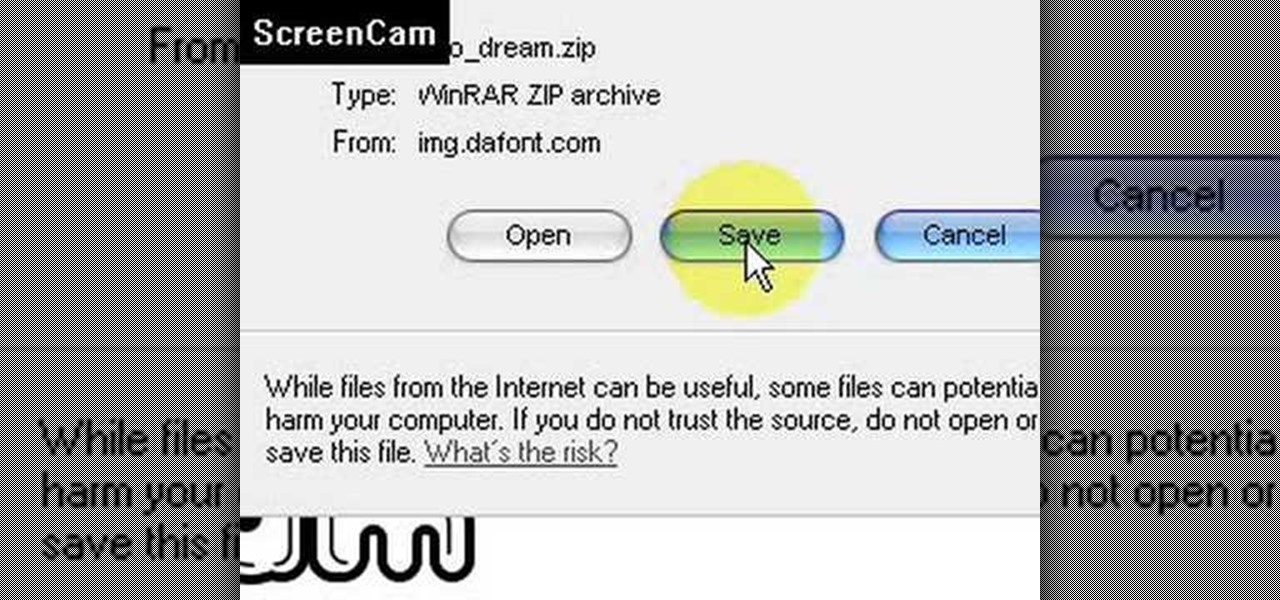
This video is about how to install new fonts in Windows XP. The first step that you will need to do is open your web browser then search for fonts. If you have found the site, just simply click on it. Then the next step is have a browse and look for the font you like. Once you have found the font that suits you best, just simply click the button "download" then save the file in your computer. Once you have saved the file in your computer, simply right-click the file and click on the "extract ...
Need help tracing an IP address to a location? Well, Tinkernut has a clear and effect way to help out.
This video tutorial from dproxisback presents how to download and install Handbrake DVD ripping tool.To avoid installation problems, carefully choose application version for each type of computer and operating system.Open your internet browser and visit http://handbrake.fr/?article=download web page.Choose correct version for your type of operating system (MacOS, Linux, Windows).Download and install the application. Run Handbrake once it's installed.Click File-Select Source. Browse for your f...

