
How To: Trim spare ribs into St. Louis style ribs
Trimming spare ribs into St Louis style ribs is demonstrated in this Barbecue Web video.


Trimming spare ribs into St Louis style ribs is demonstrated in this Barbecue Web video.

This video tutorial takes a look at how to create layers in Photoshop CS2 that build up to your signature. Then we'll pop over to Adobe ImageReady to put the finishing touches on animating that signature so that it can be used on the web or in your email application. Check out this Terry White's video now!
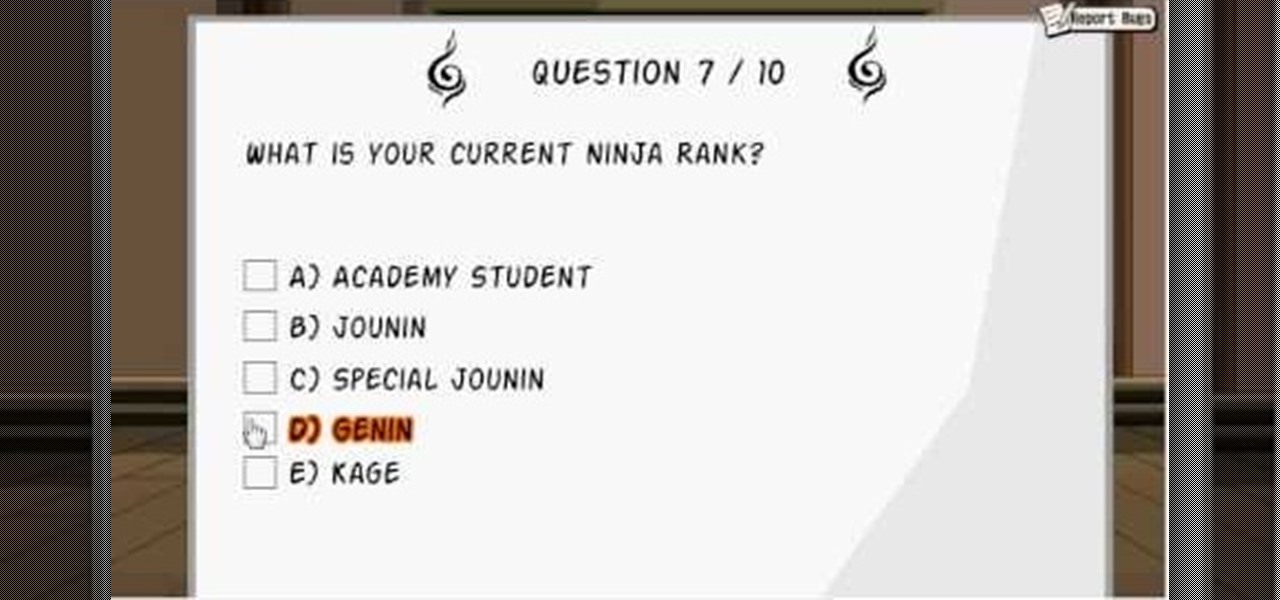
The chunin exam. It's one of the hardest parts of Ninja Saga. Can you pass the test? Or do you need a little help on this exam?

Ready to make a statement in your town and get involved? Check out this tutorial and learn how to run for mayor. If you can't beat city hall, why not join it?

There's nothing more disappointing than finding yourself all packed and ready to travel when you find your flight has been canceled. You can make the best of the situation by finding out just what you are entitled to or how to best ameliorate the situation.

You have a purebred, make it official. With a few simple forms your purebred dog can be a member of the American Kennel Club and carry on the traditions of and gain access to this exclusive organization. Your dog can have an official pedigree.
There's a great new web game called Epic Duel out on the internet, and everybody's playing it, but not everybody's hacking it, except you! Outshine them all with this EpicDuel cheat with Cheat Engine 5.5.

If you've been thinking about changing careers and you have just a little bit of time, The Ultimate 2021 Web Developer & Designer Super Bundle may be just what you need. This is also the perfect time to get it because it's on sale for $34.99, which is 98% off the regular price of $1,886. You'll get 14 courses that offer 39 hours of content on HTML, JavaScript, CSS, and more.

