It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.
Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

With Avatar, Facebook's personalized stickers for use on its social and messaging platforms, those who aren't on Facebook or have otherwise dumped the social network may feel left out.
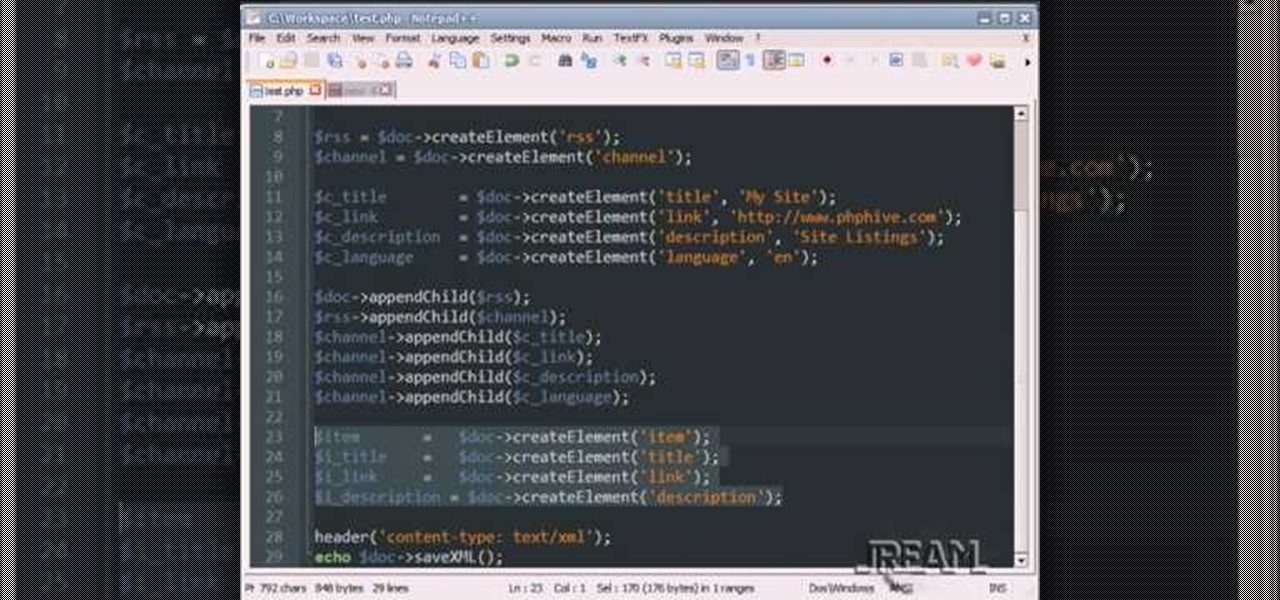
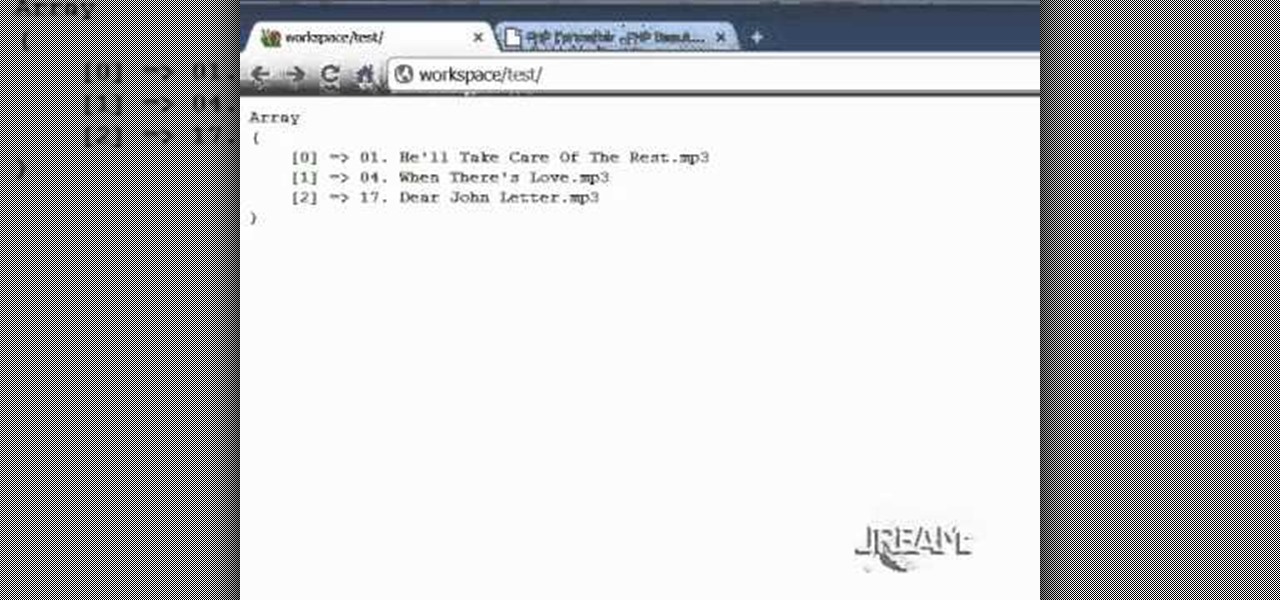
This tutorial teaches you how to create an RSS feed with PHP using DomDocument. You can generate the items with a database loop, and this example uses a very simple array. Take a few minutes and add some more knowledge to your PHP world.

