
Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.
In this video you will see how to enable payment through a third party gateway using SSL.
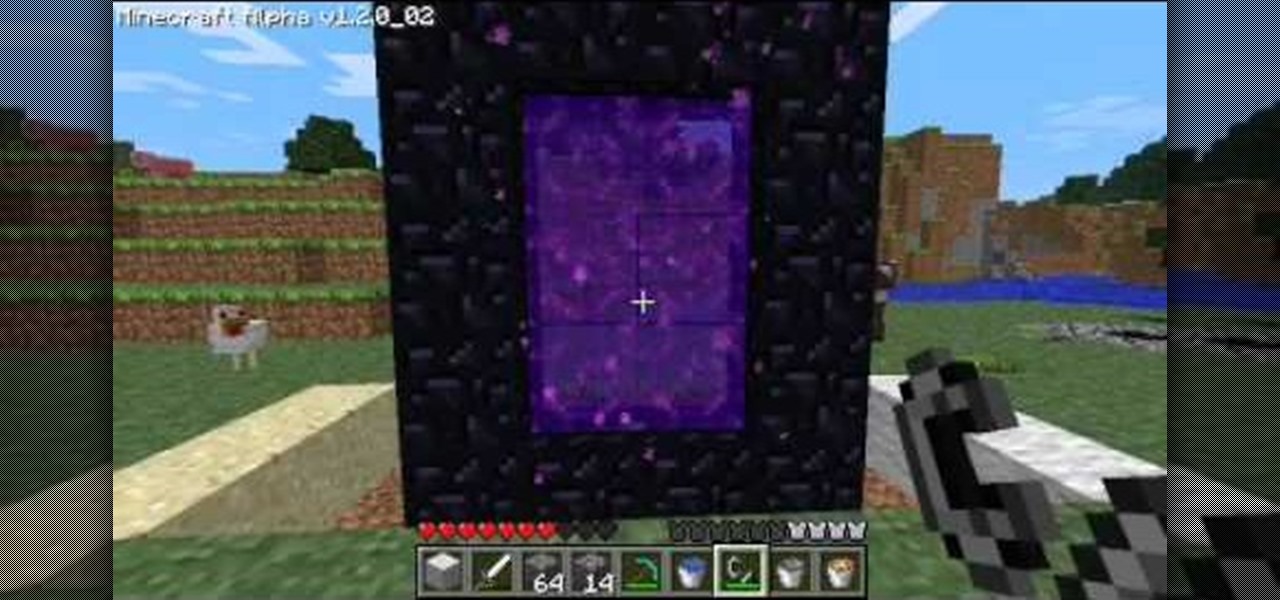
The Halloween update from Notch added many amazing features to the game including Biomes, and more! One of the more prominent, game changing additions were Gateways that lead you straight into Hell. Every step you take in Hell is equal to 16 steps in the outside world. The way you make it is through creating a gateway of Obsidian and igniting the center of it. In this video you will get a tutorial on how to make the Obsidian for the Gateway as well as how to create the Gateway and teleport in...

If you're trying to unlock the orange portals in Dark Souls, this guide should help you out. You'll need to complete Anor Londo first, but after you do, you can jump down a hole and access an alter to remove the fog barriers in front of the gateways.

This video shows you how to bypass expensive texting charges and use this free and easy way to text people without the need to download apps, go to websites, or jailbreak your device. Works on basically any cell phone. No need to ever pay $20.00 for unlimited texting with AT&T, watching this you'll be able to text for free whenever, and whoever.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Montezuma's revenge, the runs, the trots, or just diarrhea — everyone gets it sooner or later. What exactly is diarrhea good for, if anything?

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

Since it first launched in 2003, WordPress has dominated the internet. The free, open-source content management system (CMS) is used by over 60 million websites. Wordpress is undeniably one of the most popular CMS solutions in the world.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

With smartphone cameras and software getting better and better every year, more and more users are getting passionate about photography. So when you're shopping for a gift to get someone, if they have a smartphone, chances are they'll more than appreciate some tools and accessories for taking better photos with their pocket friend — and we've got some gear ideas they'll love.

Google's much anticipated eBook Store has finally opened. As of today, the digital bookselling enterprise is awaiting your needs, with over 3 million eBooks to read directly on the web or on other platforms, like Android, iPhone, iPad, Sony and Nook devices.
Hello again ! This is the second part to Fingers from a Hand Analysis perspective.Where as the first Video just covers basic introductions to the Fingers, this part two Video takes things a little bit further and examines ......Finger Shape ;- Length suggesting mental speed, Methodical or Speedy thinker ?Finger Width ;- Suggesting which level a persons interests may lay, Mental or Practical realms ?Finger Prints ;- Amazingly interesting area to explore , Fingerprints do not change.. They star...




















