By now you're probably already an expert at creating cover images for your Facebook Timeline, especially if you've taken advantage of those free Facebook cards that were (and still are) being offered. But just in case you need some help making eye-grabbing cover images, there's a few tools you can try out to streamline the process.
With the holidays right around the corner, it's easy to miss a big software update on your iPhone, and by that, I mean iOS 15.2, which was pushed out Monday, Dec. 13. There's a surprising amount of new features and changes in the updated firmware, and there are a few big ones you need to know about.

Disney Plus shows WandaVision and Falcon and the Winter Soldier are both streaming hits, but the two series could not be more different in terms of giving fans a taste of the Marvel Cinematic Universe.

The global gaming market is expected to generate $160 billion in 2020. With emerging markets in the Middle East and Africa, the planet's 2.5 billion gamers are always looking for the next great adventure.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Apple is giving iPhone owners even more options to express themselves via Animojis with a wide range of customization options for their personal Memojis.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

The augmented reality industry has an insatiable lust for 3D content, which makes an investment of $48 million into Matterport a no-brainer for investors.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Augmented reality app developer Laan Labs has shared a preview of a beta app that achieves 3D scanning with just an iPhone and produces highly-detailed models for sharing with others.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks.

On Monday morning, secretive augmented reality startup Magic Leap revealed a collaboration with Icelandic music group Sigur Rós. But the story detailing the app didn't reveal anything more than a still image of the interactive Tónandi app, leaving most of us to use to our imaginations in terms of visualizing how it worked.

Do you know when you're going to die? Your iPhone or iPad does. That's the premise behind Death Mask, an experimental app developed by Or Fleisher and Anastasis Germanidis.

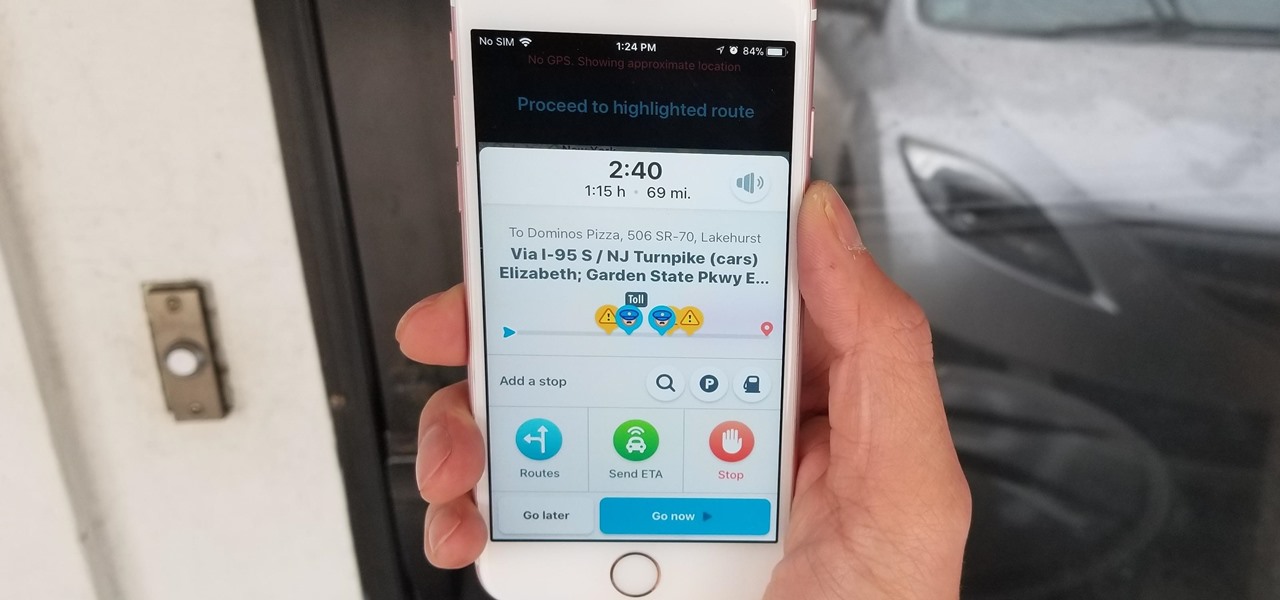
Discovering you're on a route filled with tolls while you're already on the road, with no cash on hand, is never a pleasant surprise. Fortunately, Waze has an incredibly simple solution to nip this potential headache in the bud and save you money while navigating.