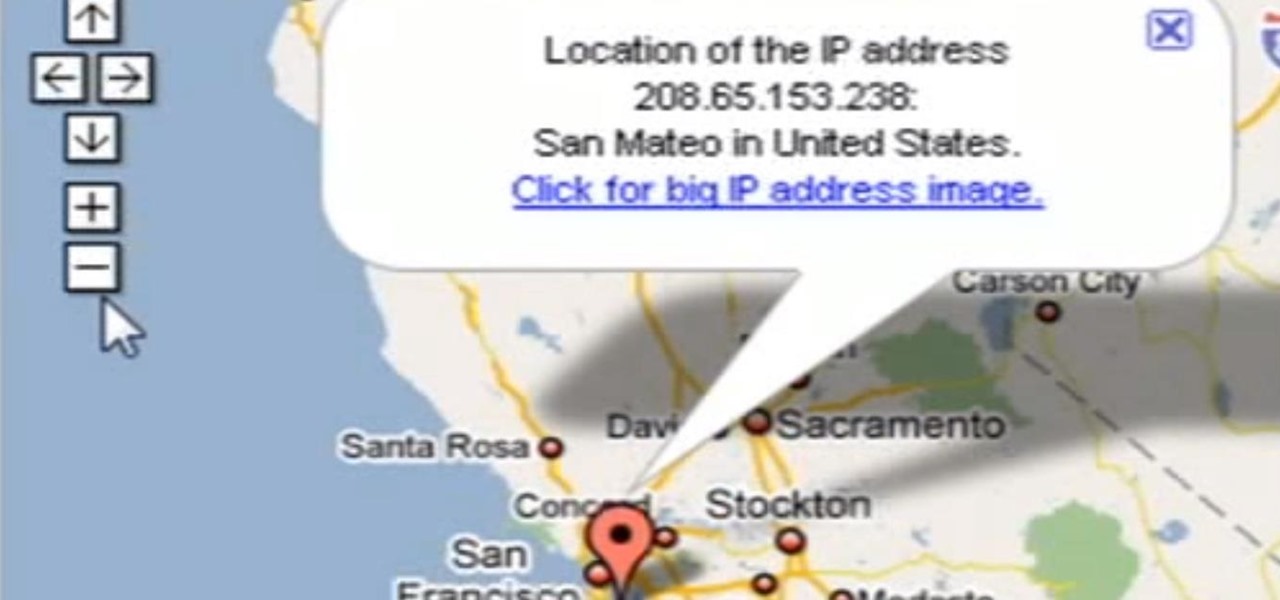
In order to access your wireless router settings in a Windows PC you need to use a command called ipconfig. The purpose of this command is to find out what your IP is. Go into the command console and use ipconfig to find out what it is but instead of noting down the IP address, we actually have to note down the default gateway values for the task at hand. Now all you need to do is open your web browser and insert the default gateway values from before into the address bar. By doing so you wil...
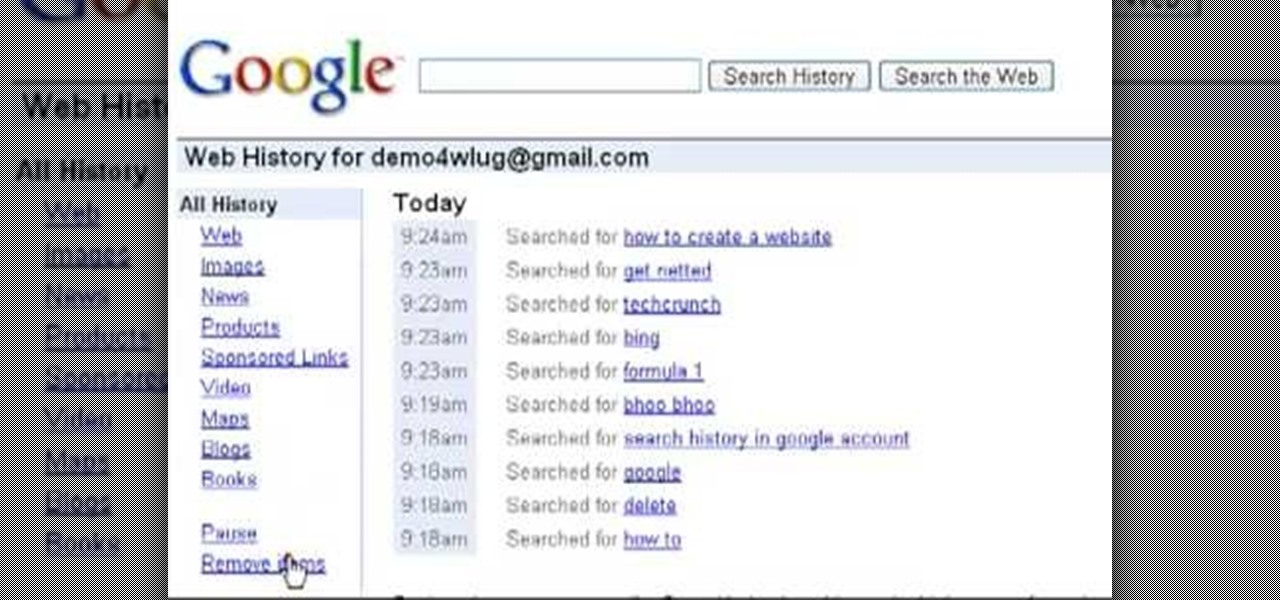
Want to clear the search history from your Google account? Well follow these simple instructions and return your history to the original settings! First log into your Google History Account at google.com/history. Next scroll down and locate "Remove Items" on the left hand side tool bar. Click on this. Next locate "Clear entire Web History" towards the top right of the screen. Then the final step is to click "Clear History". Follow through the tutorial video to get rid of all of the annoying s...

