Want to generate experience and level up your Pet Society character the easy way? Watch this cheater's guide, which will show you how to hack Pet Society for all the EXP you could ever want.

Smash glow? What the heck is that? That's exactly what you'll find out… watch this science video tutorial from Nurd Rage on how to make smash-glow crystals (triboluminescent crystals) with Dr. Lithium.

Long-time packeteer Bob Bruninga, WB4APR, developed the Automatic Packet Reporting System (APRS), which allows packet radio to track real-time events. It deviates markedly from the usual message- and text-transfer activity. Instead, APRS concentrates on the graphic display of station and object locations and movements.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.
Read This Must Need flash player 9!!

Watch this science video tutorial from Nurd Rage on how to make a lithium thionyl chloride battery, which is capable of generating 2.8v with enough current to power a LED.

Watch this science video tutorial from Nurd Rage on how to make a chemiluminescent reaction with home chemicals. Make a chemiluminescent singlet oxygen red light pulse from two simple chemicals almost anyone can buy: pool chlorine and hydrogen peroxide.

Watch this science video tutorial from Nurd Rage on how to make silver nitrate from silver and nitric acid. They show the chemistry of making this cool chemistry, colorless solid.

Watch this science video tutorial from Nurd Rage on how to make a mirror silvering solution from silver nitrate, ammonia, sugar, and sodium hydroxide.

This video tutorial shows how fifteen dollars and a half an hour of assembly can produce a working bare-bones laminar flow nozzle that attaches to a garden hose for a makeshift fountain.

In the following series of videos we will establish a particle stream that is then used to create a surface that evolves over time in Houdini 9 software.

Snapchat popularized personalized stickers for social media and messaging with Bitmoji, followed by walled-garden versions from Apple with Memojis and Samsung with AR Emojis. Even Google has gotten into the game, integrating an emoji generator for Gboard.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's control. Burp Suite contains a useful tool called Clickbandit to generate a clickjacking attack automatically.

Every once in a while, we find ourselves in a predicament where we need an inexpensive smartphone. Whether we're finally upgrading from that feature phone we held onto too long or we dropped our current smartphone, sometimes we need a quick replacement to get back on track. That's where Android One comes in.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

While ARKit and ARCore are poised to bring AR experiences to millions of mobile devices, one company is poised to anchor those experiences anywhere in the world with just a set of geographic coordinates.

Once we recover from the respiratory infection pneumonia, our lungs are better equipped to deal with the next infection — thanks to some special cells that take up residence there.

Cancer cells do a pretty good job of flying under the radar of our immune system. They don't raise the alarm bells signaling they are a foreign invader the way viruses do. That might be something scientists can change, though.

If you are an NYC commuter like me, then I'm sure you know how bad the city's transportation has gotten.

Flu vaccines can help prevent us from getting or suffering the most severe effects of the flu. But, each vaccine only protects us from three different strains of the flu. If we don't have a vaccine against all types of flu, it leaves us open for an epidemic with a flu virus we didn't expect.

Things aren't looking good for Uber after its driverless experiment in Pittsburgh soured relations with local authorities. Surprised? Me neither.

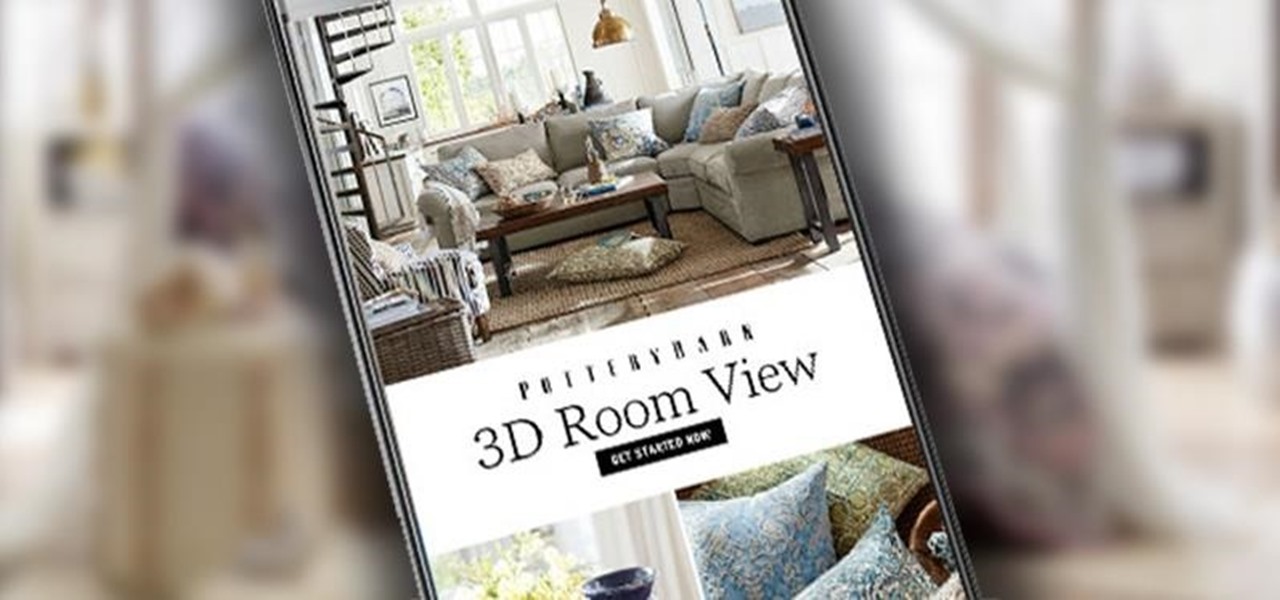
Pottery Barn has teamed up with Google to create 3D Room View, a new mobile app to allow all wannabe interior designers (like me) to pick out the perfect couch, table, or whatever, and then overlay it onto a spot in his or her house.

