Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

Gaining remote access to a phone isn't only for super hackers and spies. There are plenty of times when the average smartphone user would want to have remote access to their device.

While Siri may be the cream of the crop when it comes to smartphone personal assistants, there is always room to grow bigger and better (that's what she said). Siri, although recently expanded, is still lacking in the amount of commands and actions she can currently perform. While looking up directions and restaurants is fairly easy for Siri, asking her to gain access to third-party programs or browsers is a little more difficult.

UPDATE: The whitehouse petition has received enough signatures to require a response from the government. Your voices have been heard! Now we wait...

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

The new Call of Duty: Black Ops 2 is the hottest game on the market right now, and there's no doubt it'll end up being the most unwrapped gaming gift come Christmas morning. The first-person shooter hopes to carry on the tradition of its many predecessors in bringing the most action-packed gaming modes, along with a high-replay value, to its legions of fans.

TIFF 2012 Wrap-Up - Pounds Personally Gained: 4.5

It used to be that you only had to worry about maids rummaging through your belongings in your locked hotel room. But now anyone with 50 bucks of hardware and some programming skills can hack their way in—as long as it's locked by keycard.

Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack MyBrute with Cheat Engine (09/12/09).

Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack Mybrute for 6 fights on day of registration (08/16/09).

Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack your way to level 14 on MyBrute (08/18/09).

Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to get a pet dog, wolf or bear in MyBrute (06/02/09).

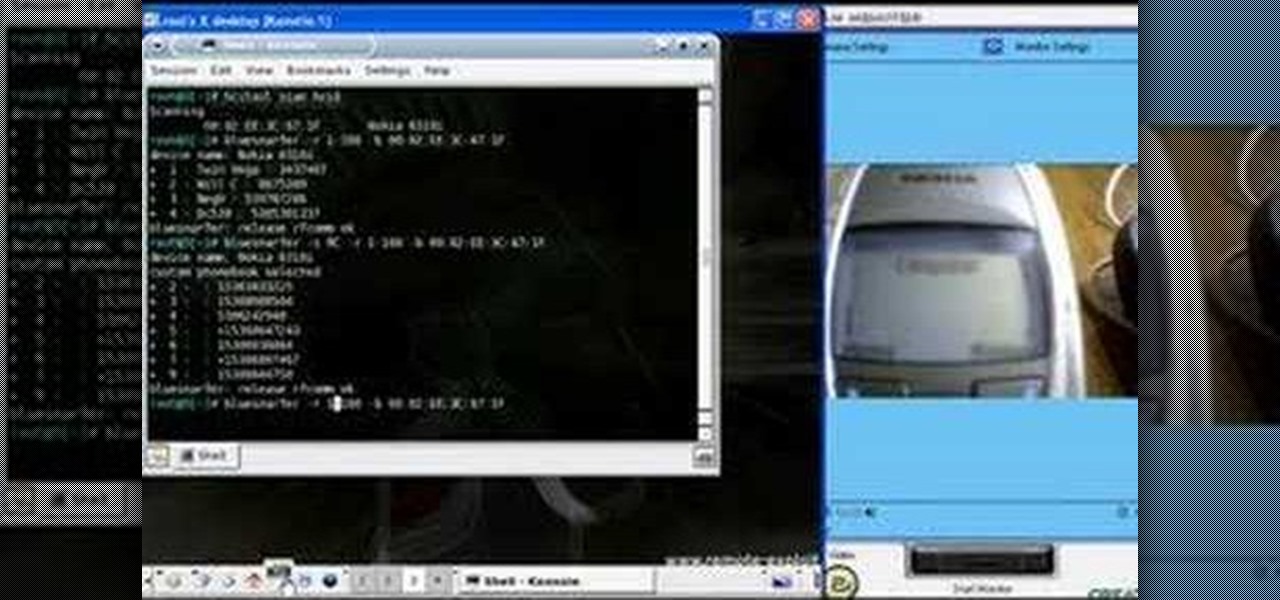
Check out this video tutorial to see how to bluesnarf a Nokia 6310i handset (cell phone). What is Bluesnarfing exactly?

You don’t have to wait to get to the golf course to practice your strokes. You’re swing path and swing plane will improve by doing these exercise and ultimately leave you with a straighter hit. This drill can even be done inside.

If you are looking to improve your piano technique then this how to video is the place to start. You will learn how to strengthen your fourth and fifth fingers with this easy piano exercise. The fourth and fifth fingers are often the weakest fingers when playing piano. You must learn to strengthen then so you can play piano better. This exercise also improves the extension between the ring finger and the pinky finger. This is a great exercise for beginner to advanced students. With this tutor...

This video is all about gaining clew first sailing skills. If you've mastered the beach starts and water starts, then you're ready to learn how to get up on the board using the clew first style. When crashing gybes, jumps, and getting into waves, the clew first water start can be a great way of getting back on the board without having to flip the rig. Watch Sam Ross show you how.

The new Pyro FX in Houdini 10 are very impressive with improved workflow. The Pyro FX are great for creating 3D fire and smoke effects. And in this video tutorial series, you will learn the Pyro FX workflow in-depth and the parameters used to create fire and smoke effects. You will also see how volumetric data is created and recorded, and how to visualize it.

