
How To: Dice an Avocado in Seconds — Without a Knife
Avocados are one of the most universally loved foods, yet a lot of people avoid them because they can be a hassle to cut, especially if you're trying to make cubes.


Avocados are one of the most universally loved foods, yet a lot of people avoid them because they can be a hassle to cut, especially if you're trying to make cubes.

We're already glimpsing the future when we look at mixed reality through a headset, but is the real evolution of this technology something that will exist as part of our bodies? As intense as that may sound, TechCrunch's Jay Donovan offers compelling reasons why it's not such a crazy idea:
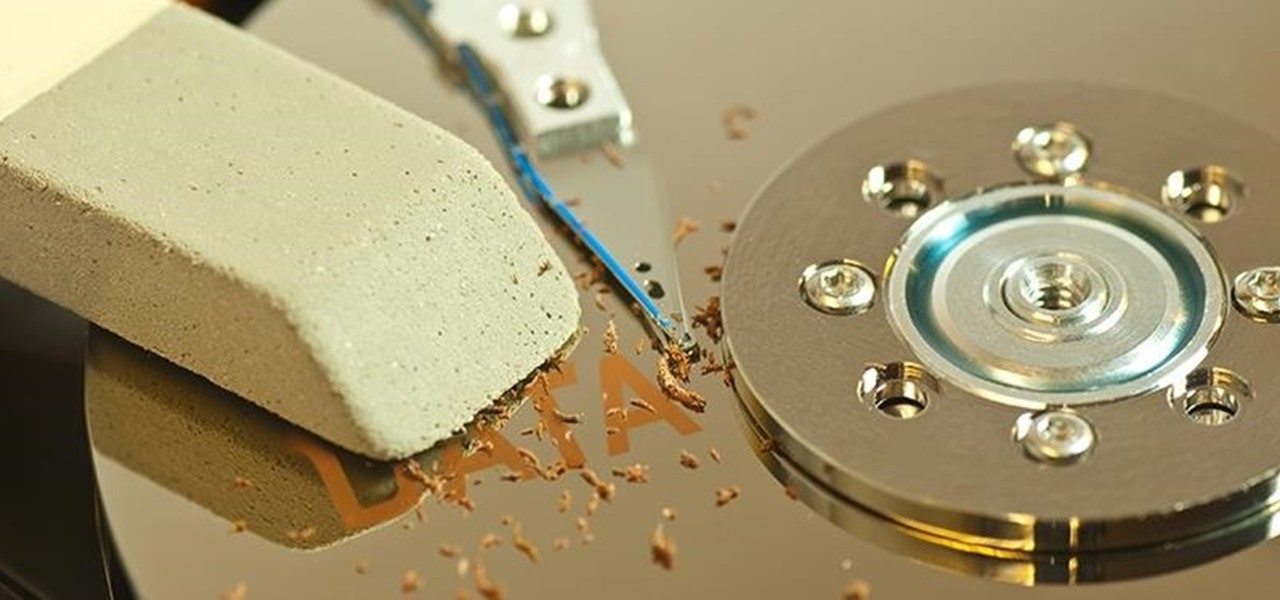
When you delete a file, Android doesn't actually remove it from your storage drive—instead, it simply marks that space as empty and pretends the file doesn't exist anymore. But deep down inside, the file that you originally wrote to that location is still physically there, at least until you randomly happen to save another file on top of that same spot.

Using a fingerprint scanner to keep intruders out of your phone might not be as secure as you think. Two researchers from Michigan State University, Kai Cao and Anil K. Jain, developed a relatively cheap and effective way to beat fingerprint readers, and successfully tested their method on a Samsung Galaxy S6 and Huawei Honor 7.

OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.