While its direct-selling model echoes brands like Avon and Tupperware, Indonesia's MindStores gives the approach a modern twist—with augmented reality.

Now that we've learned about keeping all our data safe with encryption, it's time to continue progressing through getting your Mac set up for hacking.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

From parents and other family members to friends and peers, personalities are built by environment. Though people are important in the development of our own individual personality, there are other, different influences, including what you choose to read. The books you take the time to enjoy can make you nicer and more understanding, or leave you overall unchanged.

Time is money, and if your job requires sending out hundreds of generic emails—think "Thank You" notes and sales pitches—you could save days of work by creating templates stored within your Gmail called "canned responses."

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

Minions are computer generated NPCs that spawn from the base nexus and attack enemies. You can't control your minions, but you can influence them by using smite and heal on them. Use your minions well and you'll win your games on the Fields of Justice!

Mike Callahan from Butterscotch describes how to manage the passwords on your iPhone by using the 1Password app. The application costs $5.99 for the Pro version. First, you enter an Unlock Code to give you access to the app. The icons across the bottom of the screen correspond to different features of the app. The Logins icon stores your login information. The Wallet icon stores information about your credit and bank cards. The Passwords icon holds all your passwords. The Add icon allows you ...

This Houdini 9 software video series focuses on examples of when and how to use Attribute Transfer. Part 1 covers Attribute Transfer One Point:

Selling stuff at the local flea market sounds easy enough, but it isn't anything like having a yard sale. There's a lot more to it that just getting rid of your junk, and the biggest things are being licensed and having a sales tax number. Flea market vendor may not be your first career choice but, like many, you may find it’s a lucrative full-time job or a profitable and fun sideline.

Cue ball draw refers to the way a cue ball strikes a rack of balls. In particular, if the cue ball is hit low on the ball, when it strikes a rack of balls, for the break, it will have enough backspin to wind its way back to the shooter.

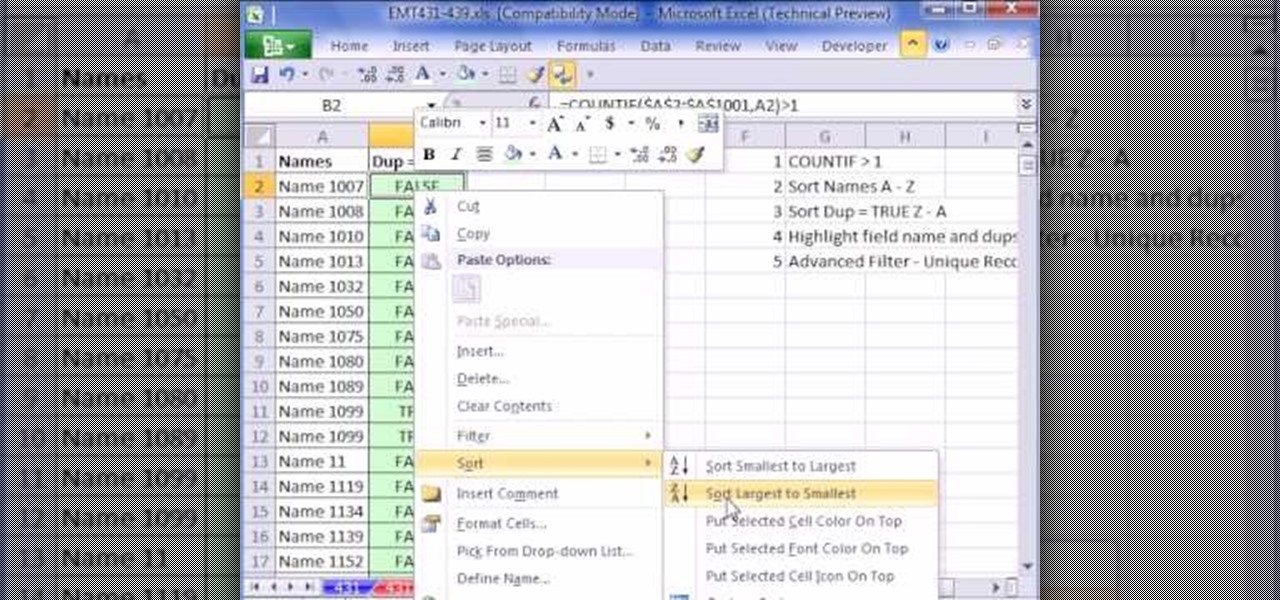
This video is about finding duplicate entries in excel sheet. The example excel sheet contains different names. There are around 1000 different names in the sample excel sheet. CountIf(range,criteria) formula has been used to do the comparison and return of results in True or False mode. Type =CountIf( now move your left arrow key, this will generate the formula like =CountIf(A2. Now press Ctrl+Shift+Down arrow, this will select all the available values in the column. Now press F4 to lock it ...

Watch this video to learn how to make a basic honey and sesame seed chicken. This delicious dish will be generating raves around the dinner table. Ingredients: A plate of sesame seeds Dark soy sauce Blossom honey Vegetable oil five pieces of skinless chicken Fresh coriander for garnish Put a frying pan onto the stove top on high. Mix in a bowl stirs equal amounts of dark soy sauce, honey and vegetable oil to make a sticky marinade. The vegetable oil stops the honey from burning. Add in chicke...

In this video the instructor shows how to upload High Definition HD videos using Camtasia Studio. Here the instructor shows how to upload the videos that you recorded using Camtasia in HD to YouTube. Now to generate a HD video you will need to record in high resolution like 1280 by 800 pixels. Now record the video at full screen. Now after recording you will have your HD video. Open the video in Camtasia and add the clip to the time line by right clicking it and selecting the option from it. ...