Dr. Lin Morel discusses stress in an easy to follow format in this short OneMinuteU presentation from 2008. Her first suggestion is to breathe deeply. She follows that up with paying attention to your body and taking care of it. Then she discusses enlisting friends for support with the stress. Her second to last suggestion is to take time to be still and rest. Her final idea is to create a plan of attack for dealing with stress so that you are prepared when it comes up. These easy steps are g...
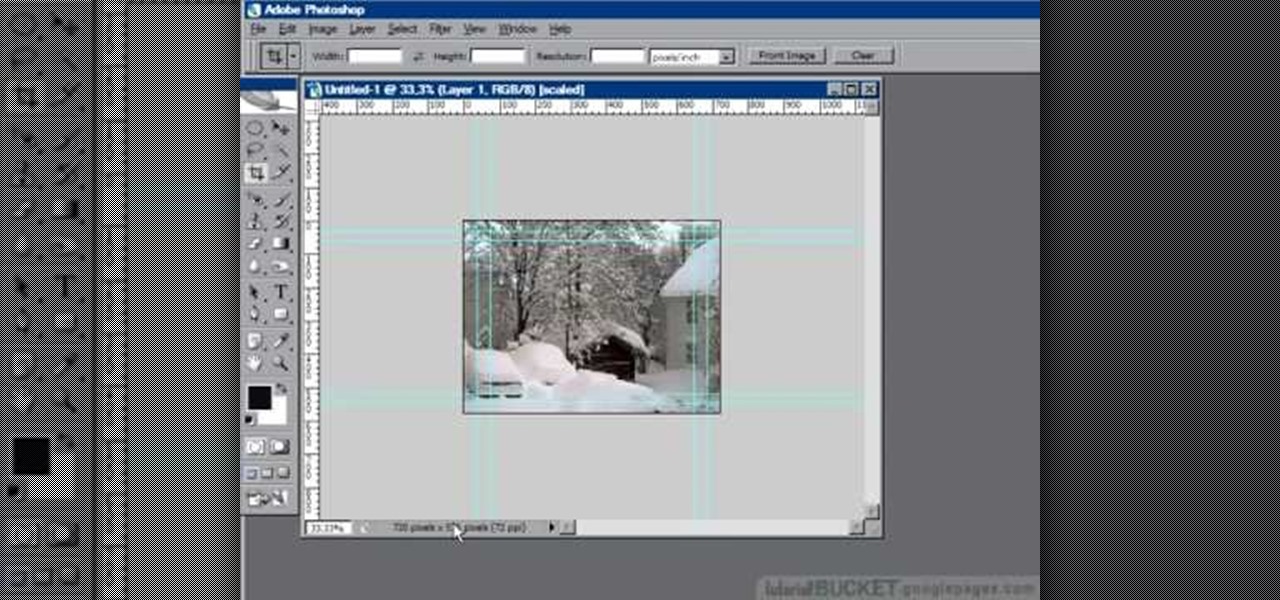
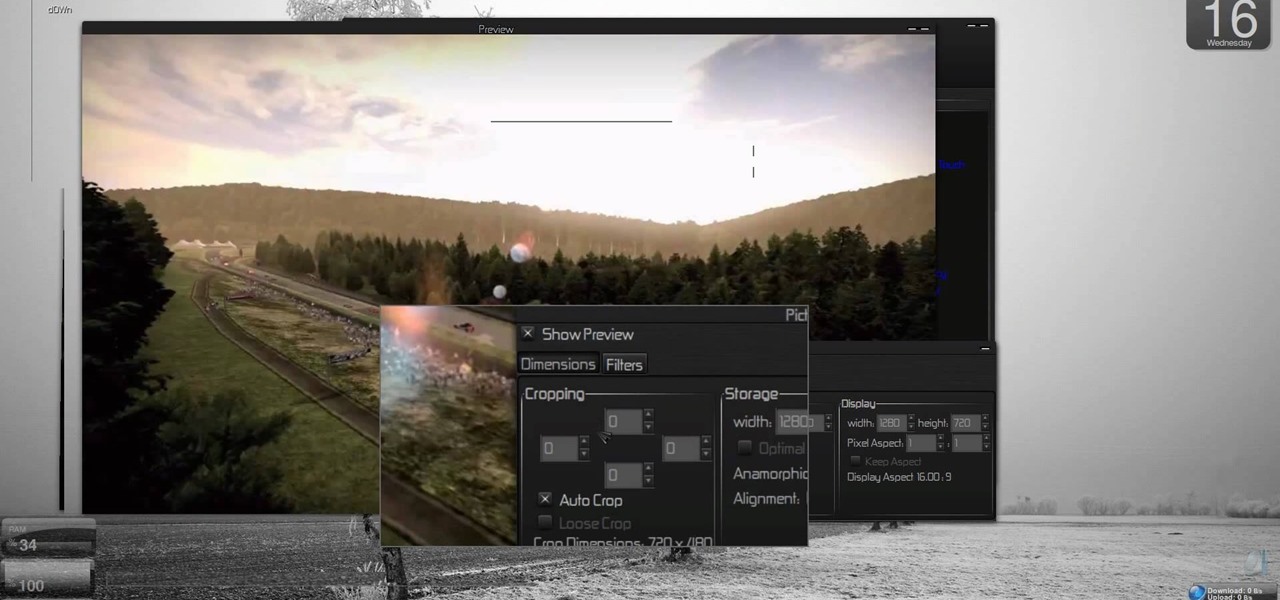
In this Adobe Photoshop tutorial the instructor shows how to prepare pan and scan images. To prepare an image by panning and scanning is quite different than preparing an image normally for using in your video. These images should be extra sized as you would perform special effects on the image in your video. This is also called as "Ken Burns" effect. Now go to the file, new menu and select the video format that you want to use according to your requirement. Enable the correct pixel aspect ra...