SEO is the name of the game. If you want your business or brand to succeed, ranking on the front page of Google is a boon. Getting to the front page of search engines takes work, but it's not impossible when you master SEO best practices.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

Being stuck inside for the near future is less than ideal, but at least you have the world of eLearning to sharpen your skills while you kick back on your couch. Case in point, The 2020 Premium Learn To Code Certification Bundle has all the training you need to start coding like a pro right at home, and it'll only cost you $39 today.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

Filmed in what appears to be a single continuous shot, war film 1917 is now the front-runner to conquer the Best Picture category of the Academy Awards after bringing home the Golden Globe for Best Motion Picture in the drama category.

What better band than Pink Floyd, the pioneers of psychedelic and progressive rock, to show the music industry how to reinvent album art for the augmented reality age?

Smartglasses from Apple have become the holy grail of augmented reality, and 2020 has been the rumored time horizon for the product's arrival for the past two years. The latest analyst report sheds more light on its potential debut next year.
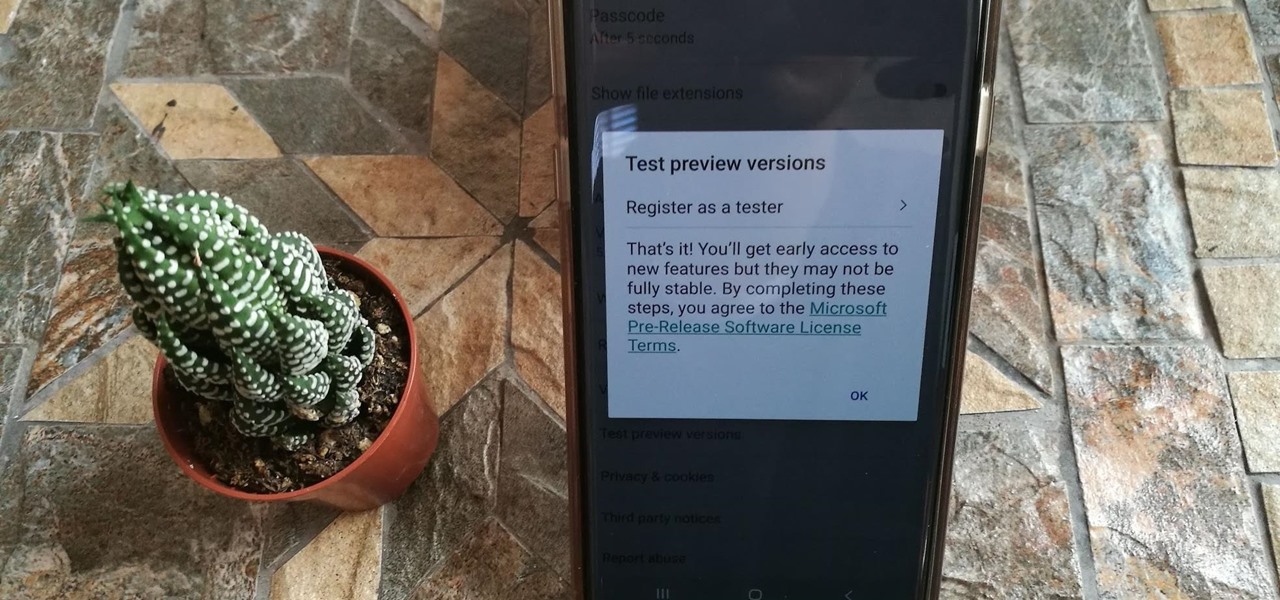
OneDrive has some really cool features, like being able to lock your files with a fingerprint. If you want to be on the forefront of these new features, you can sign up to the OneDrive beta testing program to get new feature before anyone else.
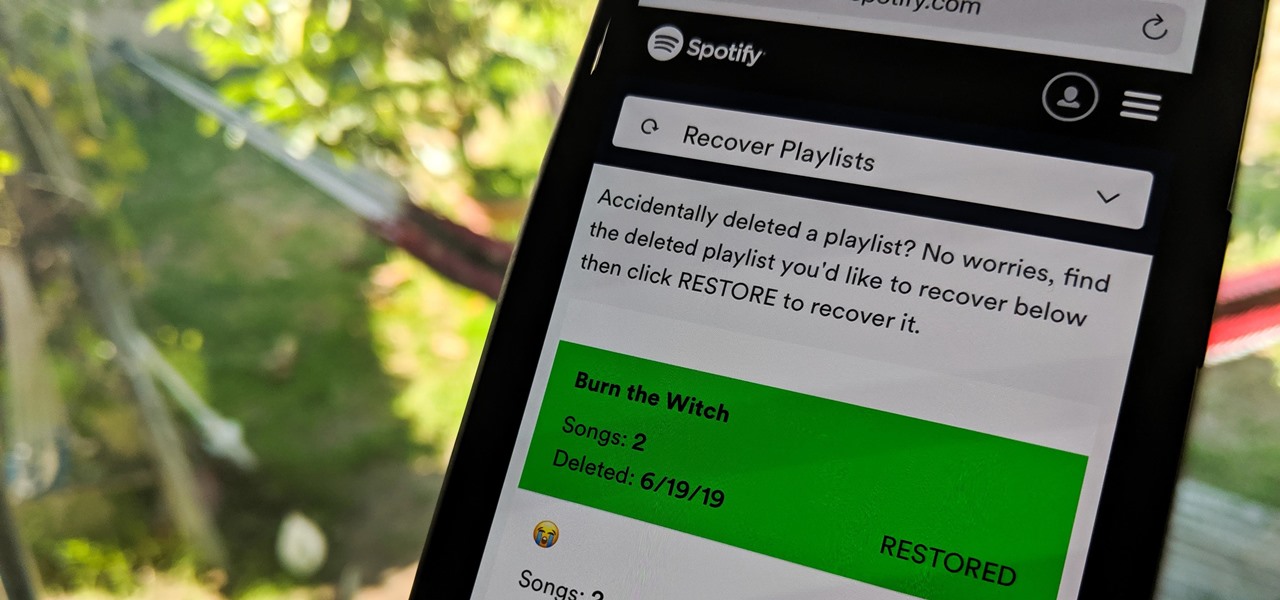
Absentmindedly or accidentally deleting your favorite Spotify playlist — which you spent hours or even days meticulously crafting — may seem devastating because there's no obvious way to bring it back. However, there is a hidden setting in the popular streaming service that can help you recover deleted playlists — you just need to know where to look.
Augmented reality platform maker Zappar and its marker-based augmented reality technology have been around well before Apple and Google brought markerless AR to mobile apps.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