Geotagging your location on Instagram is one of the most undervalued ways to generate traffic to your profile. The beauty about adding your location to your IG posts is that it allows you to be seen by other users than the ones that already follow you.

When it published its 2016-2017 catalog last year, Savannah College of Art and Design (SCAD) became the first college to leverage augmented reality technology for a college catalog.

Legacy Games, developer of mobile games for children, has just updated Crayola Color Blaster, an augmented reality Android adventure for Google Tango devices, with new content.

This is a quick and easy method for receiving the backend IP (1) of a server who is hidden behind a proxy (2) or a firewall (3).

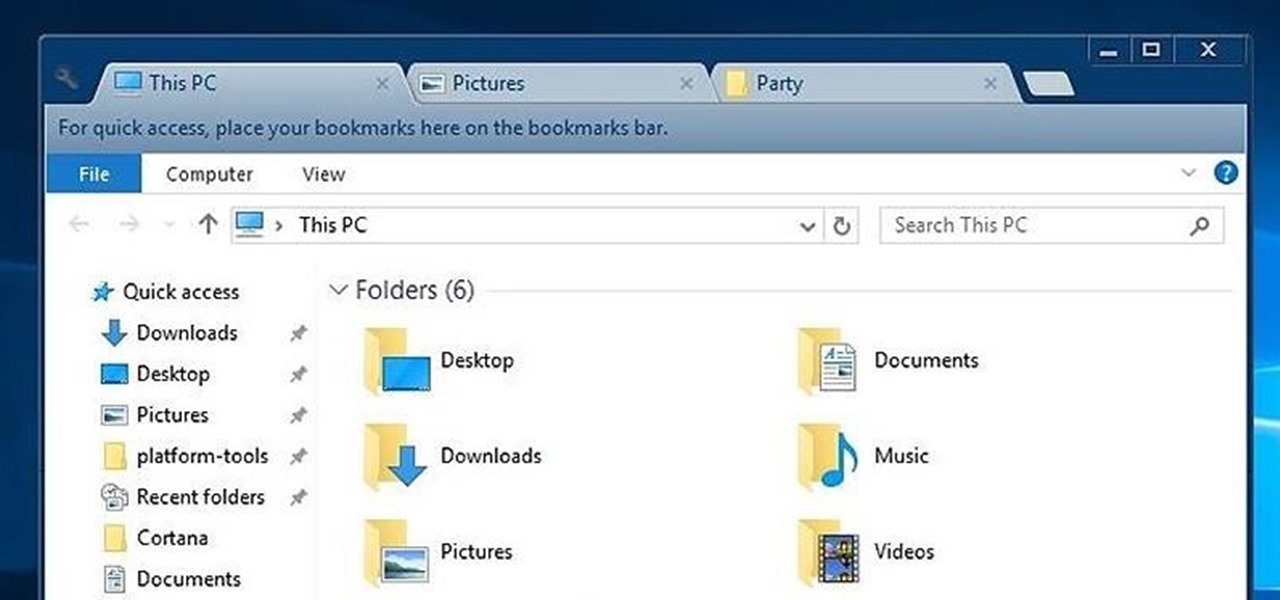
While Windows 10's new File Explorer is just as, if not more, useful as it was in previous iterations of Windows, it could definitely still be better. Two features that would greatly improve File Explorer are tabbed results and a customizable user interface, similar to how they are in Google Chrome.

As with any software, Android apps can occasionally suffer from bugs. But finding the root cause of such issues can often be difficult, and reporting bugs is a cumbersome experience.