Make sure you're getting the best experience from your Blu-ray movies on your PS3 by optimizing your PlayStation 3's audio, video and display settings. Scott Lowe for IGN, shows you step-by-step, the exact process for an enhanced Blu-ray experience.

This video shows the basics of multiplying integers. The main point that people can struggle with is the variation of signs. When multiplying integers you must always be aware of the positive and negative numbers. When you multiply two numbers that have the same signs, both positive or both negative numbers, this will always generate a positive answer. If there is one positive and one negative number this will always lead to a negative answer. This video shows very basic problems of multiplyi...

In this flash tutorial the instructor shows how to make a black and white mask animation. To do this, first start by importing your image into the flash tool and bring it on to the scene. The image should be wider than the scene. Now select and distribute the layers. Now convert those images into movie clips. Now go to frame 80 and add all frames. Get back to the first layer and create a shape that is the your mask. Now go to frame 40, select key layer and add free transform tool. Now, mask t...

In this tutorial the instructor shows how to convert a improper fraction to mixed number. In the example the instructor takes the denominator of the mixed fraction and writes it beside and keeps adding it self to the latest number and he keeps on doing that way generating a series until he reaches the value of the numerator. Now he counts the number of occurrences of the numbers in the series before the value of the numerator which gives the value of the whole number in the mixed fraction. No...

In this video the instructor talks about compound and continuous interest formula calculations. You need to understand the concepts of simple and compound interest. Only then you can understand what the bank is doing to your money which are in your bank account. Simple interest is a method where when returning a borrowed sum to some one you pay additional price for using the money all this time. Compound interest is a similar concept where you pay interest on the original sum borrowed, and al...

To tile with large format and natural stone tiles onto walls you must first make sure the walls are flat, clean, dry, and free of any dust, dirt, oil, grease, and any other loose material. Ensure that surfaces are suitable and prepared as advised. Then use the Dunlop Universal Bonding Agent where you will be applying the tile. For gypsum plaster and gypsum plasterboard, apply two coats of Dunlop Universal Bonding Agent, diluted with one part bonding agent, two parts water. Then allow primer t...

Check out this masterclass on Houdini 9.5 and how to rebuild the fire simulator. Houdini's Fluid Tools offer a powerful simulation environment for visual effects artists. Senior Mathematician Jeff Lait introduces you to the basic building blocks for generating fluids and low level tools that make it easier to control the simulations.

Everybody is going digital these days, so everybody has a reason for software like HandBrake. You can save your entire DVD collection on your computer in digital files, and you can convert videos into different formats. Check out this video tutorial on how to rip DVDs and convert videos on Ubuntu Linux, Windows, and Mac.

