality is developing the app for you thanks to Apple's ARKit.

One of the best features in Super Mario Run is the ability to unlock other notable characters from the classic series on iPhone or Android. Each playable character in Super Mario Run has a slightly different skill set — be it speed or jumping — which can come in handy in certain maps or races.

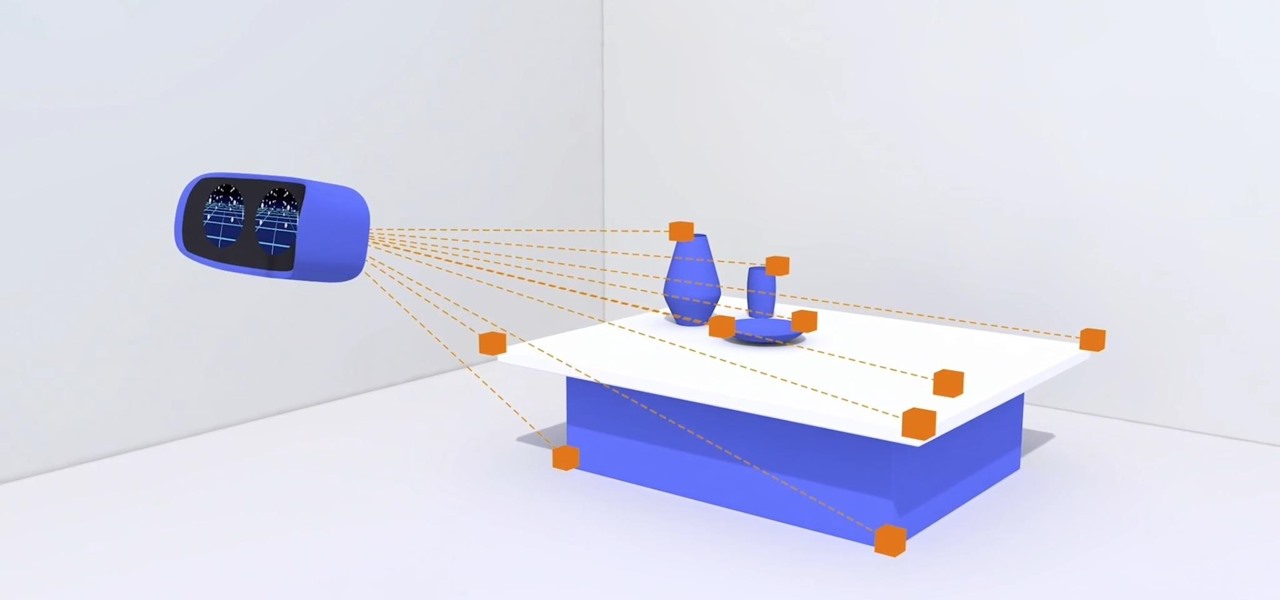
Germany-based Pupil Labs has jumped into the UX and control deep-end with a range of products that allow the user to add eye tracking to not only their existing augmented and virtual reality head-mounted displays but computers as well. This type of technology can add a new depth to the way we control devices.

The Sharknado franchise is, somehow, releasing a fifth movie "Sharknado 5: Global Swarming" (groan) next month. In anticipation of the film's release, the company has decided to create an augmented reality mobile game called, prepare yourself, "Sharknado: ShARkmented Reality".

The auto industry continues to shift into high gear to lay the groundwork for driverless cars with an electric vehicle (EV) emphasis.

The common thread between this week's Brief Reality stories is that augmented reality is beginning to prove its worth as a technology that improves workflows and processes. From customer service to healthcare to manufacturing, augmented reality is helping companies improve productivity.

After Ford's CEO Mark Fields' three-year tenure failed to keep up with the driverless industry and resulted in a 40% drop in shares since Field's took over in 2014, Ford is going in a new direction. Jim Hackett, who was previously chairman of Ford's self-driving division, has succeeded Fields as the company's new CEO.

Google announced several new devices (as well as updates to existing devices) that will take advantage of the company's augmented and virtual reality platforms.

