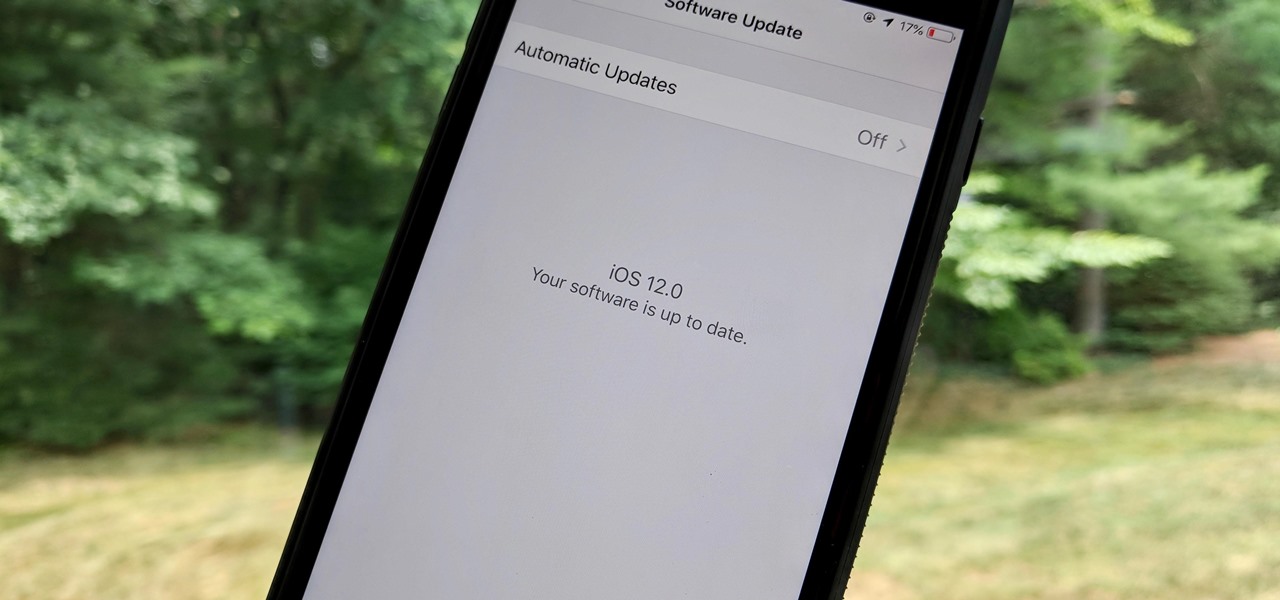
As the official release of iOS 12 nears closer each day, Apple continues to update its betas. The company released the fourth beta of the upcoming software to developers Tuesday, July 17, exactly two weeks after the release of the third developer beta which came out just a few days before the second public beta.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Every industry has its own jargon, acronyms, initializations, and terminology that serve as shorthand to make communication more efficient among veteran members of that particular space. But while handy for insiders, those same terms can often create a learning curve for novices entering a particular field. The same holds true for the augmented reality (also known as "AR") business.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

So while it is the weekend of San Diego Comic-Con, and it should not be a complete surprise — without a word of warning hitting my feed — the trailer for the upcoming film, Ready Player One was released today. And wow it looks amazing.

While some researchers look for drugs to treat HIV, other scientists delve deep into the virus itself for answers on how it causes infections.

One thing that I got more and more excited about as we got closer and closer to the Microsoft Build 2017 developers conference was finally learning about the new Acer Windows Mixed Reality head-mounted displays (HMD). Brandon Bray, Principal Group Program Manager at Microsoft, had teased us a few weeks earlier at the Vision Summit event in Los Angeles, California, and said there would be a lot more information at Build. Fortunately for us, he was right.

Think of the coolest, most unique way to create art that you can. Got it? Now think about creating that art out of living things.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

In the past, creative chefs and bakers have been rewarded for their daring in the kitchen with viral attention from the internet—like the rainbow bagel or cronut. These sensations weren't crafted for the sake of going viral, but ended up generating an insane amount of buzz anyway.

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

Welcome back! In our last training session, we covered some advanced list topics. We'll be going deeper into the advanced list rabbit hole today with lambda and lambda operators! (And I'm not talking about Gordan Freeman)