Learn how to delete your old Yahoo account from this video in simple steps. First open your web browser on your computer and go to the Yahoo home page. Now sign into your account using your username and password. Now copy and paste this link "http://edit.yahoo.com/config/ delete_user" in your address bar. Enter your password to confirm the deletion of your account. Finally enter the code to confirm and delete your account.

This video shows you how to easily remove the tracking Cookies from your web browser. Normally, if you use AVG Free, it will detect the tracking cookies but not delete them. This video will show you how to manually remove that tracking cookies without using any software. The first thing you have to do is click Start menu, then search for Run. In the Run windows, paste the following: C:\Users\YOUR PC NAME\AppData\Roaming\Microsoft\Windows\Cookies , and hit Ok button. Delete all the files that ...

Computer forensics expert Steve Burgess gives a highly informative tutorial on how to recover deleted emails in Outlook and Eudora. The most critical factor affecting the recoverability of deleted web-based emails, according to Steve, is whether the PST file, which stores all the emails, has been compressed after the mail was deleted. If this hasn't been done it is possible to hack into this file and recover the deleted email. Text-based emails, like those one creates on programs like Eudora,...

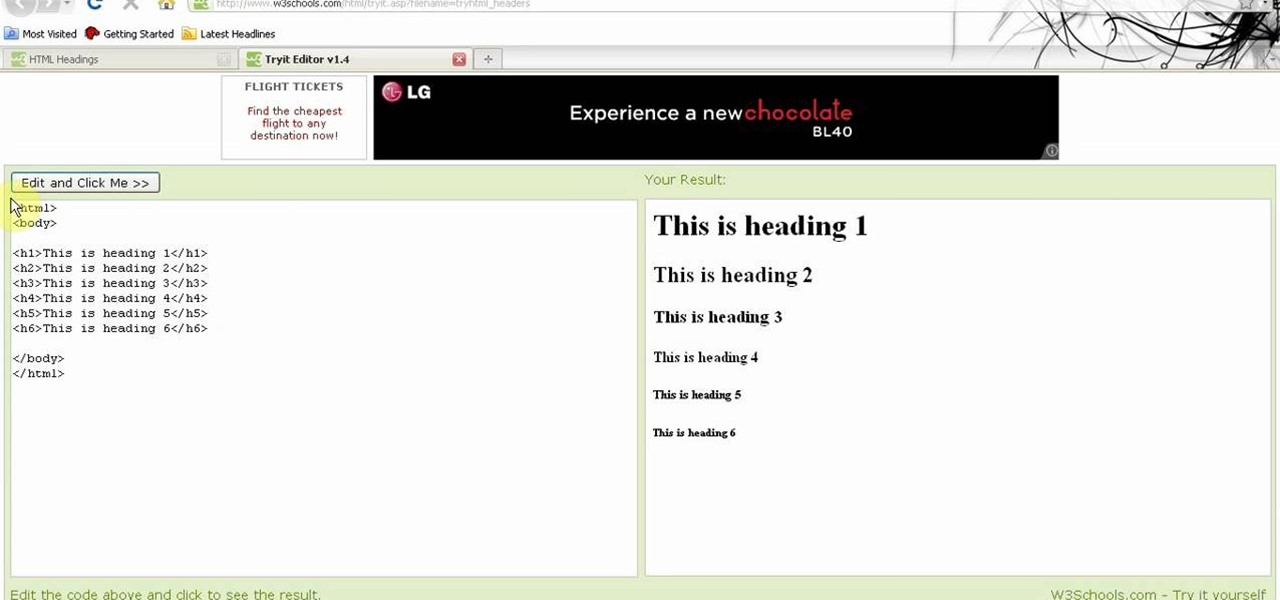
1. Visit 3schools for free and fantastic web building tutorials. 2. Find the subject you are interested in researching and simply click on it and it takes you to a video.