One major component of Level 4 and Level 5 driverless cars is in very short supply. Venture capitalists and engineers from around the world are racing to fill the LiDAR production, price, and performance void.

Hackers are good at what they do—some can even use the way you move your phone to guess a 4-digit PIN in five attempts or less. That's why most of us with compatible hones use the fingerprint scanner. It's just much more secure. Or is it?

As with any new smartphone (but especially with Apple), the iPhone 8 is generating rumor after rumor. This newest rumor, however, rocks the boat a bit, as BGR reports that the iPhone 8 may release at Apple's standard time in the fall, but the 3D camera will be pushed to the 8s.

The big Waymo versus Uber trial isn't scheduled until May, but the heat between Uber and Waymo is rising fast; Waymo wants Uber's driverless trials shut down by a court injunction, unless ex-Google employee Anthony Levandowski testifies in court.

While there are many uses for augmented reality in the automotive industry, adoption has been slow. With the plethora of makes and models on the road today and rolling off assembly lines tomorrow, developing and deploying knowledge bases that utilize augmented reality to dealerships and garages can be costly and difficult to scale.

A scary piece of malware just got a lot more terrifying this week. Security firm Comodo reports that "Tordow," a banking Trojan first uncovered in September 2016, received a massive update this December.

Having control of your basic motor functions is something most people take for granted, but for individuals with Parkinson's disease, that is not the case.

Looking to get seriously tatted up? Your best bet is probably to head Down Under. Meet Steve Butcher, a New Zealand native who is changing the tattoo game in a big way. While there are a lot of amazing artists out there, the level of detail Butcher is able to achieve is truly unbelievable.

Most popular virtual reality headsets, like the HTC Vive and Oculus Rift, require a tethered connection to the computer and that imposes some obvious restrictions on how much we can move in our space. We'd all prefer a simpler, untethered option, and Intel wants to provide just that.

Keyboards and mice work fine for computers, but in a holographic environment you'll want to do more than just point, click, and type. While we can still benefit from these input devices, complex hand-tracking methods are necessary for the evolution of mixed reality user interfaces.

The new lock screen in iOS 10 is a lot different than previous versions, but one thing that stuck around is the quick access camera shortcut. The only real difference aside from aesthetics is that now you don't have to swipe up from the camera icon. Instead, you can simply swipe to the left from right side to quickly snap a picture.

We're already glimpsing the future when we look at mixed reality through a headset, but is the real evolution of this technology something that will exist as part of our bodies? As intense as that may sound, TechCrunch's Jay Donovan offers compelling reasons why it's not such a crazy idea:

If you have personal information stored on a Kindle Fire tablet, be warned that Amazon has removed encryption support for Fire OS 5. So if you have stuff on these devices...maybe a risque book, or private notes, or pictures you'd rather not let out to the world, now would be the time to remove them. And unless Amazon changes its mind and re-enables encryption, don't use your device for anything personal, as anyone who gets a hold of it will be able to gain access to everything on it.

In my last tutorial I very briefly introduced Zanti , but in this tutorial I will start to show its many features. The first step on hacking is recon . You could use Nmap , but the problem with Nmap on Android is that by itself, in order to gain full functionality your phone must be rooted. Thank goodness for a few geniuses in Zanti's dev team whom managed to implant full fuctionality of Nmap in Zanti without rooting your phone. With that being said, boot up your Android phone and lets start ...

A few lines of code in the iOS 9.1 library cache found by Chase Fromm (@uloshe) indicate that Apple could be working on making iPhones that are Li-Fi compatible.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

