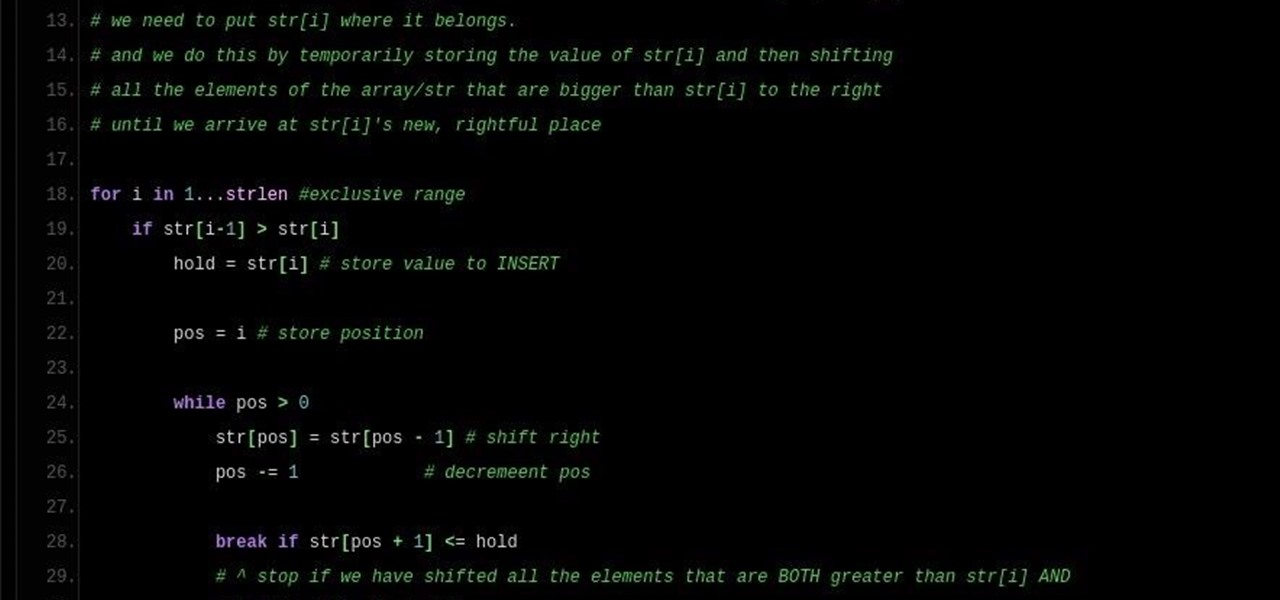
Note: a bug was found in the Insertion Sort implementations. The bug was corrected in each language. Please refer to the pastebin links for the most up-to-date versions of the sample code. Any screenshots may be behind. More about the bug can be found here.

In my last post I introduced how to use ncat to connect to your Pi remotely, but what's the point to if you can't actually hack? This tutorial I'm gonna show you how to use very simple tools for a much bigger purpose. With that said, boot up our Pi and lets wreck havoc.

Winter—or any cold, gray day, for that matter—is the best time for a warm cup of something hot. For me, hot chocolate is my "warm cup" of choice: rich and milky, deliciously sweet, and oh-so-comforting. On super-cold days when I can't feel my face, a nice, large cup of hot chocolate warms my tummy and cheers me up. (And lucky for me, it's pretty healthy for me too!)

I'll bet this scenario will sound familiar to you: you're in the middle of making a spectacular dessert that will knock the socks off of your guests, and you've almost finished gathering all of your ingredients to create your mise en place. The last ingredient listed is powdered sugar, and you reach for where it's stored, when—drat! You don't have enough for the recipe.

A salad can mean everything from fruit to meat and everything in-between, but it never means finger food. Forks are required. So that means that even though salads are versatile, delicious, and customizable, they are hell at cocktail parties. How do you hold your glass and take a bite of your salad at the same time? It's awkward.

How many times have you heard someone utter the phrase, "Now, let's break into groups"? From classroom discussions to workplace think tanks, gathering into groups to generate ideas is common practice. These forced get-togethers are intended to encourage creativity and unique thought, but they can actually do the opposite. More often than not, group brainstorming is annoying rather than encouraging, and these group sessions can actually be detrimental to your productivity. Getting together har...

Mobile scanning applications are nothing new in the world of Apple, except that the majority of them usually come with pesky in-app purchases that stifle the entire experience and render some features useless until you pay for them.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

Becoming a competitive candidate in IT and Data Science takes more than knowing a few coding languages and being good with computers. To really stand out from the crowd, your knowledge should be extensive and your experience should be diverse. The 2021 Complete Computer Science Training Bundle provides that depth of knowledge and a starting point for gathering that experience. Right now, it's on sale for just $39.99.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

This week's Apple earnings offered a report of solid performance and guarded optimism about future iPhone sales, which may be impacted later this year by issues around the current coronavirus epidemic in China.

As the Augmented World Expo (AWE) prepares to open its doors to AR developers and enthusiasts, we sat down with founder Ori Inbar to talk about AR's growth over the past decade, and what the future may hold.

iOS 12 has a feature that lets you instantly share saved Wi-Fi passwords with other iPhone users, but it can be finicky when you're sharing with multiple people. Then there's an even more pressing question: How do you share your password with Android users? Thankfully, there's a Shortcut that can solve these problems.

This week, Next Reality published its annual feature on the leaders in the augmented reality industry, the Next Reality 30. So it's no coincidence that the companies represented in the top four spots of the NR30 also made business headlines in AR this week.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

When a firm like Techstars believes that augmented reality is an attractive industry to invest in, there's a high probability that it's right.

