At its F8 developer's conference in 2016, Facebook went on record with a roadmap that called for augmented reality integration into Oculus within 10 years. Now, it appears as though Facebook is accelerating those plans.
Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

After joining Google and Huawei in underwriting the UW Reality Lab at the University of Washington in January, it appears Facebook is already seeing a return on its donation.

Magic Leap One owners with itchy trigger fingers may have their itch scratched next week, as Magic Leap has shared a brief teaser on Twitter for the long-awaited Dr. Grordbort's Invaders game from Weta Workshop.

The Super Bowl of bicycle racing, the Tour de France, added augmented reality to its TV broadcast this year.

Fast-casual burger restaurant Bareburger expects to soon replace all of its paper menus with 3D models of its burgers and other items rendered in augmented reality, but for now, the company is preparing some rather interesting limited AR interactions.

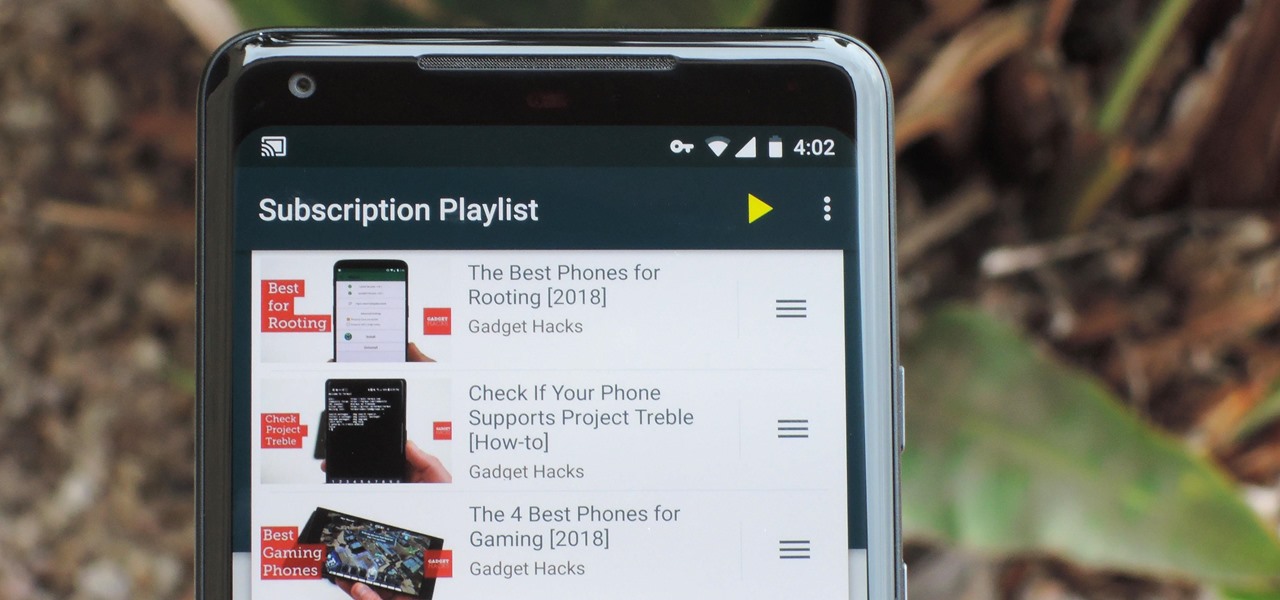
Sometimes I'm convinced Google has ADHD. They'll create a great product, then get distracted by the next moonshot and never put the finishing touches on their last project. Case in point, you can't just cast a playlist of your subscriptions from YouTube to Chromecast, even though that's how many people prefer to use YouTube.

When a firm like Techstars believes that augmented reality is an attractive industry to invest in, there's a high probability that it's right.

