In this Quick Clip, I'll be showing you how a supercooled soda is transformed into a slushy "slurpee" in under 4 seconds. I was inspired to do this little soda trick by The Super Effect's video on YouTube from a few years ago.

Don't panic the next time you pull an empty tub of butter from the fridge. If you have some heavy whipping cream, save yourself a trip to the grocery store and just make your own. When heavy cream is shaken violently for a long enough duration, it turns to butter—and if you're doing it by hand, it also feels like your arm turns to jello.

While Siri's integration with the iPhone is becoming increasingly substantial, restrictions with the intelligent personal assistant are apparent when it comes to third-party apps like Google Maps, Netflix, and Spotify (unless your iPhone is jailbroken, of course). As an avid Spotify user, it's distressing that I can't use Siri to navigate through the music streaming service's extensive library. In the car, I use Spotify about 90% of the time and it can become increasingly frustrating to chang...

Here's how to make a simple form of a slow burning fuse from materials around the house. WARNING: Ignition of an incendiary or explosive material may not be legal in your area, so check local laws before attempting. Use of this video content is at your own risk.

If you have the international version of the Samsung Galaxy S2 (I9100) and are sick and tired of waiting for the Jelly Bean update to hit your device, you're in luck—XDA-Developers member izap has leaked what appears to be the final version of Android 4.1.2 for the S2.

One of the biggest downsides to the iPhone is that it isn't as easy to customize as other smartphones. It's true that this makes Apple products more secure in some ways, but it also means that you have to jailbreak your phone and void your warranty if you want to change certain things.

Cooking isn't something that interests me much, unless it results in a fast burning fuel and a successful rocket launch!

Planning on getting the iPhone 5, but want to keep your SIM card? The new nano-SIMs that manufacturers are adopting will be even smaller than the micro-SIMs that most of us currently use. It's fairly easy to cut a regular SIM down to a micro-SIM, but because the nano-SIM will be thinner as well as smaller than the micro, cutting it down to size will require a little more work. Photo by Tech Digest

The worst part of moving into a new place is, well...moving. It's tedious, a lot of hard labor, and it can take forever, and don't even get me started on all those labels. It's also one of the only times in your life when everything you own can be stolen at once, since it's sitting in a movable container. Rather than risk losing everything, try this DIY Moving Truck Alarm System by Tim Flint that lets you know when the loading door is opened so you can catch would-be thieves red handed.

Motorola launched a new webpage on Friday that tells Android users how to unlock the bootloaders on a limited number of new Motorola smartphones and tablets. This new 'Unlock My Device' page helps demystify the process and make it easier for users to customize their phones.

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

Assuming that you are living north of the equator, ‘tis the summer season for brewing your own sun tea. Unlike the conventional method of dunking tea bags in boiling hot water for several minutes, sun tea is brewed over the course of several hours through the natural heat of direct sunlight.

Do you like games like Monopoly, Risk, Stratego, Dungeons and Dragons, Chess, Checkers, Uno, Battleship and Connect Four? If so, this board/card game could be next for you.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

The hunt for the mixed reality use-case that wins over consumers' hearts and creates a critical mass is a problem every developer would love to solve. Not only would they find themselves rich and famous seemingly overnight, but they would also end up making one of the various possible hardware solutions a viable place for other developers to put their time and energy.

Looking for ways to hack your favorite games without having to take the risks of Cheat Engine? This video shows you how you can hack the web game Swords and Sandals 2 without having to rely on any program at all.

This video is designed to help deaf people, or those with hearing impairments, learn how to do basic first aid. Specifically, this video deals with sever bleeding and how to stop it, and is taught in sign language.

Doing electrical work is one of the most intimidating tasks for a novice home repairman. But if you know what you're doing, the risk is pretty minimal. In this clip, Mark Donovan of HomeAdditionPlus.com shows us how wire a combo outlet with power.

Craving cookies but don't want to turn your kitchen into a sauna? Don't fret. Just turn your car into an oven! Watch this video to learn how to bake cookies on your car's dashboard.

Everyone gets cut every once in a while, but sometimes those cuts can be more serious than expected. It could turn into severe bleeding, and there's a certain way to deal with this type of bleeding in a victim. How would you treat someone who was bleeding severely?

Thawing frozen food on the countertop or in warm water may put your family at risk from food-borne bacteria. Keep them safe by following these methods.

There's nothing more maddening than opening the office fridge and discovering your lunch is gone. Put an end to the stealing with some of these strategies. This video will show you how to deter coworkers from stealing your lunch.

Three hundred people die every year from carbon monoxide poisoning. Don't risk being a part of that statistic.