Hello, *Note This is my first how to post on here, so please correct anything that I have missed and let me know if anything I explained is unclear and I will try to clearify. Also I am a NOOB when it comes to this art, so I might have missed something, if so please inform me so I can better myself*
How to do an NMAP scan on Armitage to find IPs within a certain range. Armitage is a gui interface of Metasploit, and advanced hacking/exploiting program. It can be downloaded from http://metasploit.com/ and http://fastandeasyhacking.com/ and you will need NMAP. http://www.nmap.org/

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

When security firm Zimperium discovered Android's biggest security risk in years, it sent shock waves through the ecosystem. As a result, Google, LG, and even Samsung decided to change the way they issue updates to their devices, by pledging to release monthly security patches to plug up loopholes exactly like this one. Yeah, it's that big of a deal.

White rice is cheap, filling, and tasty. No wonder so many countries in the world rely on it as a mealtime staple, including most of East and Southeast Asia. Alas, because of its relative lack of nutrition and its high calorie count, consuming lots of white rice regularly also puts people at risk for diseases like diabetes and obesity.
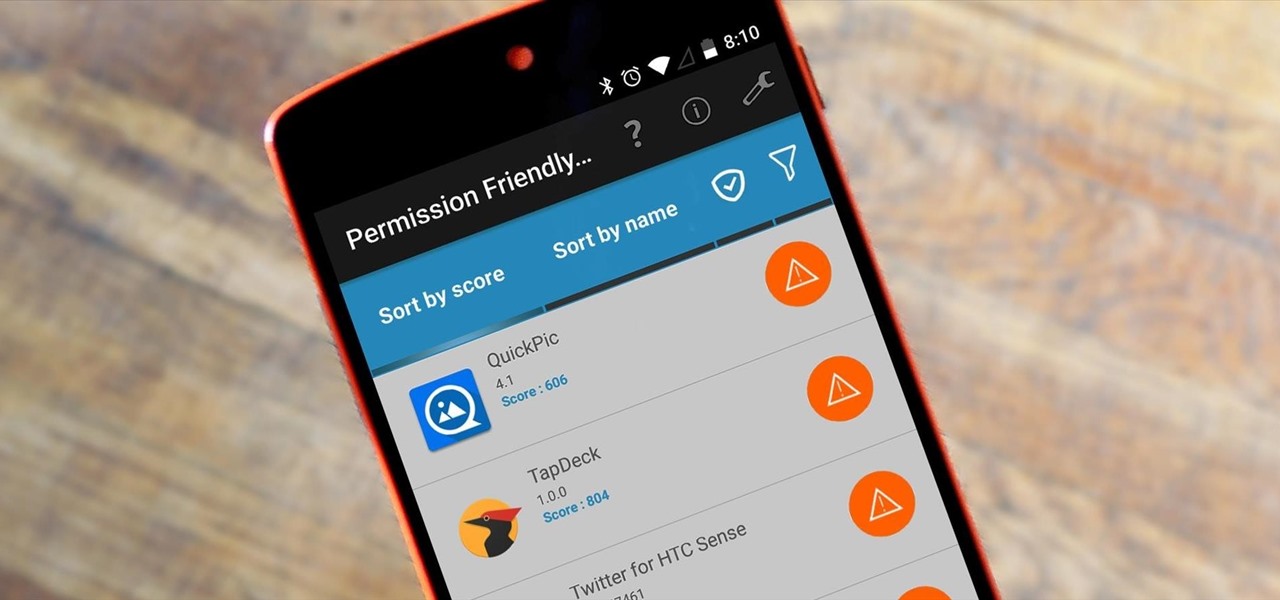
Android's permission system doles out access to certain system-level functions. Without it, our favorite apps wouldn't be able to perform their most basic operations. Picture a camera app that didn't have permission to access your camera sensor—now that wouldn't be much fun at all.

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

Whether you use a third-party keyboard or the stock offering, your Samsung device keeps a history of the last 20 words you copied on its clipboard. Samsung added this feature to Android to help make multitasking a bit easier, but if you use a password manager like LastPass, this feature quickly becomes a gaping hole in security. While you're copying and pasting your various passwords, the last 20 of them become freely available to anyone that gets their hands on your device.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.
Hello everyone. The red ring of death of Xbox 360 has been a huge problem since the beginning of Xbox 360. Many gamers like me have faced this problem and the red ring of death (RROD) is one of the biggest reason behind all the rant on Xbox 360 gaming console.