A vaccine against HIV might prevent the disease that we can't seem to cure. Some HIV patients make antibodies that can take down the virus, much the way a vaccine might. But, scientists haven't been able to provoke that type of response in other people. However, in a process that might work in humans, a group of researchers has successfully generated antibodies in cows that neutralize multiple strains of HIV.

Today at Microsoft Build 2017 in Seattle, Washington, ScopeAR announced that their mixed reality smart instruction development platform, Worklink, will now work with the Microsoft HoloLens in addition to the mobile devices that are currently supported.

In a race to make self-driven cars mainstream, Intel announced today that they've bought Israeli microchip technology company Mobileye for $15.3 billion, setting the stage for Intel to dominate a large portion of the driverless market.

Microsoft has the HoloLens and Google has their money on Magic Leap (as well as their own Tango and Cardboard, among others), but we've heard next to nothing about how Apple plans to enter the virtual/augmented/mixed reality space. A new patent offers some clues.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Hello everyone. It's been a while since I've posted anything (with good reason). But, now that the digital dust has settled, it's time to be an adult about this. I will be continuing to post to Null Byte on a smaller scale, and will also fully participate in whatever communities Null Byte members branch into.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Hello everyone Today I will show a different way to exploit a windows machine with a reverse https payload..."wait...why https? Isn't tcp good anymore?"

Live Photos is an interesting new feature introduced by Apple on the iPhone 6S and 6S Plus models that captures the moments immediately before and after you snap a picture in the Camera app, resulting in a GIF-like animation.

Chromecasts can make for some fun nights. Whether you're setting up a collaborative YouTube watch list, letting everyone add to a giant party playlist, or playing games like Cardcast and Big Web Quiz, Google's streaming media stick is a hit by all accounts.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Are you constantly traveling? Well, as a Hilton HHonors member, you can enjoy special treatment at all of their hotels and resorts. It's free to register, but the difficulty lies in climbing up their membership level. To reach Gold elite status, Hilton HHonors requires that you have a minimum of 20 stays, 40 nights, or 75,000 base points—all in one year. While this may very will be easily attainable for those with jobs that revolve around traveling, it's almost damn near impossible for the re...

The new Pyro FX in Houdini 10 are very impressive with improved workflow. The Pyro FX are great for creating 3D fire and smoke effects. And in this video tutorial series, you will learn the Pyro FX workflow in-depth and the parameters used to create fire and smoke effects. You will also see how volumetric data is created and recorded, and how to visualize it.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

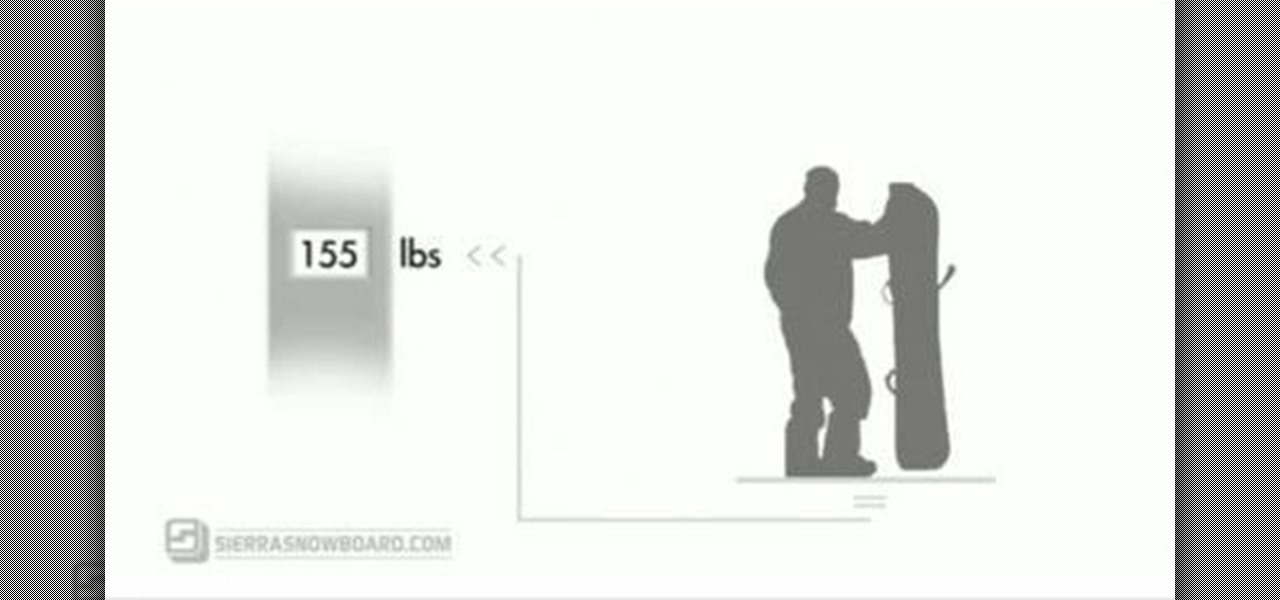
In this video, Sierra Snowboard gives us some tips on how to select the snowboard that's right for you. Each board comes in a number of different sizes, and most boards come with a size chart specific for that board. These charts can be vague, but are good starting points for selecting your size. One thing to consider is your bossy type. The weight of the rider is the primary factor in selecting the size of a snowboard. You'll notice that the height of a rider is not listed on a size chart. I...

