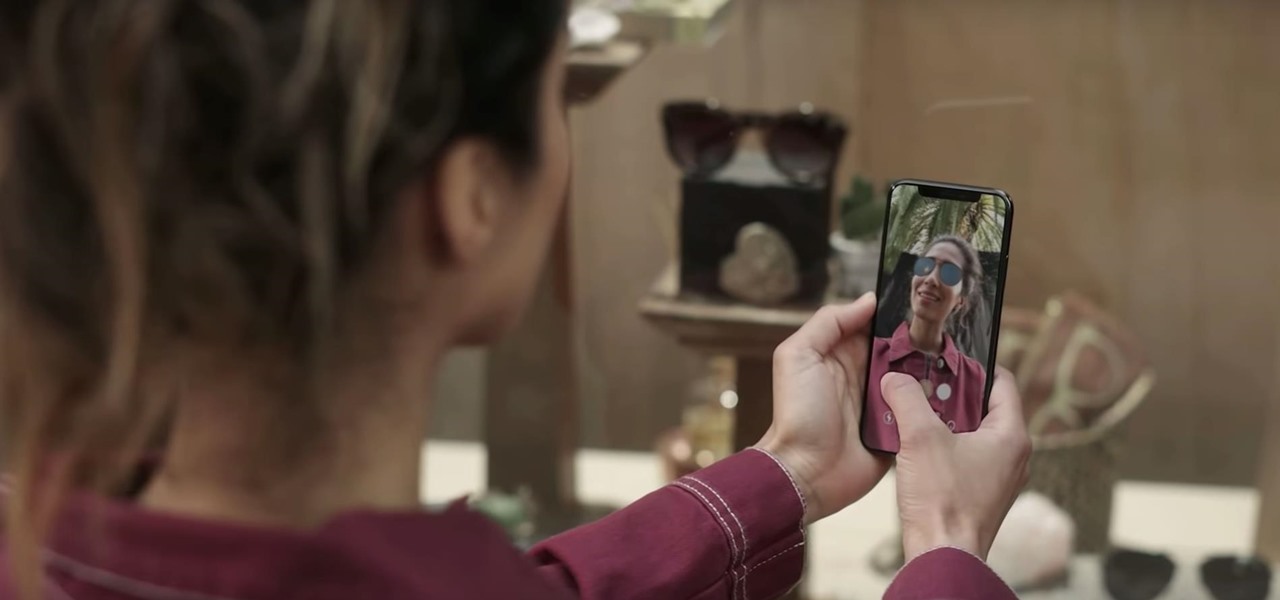Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

One Instagram creator's augmented reality homage to Disney's deep bench of animated characters has earned him fifteen minutes of fame.
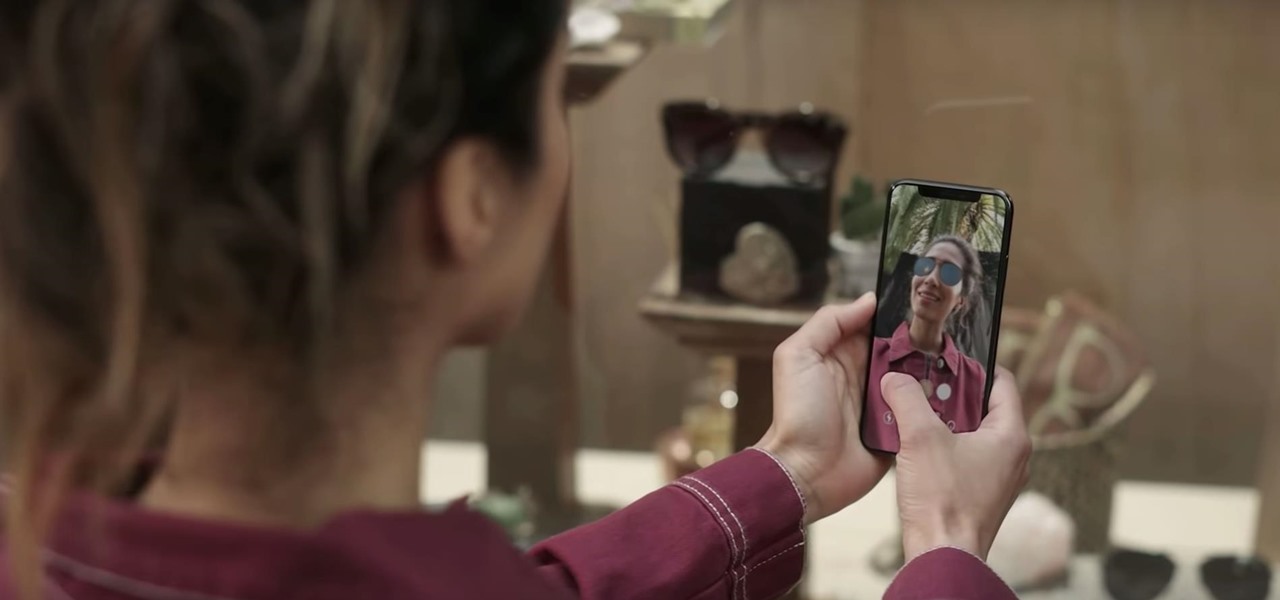
If there's any lingering uncertainty as to the mainstream viability of augmented reality, a list of the top mobile apps and games of 2019 serves to dispell those doubts.