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

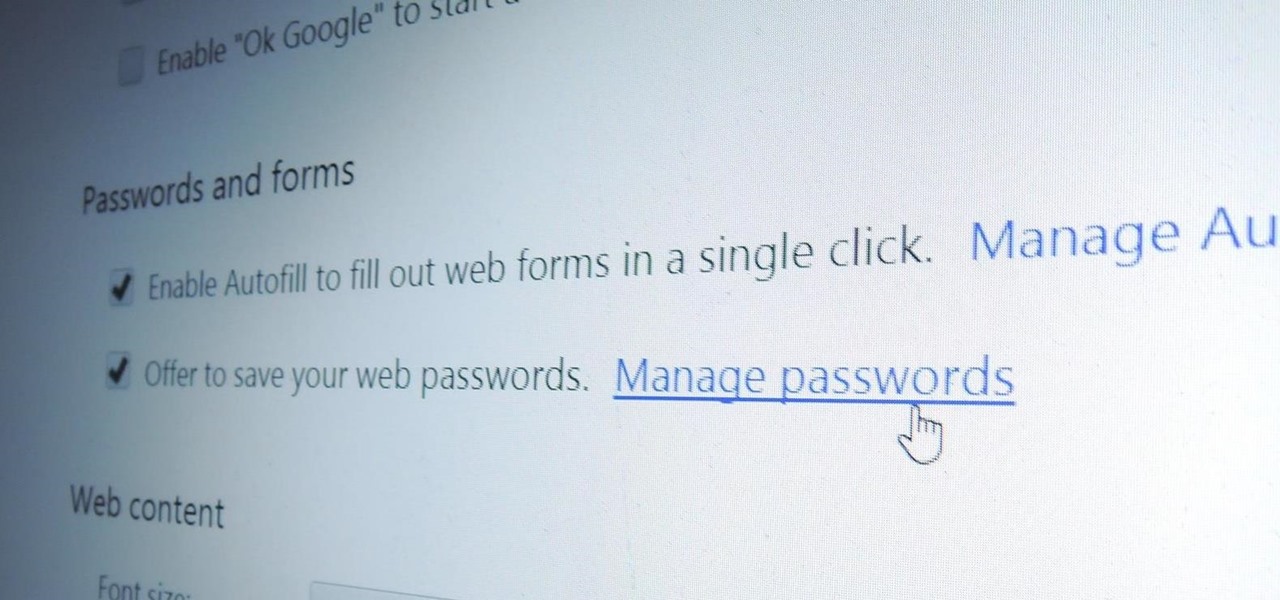
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

Generative artificial intelligence has taken the tech world by storm, and Google's AI chatbot will give you a taste of what it offers.

Navigating a pandemic is new for everybody, which makes staying on top of your finances more important than ever. Fortunately, financial freedom is possible when you focus on budgeting and investing wisely.

For the average consumer, augmented reality is a fun way of dressing up photos and videos for social media. However, AR is also gaining momentum as a medium for storytelling, particularly in sharing powerful messages.

Google Meet might not have virtual backgrounds like Zoom, but it hits all of the other basics, from hosting many multiples of video participants to sharing your screen, that you'd expect from a robust video conferencing platform.

There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

If you're concerned about your privacy, TikTok might not be the app for you. Its shady practices with user data have been the subject of concern, criticism, and even legal action by the US government. Then again, it's just so addicting. If, like me, you're not going to stop using TikTok anytime soon, you should at least know how to view the personal data it has collected on you.

Starting February 21, you can preorder your Galaxy S20, S20+, or S20 Ultra. Samsung includes everything you need to get started in the box, but probably not everything you'll want. Let's go ahead and bridge that gap.

One of the hallmarks of augmented reality's coming of age is that the technology is starting to find a home in business categories that are less obvious compared to typical AR enterprise use cases.

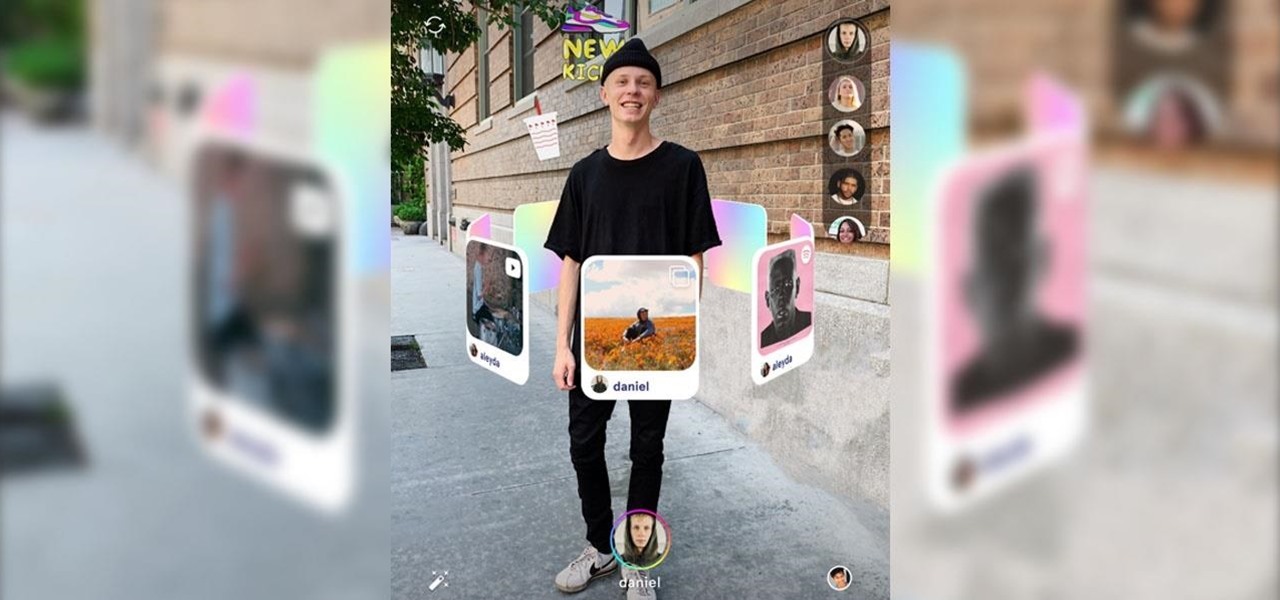
In a world full of augmented reality camera effects apps, one app is going in a more social direction.