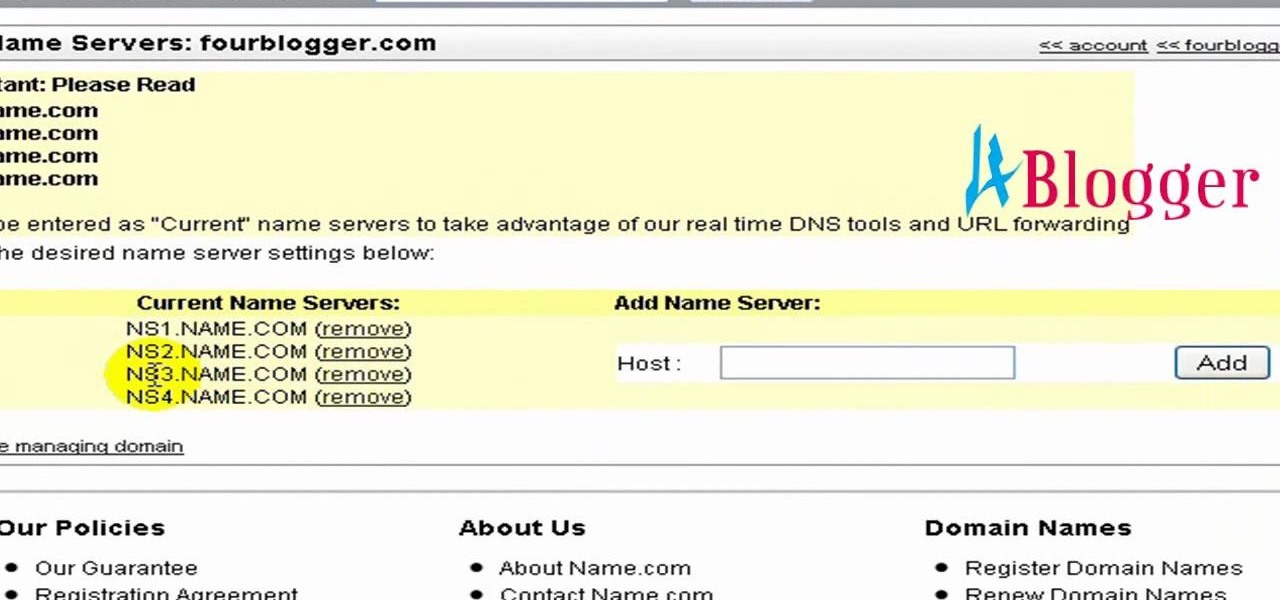
Edit name servers in the domain management area. If you're buying domain and web hosting from a single provider, like Hostgator, then the domain name automatically has a corresponding host.

Cheat Engine 5.5 is the best possible way for you to hack flash games on the internet, on Facebook, and on many other popular web game sites. If there's a hack out there for a game, more than likely it involves Cheat Engine. A lot of people don't actually know how to get the hack app, but it's actually super easy. Just Google it, or simply go to http://www.cheatengine.org, or go directly to the downloads page to find the Cheat Engine 5.5 download.

At midnight on February 17, 2009, all full-power television stations in the United States will stop broadcasting in analog and switch to 100% digital broadcasting. Digital broadcasting promises to provide a clearer picture and more programming options and will free up airwaves for use by emergency responders.

This innovative handset makes user convenience its priority. Created with the aim of overcoming the limitations of existing mobile phones, every function is available through a flexible layout of navigation keys. Fixed keypads are a thing of the past with the LG KF600 Venus cell phone.