If you've ever wanted to barge into Jerry Seinfeld's apartment like Cosmo Kramer, you can now do so without having to book a ride on the Peterman Reality Tour.
Nearly a year to the day after the unveiling Magic Leap One, Magic Leap has dropped another update to the Lumin OS that runs the device.
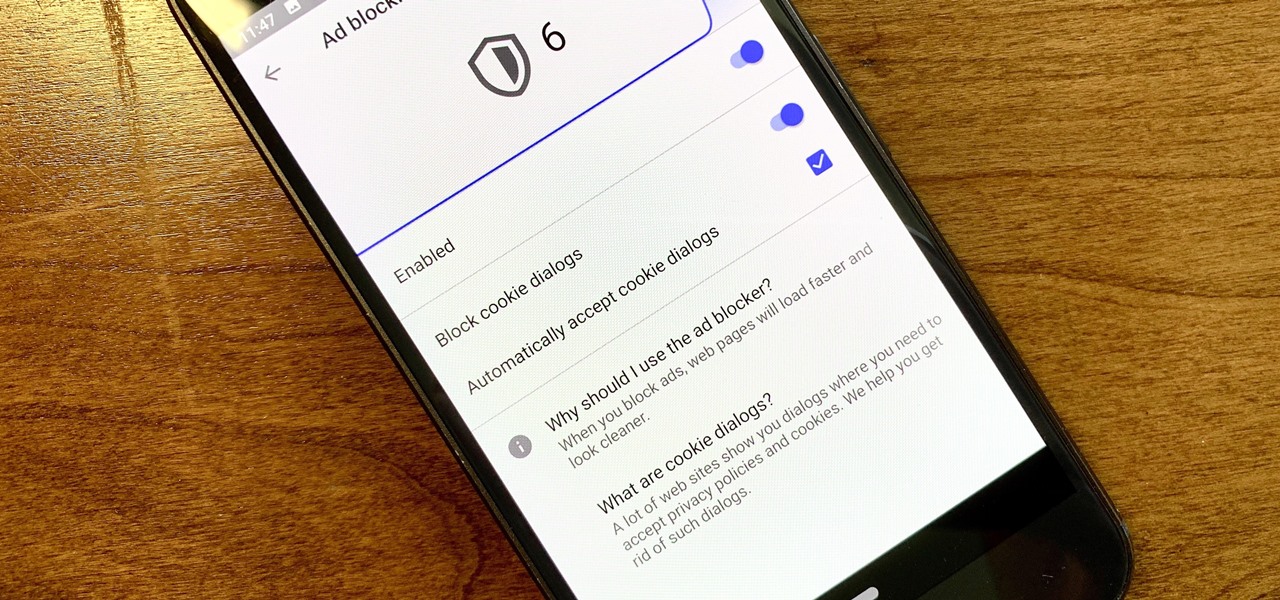
Ever since the GDPR was implemented, it seems every website on the internet needs to inform you of how its privacy policies have changed. If your web browsing experience has been marred by a constant barrage of these cookie pop-ups and privacy dialogs, you should know there's an easy way to block these web annoyances so you never have to tap another checkbox or accept button again.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Developers can now publish augmented reality experiences that are viewable through the experimental version of Chrome and ARCore.