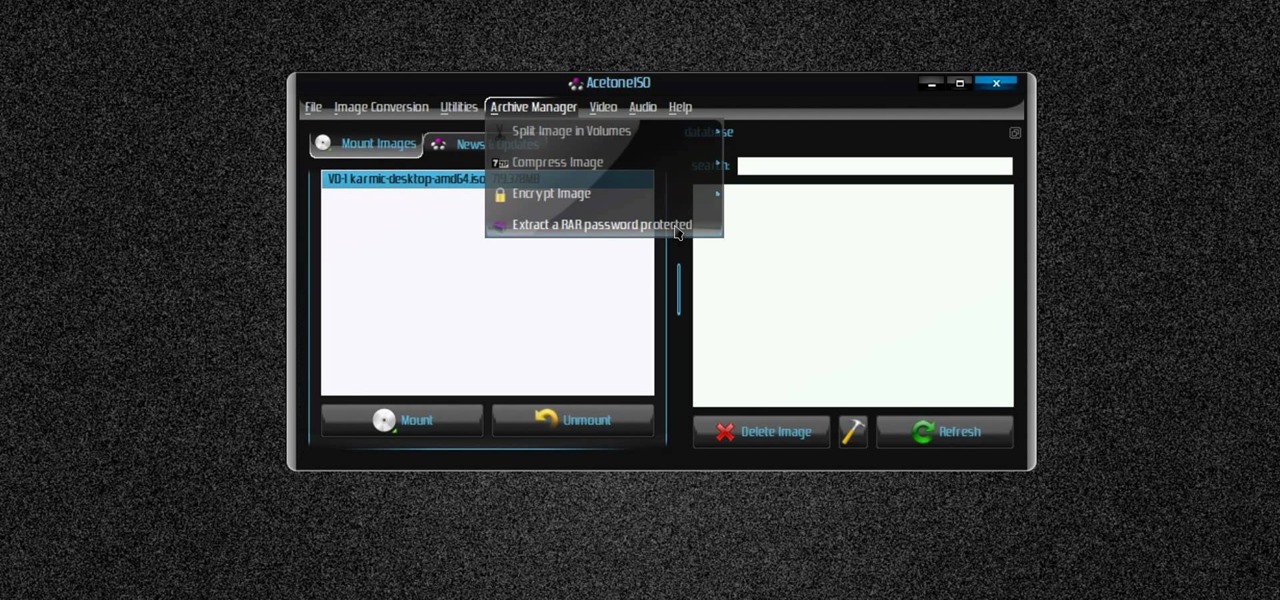
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to manage CD/DVD images with ease on Ubuntu Linux.

Most people don't use their cameras to make movies (really bad quality and a sort of user-generated content feel are probably the culprits) but cameras with a record function are great for those impromptu memory-making moments when your dog tries to do a handstand or your grandma unloads the biggest belch ever.

Get moving! Learn how to walk, run and jump your way through LittleBigPlanet. LittleBigPlanet exclusively for the PLAYSTATION 3. It lets you PLAY alone, or with friends, in a world of infinite possibilities. Run, jump, grab and swing your way thru imaginative levels and mini-games. If you're feeling creative, you can CREATE your own levels, enemies, obstacles and even storyline. Once done, SHARE them with our online community of thousands of User Generated Levels from around the world for

Stick it to them! Learn how to resize, rotate, and stamp your sticker collection in LittleBigPlanet.

Get some clothes on! Dress up or Dress down, learn how to express your own SackFashion for Little Big Planet on PS3.

Check out this video tutorial to show you how to use a Canon Rebel digital SLR camera. This video was made by the equipment room at CUNY Journalism School in New York.