After opening up its Spark AR platform on Instagram for all creators, Facebook is already expanding the platform's capabilities on its Snapchat killer.

The 15-year-old star of the 1980s-inspired hit series Stranger Things, Millie Bobby Brown, may have (spoiler alert) lost all her powers as the character "Eleven," but in the real world, she still has augmented reality in her arsenal.

A relatively unknown musician from the early-'70s that's gained popularity stateside over the last ten years just got the remastered treatment with two new reissues available on CD and 180-gram vinyl. And they're available right now.

There have been enough music artists releasing Snapchat AR experiences over the past week to fill a small festival. Count them with me: Bruno Mars. Gucci Mane. Kodak Black. Missy Elliot. Imagine Dragons. Panic! At the Disco.

After hosting an augmented reality experience using its Snapchat Landmarker technology at the Statue of Liberty, Snap is now giving creators the opportunity to create their own Lenses with Lady Liberty.

As a root user, you have a lot of responsibilities to make sure your phone stays secure. Expectedly, some things may slip through the cracks. Remembering to check which apps have been granted root access is extremely important. All it takes is one bad app, so it's good to learn how to avoid that at all cost.

Fast-food chain Jack in the Box has decided to put an augmented reality twist on the traditional sweepstakes promotion by employing the immersive powers of Snapchat.

While Magic Leap has remained mostly silent regarding its plans for its Magic Leap One successor, the software team continues to makes strides with improvements to the device's Lumin OS and SDK.

The longer it takes Apple, Snapchat, Facebook, and other tech giants to build their own version of augmented reality headsets and smartglasses, the longer runway of practical experience Microsoft gains with the HoloLens and its sequel. The latest example: AR cloning.

In the last few years, the HoloLens has become a popular tool for use in medical procedures and training. But recently, the Magic Leap One has gained momentum in the space as well when it comes to medical use cases.

