Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

This instructional gambling video teaches you the basics of craps. Learn the rules and etiquette of playing the game as a beginner.

This gambling video shows you some strategies in placing your bets on the 6 & 8 in craps.

Who says Vegas is only good for gambling? This is a level-by-level walkthrough (on realistic difficulty) of Rainbow Six: Vegas for the PS3, XBox 360, and PC. A helpful voiceover commentary is included.

Place slip knot on hook. Hold yarn taut with 2 sets of 2 of fingers placed about 1½” apart, with tail in other hand. Create loop that crosses over bottom of 1st strand with loop toward right side. Fold loop over main strand going past tail. Insert hook below at tail strand. Pull up a loop using main strand for this loop. Pull 2 ends of yarn taut while leaving slip knot on hook. In 1st chain work 1 single crochet. Skip 2 chains; work 1 double crochet in 4thchain. Picot stitch by chaining 3 & a...

Getting angry makes you look weak, especially in an argument. Defuse your temper with these helpful tips.

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

While any form of gambling is set up to make you lose, there are some tips and tricks, shown in this how-to video, to help even the playing field. Penny arcade slots are a reasonable place to start, as the stakes aren't too high, so neither side (you or the arcade) has that much to lose. Watch this video conning tutorial and learn how to beat an arcade penny slot machine.

This gambling video show you some of the worst bets to make on a craps table and how to avoid them.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

After winning the 2015 FIFA Women's World Cup, the USA Women's National Soccer Team is ready to defend its title in the 2019 tournament.

Now that the NCAA Basketball Tournament is underway, 7-Eleven has decided to launch an augmented reality experience to remind basketball fans where they can quench their thirst throughout March Madness.

If two hands are better than one, then two hand-tracking SDKs must be better than one as well. After uSens announced its Hand Tracking SDK at the Augmented World Expo in Santa Clara on Thursday, ManoMotion unveiled the latest version of its own SDK. Both technologies give apps the ability to track hand gestures with just a smartphone camera.

Last week, I tried out StackAR, a puzzle app updated to support ARKit where the AR features felt mostly unnecessary.

Disruptor Beam just soft launched The Walking Dead: March to War in the Philippines. It's not officially available in the US yet, but there are ways to play this take on Robert Kirkham's post-apocalyptic masterpiece regardless of where you live.

Mobile augmented reality developer Blippar has escalated the augmented reality advertising arms race, introducing a new rich media ad format that enables augmented reality experiences without a dedicated app.

Uber's chance at driverless domination may be ripped away as its legal battle with Waymo escalates. The company's self-driving program is now under threat of closure if the allegations of premeditated theft are proven

The first augmented reality hardware and software functional requirements guidelines have been released today by UI LABS and the Augmented Reality for Enterprise Alliance (AREA).

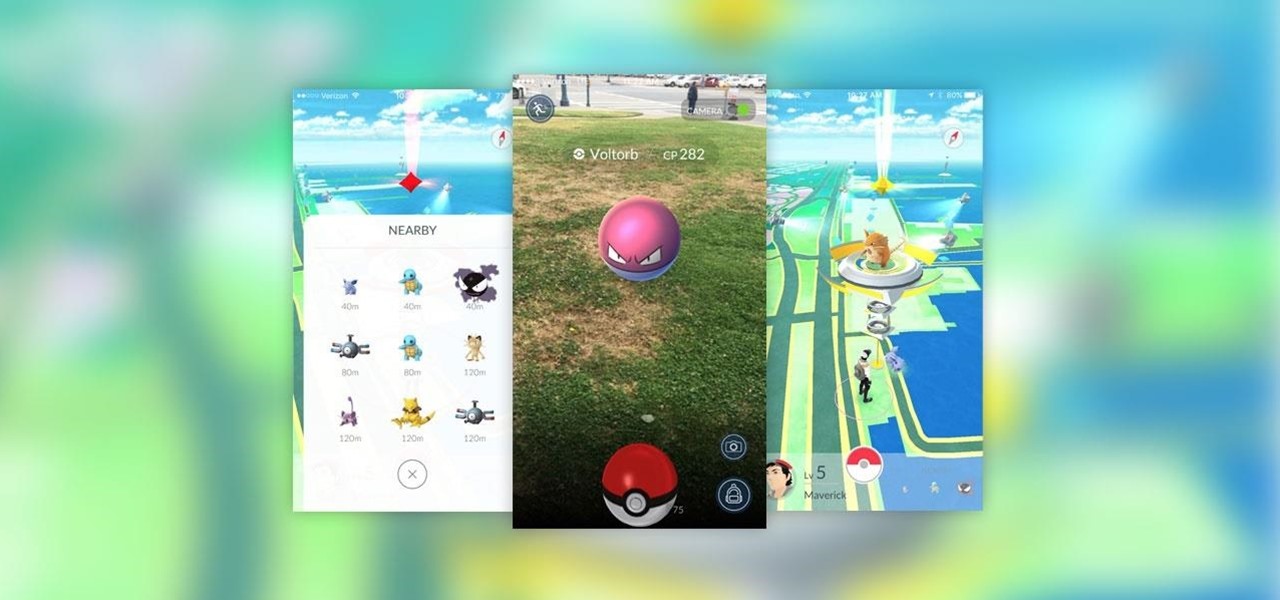
Pokémon Go takes the popular franchise and brings it into the real world through augmented reality, allowing us to play the game while exploring our physical environments at the same time. It doesn't just put pocket monsters into a more realistic context, but it changes the game in some major ways that may delight some players... and upset others.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