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

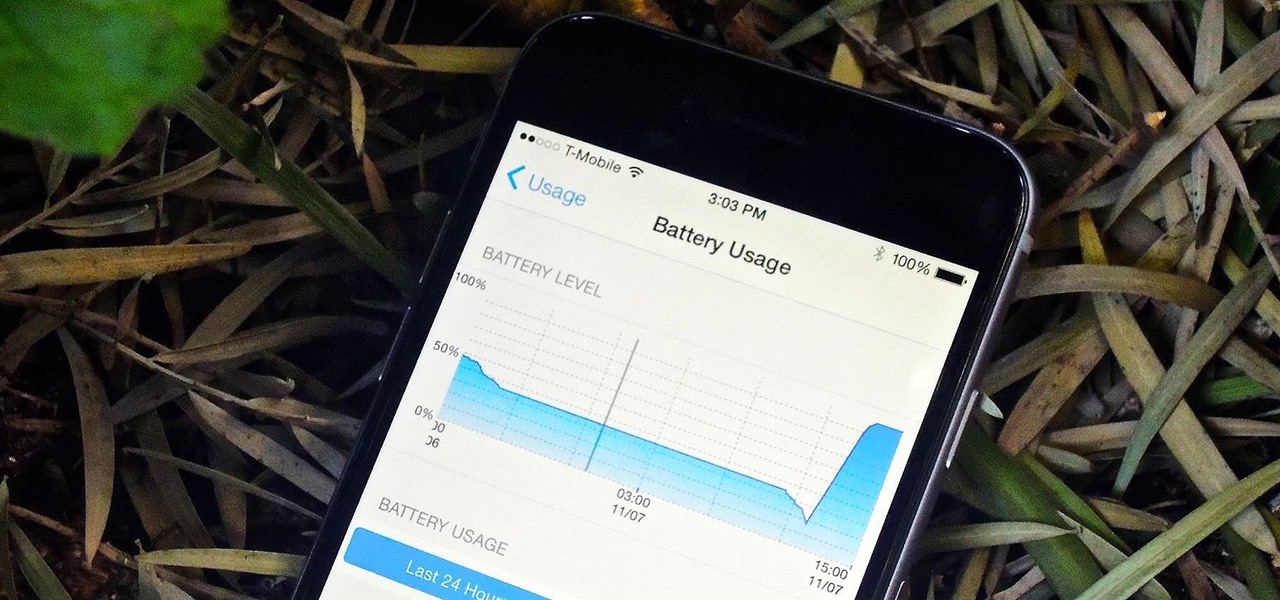
One of my favorite new additions to iOS is the ability to view battery usage stats on a per-app basis, which is helpful in knowing exactly which apps are taking up all of my iPhone's battery life. If you jailbreak iOS 8 on your device, you can take Apple's stock battery stats feature even further to give you details on how those apps are actually using the battery.

HTC is one of the few OEMs that make it easy to unlock the bootloader on their devices. And while they do warn you that doing so voids your warranty, they don't tell you that it also prevents you from collecting promotions that come with their devices.

This past year, Facebook spent $19 billion purchasing the popular messaging app WhatsApp, and for good reason. Mark Zuckerberg isn't going to spend that type of money on just any application. WhatsApp is widely popular and frequently used by more than 500 million users worldwide, which is almost twenty percent of the Earth's population.