With four major carriers, buying an iPhone X or iPhone 8 can be more complicated than you'd think. While Apple has its own iPhone upgrade program, AT&T, Sprint, Verizon, and T-Mobile all have versions of their own. Which plan you choose depends on your needs and, of course, your carrier. However, getting around to upgrading can be challenging to say the least.

Every Tuesday, Next Reality will give readers a rundown of the augmented and mixed reality news briefs from the preceding week that we didn't cover already. This way, you'll never miss anything of importance in the Next Reality landscape, and will always know what's going on with new augmented and mixed reality tech and applications.

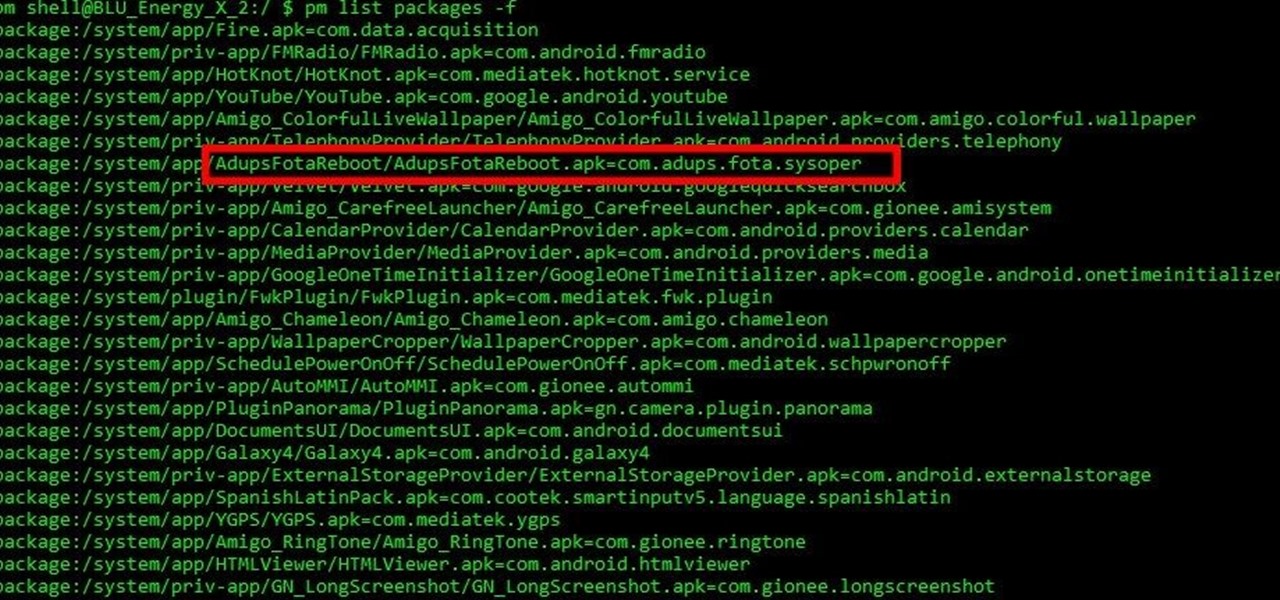
Mobile security researchers at Kryptowire recently uncovered spyware preinstalled on hundreds of thousands of Android smartphones by FOTA provider Adups which was gathering personally identifiable information (PII) such as call logs, app usage data, and even the full contents of text messages and sending these to a third-party server—all without the users' knowledge.

Pumpkin pie is a symbol of autumn, and it's the traditional dessert to whip up for your fam when Thanksgiving Day arrives. But year after year of the same old thing can be a total bore if you're not a strict traditionalist. So, we found 8 unique ways to make that pie a little less snooze-fest and a little more interesting.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Alright, NB community! Here we go... Bubble Sort. What Is Bubble Sort?

Nothing about living in a snowy climate is easy, but life with a snowy, frozen car doesn't have to be the worst part of your day. With a few clever hacks and some anti-weather tactics, you can fight off frozen windshields, icy locks, and even stubborn car doors, while keeping your car running smooth all winter. 1. Deice Your Car Locks in Seconds

Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more.

I recently had a small gathering of friends over for a quick cookout consisting of mostly burgers on the grill. One of my friends informed me beforehand that she didn't eat red meat, but that she would be perfectly okay with eating a turkey burger.

Be it happy hour, a Super Bowl party, or just a gathering of friends, buffalo wings are a universal favorite. Since they're usually prepared for large groups, there is always a mix of both those that aren't counting their calories and others who are.

Well, first things firsts, it's been awhile! I'm sorry the series has been dead for a little bit, but I recently hit some personal relationship issues and needed to take some time to think. But, now that it's all said and done, the dust can settle and we can start training again!

"Beer is proof that God loves us and wants us to be happy." We've all seen the quote, attributed to Benjamin Franklin, on numerous shirts, glasses, and bar signs. It's a good, if overused slogan. It makes one clear, indisputable point: beer is great, and life is better with it.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

Keeping your home clean is an endless battle with time, motivation, and the easy availability of cleaning supplies. That's where the Hard Surface Floor Cleaning Robot Vacuum comes in. This magical device will save you time by automatically keeping your floors clean, never requires motivation, and doesn't require additional supplies beyond occasionally emptying the dust bin.

Even as the world continues to grapple with the pandemic, the tech industry continues to chug along, with some looking for ways to present new products, and in some cases continue major conferences that reveal the latest in augmented reality developments.

Since its release in 1991, Python has become one of the world's most popular general-purpose programming languages. From data mining and web programming to cybersecurity and game design, Python can be used for virtually everything online.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.