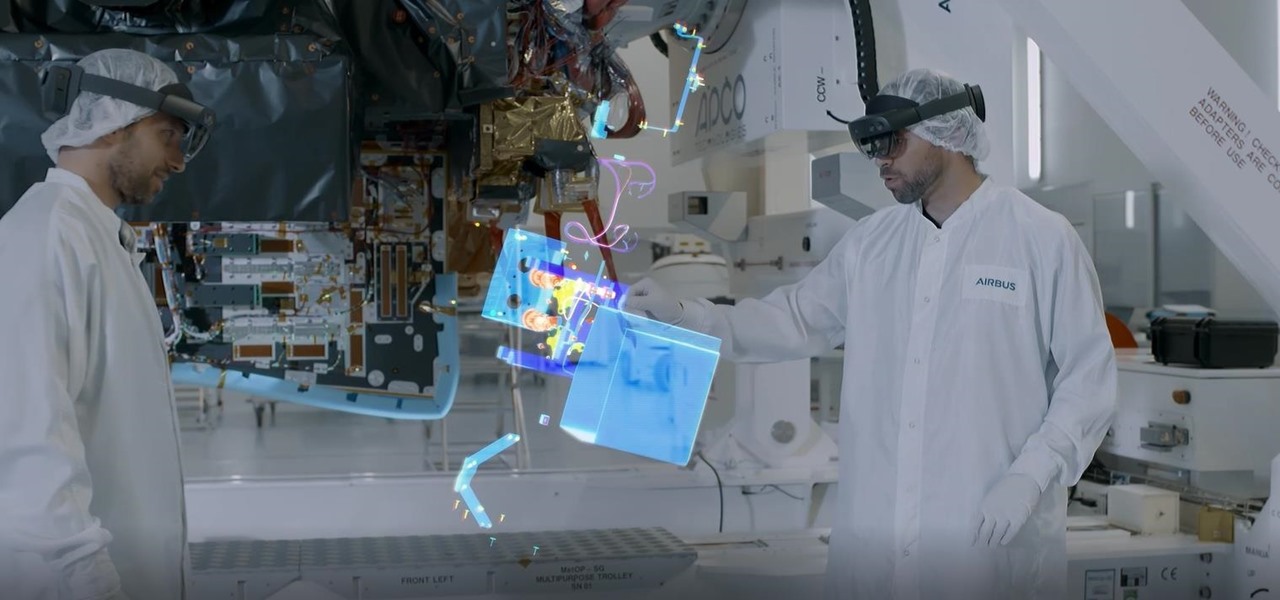
Aircraft manufacturer Airbus is so impressed with the boost in productivity it has gained from Microsoft's HoloLens, the company will begin offering augmented reality software to its customers.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

It's easy to forget just how cool face filters are. Augmented reality has come a long way, and apps like Instagram now offer a suite of impressive effects to play with, but some of the best ones aren't easily found. There is a treasure trove of exclusive, custom face filters that are unavailable to the general public, but not at all inaccessible — you just need to know the trick to getting them.

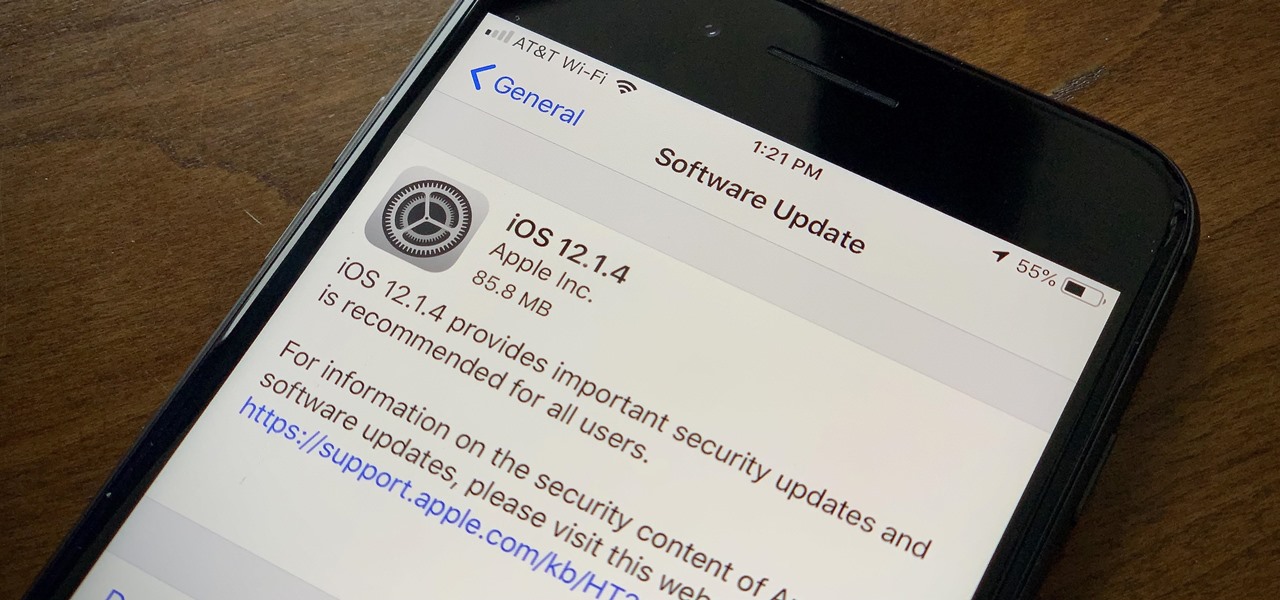
Apple found itself in serious trouble last week when a teenager discovered a critical FaceTime bug that threatened the security of nearly every iPhone user. The bug enabled a user using Group FaceTime to access either the microphone or the camera of a recipient before they answered the call. According to Apple, the issues have been fixed in an iOS 12.1.4 update released Thursday, Feb. 7.