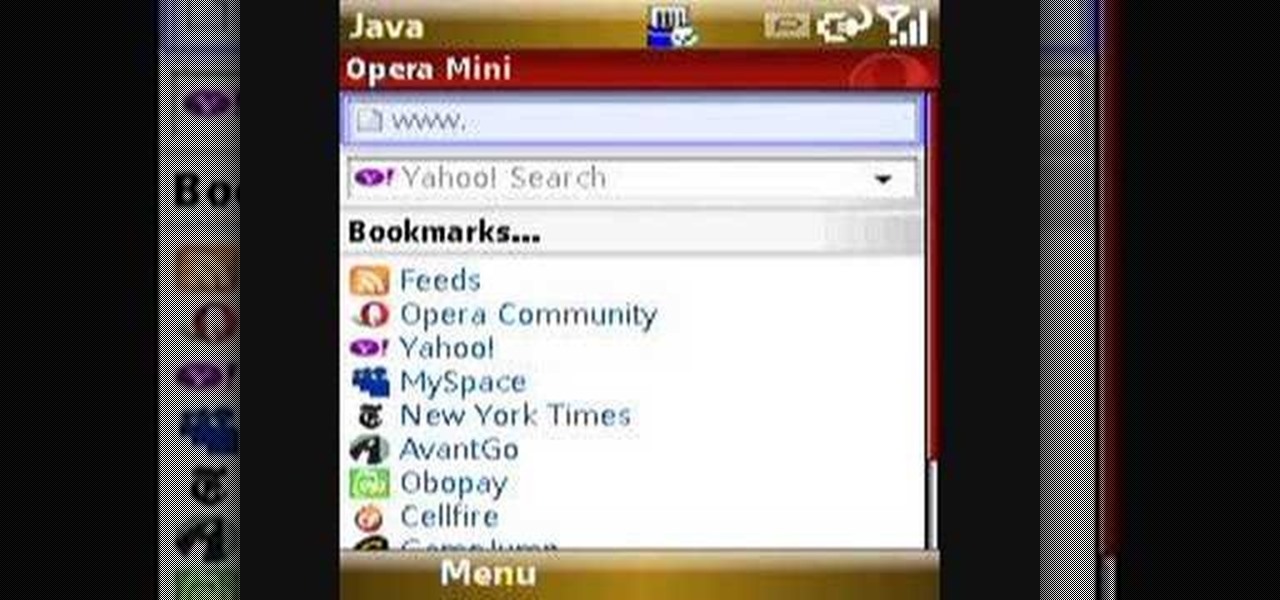
Check out this quick video tutorial on how to install Opera Mini 4 on the T-Mobile Shadow cell phone.

This guy has a lot to say about using the text tool in Photoshop, so he put it all into a 4 part video. Part one covers create, select and edit Text, Point Text and Paragraph Text options. Part two covers Options bar, Great Shortcuts, Character Pallet and Resets. Part three covers Text align, Paragraph palette, Hyphenation and Justification. Part four covers Text for Web, Text Wrap, Text Masking.

Not all websites need a dedicated mobile app, which is why so many don't. Web apps are now designed to scale to different screen sizes, so mobile sites in your web browser are easy to navigate and utilize. Still, there's just something about an app on your iPhone's Home Screen that makes it feel more like an app from the App Store.

Screen mirroring software has been around for ages, allowing you to mirror your iPhone to a projector, laptop, TV, or another device. It's useful to have during lectures, presentations, and meetings, so it's no wonder why Apple created its AirPlay technology. However, AirPlay doesn't work in all situations.

Since launching its web-based AR platform in 2018, 8th Wall has continued to push the boundaries of what brands can do with AR experiences outside of native apps.

With each update, Chromebooks are slowly becoming the Android tablet we always wanted. They already run your favorite Android apps and recently added a multitasking feature introduced to Android smartphones a few years ago: picture-in-picture mode.

The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus.

Over the past year, Magic Leap has teased its cross-platform vision of the AR cloud, which it dubs the Magicverse. While the company shared a timeline for its debut next year, it also served up new developer tools for the present.

As excitement looms for Apple's annual parade of pomp and circumstance for its latest lineup of iPhones, some hidden hints in an internal build of iOS 13 has Apple enthusiasts salivating for what Cupertino is testing in the AR wearables realm.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