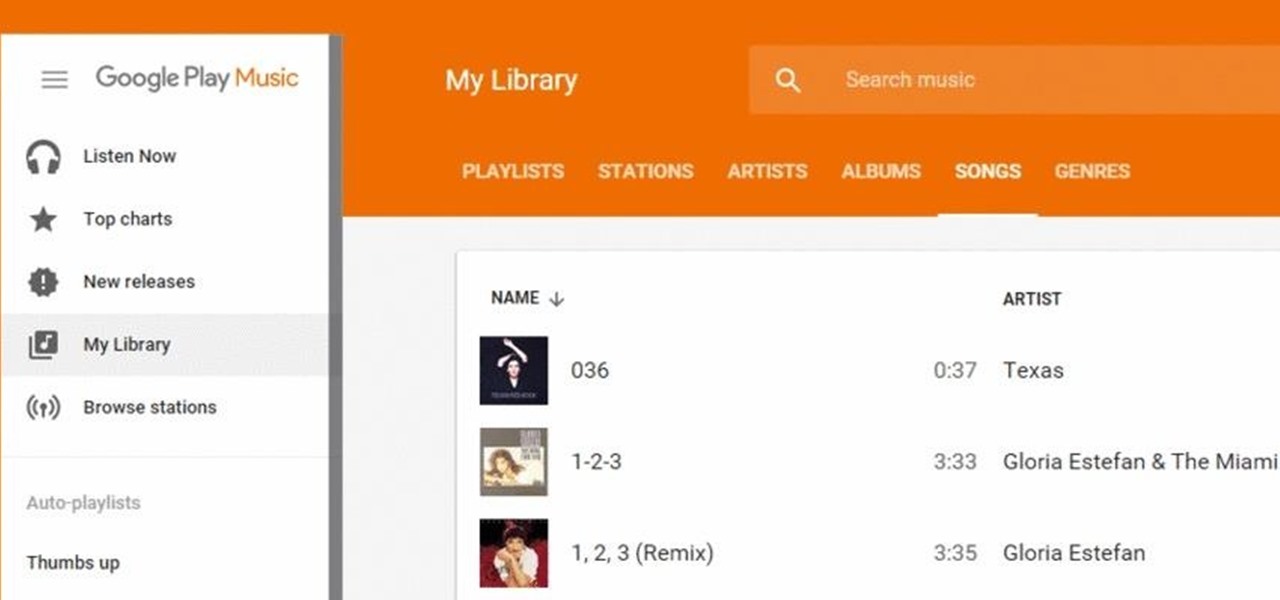
Google Play Music has been my go-to music service ever since its release. The free cloud storage for 50,000 songs and full access to Songza-powered radio stations make it a great music app, even without the $10/month streaming service.

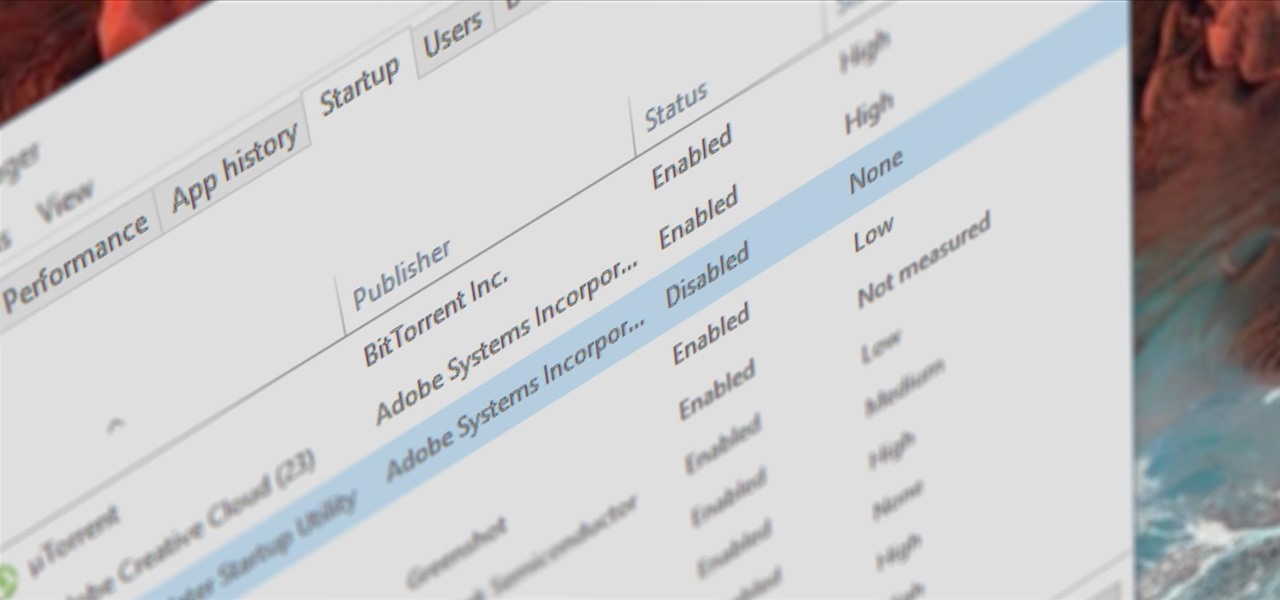
Microsoft had boasted that Windows 10 starts up as much as 30% faster than Windows 7 would on the same device, but depending on your setup, this can still be incredibly slow. Many programs choose to start up alongside Windows, which can make booting your PC quite a hassle.

