Many of us were required to take a foreign language in school, but sadly, many of us are far from fluent in said language. To be a better citizen of the world, learning popular and rare languages would be dope, but in reality, that's probably never going to happen. If you ever do find yourself in a situation where you're messaging people who don't speak your language, there's an app that can help you.
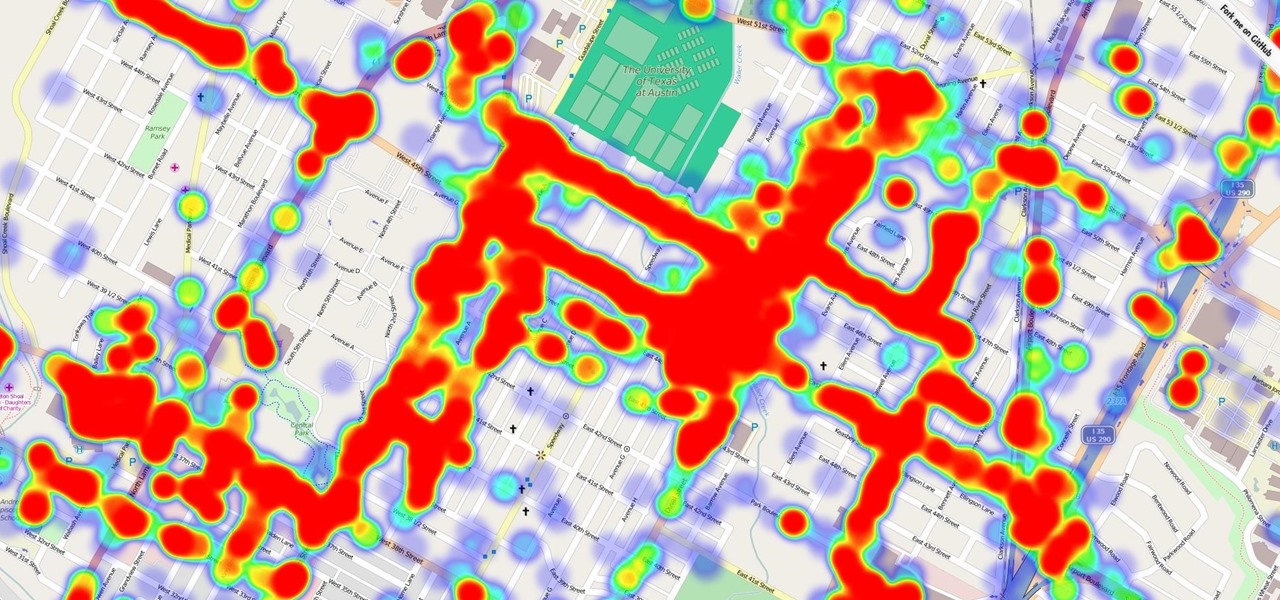
With an Android device left at its default settings, your location history is automatically recorded. You can view and manage this data, but the simple interface of points plotted on a map leaves a lot to be desired.

With the release of the ARChon Runtime, many Android apps can now be run within the Chrome web browser. Minor changes must be made to existing Android APK files before they can be installed on Chrome, so the process isn't exactly as easy as pasting an Android app into a folder on your computer.

Sharing files has always been one of Android's greatest strengths. A system of "share intents" allow apps to freely exchange data with each other, making it possible to take a picture with your favorite camera app, then send it over to your choice of photo-sharing apps, for instance.

Unlike the suave 007 that Daniel Craig portrayed, I am not a spy, nor am I that charming, but I do occasionally enjoy taking a stealthy video. Maybe I'm a jerk, but I often catch people doing ridiculous things and just think, "Aren't you embarrassed?"

Videos are great for catching fleeting moments, and photos are insanely easy to share with anyone, but how can you get the best of both worlds?

Sometimes, ceiling fans just don't cut it. They spin meekly, barely generating any air flow to cool down your sweltering room. Or, when turned up high, they can wobble wildly, shaking and vibrating as if the ceiling is about to come crashing down. If this sounds like your ceiling fan, chances are the solution is a simple as flipping a switch.

You've seen the Samsung Fingers and the Emoji Translator, and I know you spent a good part of the day catching Pokémon, but now that April Fool's Day is officially upon us, the flood of gags has reached a tipping point. Here's the best of what we've seen today.