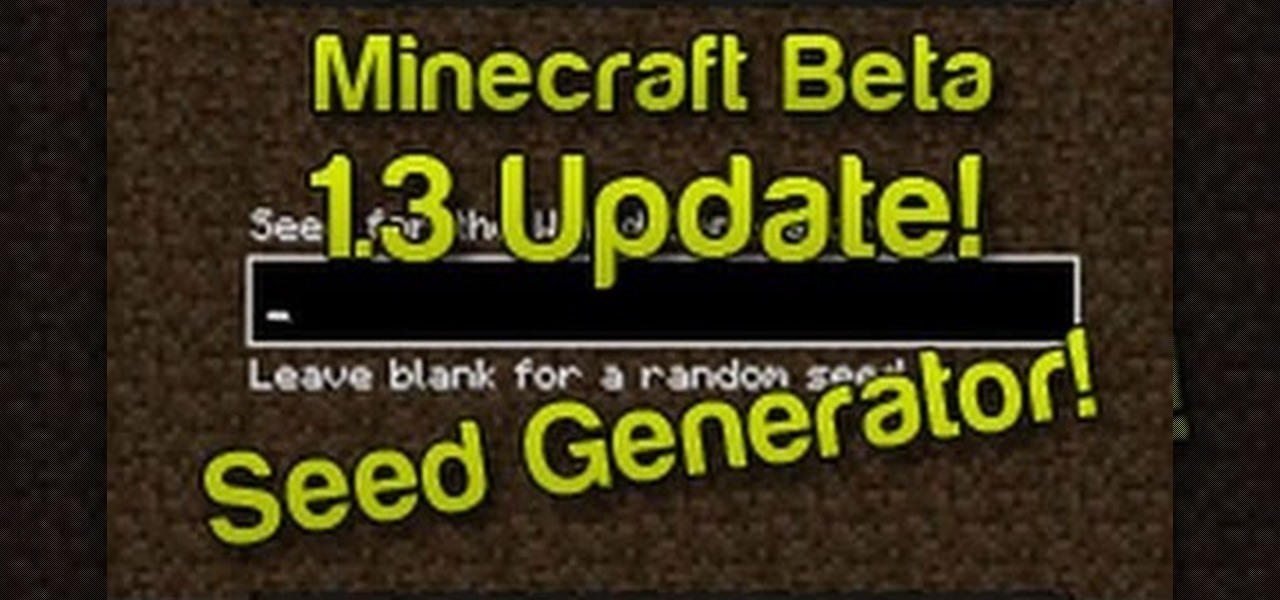
Minecraft generates a new world every time you start a new game. This adds tremendous replay value, but also means you can easily get screwed by starting a game that's in a world that just happens to suck. No more! The 1.3 Beta update released in February allows you to both create as many world as you want AND do many more things with seeds than before. Every world has a seed, and now you can save the seed from any world you make to reuse later and load millions of seeds preloaded into the ga...