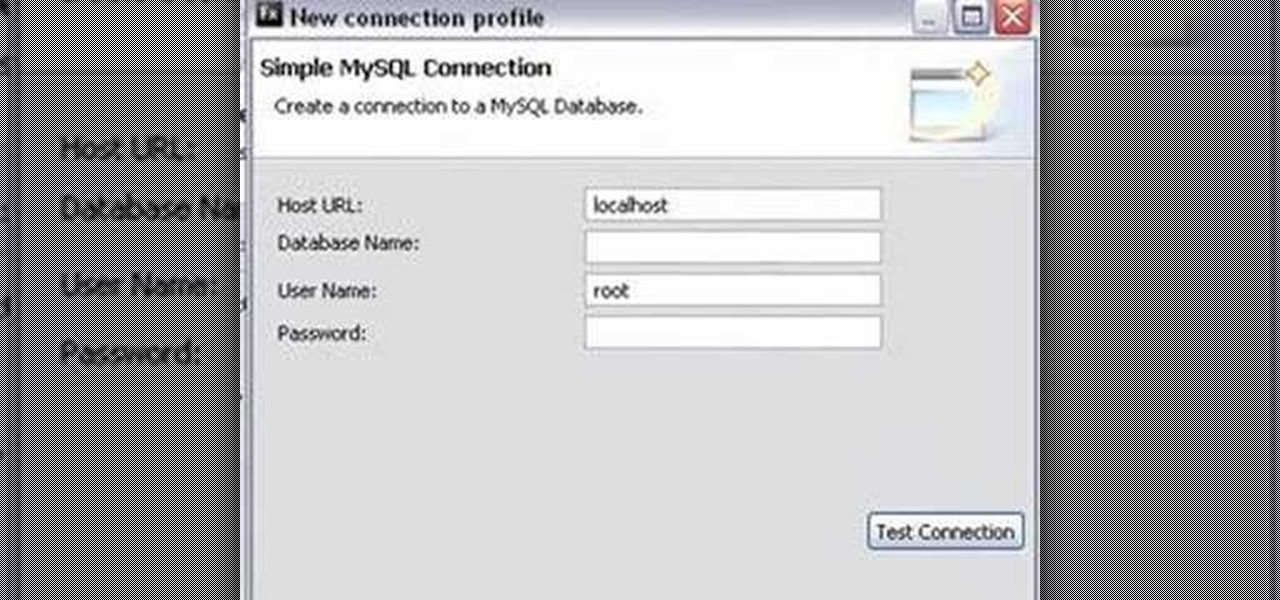
This tutorial demonstrates how to create what is called a complete client-server web application which consist of a Web Application, PHP, and MySQL. The tutorial shows how to automatically generate the PHP necessary to talk to a MySQL database using Adobe Flex Builder 3.

This Houdini n9 software tutorial covers a very simple lighting and rendering scene to show the basic workflow for generating a PBR render. We use a digital asset to quickly establish a group of geometry to light. In the lesson we also add an area map so that we can extract the lighting information from it. There are two .rat files to experiment with, the seashadow.rat file simply provides a pattern. The st.peters_cross.rat is an HDRI image from the Debevec site. Watch and learn how to set up...

In this video tutorial you will learn about a very powerful feature in Houdini called Copy Stamping.

Continuing on with budget lighting, we explore using Fluorescent and LED lights, along with using available light, bouncing it with a reflector. These setups will work great for interviews, video casting, vlogging, and the likes. These lights use less power and also generate much less heat then big halogen work lights, and the price can't be beat. We also show the benefits of adjusting white balance on your camera, with lots of before and after shots. If you are shooting independent movies, s...

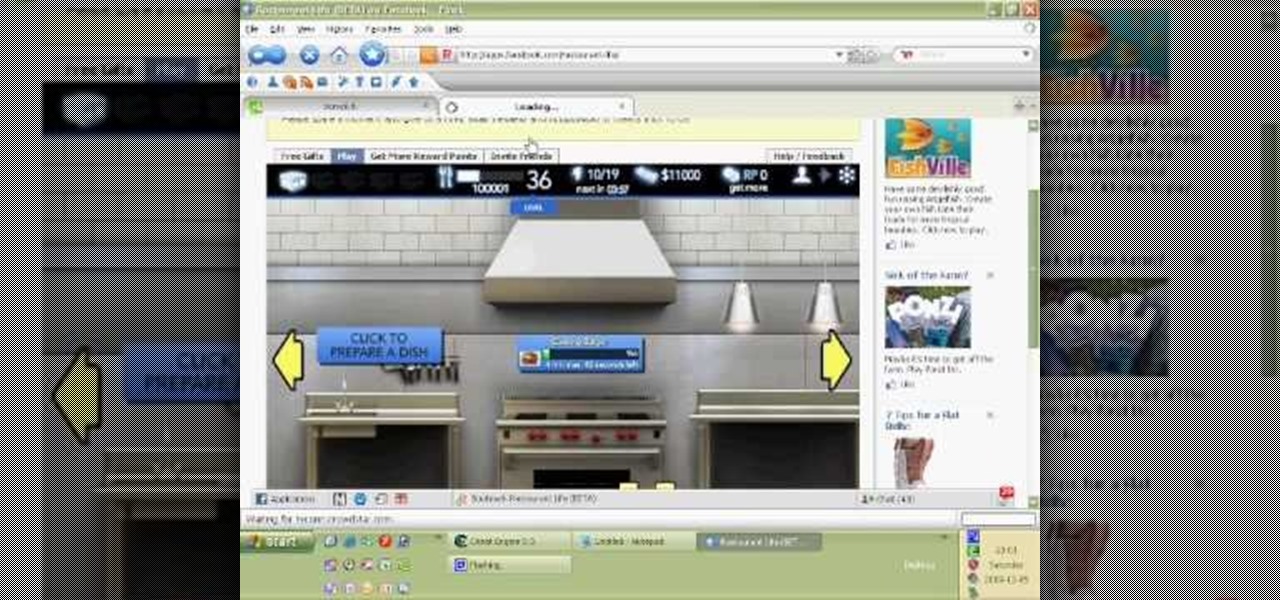
Watch this video tutorial to learn how to level hack Restaurant Life (12/05/09). 1. Open RL and Cheat Engine 5.5, then point CE 5.5 to the process of your browser.

This is a jumprope hack for Pet Society. It's called the Auto Jump + Coin hack, and involves your jumprope, Cheat Engine, and a little code generator.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

If you're a long-time Spark user, you'll know that one of the only drawbacks to the app used to be its lack of rich text-editing tools such as hyperlinking. If you needed to link out to a site in an email, your best bet was to grab a computer to get the job done. Well, close those laptops and shut down those PCs — Spark corrected this issue, implementing support for hyperlinking right into the app.

Every industry has its own jargon, acronyms, initializations, and terminology that serve as shorthand to make communication more efficient among veteran members of that particular space. But while handy for insiders, those same terms can often create a learning curve for novices entering a particular field. The same holds true for the augmented reality (also known as "AR") business.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

A market research report, posted on February 27, 2017, forecasts that the image recognition market will grow to nearly $40 billion worldwide by 2021. The market, which includes augmented reality applications, hardware, and technology, generated an estimated $15.95 billion in 2016. The report estimates the market to grow by a compound annual growth rate of 19.5% over the next five years.

Hello again, reader! In this post, we are going to cover some data types and how to declare variables. It shouldn't be too hard so just sit back, relax, grab some popcorn and enjoy the ride (while you still can!).

This is a quick and easy method for receiving the backend IP (1) of a server who is hidden behind a proxy (2) or a firewall (3).

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

As with any software, Android apps can occasionally suffer from bugs. But finding the root cause of such issues can often be difficult, and reporting bugs is a cumbersome experience.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

One of the roles our government has taken on is to provide us with information to be used in making decisions.

The term blog is a shorthand for web-log. It can be considered as a online and publically viewable diary of user generated content usually sorted by date.

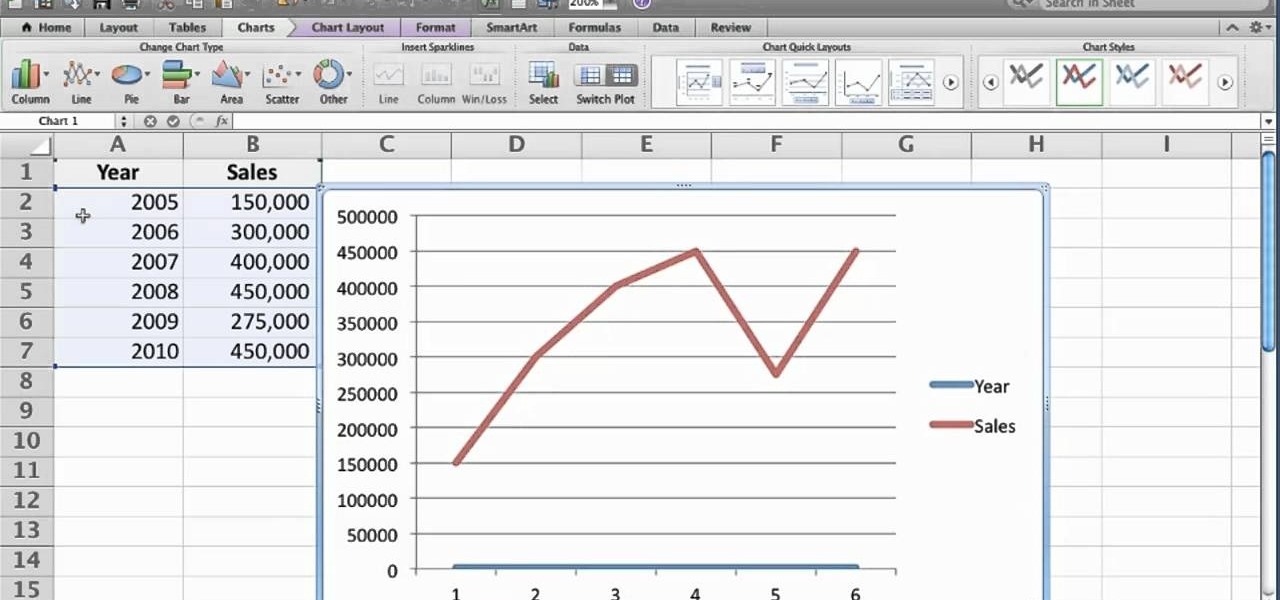
Want to generate a line chart in Excel 2011? This video will show you how it's done. Whether you're new to Microsoft's popular digital spreadsheet application, new to Excel 2011 or even an expert merely looking to brush up on the fundamentals, you're sure to be well served by this quality video tutorial from the folks at Lynda. For all of the details, and to get started creating and using line charts to visualize data in your own MS Excel '11 projects, watch the video.

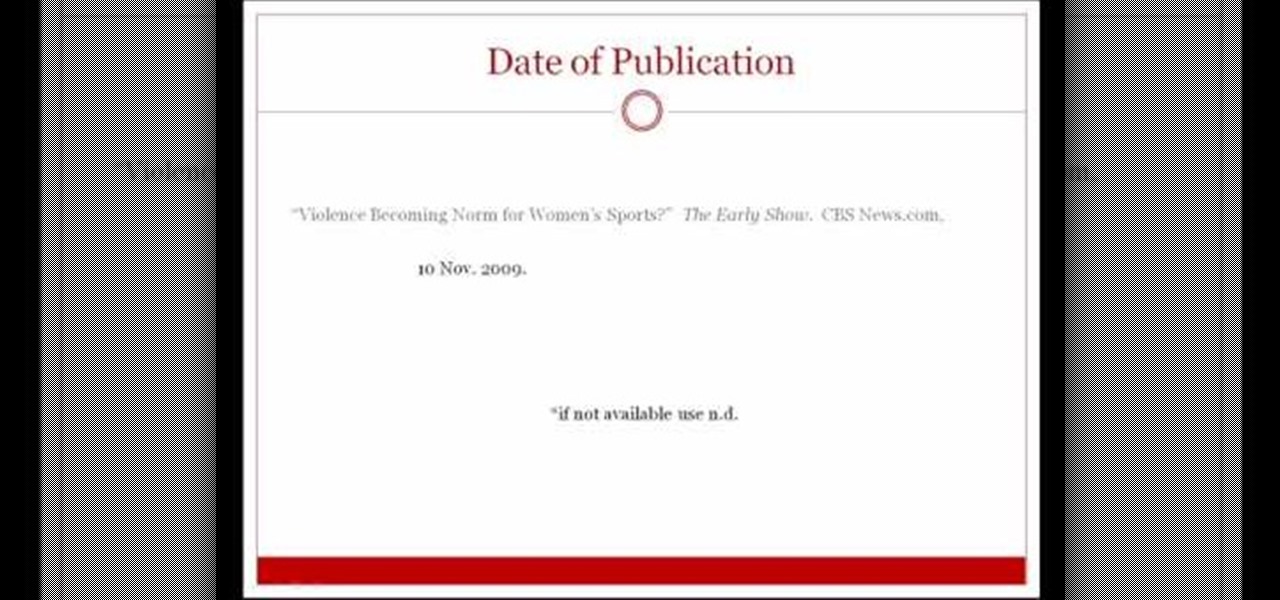
If you're writing a college essay or report, your bibliography is a painful, yet necessary part. And thanks to all of the information available on the World Wide Web, most colleges and universities accept websites as resources in your bibliography. But citing websites can be confusing when using the MLA citation format. This video will breakdown the process.

It's like magic. Creating a .LOG file has never been easier. And all you need is Notepad on your Windows PC. After creating this LOG file, Notepad automatically inserts the current date and time after the last line. Check it out. If you've ever wondered about LOG file types, this Notepad trick is must.

In this tutorial, we learn how to root your G1 or MyTouch 3G with one click. First, go to theunlockr and download the MyTough 3G Root video. Now, go on your phone and click on the settings. Go to applications, then check "unknown sources", then go back and click on "sd card" and un-mount it, then format it. Once the numbers pop up again, it means your card is mounted and formatted. Now, plug your phone in with the USB cable to your computer and mount it. Now, go to the site and download the t...

Need some help figuring out how to generate proxy objects in RealFlow? Never fear. This guide will show you how it's done. Whether you're new to RealFlow's popular fluids and body modeling software or are just looking to get better acquainted with the application its various features and functions, you're sure to enjoy this free video software tutorial. For more information, and to get started using this trick in your own RealFlow projects, watch this 3D modeler's guide.