There was one company at the 2015 LA Auto Show that had everyone intrigued. They didn't have a big booth, and they only had one car on display, but they definitely had everyone's attention.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

In modern versions of Windows, Microsoft made quite a few changes to Windows Explorer, the first of which is a new name—File Explorer. Another huge change that most will notice is that File Explorer now has a new look sporting the Ribbon interface.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

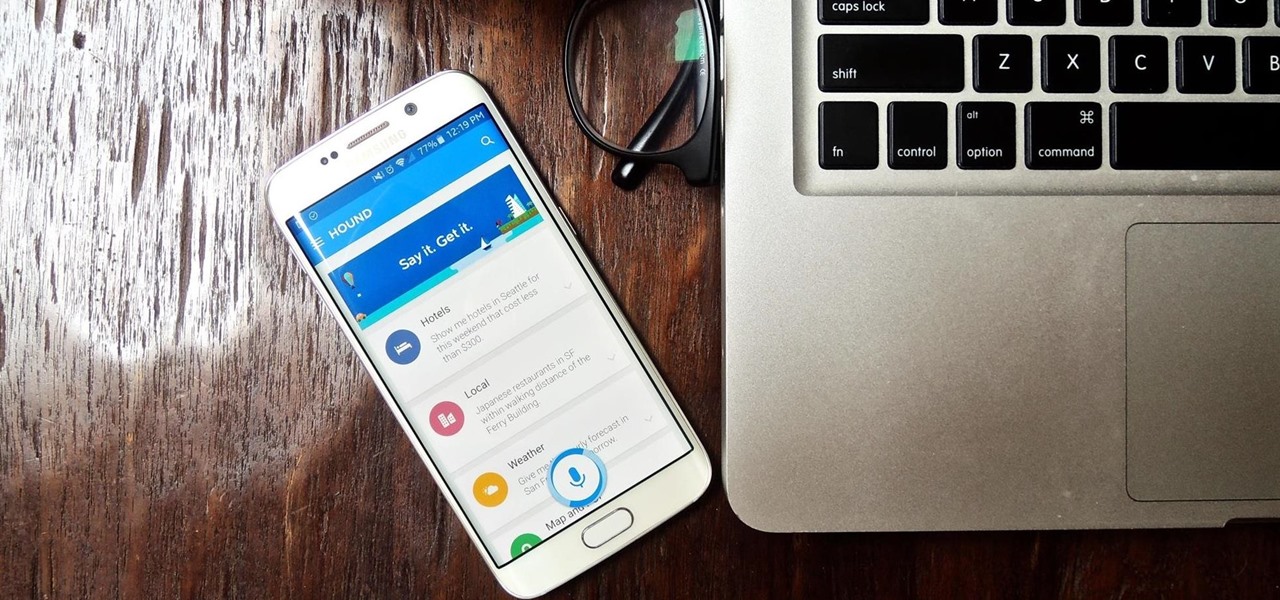
SoundHound's new virtual assistant application, Hound, is gaining a lot of buzz in the tech world—especially after a demo video showed just how awesome it works (it has amassed over 1.6 million views in under a week).

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

If there's one gripe I have with Android Lollipop, it's the new volume menu. When Priority mode was introduced, the stock volume panel was revamped to accommodate it, and somewhere along the way a bit of functionality was lost.