There are so many mods we can apply using a custom recovery. From themes to bug fixes and feature ports, a typical rooted user spends a decent chunk of time in TWRP Recovery.
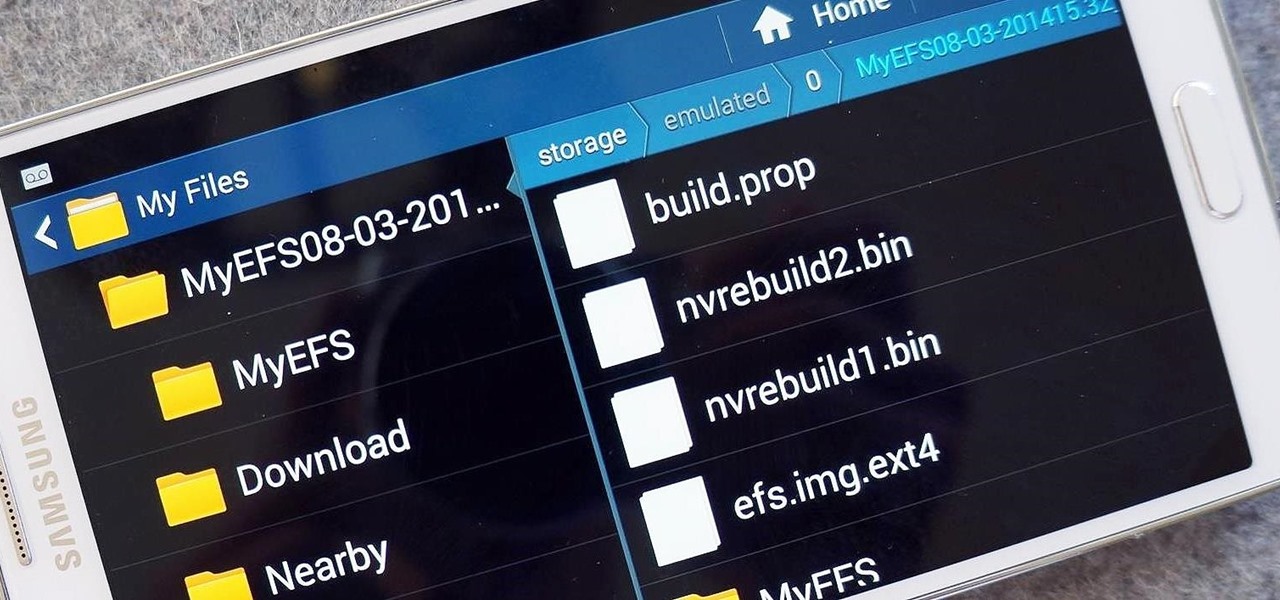
The options for customization are virtually endless when you're rooted and have an unlocked bootloader and custom recovery. However, there is always risk involved when flashing new mods or installing new ROMs. I always make backups in case something happens, but when I'm testing certain mods out, I sometimes get a damaged EFS partition.