Learn how to do speed full sit ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

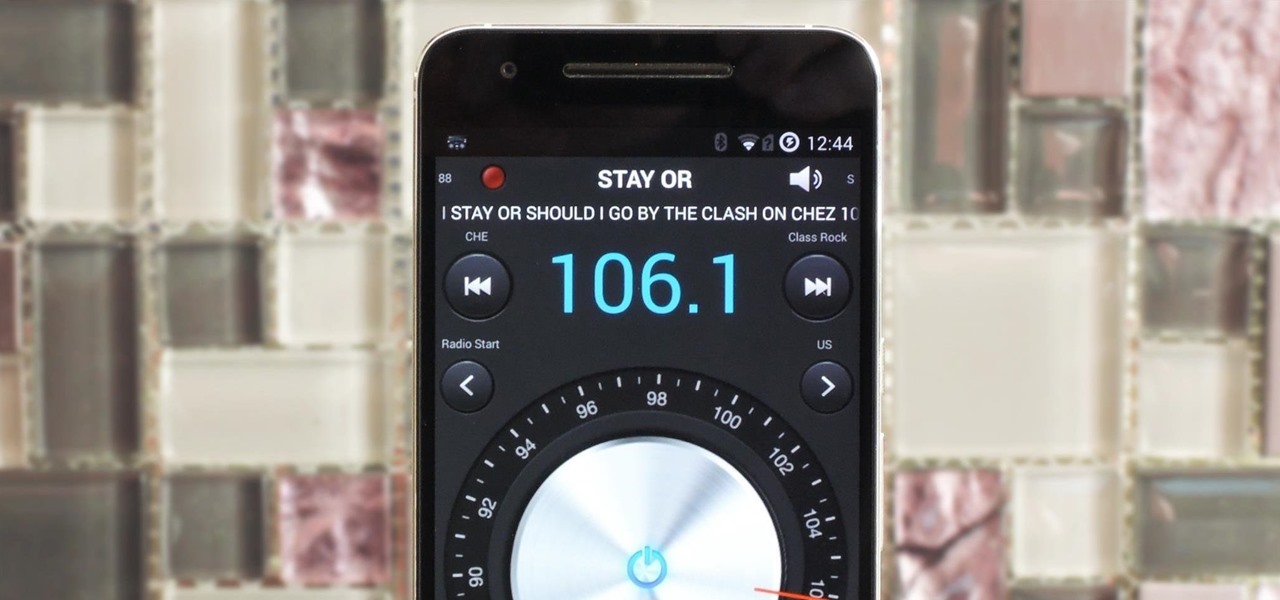
Android smartphones have all sorts of connectivity chips built in, including Bluetooth, Wi-Fi, GPS, NFC, and mobile data. But what about AM or FM radio, two of the most common methods of wireless communication?

You're a committed environmentalist but you love your candles. What are you to do? Did you know that you can recycle your candles? There's bound to be stuff left over. Just watch this video and learn!

Purchase the necessary equipment for this project. Pumice stones can be purchased at any beauty supply store. Chlorine can be purchased from any household supply store. Sodium bisulfite can usually be found at hobby stores. Obtaining the industrial washing machines for personal use is the hardest step. Call local cleaners to see if they will allow you to use their machines. Soak the pumice stones in chlorine overnight. This will allow them to soak up the bleach and create a good absorbency fo...

Ever wanted to know how to disable an attacker? The trick to getting away from an assailant – even one who's bigger and stronger than you are – is to hit 'em where it hurts.

Testing products for a living is a bit more complicated than it sounds. You Will Need

Thanks to modern "smart phones" and the internet, media by the people, for the people is finally a reality. Here's how to use your phone to be a mobile journalist.

Everybody knows it really shouldn’t matter, but sometimes entering a school cafeteria without a lunch mate can seem like walking the plank. Here’s how to survive the stroll.

Lose weight while sitting on the bus, train, or in your car with these stealthy moves. You Will Need

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

The no scalpel vasectomy has been reported to reduce the risk of pain, bleeding and infection. It can be performed under local anesthesia. Dr. Bird demonstrates his standard technique for a how to perform no scalpel vascetomy: lidocaine infiltration, skin penetration, vas isolation, electrocautery dissection, partial fixation, luminal cuaterization, clip application, and closure.

Dr. Aaron Katz encourages men to be proactive about prostate health and getting screening, paying attention to risk factors and taking supplements that may prevent prostate cancer.

Dr. Aaron Katz offers an herbal approach to prevent prostate cancer, based on the results of a study that proved Zyflamend blocked cancer from forming in men at risk.

Drone mishaps, such as the collision that scratched a military helicopter in New York, are becoming something of an everyday hazard.

One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.