Google Glass is all about transforming the world around us with little to zero interaction from the wearer. Much of this is done using augmented reality—a live view of physical, real-world environments that are augmented by computer-generated input in the form of graphics, sights, and sounds.

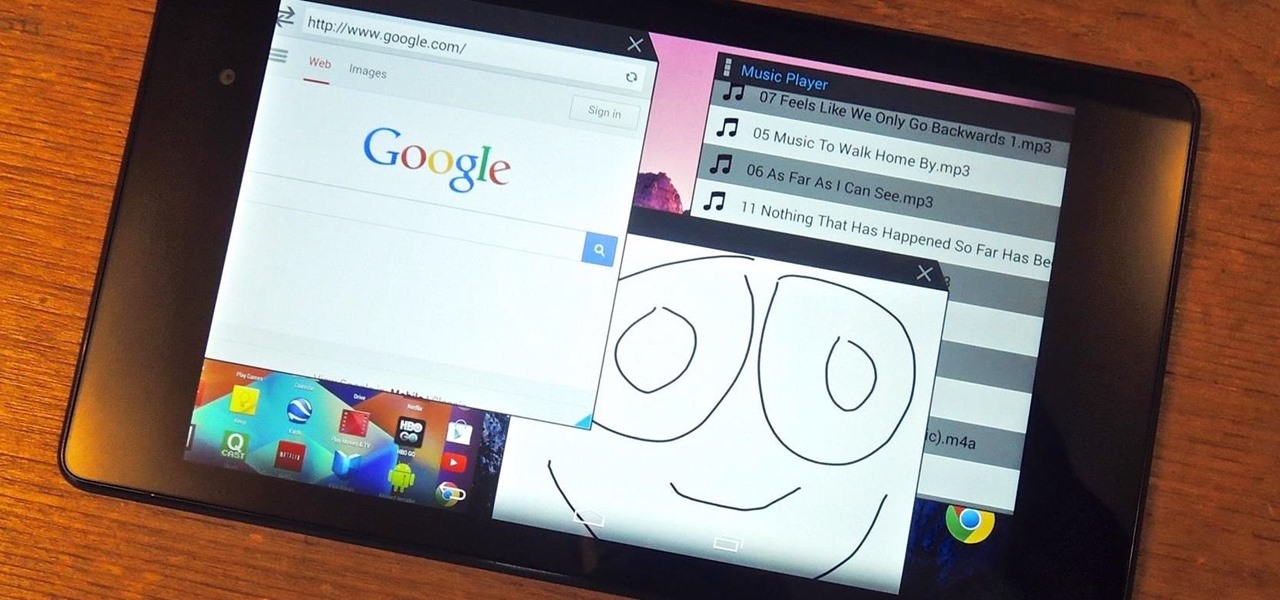
Recently, I offered a guide detailing how to run two separate windows on a Nexus 7 tablets for better multitasking. While extremely useful, that mod was limited to only two windows, and you also needed root access to use it.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

WhatsApp is one of the most well-known and most utilized cross-platform chat applications available today. It's free for one year, and only $0.99 a year after, which is chump change when you realize there are no hidden costs like international charges. Basically, it creates an easy to use forum for you and your friends to chat, regardless if they're an Android or iPhone user.

Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!

Sony's Xperia Z, which has generated quite a deal of excitement since its launch at the CES in Las Vegas last month, is already sold out in France with its expected U.S. release to be sometime in March. It's 5-inch, 1080p display puts it up there with some of the best smartphones in the market. It runs on Jelly Bean 4.1.2 and comes with expandable storage. Also, the Z comes with an incredible 13MP rear camera with the capability to dish out 9MP photos at 14fps, shooting roughly 999 stills in ...

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

When we surf the web, we tend to do it for selfish reasons. Whether it's on Facebook, Twitter, YouTube, Pinterest, or Wikipedia—we're trying to connect with people, voice our opinions, watch funny videos, or do research for that 12-page paper due tomorrow. Whatever it is, it's usually to benefit ourselves. Well, what if you could not only benefit yourself while surfing the web, but benefit others in need, without even having to alter your habits?

The mighty Arduino microcontroller can be used to show children how robots work, it can be used to hack into hotel rooms, or it can be used to let you know when you've got a new job opportunity!

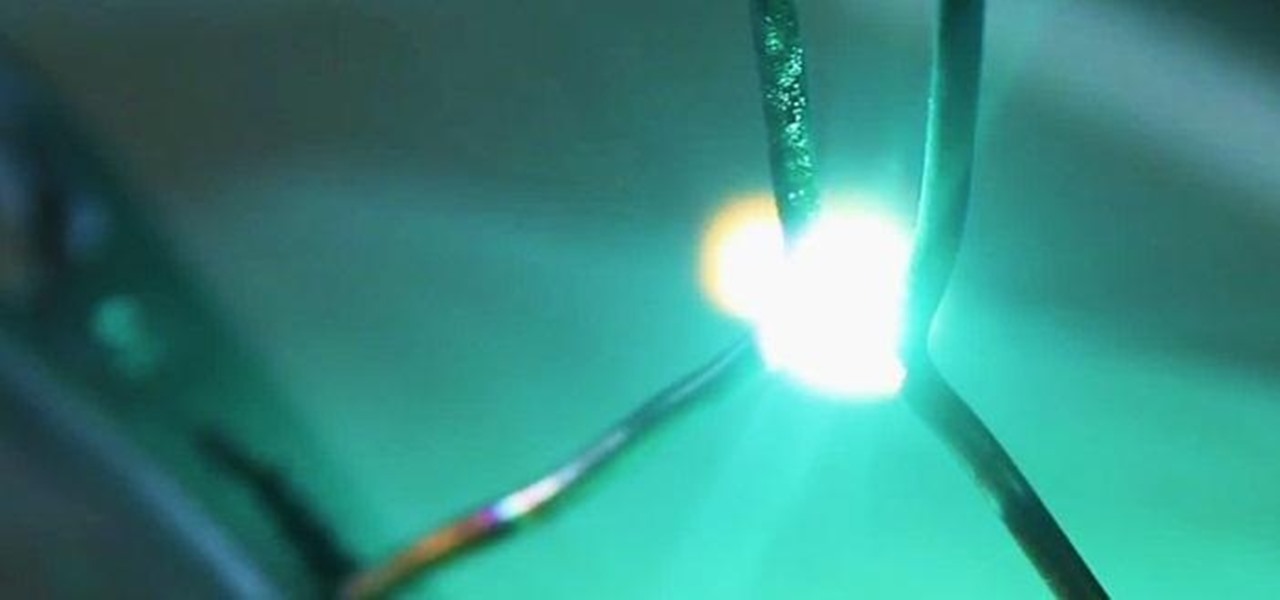
With the microwave oven transformer (M.O.T.) salvaged in a previous project, a simple electrical circuit can be rigged to get high voltage arcs to fly outward and upward along a "V" shaped spark gap.

In this tutorial, we learn how to play the Dungeons and Dragons role playing game. To get started, you will most likely join an existing group, which is the easiest way to get started. You will be part of a story and have different adventures, depending on how your group is ran. You will need to have a full set of dice to play this, then go through the different adventures on the game. You will also need a character sheet to play and your player's handbook. Make your character, and pick all o...

This video is about a particular pool or snooker game shot technique called "Shooting or Going around the Angles." The presenter, with a alias name of 'Forcefollow', first describes a particular 9-ball pool game situation that would require this technique, using a computer generated picture image to show an overhead view of the pool table, with the pool balls in question placed at certain locations within the table and showing the various angle trajectories paths of the desired ball to be str...

Siri has long relied on basic sources like Google and Wikipedia for answers, but with iOS 18.2 and iPadOS 18.2, Apple is taking its virtual assistant to a new level by integrating ChatGPT. Now, you can use Siri to generate text and images with ChatGPT — and that's not all. ChatGPT is deeply integrated into Apple Intelligence and goes beyond just Siri.

Disney Plus shows WandaVision and Falcon and the Winter Soldier are both streaming hits, but the two series could not be more different in terms of giving fans a taste of the Marvel Cinematic Universe.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

In order to increase the security and harden the integrity of an email account and its content, you'll want to use PGP on your Windows, macOS, or Linux computer. This is usually the first thing security analysts do to protect communications with encryption, and everyone else should consider it too, especially since there's an easy way to incorporate PGP that anyone can follow.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.