Hydrazine sulfate has many uses, but most notably, it's been used under the trade name of Sehydrin, a treatment for anorexia, cachexia and some even think cancer. But for we DIY chemists, it's useful for something entirely different— as a substitute for the more dangerous pure liquid hydrazine in chemical reactions. NurdRage shows you how to make it via some hypochlorite and the Ketazine process.

C For Chemistry delves into the chemistry of science experiments. This chemist knows what he's talking about. These chemistry experiments are not only fun, but very educational for all of those interested in scientific chemical reactions and properties.

Watch this science video tutorial from Nurd Rage on how to make copper sulfate from copper and sulfuric acid in three ways. They show you how to make copper sulfate from copper and sulfuric acid using two chemical methods and one electrochemical method.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to use the iPod and Genius on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

Watch this science video tutorial from Nurd Rage on how to make nitric acid. They show three ways to make nitric acid based on two different chemical approaches, both of which can be done using easily accessible materials.

Make sure you use FLASH Player 9 First: Deinstall Flash Player 10

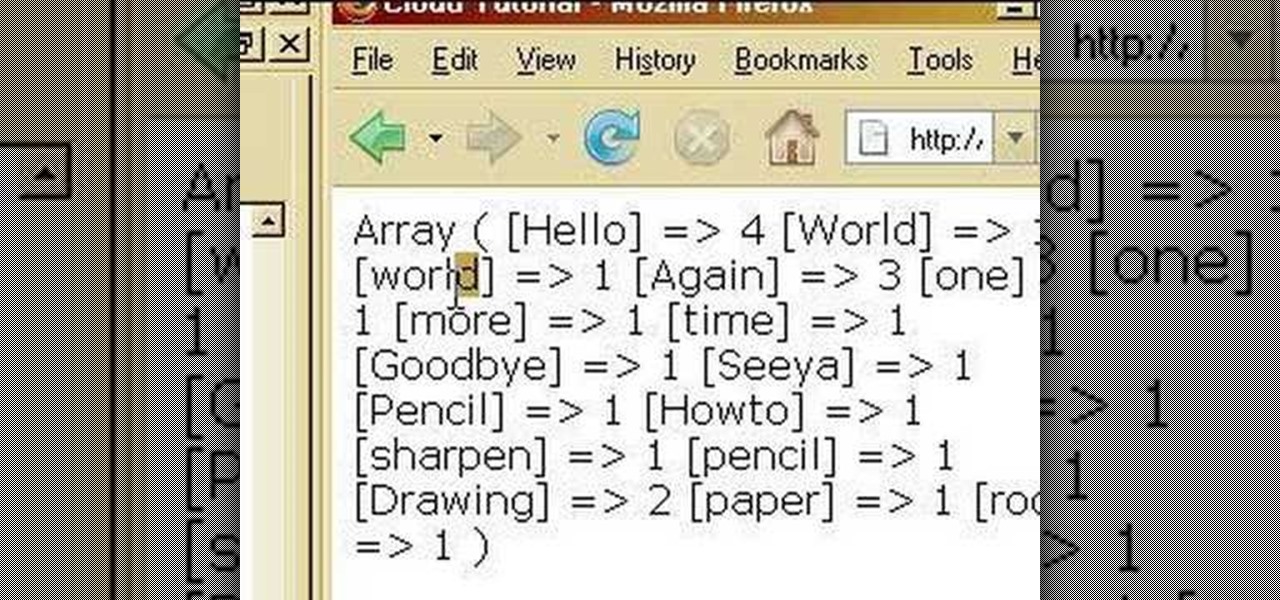
How to generate a tag cloud - a collection of tags that displays keywords in different sizes based on their frequency of use - using PHP.