If you're programming with PHP and you generate a list of music files, you'll want to find a way to play them. This video shows how to use the Yahoo Media Player to play the list of mp3s you've created, with your PHP coding.

In this clip, you'll learn how to generate admin command prompts on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

Want to design a playing card logo? With Adobe Photoshop, the process is simple. Whether you're new to Adobe's popular image editing software or simply looking to pick up a few new tips and tricks, you're sure to benefit from this free video tutorial from the folks at IT Stuff TV. For more information, including step-by-step instructions on how to generate your own digital playing cards in Photoshop, watch this graphic designer's guide.

Generate a 3D leaf logo in Adobe Photoshop! Whether you're new to Adobe's popular image editing software or simply looking to pick up a few new tips and tricks, you're sure to benefit from this free video tutorial from the folks at IT Stuff TV. For more information, including step-by-step instructions on how to create a 3D leaf logo in Photoshop, watch this graphic designer's guide.

Want to design vector (i.e., infinitely scalable) animal characters? With Adobe Photoshop, the process is a breeze. Whether you're new to Adobe's popular image editing software or simply looking to pick up a few new tips and tricks, you're sure to benefit from this free video tutorial from the folks at IT Stuff TV. For more information, including step-by-step instructions on how to generate your own cute, non-scalar mouse head logo.

Want to make a Windows Vista-style icon? With Adobe Photoshop, the process is a breeze. Whether you're new to Adobe's popular image editing software or simply looking to pick up a few new tips and tricks, you're sure to benefit from this free video tutorial from the folks at IT Stuff TV. For more information, including step-by-step instructions on how to generate your own Vista-style logos in Photoshop, watch this graphic designer's guide.

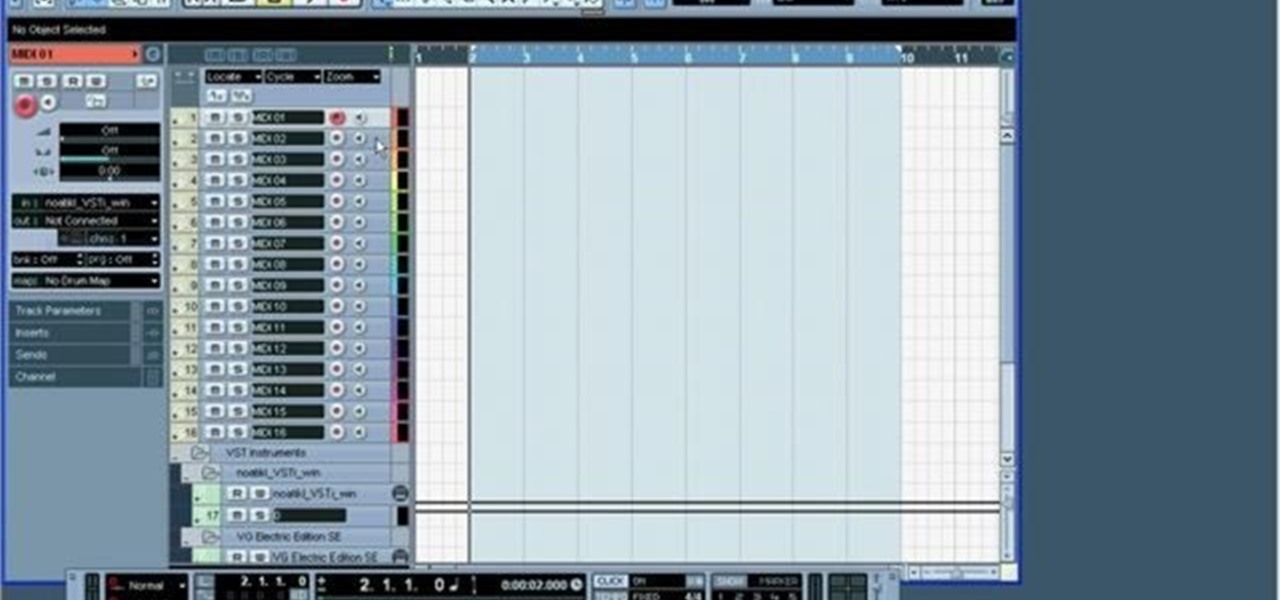
This video tutorial shows how to use the noatikl generative music VSTi with Cubase, for both Windows and Mac. noatikl is a generative (MIDI) music engine. It creates musical information in the form of MIDI notes, and can also generate and send MIDI controller information.