Electronics maker Epson is courting developers to its Moverio smartglasses with an updated software development kit (SDK) and integration with a web-based tool for publishing augmented reality experiences.
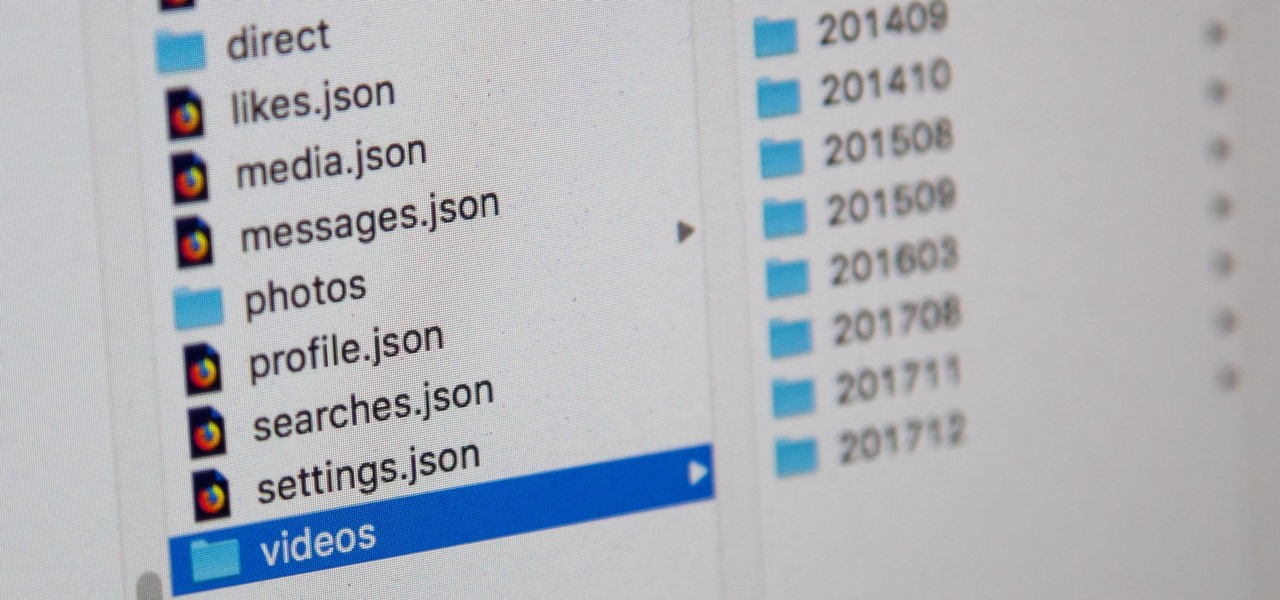
Facebook, parent company of Instagram, has allowed you to download photos and other account data for some time now, but the data request feature is also now available on Instagram to meet the GDPR data portability requirement in the EU — and it's available worldwide, not just in Europe.

With its recent acquisition of 3D gaming engine PlayCanvas, Snapchat parent Snap, Inc. appears to be preparing a challenge to the existing players in the world of game development, particularly in terms of augmented and virtual reality gaming.