You're trying to mow your lawn, but the engine on your pull-string push mower isn't turning over— why won't it power up? Well, if your lawn mower was stored outdoors for a large amount of time, chances are that the recoil has built up some corrosion or is simply sticking. This video will show you a very simple repair, where you only need to remove 2 or 3 screws to gain access to the mechanism, then grease with silicone spray.

If you're a pee wee coach, you know that coaching kids is a tough job. Children can even be more difficult to work with than adults, but it's the best time to shape them into a great sportsman… and to get faster!

Dolphins are some of the best, most graceful swimmers in the sea. Majestic and beautiful, they achieve both speed and form while looping from wave to wave.

In this 5 part tutorial video, you will learn how to dance the Soukous. Soukous is a vernacular dance which is one of many roots of swing dance. Originating in the Democratic Republic of Congo, this form of dance has been modernized, much like today's swing is a descendant of the cakewalk and Texas Tommy.

Linux is a diverse and powerful operating system that virtually every IT professional must learn and know well. Whether you realize it or not, you have likely already used a Linux device, and learning to design things for it is a key step in any Data Science career path.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

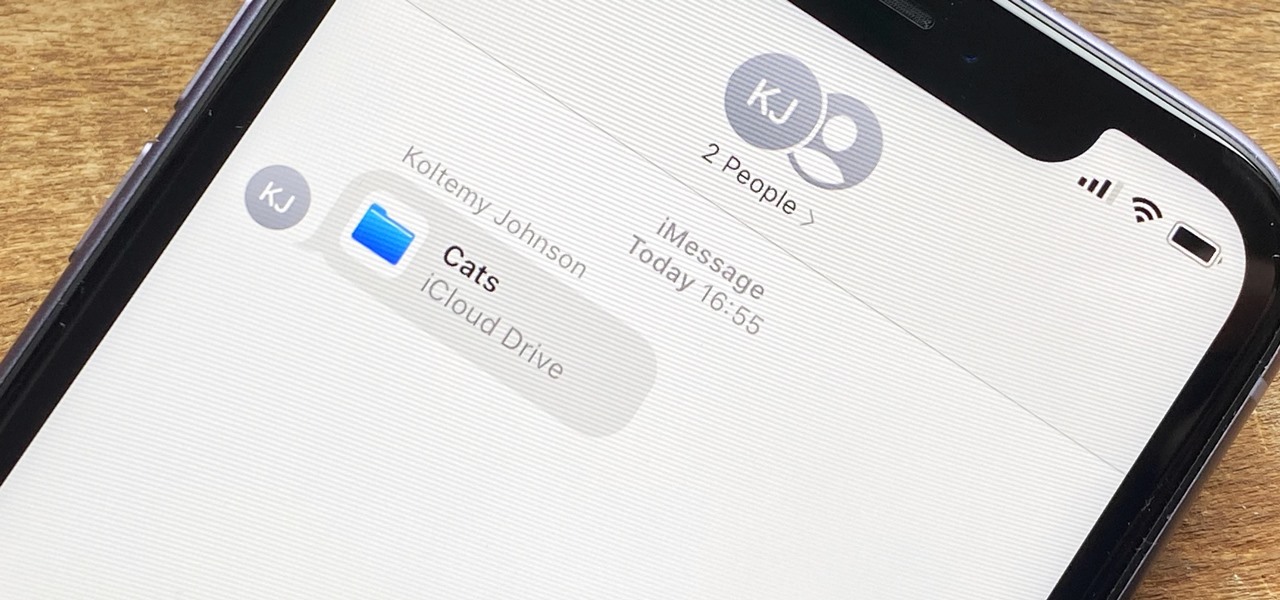
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permission settings.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

When you think about it, isn't life just one big open-world RPG just begging to be conquered? We all have a set number of specific tasks or chores we must complete every single day like clockwork. Sometimes, these items on our to-do list can become tedious and cause us to lose motivation. What if you could take those tasks and turn them into something awesome instead? Now you can.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

It's easy to forget just how cool face filters are. Augmented reality has come a long way, and apps like Instagram now offer a suite of impressive effects to play with, but some of the best ones aren't easily found. There is a treasure trove of exclusive, custom face filters that are unavailable to the general public, but not at all inaccessible — you just need to know the trick to getting them.

Last year's augmented reality investments roundup was impressive. And in 2018, the dollars flowing toward AR haven't decreased, as venture capitalists and strategic investors continue to aggressively fund AR startups at a rapid pace.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

If you're looking for your gaming fix and nothing on the App Store is piquing your interest, you should give soft-launched games a try. These are games that haven't been released in the US yet because they're getting tested in smaller markets first. Using a simple workaround, you can install them on your iPhone in any country.

If bezel-less was the goal of OEMs in 2017, 2018 seems to be the year of the notch. Thanks in no small part to Apple's iPhone X, more and more smartphone manufacturers are designing their displays with this polarizing cutout. While many are frustrated with the trend, it's worth taking the time to consider what each phone gains with the unique design.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

In what's becoming something of a regular occurrence, Magic Leap has yet another internal, unforced error on its hands. Thankfully, this time it's not about legal skirmishes or theft, but a rather unusual break from company protocol that has been quickly swept under the rug.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

Super Bowl LII will bring millions of football and non-football fans together to watch the big game on the big screen. But without a cable subscription, this process can be a little daunting. Luckily, the Google Play Store and the iOS App Store offer a few ways to accomplish this — no cable contract required.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.