You can learn how to make the ice hockey side stop. Side stops is a side motion stop; not a snowplow stop. You need a strong knee bend to generate that scraping, stopping motion.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

While chatting in Hangouts on Android, inserting an emoji or animated sticker can instantly make the conversation more fun, but they'll eventually lose their charm, as most things do. Even if you add GIFs to your texting arsenal, things could get stale. That is, unless they're personalize GIFs you actually make yourself (the process is really simple).

Snapchat popularized personalized stickers for social media and messaging with Bitmoji, followed by walled-garden versions from Apple with Memojis and Samsung with AR Emojis. Even Google has gotten into the game, integrating an emoji generator for Gboard.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

A vaccine against HIV might prevent the disease that we can't seem to cure. Some HIV patients make antibodies that can take down the virus, much the way a vaccine might. But, scientists haven't been able to provoke that type of response in other people. However, in a process that might work in humans, a group of researchers has successfully generated antibodies in cows that neutralize multiple strains of HIV.

Flu vaccines can help prevent us from getting or suffering the most severe effects of the flu. But, each vaccine only protects us from three different strains of the flu. If we don't have a vaccine against all types of flu, it leaves us open for an epidemic with a flu virus we didn't expect.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

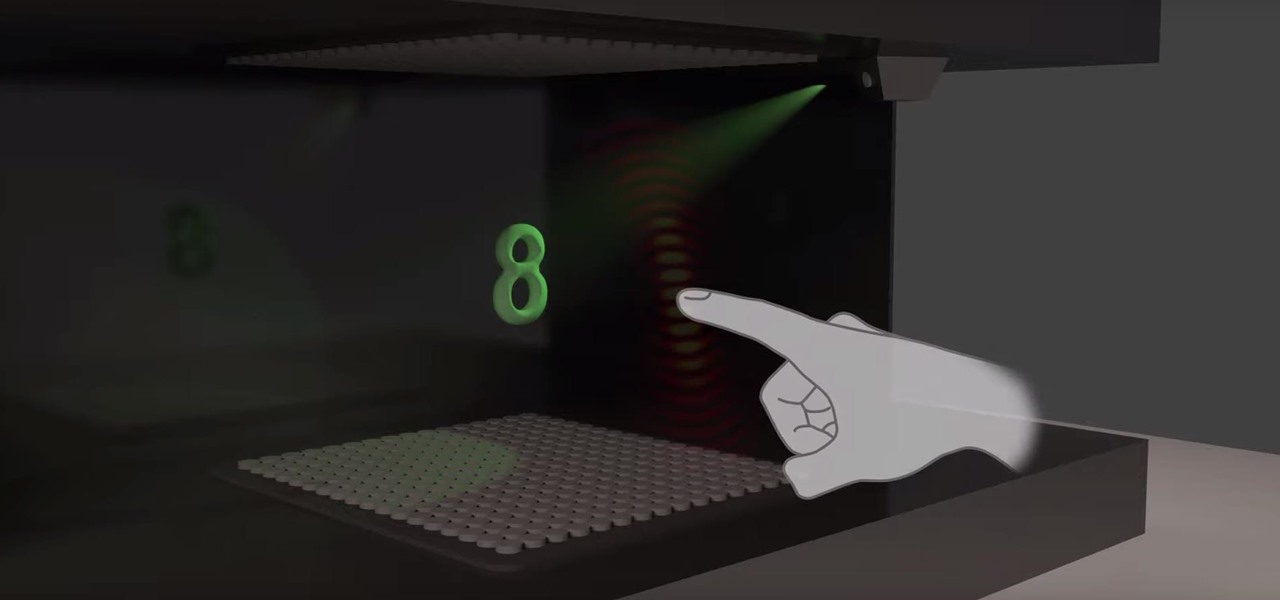
Most augmented reality experiences are purely visual, with spatial audio gaining in popularity to make visual experiences more realistic. However, leveraging the sense of touch may be the next frontier for AR experiences.