As demonstrated by holographic experiences for the Microsoft HoloLens and the Magic Leap One, volumetric video capture is a key component of enabling the more realistic augmented reality experiences of the future.

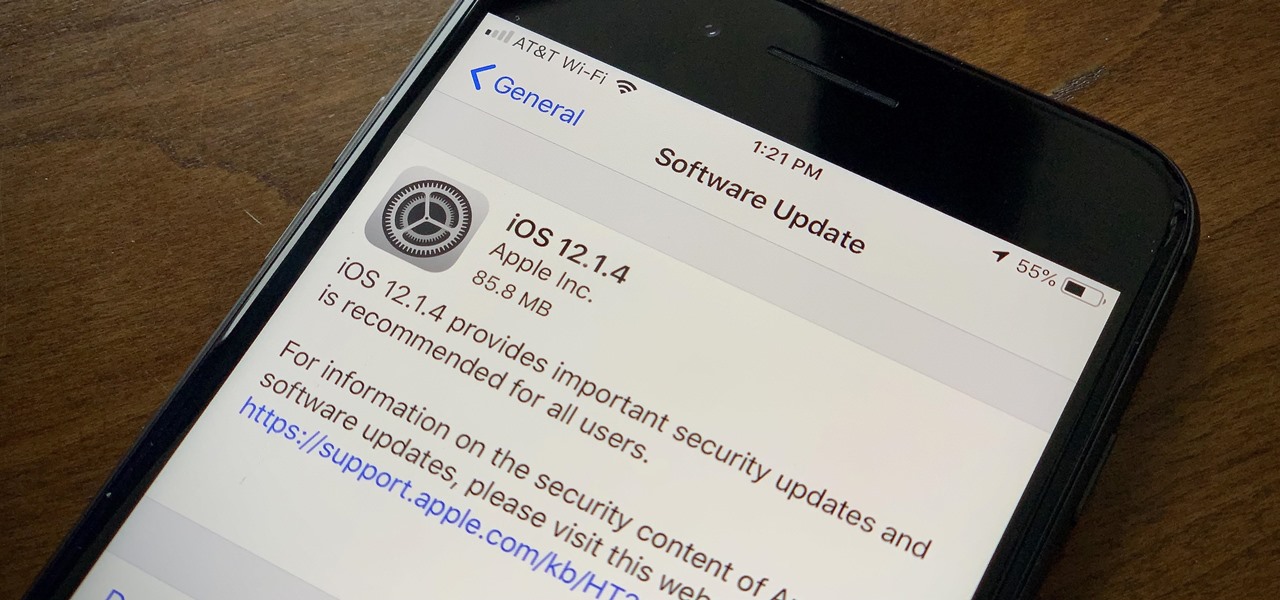
Apple found itself in serious trouble last week when a teenager discovered a critical FaceTime bug that threatened the security of nearly every iPhone user. The bug enabled a user using Group FaceTime to access either the microphone or the camera of a recipient before they answered the call. According to Apple, the issues have been fixed in an iOS 12.1.4 update released Thursday, Feb. 7.

Augmented reality gaming company Niantic Labs is now instigating conflicts between Pokémon GO players, but it's not as bad as it sounds.