If you're an Apple fan, AirPods are the must-have wireless headphones to own. They know when they're in your ears, will pause music when one is taken out, and when you pair them with your iPhone they'll already work on your Mac, iPad, and iPod touch using the same Apple ID. However, whenever you use them on any other device, you have to manually reconnect them later to your iPhone.

Among a crowded field of AR cloud companies aiming to power the future of augmented reality by creating a world of persistent holographic content that lives in a cloud, accessible across devices and accounts, Ubiquity6 is hoping it has found a way to differentiate its platform.

Last year's augmented reality investments roundup was impressive. And in 2018, the dollars flowing toward AR haven't decreased, as venture capitalists and strategic investors continue to aggressively fund AR startups at a rapid pace.

Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.

Nearly a year to the day after the unveiling Magic Leap One, Magic Leap has dropped another update to the Lumin OS that runs the device.

As highlighted in our article on how to enable Google Now in Action Launcher, doing so takes away the Quickdrawer. This effectively ruins one of the more beneficial features of Action Launcher, making it a tough choice between the two options. So I looked for a solution and found one that works.

Mobile augmented reality pioneer Blippar has now completed its fall from hopeful AR startup to the immersive computing history books.

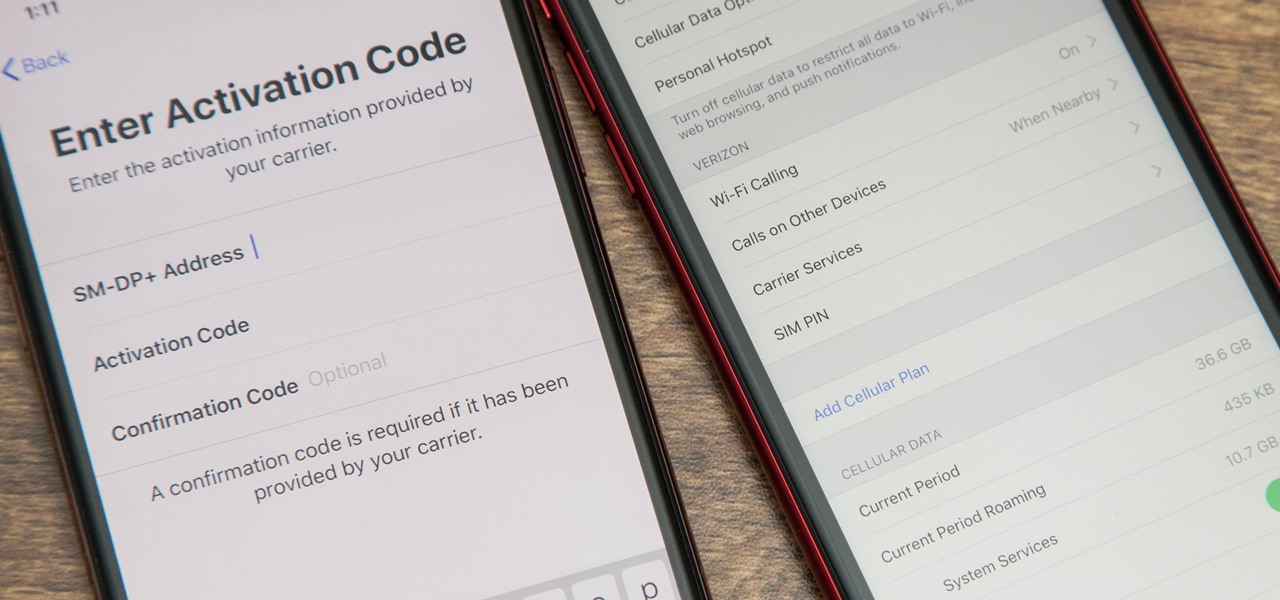
With an iPhone that includes a digital eSIM option aside its standard Nano-SIM card, you can have two cellular service accounts. One can be your primary line with your main wireless carrier, and the other can be from your main carrier or another provider. The eSIM account can be prepaid or postpaid as well as data-only, which is great for traveling. But which wireless providers support eSIM?

