There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?

With the whirlwind of noise surrounding the COVID-19 virus sweeping the nation, it's not hard to default to panic mode. One of the best ways to avoid panicking, however, is to follow trusted sources of information and avoid all of the opinions and trolls that don't reflect reality.

We've been so worried about volumetric scans possibly robbing celebrities and performers of their agency and right to control their image that, somewhere along the way, we forgot that scans may not always be necessary to produce passable holographic performances.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional and physiological well-being with your smartphone.

There are times when physically interacting with your iPhone is less than ideal, like when you're cooking or driving. Fortunately, iOS 13 has you covered regardless of the circumstance you may find yourself in. With the new Voice Control feature, you can control pretty much everything on your device without even touching it.

This week's Magic Leap Lumin OS update contained a number of goodies, including iris authentication, and a way to stream to Twitch from the device.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

In our comparison of the best gaming phones in 2019, the winner actually surprised us. A phone that most people don't know about from a brand you probably haven't heard of ended up as the clear winner. But how? Well, it ticked so many flagship boxes despite its midrange price tag.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.

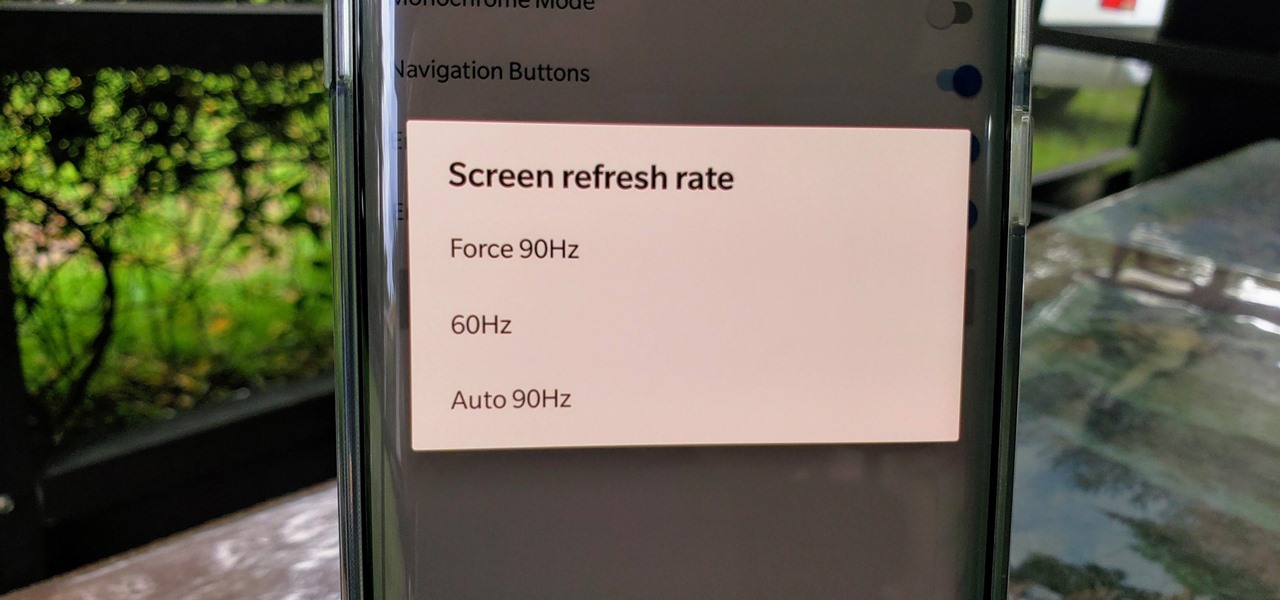
One of the standout features of the OnePlus 7 Pro is the 90 Hz display. A higher refresh rate means smoother gameplay for all your favorite games, which is precisely what you'd want out of your gaming experience. However, not all games play nicely with these higher refresh rates — but luckily, there's a pretty simple fix.

TWRP is a name many are familiar with since it allows your Android device to install any custom file of your choosing. You can create a NANDroid backup to keep your data safe or even use Magisk to achieve full root access. In fact, TWRP is often seen as the gateway to modding your system for creating a unique user experience.

Whether you're used to 3D Touch or Haptic Touch, deleting and rearranging apps and folders on your iPhone is a little bit different in iOS 13.

Since we wouldn't have Android without Google, everyone has come to realize that the Pixel smartphones are a prime example of what an Android smartphone should be. With so many unique software related features, no wonder people want that Pixel experience.

In a way, Twitter is the town square of our era, where people can share and discuss ideas on a wide variety of topics. While the tech giant has its own app for Android, it's pretty bare-bones when it comes to features. This has paved the way for third-party clients that are rich with customization options.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

If you ask Siri to check the weather on your iPhone right now, you'll get information from the stock Weather app in iOS — even if you have and prefer other weather apps installed. But that doesn't have to be the case. Thanks to Siri Shortcuts in iOS 12 and later, you can set specific phrases that Siri will respond to for any compatible weather app you want.

Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

Apple may pride itself on its commitment to user privacy and security, but it isn't invulnerable. We now know there is a bug in the latest version of iOS 12 and iOS 12.1 beta that allows those in the know to bypass your passcode and access contacts and photos. This applies to both Face ID and Touch ID-enabled iPhones. Not only do we know about the bug itself, we know exactly how to exploit it.