Following the surprise release of Magic Leap's SDK on Monday, March 19, Unity, Unreal Engine, and Mozilla followed up by announcing official partnerships with the company.

Transparent display maker Lumus has reached a deal to license its augmented reality optical engine models to Quanta Computers for mass production of displays for consumer smartglasses.

A potentially groundbreaking new app targeting retail financial services hopes to bring augmented reality to your local bank and credit union.

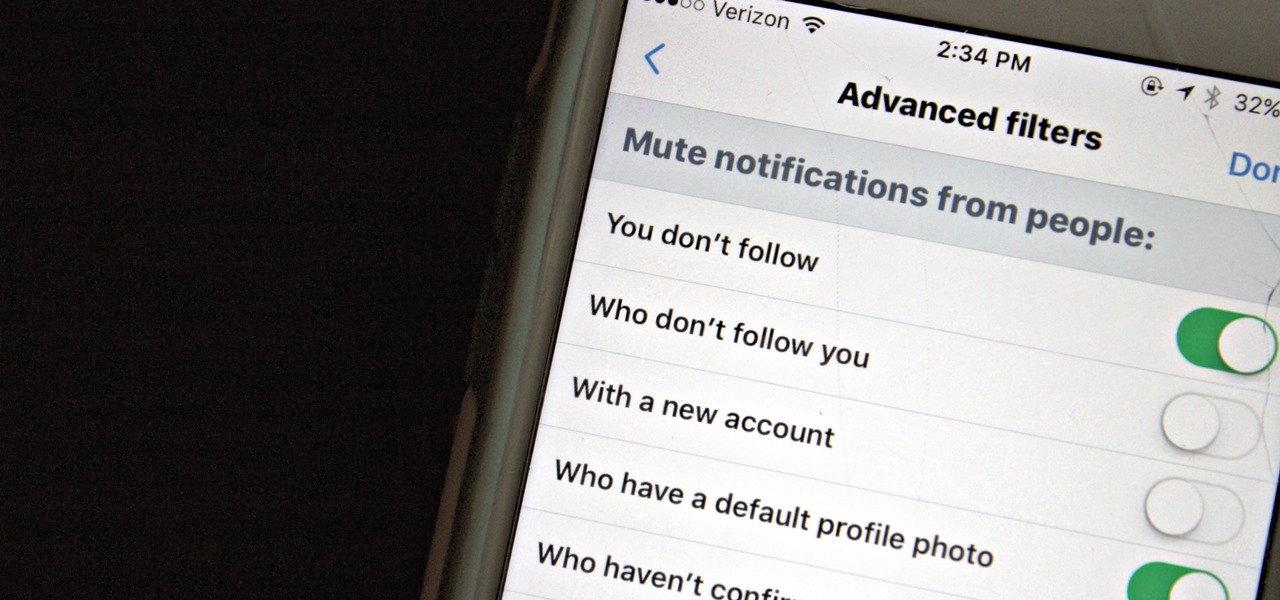
Twitter is a hotbed for abusive accounts. Because it's such an open app, strangers from all over the world can see your tweets. Obviously, not everyone agrees on everything, but sometimes things can escalate to the point where it's considered harassment from people you don't even know.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

So, your buddy's getting married and it's time for that age-old tradition the "bachelor party". Make sure the party goes off with out a hitch by remembering the goal is to have fun and not to ruin the wedding, get a DUI or destroy the reputation of your friends. Plan accordingly.

Conflict is a part of life but how you deal with that conflict is up to you. You may find yourself in an argument and instead of making it a shouting match, employ some techniques that will be sure to keep this conversation civil.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

While the big names in augmented reality demonstrated the breadth of opportunities in the industry's landscape this week, one new startup showed off what is possible further in the future.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Augmented reality plays a key role in the evolution of adjacent technologies, such as 5G connectivity and brain-control interfaces (BCI), and the business news of the week serves up proof points for both examples.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

The hunt for the mixed reality use-case that wins over consumers' hearts and creates a critical mass is a problem every developer would love to solve. Not only would they find themselves rich and famous seemingly overnight, but they would also end up making one of the various possible hardware solutions a viable place for other developers to put their time and energy.

In a disturbing turn of events, Uber has been tracking oblivious iPhone users even after they removed the application from their phone. Two years ago, the situation escalated to such an extent that CEO Travis Kalanick earned a slap on the wrist from Apple mogul Tim Cook.