At its F8 developer's conference in 2016, Facebook went on record with a roadmap that called for augmented reality integration into Oculus within 10 years. Now, it appears as though Facebook is accelerating those plans.

The Super Bowl of bicycle racing, the Tour de France, added augmented reality to its TV broadcast this year.

In off-record discussions with AR experts, the consensus on ARKit is that it takes a software approach to the depth-sensors available on Tango devices. As a result, the toolkit has shortcomings, such as detecting walls and vertical surfaces.

In the perpetual search for a renewable and convenient energy source, our bacterial friends have once again stolen the limelight.

Microsoft has the HoloLens and Google has their money on Magic Leap (as well as their own Tango and Cardboard, among others), but we've heard next to nothing about how Apple plans to enter the virtual/augmented/mixed reality space. A new patent offers some clues.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

When I see the words "free trial," I know I'm probably going to have to whip out my credit card and enter in the number to "not get charged." Then I end up forgetting about the trial and want to kick myself in the ass when I see my statement at the end of the month.

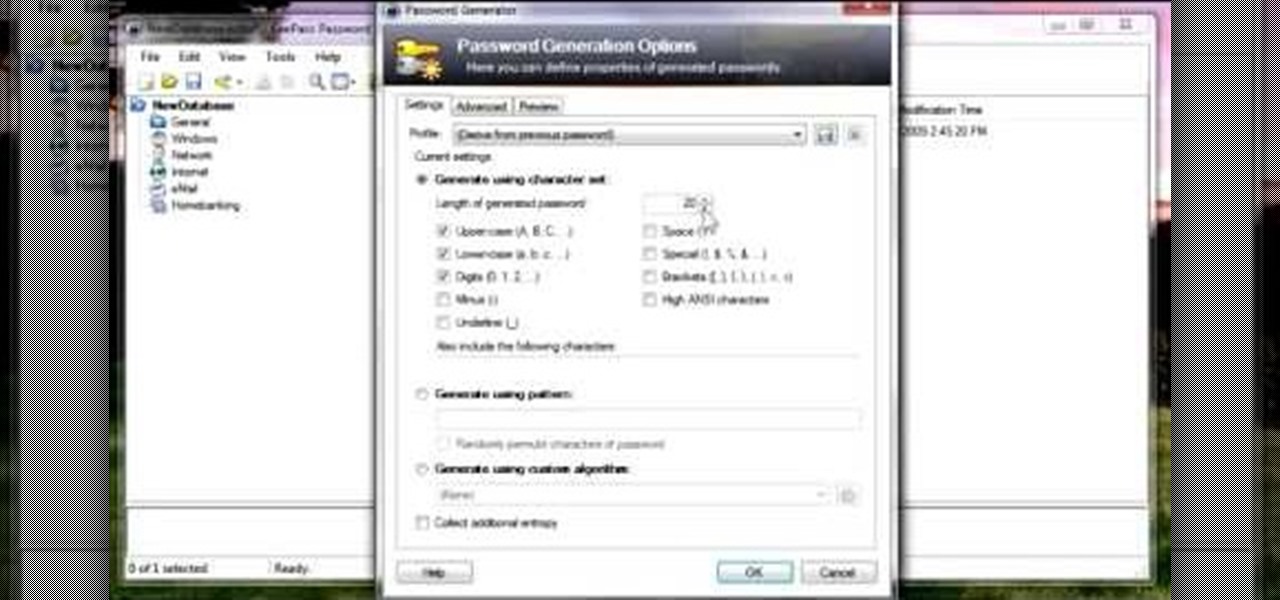
In this video, we learn how to use KeePass password generator. First, open the entry to edit the existing password and type in your username and e-mail address. Type in notes if you need it, then click on the bottom key icon. This will generate a password for you when you click on it and cover it up. If you click it once more, it will uncover what the password is. You can decide what kind of password you want and make one specific for the account you're using. When finished, you will have a n...

There are three components of hitting a 300 yard drive in golf. 1st component is make sure that the top edge of the club should be below the top of the golf ball. The second component is making a complete turn in the back swing. The shoulder here should turn more than 90 degrees. The third component is to swing with tempo so as to maintain the rhythm and balance of your body. This step of the tee consumes more than 80 % of the potential energy of your body. So using these 3 steps you automati...

If you're like me, you don't have time to sit down and leisurely read an entire article from start to finish — but you still want to be informed throughout the day. Instead of just browsing the daily headlines, there's a free service that will summarize any article you throw at it, giving you a better idea of what's going on without committing to reading an entire article.

The US Department of Treasury isn't generally known for being on the very edge of technology innovations (see the current hubbub around crypto), instead usually waiting until certain tools have been battle-tested in the mainstream or enterprise sector.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.