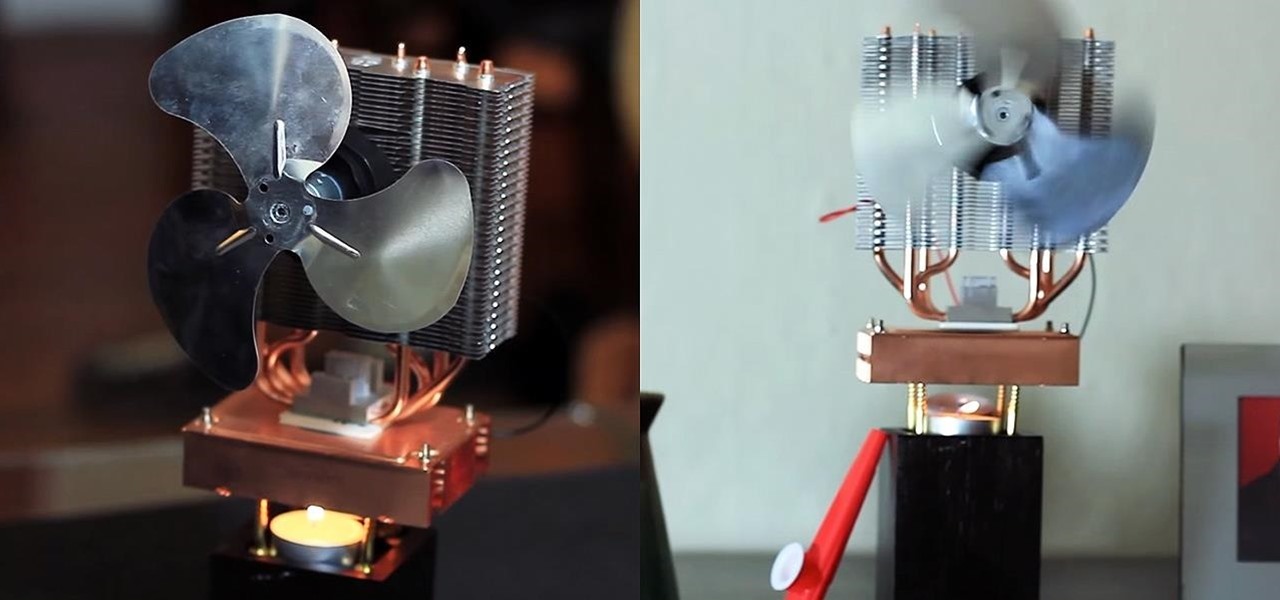
Staying cool in the summer heat sometimes feels like it takes all the energy in the world. But what about a fan using no-cost electrical energy? If you're looking to keep cool during a power outage, or if you don't want to break the bank by running your DIY air conditioner all day long, you can use candlelight to power a fan!

There are thousands of fonts you can download online. Some are free, some you have to pay for, but they all have something in common—if you can get them, so can everyone else. If you want a truly unique font that no one else is using, you have to make your own, and what's more unique than your own handwriting?

Every iPhone, iPad, and iPod Touch owner has that one folder which contains those never used apps. You know what I am talking about, the folder that contain Stocks, Voice Memos, Game Center, Compass, Newsstand (That's right, iOS 7 allows Newsstand to be placed in a folder!!). What do you call that folder? "Junk," "Hardly Used," "CrApple?" Why not call it nothing at all.

Striping tapes are very popular these days , among nail enthusiasts. One of the main reasons is that not only is it super easy to use, but you can literally create hundreds of styles by using them right !

Feeling nostalgic for Super Mario Kart, but don't want to fire up the old Super Nintendo? Never fear, with a free Flash-based emulator called SNESbox, you can relive the 90s and play all your favorite games right from your browser, without having to install anything. With 1,861 games, if there's something made for the Super Nintendo that you want to play, they almost certainly have it. Sure, there are tons of emulators you can use, but SNESbox is different in that it gives you the ability to ...

Google has just launched a new revolutionary augmented reality game for Android called Ingress. Their new mobile game centers around the fight for control of the minds of everyone here on Earth. It's a freaking worldwide fight—from your smartphone! While augmented reality in is nothing new in the smartphone gaming world, it has never seen the likes of this. With an almost Halo-like storytelling, Ingress seeks to bring out gamers all across the globe to perform physical activities by transform...

For this project, I decided to rip apart a microwave I found in my neighbor's garbage can to see what was inside. With permission, of course! True story!

There's no charge for this electricity! All you'll need for this project is... Now, watch and learn how to make your own emergency power if you find yourself in a bind.

I'm always looking for solutions to problems people are having with their smartphones. This means I spend a lot of time browsing forums and release sites looking for new apps. In doing so, I find a lot of apps that don't quite solve a major problem, but are nonetheless pretty cool. I came across four of those this week.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.