The latest cosmetics brand to launch its own augmented reality try-on tool is Cover Girl, which introduced its browser-based experience this week.

There are over 3 million apps in the Google Play Store, all optimized for the small screen in your hands. While that number sounds staggering, there are still many online tools and websites that require you to use a mobile browser since app development is expensive. However, that's where Progressive Web Apps (PWAs) come into play, a cost-effective way to turn websites into mobile apps.

During its third-quarter earnings call, Apple CEO Tim Cook said that "AR is going to change everything."

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Before the release of the Galaxy S8, Samsung quietly uploaded one of their core TouchWiz apps to the Google Play Store as a beta. Samsung Internet, as it's called, has been a staple on all Galaxy devices for years now, but you can now try the browser on any Android phone.
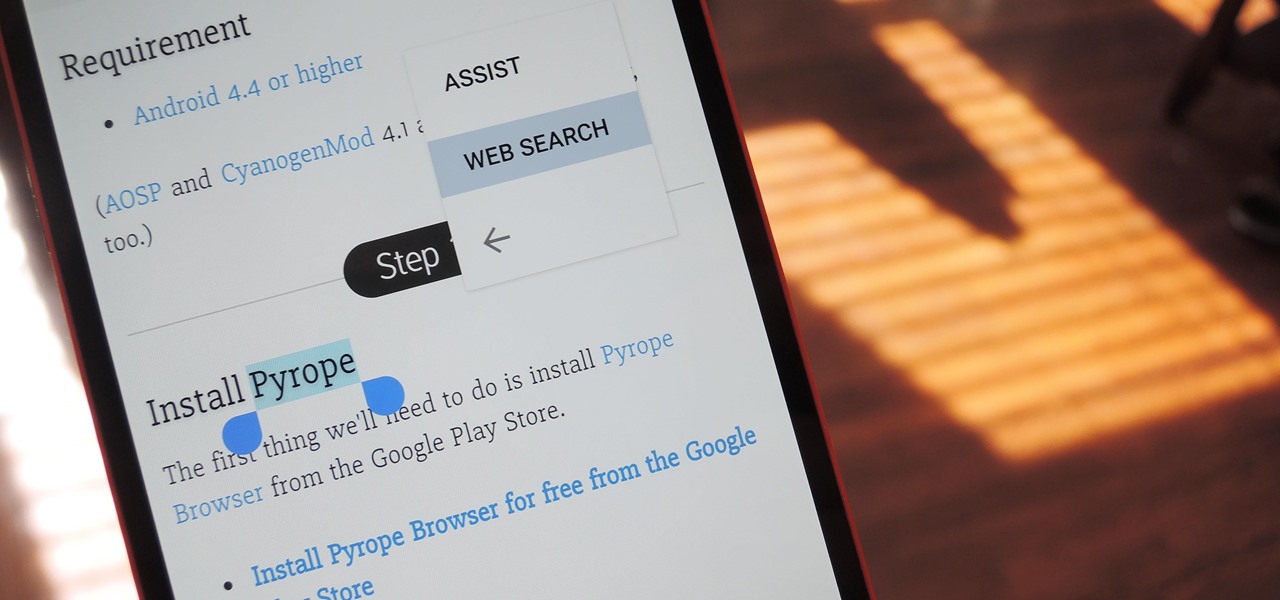
Chrome's text selection interface is pretty nice, but it could definitely use some improvements. For instance, when you're in Incognito Mode, you can't perform a web search for words you've highlighted. And when you're typing out a forum post or using any text input field, for that matter, there's no option to search or share any of the text you've written.
Mixed reality can give you the feeling that you've uncovered a hidden world layered into the physical one you already know. This can happen in so many ways, from a trading card that births a hologram or a first-person shooter with robots blasting through your walls. Xperiel—a California-based augmented and mixed reality company—wants to create a platform to make that a whole lot easier for developers.

Google is reportedly working on an iOS keyboard that brings key features to the iPhone, including Google's image and text search functions. (GIFs, yay!) According to The Verge, the keyboard has been in development and testing for months, and will act much like the Android version.

This Video is about my Trying a New Braid pattern for a Crochet Weave.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

I will Show you in this Video How I dust my Ends... PLEASE NOTE: