Milking a cow can yield multiple gallons of milk per session. This video tutorial demonstrates how to milk a grass fed cow by hand, and provides ways to make your cow more cooperative throughout the process. All you'll need is a cow, a stool, and a patient work ethic.

This video shows the method of getting past blocked sites and opening them using proxy servers. The method shown is useful when the sites are blocked using another site. In this case it is 'www.lightspeedsystems.com'. It can be done using proxy servers. In the case shown it is 'treesniff.com'. The URL is typed and we choose the option of 'Continue to this website'. Press 'No' for the security information. After this the page of the proxy server is displayed. Type the name of the website you w...

In this video tutorial, viewers learn about nutrition that will help lose fat and gain muscle. Users learn about the meal they should consume after a workout session. The meal should be predigested to help recover muscles rapidly after a workout. The meal advised to digest is whey protein and a banana. The amount of protein consumption depends on the weight of the user. Users can choose to simply consume the protein with just water or by blending it with other nutritional sources such as the ...
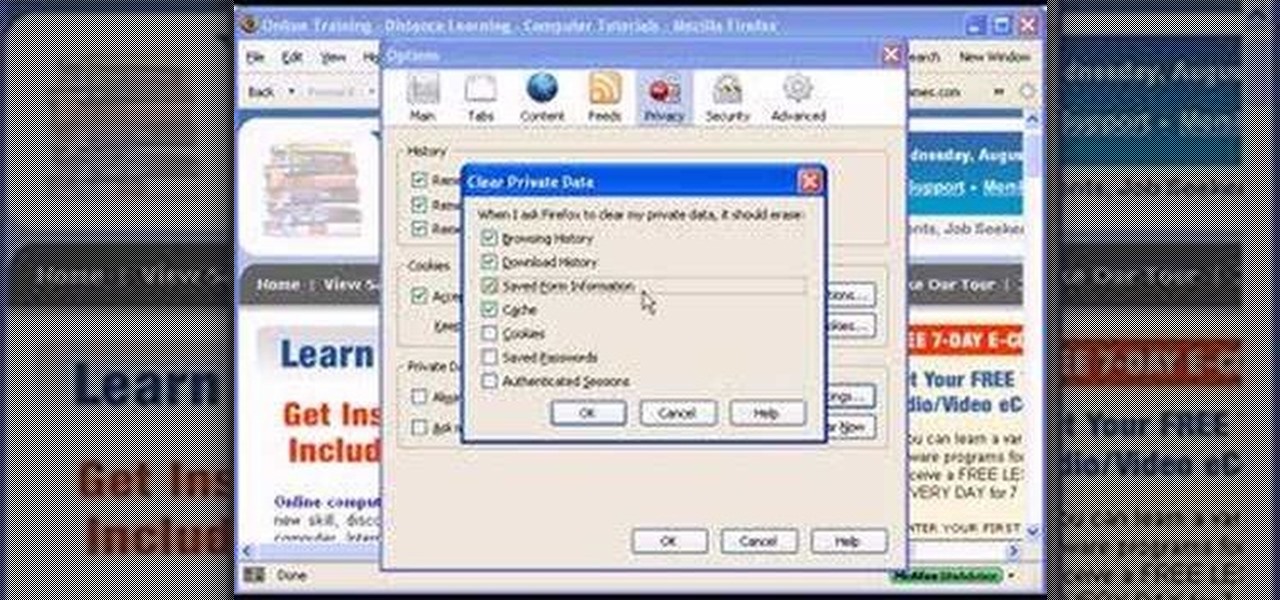
Steps to clear the cache on Firefox and delete unnecessary temporary files from your computer. In your Firefox browser go to TOOLS. Click on OPTIONS. Then go to PRIVACY tab. Click on PRIVATE DATA section and click on SETTINGS. Now you can clear the following items: browsing history, download history, saved form information, cache, cookies, saved passwords, authenticated sessions. Check what you'd like to remove, specially the cache option. Mow click on OK button. click on CLEAR NOW and click ...

Darin Steen of Major League Health explains how to lose weight with a healthy meal after a workout. What you put in your mouth composes 70% to 80% of fitness fat loss gain. Meals that you eat after intense workout sessions are very important. Eat a meal that is predigested and absorbed quickly like whey protein and a banana. Eat your meal 30 minutes to 60 minutes after your workout. For people weighing 120 pounds to 140 pounds, use 15 grams of whey protein and a half of a banana. For people w...

In this video Chef Jason Hill of Cooking Sessions shares his southwest sauce recipe which is used on burgers, sandwiches, salads and dips. For the southwest sauce you will require 1/4 cup of cilantro leaves, 1/2 a tomato, 1/4 onion, 1 Serrano pepper, 1/2 a teaspoon of cumin, 1/2 a teaspoon of kosher salt, 1/4 teaspoon of cayenne pepper, a cup of mayonnaise, a cup of sour cream and a clove of garlic. Add the ingredients into a food processor and grind it to a puree as shown. After that add the...

Looking to shed that baby weight? In this three part tutorial learn how Iris completely lost her baby weight in one year and got back to wearing her pre-pregnancy clothes before her baby's first birthday. In the three parts of this advice session, the following topics are touched on: details of Iris' weight gain & weight loss, how she did it, what routines she followed, and how she found her motivation.

This video tutorial is about Android, and no it's not a robotic creature, it's a software platform and operating system form mobile phones and PDAs. The Android system is based on Linux and was developed by Google and the Open Handset Alliance. Code is managed in the Java language, but can be written in C also, although C is not officially supported. A lot of the new cell phone and other mobile devices will be running off of Android, so know how to use it.

Want to get rid of neck pain? Then try using massage as a pain reliever. Follow along with this diet and health how-to video to learn how to massage pain in the neck. When massaging the neck it is important to focus on all sections of the neck like the lateral and anterior sides. With a few thirty minutes massage sessions you notice the pain in your neck start to go away.

Professional BMX rider Ben Snowden teaches you how to do a 540 on a box jump landing, quarter pipe, and vert ramp. He also throws down some extra moves at the end of the video tutorial in a bonus solo riding session. So, if you want to be an awesome BMX bicycle king, just learn how to do a 540 trick on a BMX bicycle. Ben Snowden will tell you all about it, but he recommends you already know how to do a 180 or 360 spin on your bike.

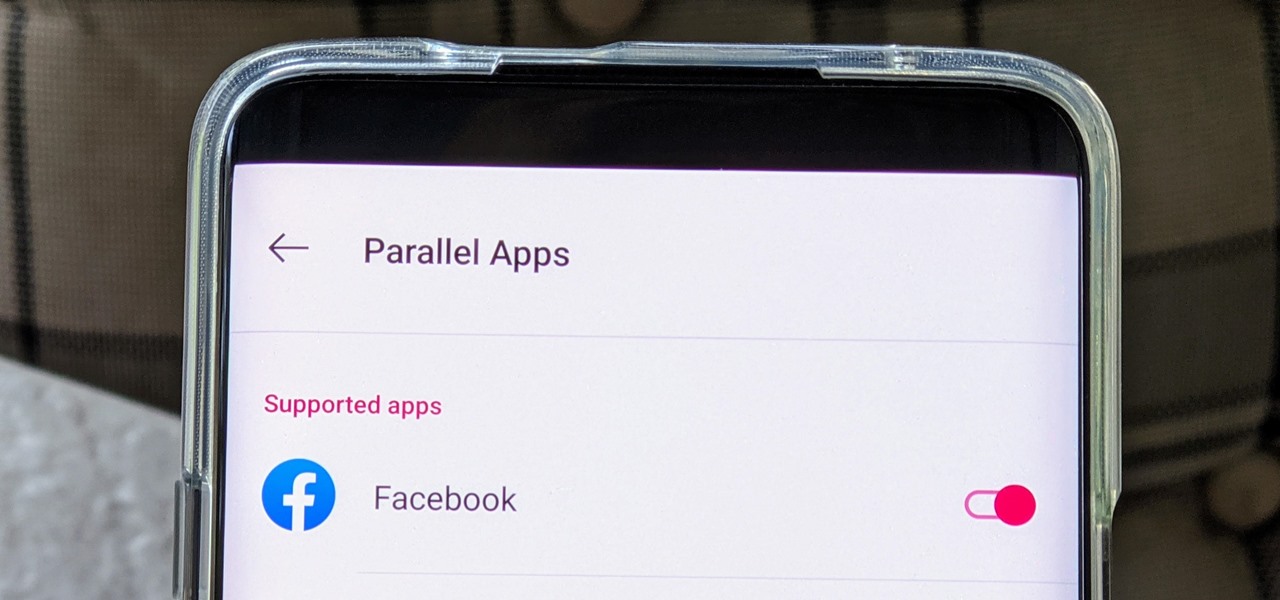
The Facebook app only supports one account being logged in at a time — but what if you need one for work and one for your personal life? That would normally involve logging out and logging in every time you need to switch accounts, but your OnePlus device offers a much better solution.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

After Apple unveiled ARKit 3 at WWDC on Monday, Unity Technologies wasted little time on ensuring its developers can take advantage of it.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

If you've been debating on whether or not HTC's new virtual reality headset, the Vive, is worth the $800 price tag, then you'll be able to find out for yourself soon enough.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

At the beginning of regular gameplay in Grand Theft Auto 5, you play the role of Michael robbing a bank in North Yankton with his accomplices—shooting police and evading a high-speed train in the process. While you do revisit North Yankton during regular gameplay in Los Santos, it's strangely unavailable for online play.

This instructional gambling video teaches you the basics of craps. Learn the rules and etiquette of playing the game as a beginner.

This gambling video shows you some strategies in placing your bets on the 6 & 8 in craps.

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

Who says Vegas is only good for gambling? This is a level-by-level walkthrough (on realistic difficulty) of Rainbow Six: Vegas for the PS3, XBox 360, and PC. A helpful voiceover commentary is included.

You aren't just born with broad Stallone shoulders and arms, gentlemen. Of course we know you wish you never had to work to get those tight, chiseled arms and shoulders, but even the best of the best - that's right, including Stallone - have to work what their mama gave them to keep in shape.

In this tutorial, we learn how to remove stretch marks with lasers. The laser treatment is the most effective for removing stretch marks. This will turn the purple marks lighter, and once they are silver/white, they will make those less apparent. The Affirm laser treatment is proven to be extremely effective to remove the stretch marks, and make them only noticeable under a microscope. It will take several sessions to drastically remove the stretch marks, but it will be worth it in the end. D...

This video provides a demonstration of how to beat the bosses of maps one through four of Epic Quest. The video game is an arcade style fighter where you lead teams of three creatures into battle. The first boss is a solitary enemy, easily taken down. The boss pair on map two is only slightly more challenging. The three squid creatures on map three are easily taken down, if you are level 31. On map four, you should be more careful. This boss team requires the use of several potions and healin...

While any form of gambling is set up to make you lose, there are some tips and tricks, shown in this how-to video, to help even the playing field. Penny arcade slots are a reasonable place to start, as the stakes aren't too high, so neither side (you or the arcade) has that much to lose. Watch this video conning tutorial and learn how to beat an arcade penny slot machine.

In this photography tutorial video, the self-appointed "Prince of Cheap" shows you how to use natural light and enhance it with continuous fluorescent light for some really killer headshots that stand strong! This photographs are really strong. In this 5 minute clip, David explains his thought process while you watch one of his garage shoots that lead to great quality and many "How'd he do that?" exclamations. This time you'll be able to see him on his session! How much can you learn in 5 min...

This gambling video show you some of the worst bets to make on a craps table and how to avoid them.