QR codes are so handy. Nowadays, all you have to do to scan one is open your phone's camera app and tap a button. But creating one is a different story — online QR code generators aren't always trustworthy, and most phones don't have a built-in feature for it. Thankfully, Google Chrome now does.

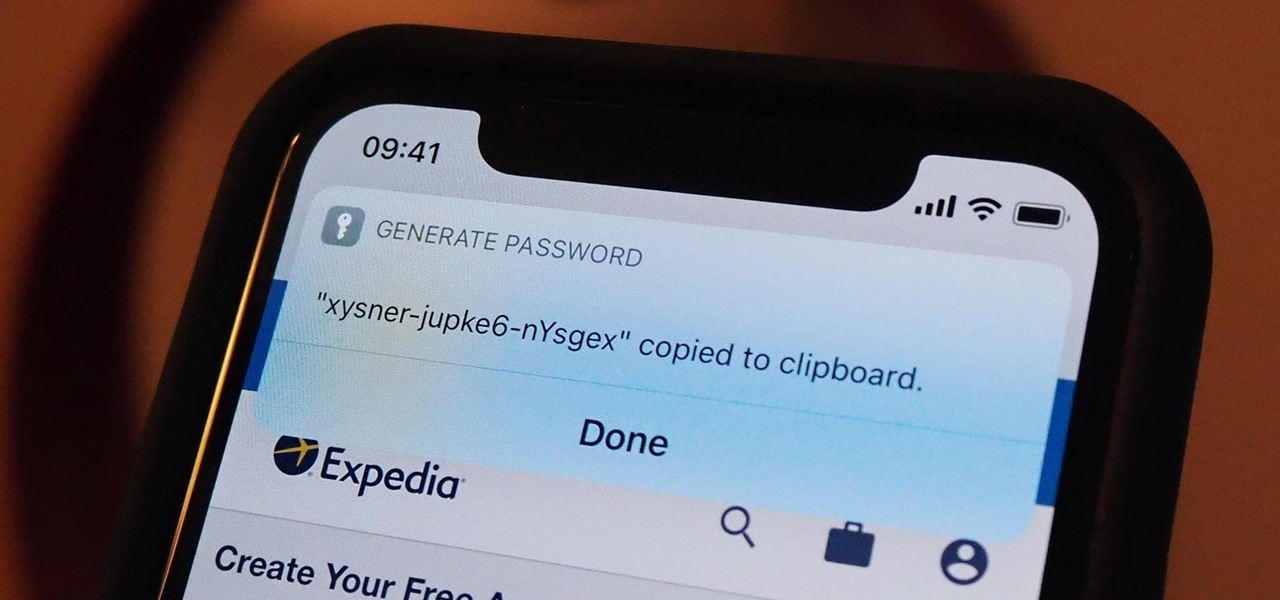
Apple's password manager, iCloud Keychain, lets you securely save important login credentials for apps, websites, and services that sync up across all of your Apple devices — iPhone, iPad, iPod touch, and Mac. One of its biggest highlights is that it can create strong passwords for you. Unfortunately, it doesn't always work, and in those cases, there are other ways to generate random, strong passwords.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Win you opponent at squash. This how to video is a quick squash playing tutorial that goes over some of he basics of the sport. Learn about proper racquet grip, writs tension, and how to generate power in each stroke.

Check out this video tutorial on how to generate an Excel worksheet using XML. There's a free library from CarlosAG.net, and you need to get the free dll file from there. This video will show you how to use it. You need to use CreateExcelFile in Microsoft Visual Studio to use the XML. You will need to use Microsoft Excel 2003 or 2007 to open this file.