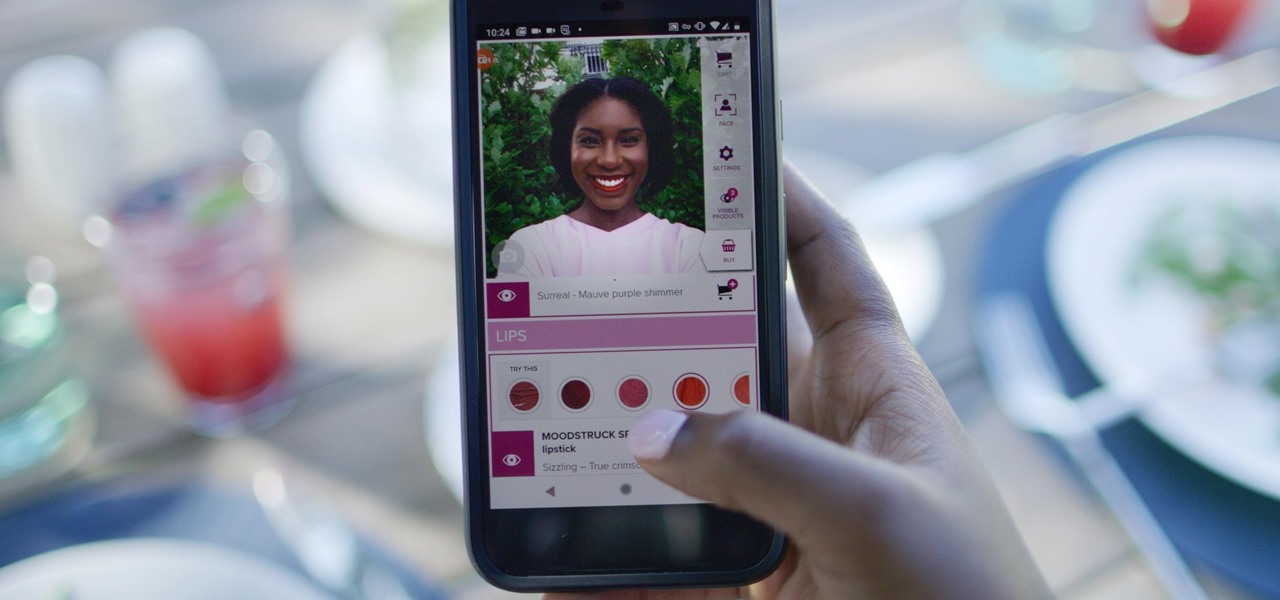
Now that some of the best-known beauty brands are leveraging augmented reality to market and sell products, the rest of the market is beginning to catch up — fast. The latest competitor to add AR to its arsenal is direct sales makeup company Younique.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

Apple had its Worldwide Developers Conference on June 3, 2019, which showcased big software announcements for all of Apple's hardware, and anyone can watch the keynote as it happened.

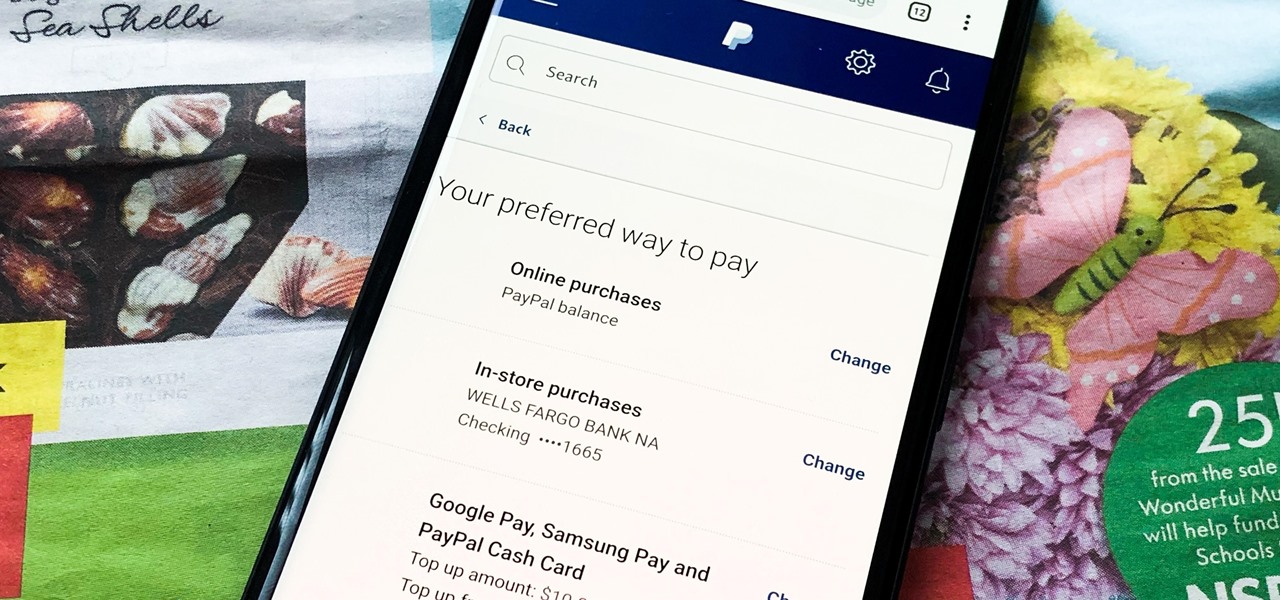
Making a purchase through PayPal is great because you have the option to pay using your account balance, a bank account, debit card, credit card, rewards balance, or even PayPal's own credit product. You need to pick one to be your preferred payment method for each in-stores and online but, unfortunately, changing these preferences can get a bit tricky on your iPhone or Android phone.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use your money with Apple Pay, it's still a good idea to disable it until you find your iPhone, just in case.