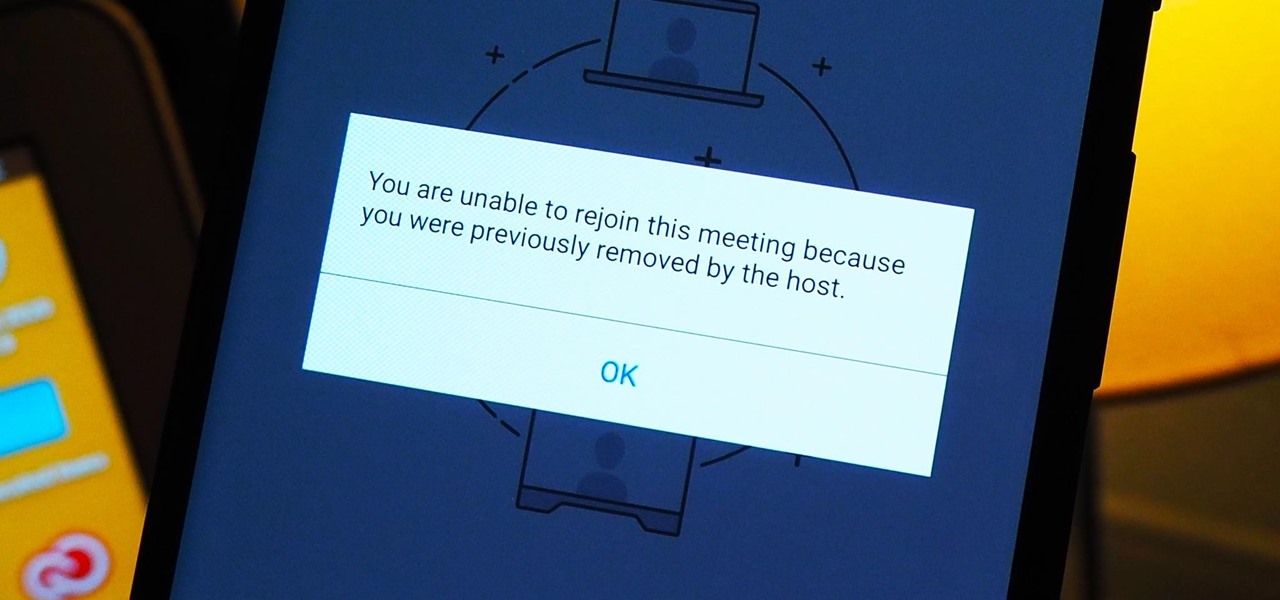
As more and more people use the video conferencing service Zoom, the chances of trolling behavior and attacks only increase. But it's not just "Zoombombers" you need to worry about. A heated discussion between family, friends, or colleagues could turn sideways real quick, and sometimes the best course of action is to remove the participant from the group video meeting altogether.

The business world is currently figuring out how to deal with the coronavirus crisis, with many offices opting to work remotely for at least the next few weeks as a safety precaution. Predictably, this has thrown remote meeting software back into the spotlight, especially augmented reality solutions.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

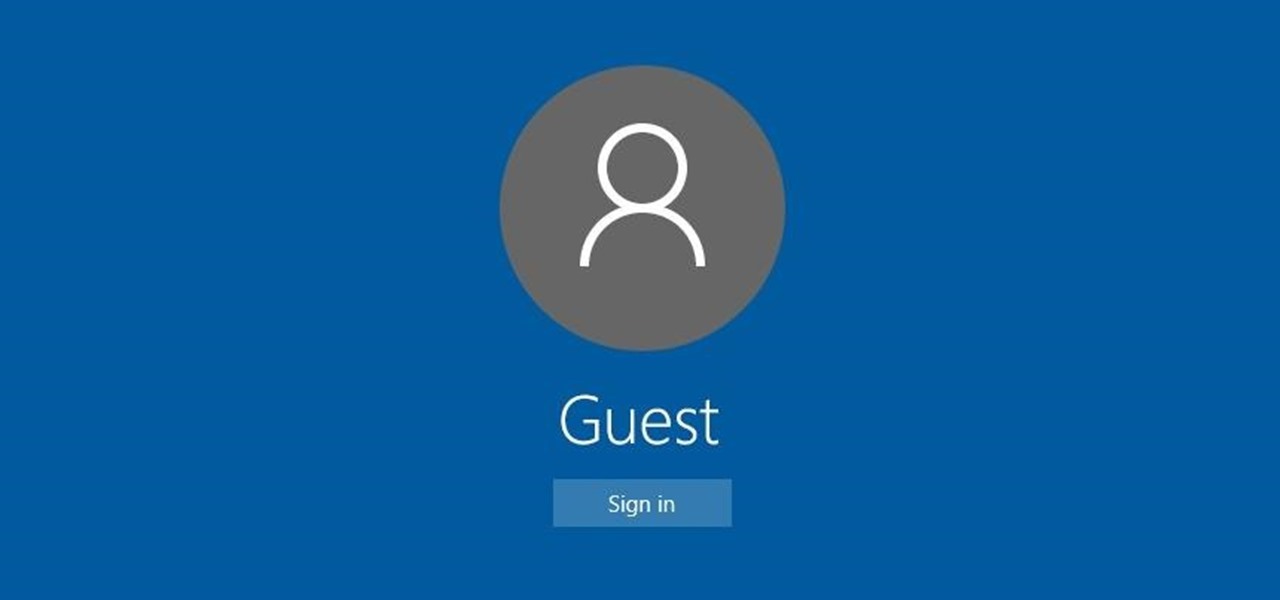
For reasons unknown, Microsoft decided to change the way the Guest account feature in the new Windows 10 operating system works. In previous versions, the Guest account feature allowed you to set up a limited account for other users so they don't have access to your important documents and settings. Now, the process requires assigning an email to a new account and configuring share settings.

Heavy Water & Light Ice Experiment. What happens? Ice floating over vegetable oil but it decreases in baby oil.

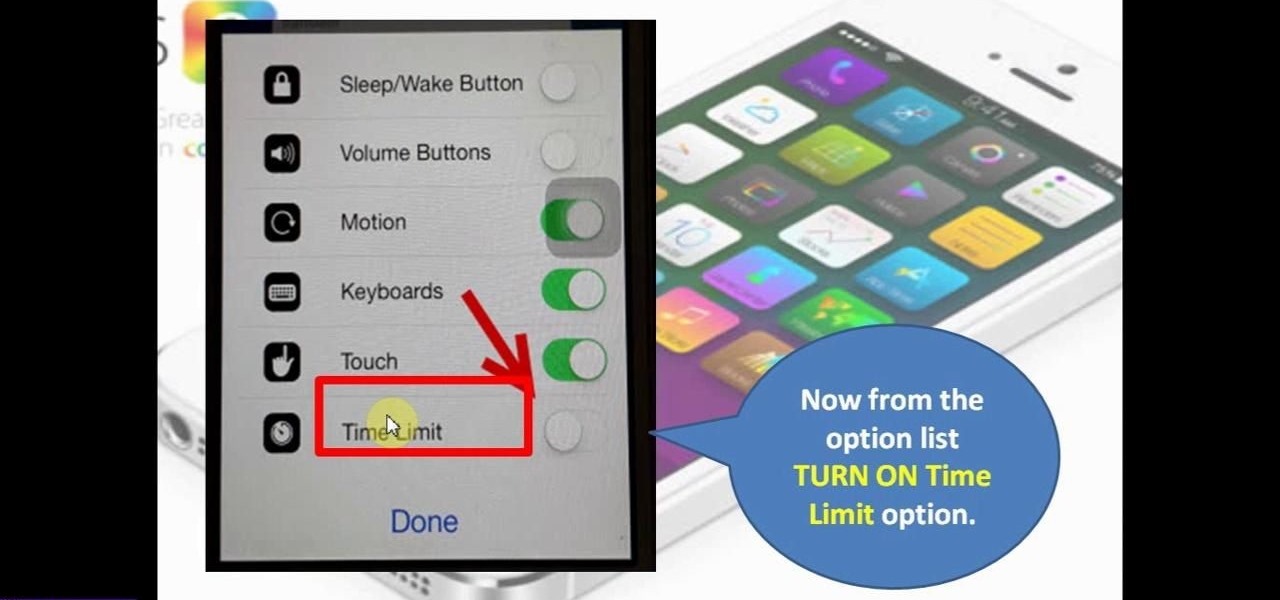
This video will show you how to set time limit for your children games in your iPhone or iPad. This will restrict children from excessive use of your iPhone or iPad. When this time limit is over, the game your child is playing will be stopped automatically. They will not be able to continue playing games until you start a new session for them. So please watch the video and employ it in your phone.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

How many times have you heard someone utter the phrase, "Now, let's break into groups"? From classroom discussions to workplace think tanks, gathering into groups to generate ideas is common practice. These forced get-togethers are intended to encourage creativity and unique thought, but they can actually do the opposite. More often than not, group brainstorming is annoying rather than encouraging, and these group sessions can actually be detrimental to your productivity. Getting together har...

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.