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.
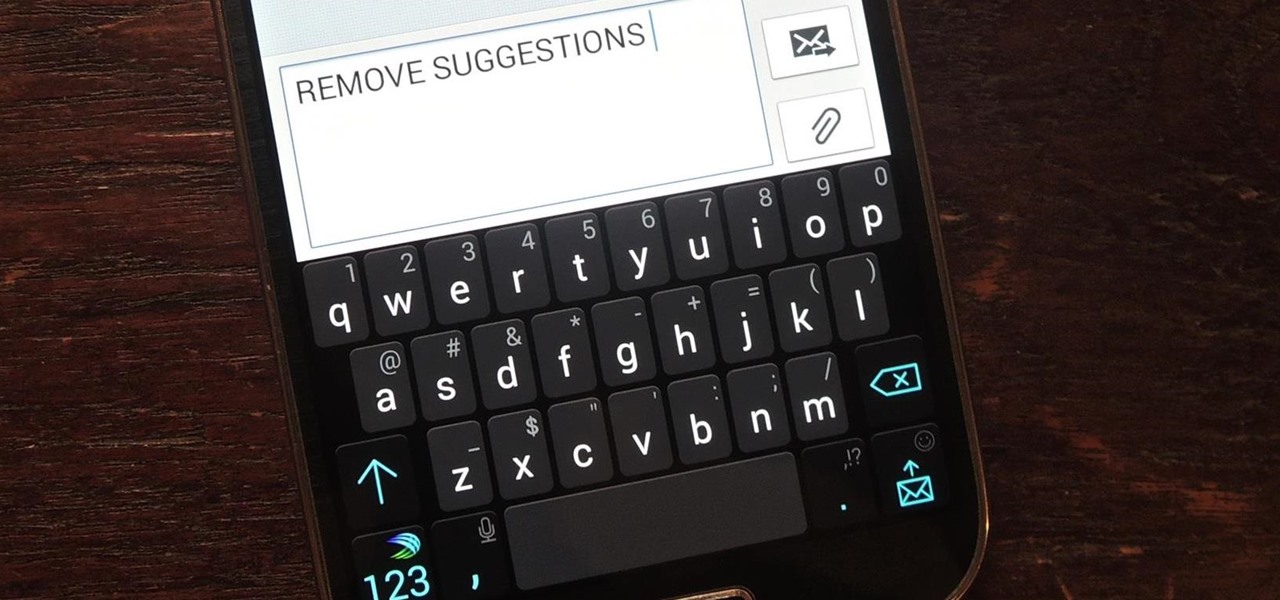
Auto-correction is a double-edged sword if I ever saw one. It's great because I'd have an abundance of typos without it, yet it's extremely frustrating (and embarrassing) when it doesn't actually work. Just take a look at the very recent example below from Breaking Bad star Aaron Paul. Funny for us, embarrassing for him. I have a particularly difficult time typing on small keyboards (i.e. fat-finger syndrome), so disabling auto-correction on my Samsung Galaxy S4 is a no-go. I'm willing to ris...