This year's holiday shopping season is shaping up to be fertile ground for augmented reality to show its worth, as both Walmart and Target have crafted immersive experiences designed to engage shoppers in the coming weeks.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

The OnePlus 5 doesn't have too many weak spots, at least not when you consider the price. But you might feel that the company with the slogan, "Never Settle," might have actually settled a bit with its camera. The OnePlus 5 and 5T don't have bad imaging specs, but they could use a pick-me-up, which is what we're about to provide. There's a bit of a catch, though.

Fresh off shipping an augmented reality game for Magic Leap, Resolution Games has farmed another $7.5 million in funding through a Series B round.

At its annual MAX event kicking off on Monday in Los Angeles, Adobe gave the audience a new preview of its forthcoming Project Aero augmented reality authoring tool during the keynote presentation.

Earlier this year, Samsung released the Galaxy J3 and J7 to select markets. These two devices are the latest in the J series, Samsung's super-budget series that tries to rewrite what it means to be a budget phone. Now, starting September 14th, you will be able to get them GSM unlocked.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

As it prepares to ship its first product by the end of the summer, Magic Leap has managed to impress yet another high-profile investor in telecommunications giant AT&T.

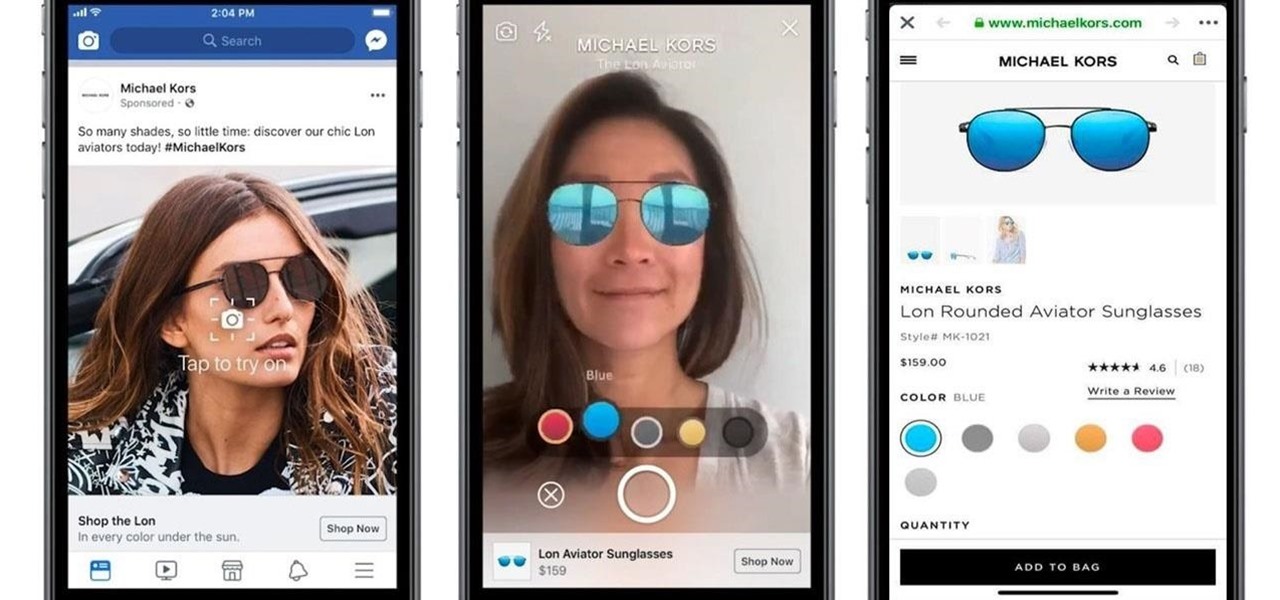
Facebook is preparing to make augmented reality experiences for brands more visible in its mobile app with Tuesday's introduction of augmented reality ads in its News Feed.

When you receive a photo or video from a contact in WhatsApp, after you load it, it's automatically saved to your phone's local storage. That means all received content from WhatsApp is visible to anyone who gains access to your default photo gallery. Luckily, there's a new feature available for the Android version of the app that can prevent this from happening.

Consumers are chomping at the bit for augmented reality smartglasses from Cupertino's finest, but one market analyst is saying not so fast, Apple fans. Meanwhile, automotive AR is gaining speed, with the latest milestone coming courtesy of a major investment in waveguides by Continental. And although mobile AR apps have already arrived, retailer Target is taking a different approach. So why is Target tinkering with web-based AR? Answers below...

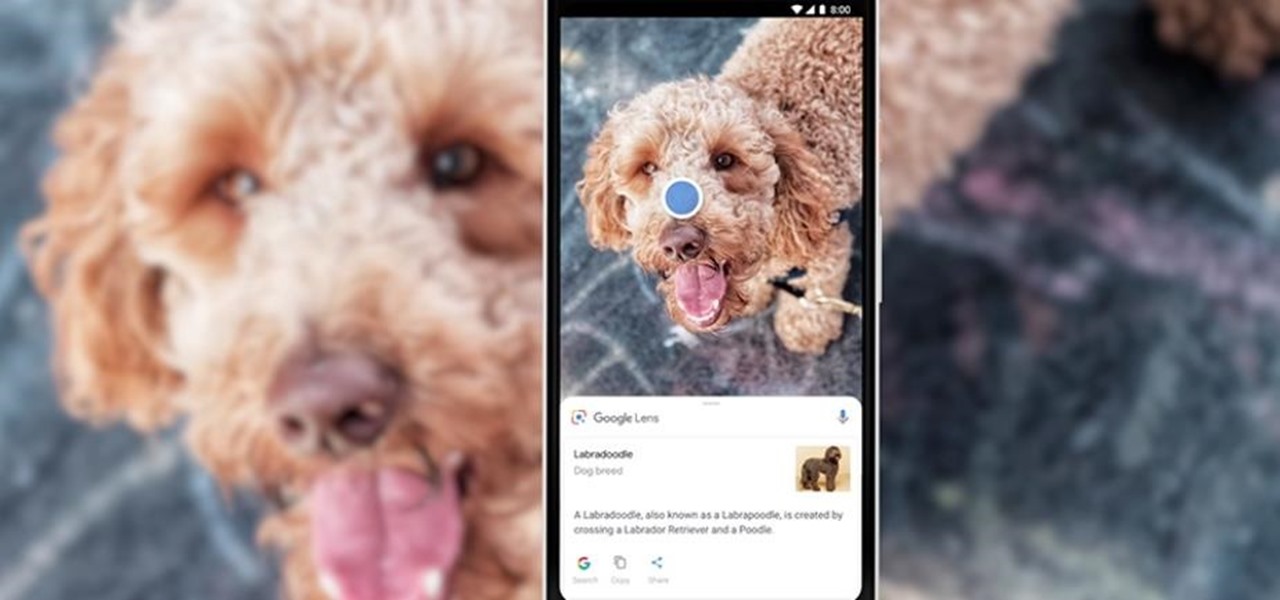
During Tuesday's keynote at the I/O developer conference, Google unveiled new capabilities for its Lens visual search engine and expanded the availability of the platform in smartphone camera apps.

You're at the bar, but your friend can't find you. You could call them, but that wouldn't feel very 2018. Instead, let your iPhone do the talking. Right in the Messages app, you can easily send your friend your current location — all without interrupting the friends you're hanging out with.