Browsing the web can be dangerous. With all of the various threats out there, it isn't enough to just avoid bad links and visit only HTTPS websites. You need to take advantage of the tools available to you so you don't end up the victim of some scam. Fortunately, Opera is making this a bit easier.

Hollywood has already proven that it's on board with augmented reality, with examples ranging from Avengers: Infinity War to Ralph Breaks the Internet. But one startup wants to make the augmented reality content that's being used to promote TV and film entertainment smarter.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

The next big event Apple is holding is WWDC 2018, its Worldwide Developers Conference, is about to happen. If you want to see the first glimpse of iOS 12 for yourself, as well ARKit improvements, Apple Watch news, and maybe even some macOS announcements, here's how you can tune into the event right at home from your computer or mobile device.

The iOS App Store is a big place, offering over two million applications in total. However, there are actually some apps you can and should install on your iPhone that the iOS App Store doesn't include. And no, these apps do not require any difficult jailbreaking or complicated sideloading techniques — they are really simple to install.

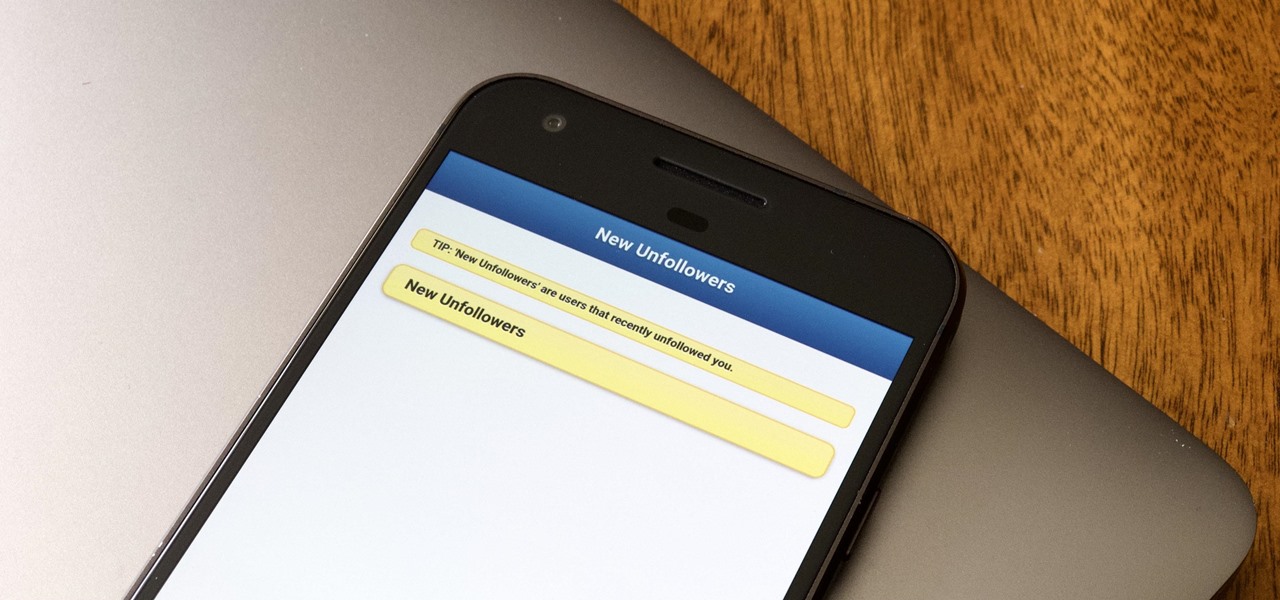
Followers are everything. After all, you need someone to listen to your tweets about last night's episode of your favorite TV show. But what about when people unfollow your account? Not only have you lost part of your follower base, you have no idea who left. Luckily, there are tools out there to help you learn just that, even if Twitter itself won't give up the info.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

Safari for iPhone is generally a good mobile browsing experience — except when it isn't. Popup ads are a real issue, and they cause both great annoyance as well as concern over iOS security. How do you stop these nuisances and return to a web without fear of popups?

There was a time when building a website required coding knowledge. Eventually, software came along that made the process easier, and then services like Squarespace made it dead simple for even a technical novice to design a website.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.