Apple's iOS 12 has finally landed. The big update appeared for everyone on Monday, Sept. 17, and hiding within are some pretty amazing augmented reality upgrades for iPhones, iPads, and iPod touches. We've been playing with them ever since the iOS 12 beta launched in June, and here are the things we learned that you'll want to know about.

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

Yesterday, I talked about what I think is the most immediately mainstream-friendly app on the Magic Leap One is (Screens), and now we'll touch upon the runner-up: Helio.

Now that the Magic Leap One is officially out in the wild, users are already beginning to find out exactly how it works and what it might be useful for in the augmented reality space. But there are still other, more unique questions that remain unanswered.

For the second time in a row, Apple pushed out a new iOS 12 developer beta on a Monday, and for the first time this round, they've done it only one week after the last one. While the August 6 release of iOS 12 developer beta 6 doesn't contain a wealth of updates, there are still a few things you'll want to know about.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

During its presentation at Unite Berlin, Magic Leap gave attendees a crash course in developing experiences for Magic Leap One (ML1), we found out quite a bit more about how the device works and what we can expect to experience with the device.

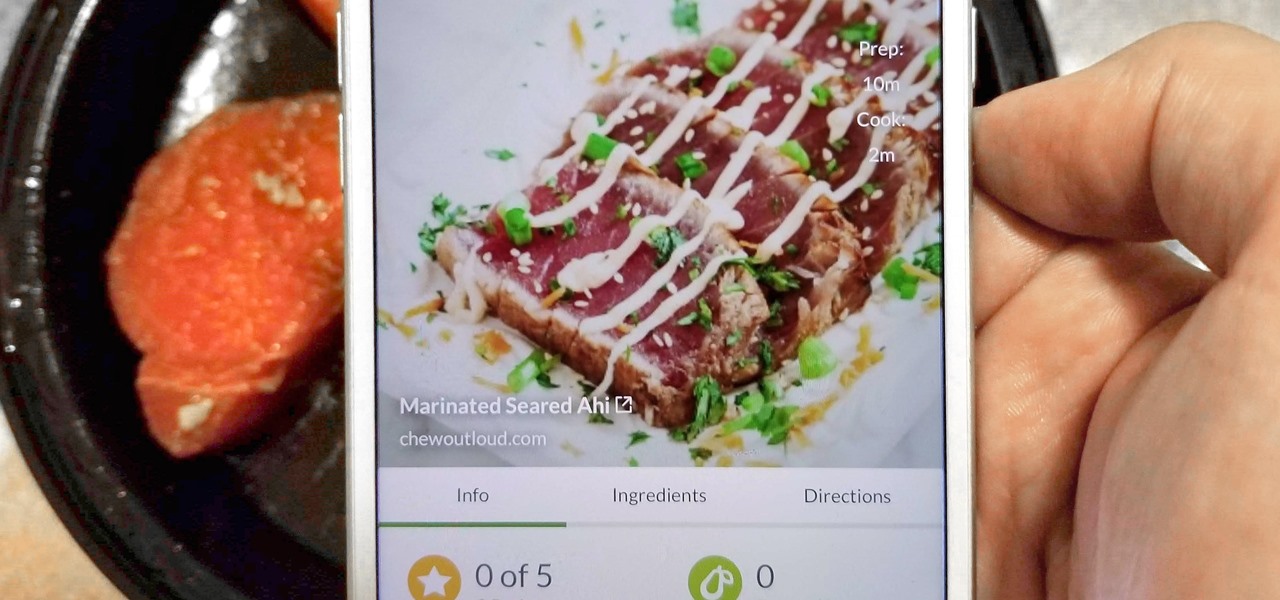
With Tasty dominating Facebook videos and online cooking flourishing, it can be cumbersome to keep track of all your recipes. Someone might send you something, and storing it in an app like Pocket is like jamming all your school papers in one folder — it just isn't practical. Fortunately, there's a better way to catalog your recipes so you can always have them on hand.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

Thanks to Apple's ARKit 2.0 augmented reality framework in iOS 12, we now have a "Measure" app built right into our iPhones that can measure real-world objects. No more physical tape measure or ruler. No more guessing. Just whip out your iPhone, open the app, put your camera, and get measurements. Before you do, however, there are a few things you'll want to know.

Over the years, we've seen security breach after security breach, as well as high-profile data scandals where collected personal information was misused by companies. Apple makes customer privacy a priority, so there have been few issues to worry about when it comes to its services on your iPhone. However, there are still plenty of privacy settings to explore and change, especially within Safari.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

One of the best gifts that someone with an iPhone can receive is a paid app, hot new movie, bestselling album, gift card, or anything else in iTunes, Books, or the App Store that costs money. Even if it's a small $0.99 game that you heard a friend talking about, a gesture like this can go a long way. Gifting apps and media is now easier than ever, even if you don't have an iOS device yourself.

While everyone was marveling at the latest drama over at Magic Leap involving employees last week, a major rumor listed in one of the reports, related to the company's flagship device, was mostly overlooked.

Chances are, you just point, shoot, and share photos and videos on your iPhone without a second thought about how your privacy is affected. It's fairly easy to do so since the Camera and Photos apps that Apple provides seem so innocent. But there are a few things you need to know when it comes to shooting media, sharing it, and even deleting it.