It's the holiday season, and the tech industry is giving consumers several AR products and apps as gift-giving options.

With Android 10 hitting the streets (at least for those mobile devices that get quick updates) and the public release of iOS 13 dropping on Sept. 19, Google is releasing an update on Thursday to ARCore that adds some fantastic new benefits to its cross-platform capabilities.

When you think about it, isn't life just one big open-world RPG just begging to be conquered? We all have a set number of specific tasks or chores we must complete every single day like clockwork. Sometimes, these items on our to-do list can become tedious and cause us to lose motivation. What if you could take those tasks and turn them into something awesome instead? Now you can.

With Google taking on the sidewalks with augmented reality walking navigation for Google Maps, Apple has its sights set on the road.

As you might know, Tidal differentiates itself from the competition with its audio quality. Unlike Spotify and Apple Music, it aims to give its subscribers studio quality audio from any device. However, before you sign up for Tidal, be aware there are few steps you need to take in order to stream such high-quality music.

So you've been using iOS 13 for a little while and noticed your iPhone is pretty slow to charge. Using the 5-watt power adapter out of the box, in the time it used to take your iPhone to charge its battery to 100 percent, your iPhone is stuck at 80% or below instead. That's because Apple introduced a new feature in iOS 13 that slows down charging — but for a good reason.

If online retail is war (and who says it isn't), then CGTrader is prepared to arm its allies with augmented reality ammunition.

In case you thought the long and unfortunate story of ODG was over, hold on, there's one last chapter to tell.

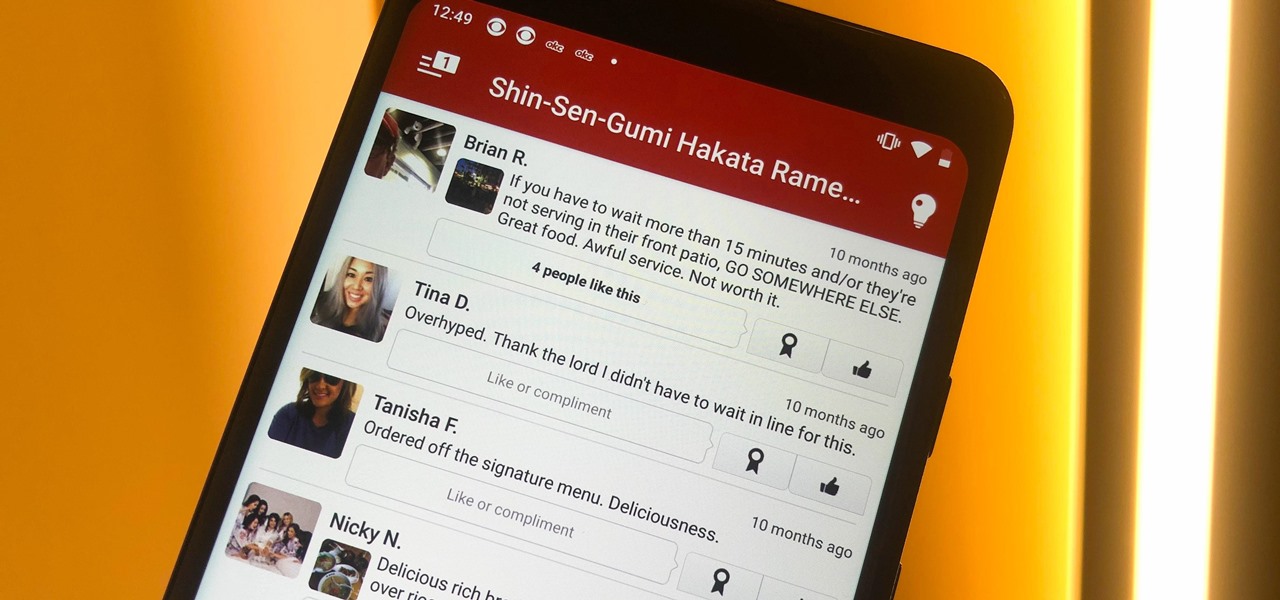
Yelp reviews are great for getting a feel for how a business operates, but they can't always be trusted, and they don't always get to the point fast enough. That's where "Tips" come in, and you can view and make them whether you're on an iPhone or Android phone.

Smartglasses maker Vuzix has emerged with the first hardware powered by the Snapdragon XR1 chip, roughly nine months after Qualcomm introduced the chipset designed to drive augmented reality wearables at the Augmented World Expo in Santa Clara.