Copy and paste keyboard shortcuts are beautiful gifts from the gods, and any website that blocks such an offering can burn in hell. But really, Cmd+C and Cmd+V (Ctrl+C and Ctrl+V for Windows folks) are second nature to most of us, so it's very frustrating when sites like PayPal don't let us use them.
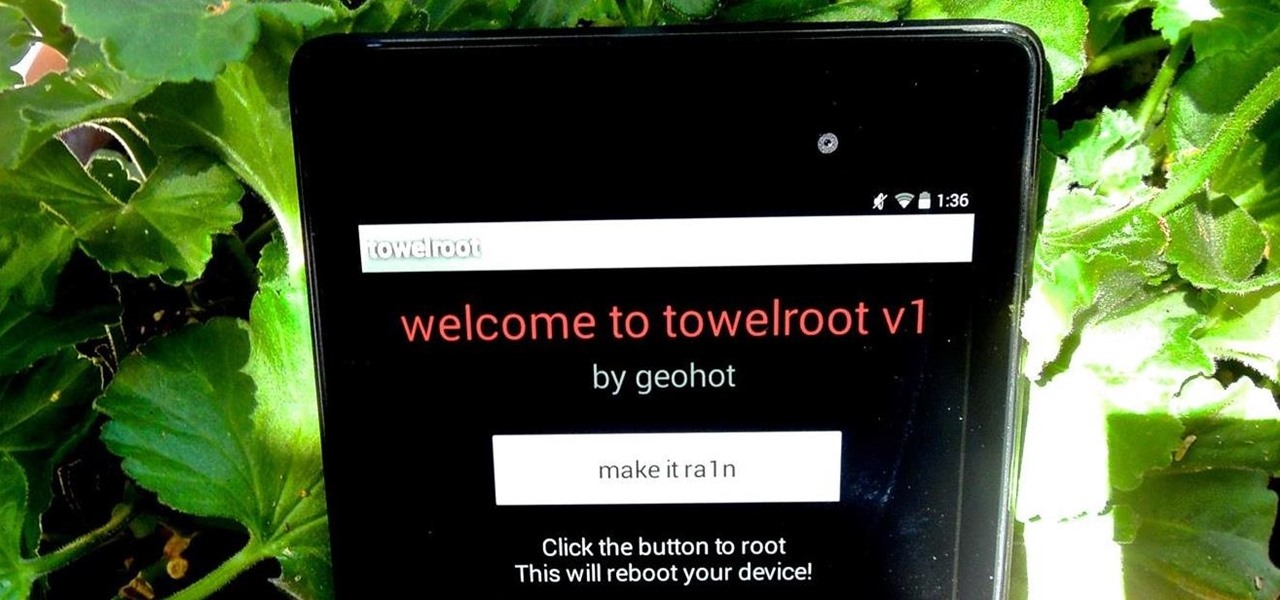
Rooting your Nexus 7 tablet is now easier than ever. Previous rooting methods required connecting your tablet to a computer and using any one of a number of programs and/or ADB commands. Now, it's as easy as downloading an app on your phone and tapping one button.
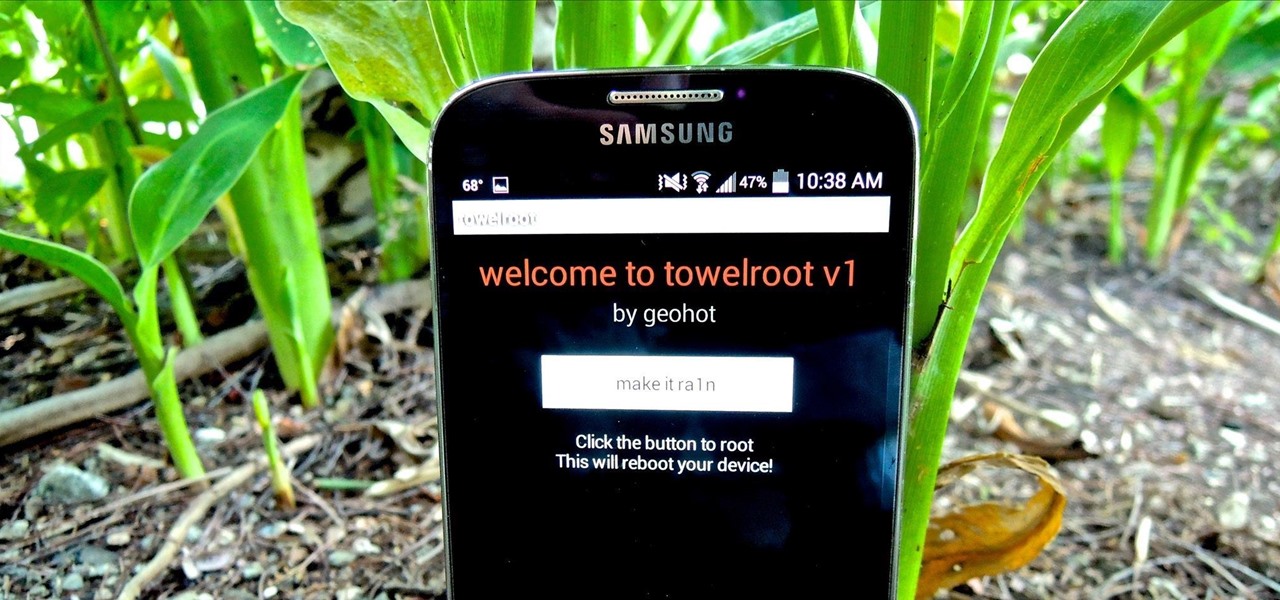
Something pretty awesome happened over the last couple of days. George Hotz, better known as Geohot, the infamous hacker known for jailbreaking iOS and exploiting the Sony Playstation 3, has brought joy to owners of just about all Android smartphones and tablets, especially those on AT&T and Verizon.
In a era where cyber security is becoming increasingly important, Comcast has decided to use its customers' routers to provide hotspot access to the public. A new program, outlined by Dwight Silverman over on the Houston Chronicle website, seeks to provide Xfinity customers with city-wide Wi-Fi hotspots by using, well...other customers' wireless routers.

While living alone, I grew to enjoy cooking. Not only was it necessary to my existence, but it was cheaper than eating out. One thing I really came to love was garlic, especially its smell. If a recipe didn't ask for it, I added it anyways.

It's here... Update: May 1, 2014

Adding water features to your garden can help to create an enviroment that more closely resembles nature. The sound of a trickling fountain can make your garden feel more peaceful and relax. Paul Tamate, a leading landscape designer working with water features and Asian-inspired garden designs in San Francisco says, "design spectacular water features as the centerpiece of gardens that serve as retreats from modern life."

Hopefully you never have to deal with a grease fire, but if it happens, how you handle it is important. A grease fire isn't like a regular fire, and trying to put it out the same way can make it worse. Grease fires are caused by letting oil get too hot, so the best way to prevent them is to never leave your kitchen unattended. Oil smokes before it burns, so if you see your pan start to smoke, take it off the heat before it has a chance to catch fire. If you're outside grilling, you can add a ...

There's no shortage of ways to filter water, but it doesn't get much simpler than this. Researchers at MIT have found that you can turn dirty water into drinking water with nothing more than a stick.

Rock-hard ice cream is the bane of my culinary existence. If I try and scoop it out with a spoon, the spoon invariably bends. If I use a traditional ice cream scooper, I end up with a torqued wrist and one or two pathetic curls of ice cream for my efforts.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

I can be pretty forgetful. If there's something important to remember, I need to jot it down right away or risk losing it forever.

It's always the snack you're most looking forward to that ends up being moldy when you open the fridge to grab it. Always. That slice of leftover pizza or chunk of cheese you've been thinking about all day? We've all been there. What separates us is how we choose to deal with it. Personally, I toss anything that has even the slightest hint of mold, but not everyone errs on the side of caution. Some people don't mind the risk and just cut off the green or fuzzy parts and eat the rest.

Drilling holes in wall tiles is a fairly easy skill to master once you know how. Follow these simple steps on how to drill a hole in a tiled wall for a hassle free experience.

A lot of computers come with a ton of pre-installed software from the manufacturer, some of which you need and some of which you could most certainly live without. And over time, you may have downloaded and installed a bunch of programs and apps that you probably can't even remember. Now, you could go ahead and uninstall everything that you don't think you need, but then you run the risk of removing something that could really mess up the system. When I open up my Programs folder, I feel like...

I had my wallet stolen a few months ago, and I knew I would never see it again. My biggest gripe was not the credit cards in there, since they're easily cancelled, but the gift cards. I had some pretty good gift cards in there, and there's no way to get those back.

For the most part, nobody makes money off of Facebook. Sure, some people make a living by updating pages for businesses and celebrities, but hardly anyone gets a dime from the site itself.

Not many people fly kites anymore. Most of us don't have the patience or attention span because, let's face it, we're used to smartphones and other gadgets that have games and apps galore to entertain us. Heck, you can even fly a kite on them if you really want.

Here's a technique I used to whip up a batch of super cheap and easy to make smoke flares! WARNING: Ignition of an incendiary or explosive material may not be legal in your area, so check local laws before attempting. Use of this video content is at your own risk.

Maybe not water per-se, but with this simple technique you can turn one of the most abundant materials on earth into a highly explosive gas.

There is no better example of a risk-versus-reward scenario than jailbreaking your iPhone or rooting your Android phone. While both jailbreaking and rooting undoubtedly has its advantages, this possibility of something going wrong and you ending up with a 500-dollar doorstop is never too far out of mind.