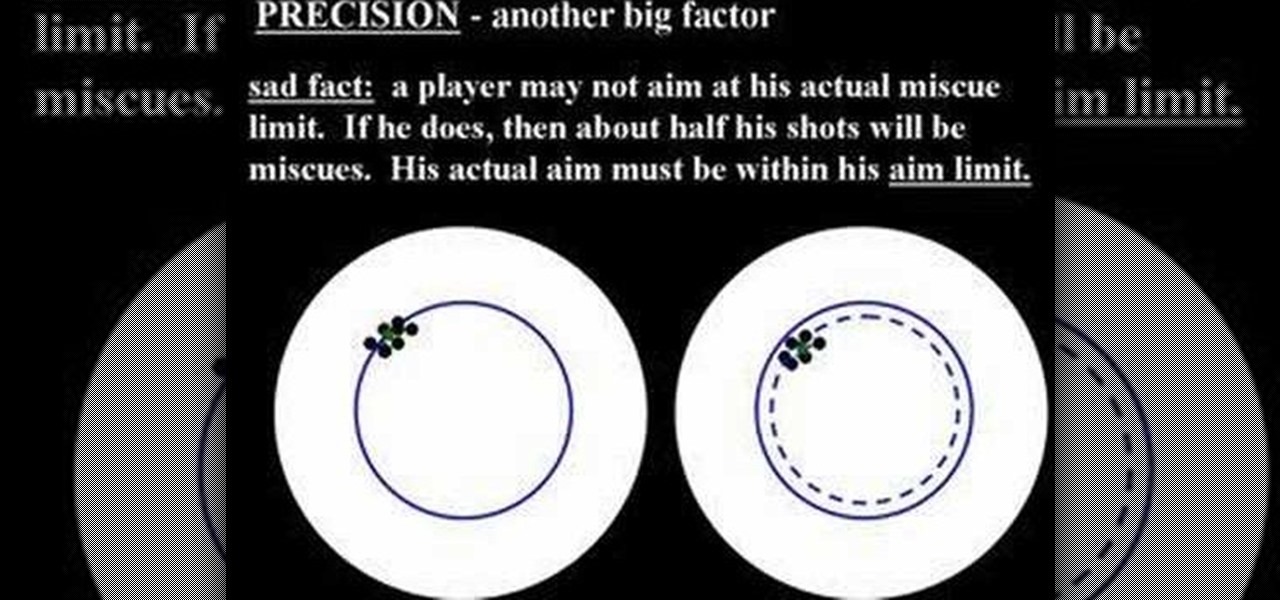
Cue ball draw refers to the way a cue ball strikes a rack of balls. In particular, if the cue ball is hit low on the ball, when it strikes a rack of balls, for the break, it will have enough backspin to wind its way back to the shooter.

This video explains how to throw a football like a quarterback. With your elbows bent at a 90-degree angle, hold the ball in front of your chest with the fingers of your throwing hand across the laces of the football.

PDFs are the industry standard for document sharing. However, sometimes PDFs generated by non-Adobe apps can tend to be larger than they need to be. In this video you’ll learn how to make your PDF files smaller even if they were not generated by an Adobe product.

In the perpetual search for a renewable and convenient energy source, our bacterial friends have once again stolen the limelight.

Closed captions are great for watching YouTube videos on mute, or simply following along with a video that's hard to understand. It's easy to turn on captions on YouTube's desktop site, but in the YouTube Android app, the closed captions settings are tucked away.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

If you thought Google was sitting on the sidelines of the growing race toward mainstreaming augmented reality, think again.

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

Drawing in Apple Notes can be fun, but our sketches may not always turn out as polished as we'd like (cue the "my 5-year-old can draw better than that" jokes). Thankfully, Apple's new Image Wand feature in iOS 18.2 and iPadOS 18.2 aims to make creating professional-quality visuals a breeze, even if you lack artistic skills.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

Your smartphone has a ton of ringtone options built in, but ringtones haven't really changed much in the past decade, and it's definitely not cool to hear someone in the supermarket with the same lame ringer. While replacing the stock sounds with a song of your choosing is the best way to keep your phone personalized, why not go a step further using a video?

Playing around with plastic lightsabers is juvenile; playing around with digitally generated, realistic-looking lightsabers is gangsta.

Jeff Schell walks you through a few quick methods of making your titles appear less "computer-generated." This includes adding a linear gradient fill to the title as well as adding a soft Gaussian Blur to reduce the "computer crispness" of the text.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

Hello everyone. It's been a while since I've posted anything (with good reason). But, now that the digital dust has settled, it's time to be an adult about this. I will be continuing to post to Null Byte on a smaller scale, and will also fully participate in whatever communities Null Byte members branch into.

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Magic Leap One owners with itchy trigger fingers may have their itch scratched next week, as Magic Leap has shared a brief teaser on Twitter for the long-awaited Dr. Grordbort's Invaders game from Weta Workshop.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

Video: . Nobody likes an RV or camper toilet that smells, this video will show you how to prevent your RV toilet from smelling.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

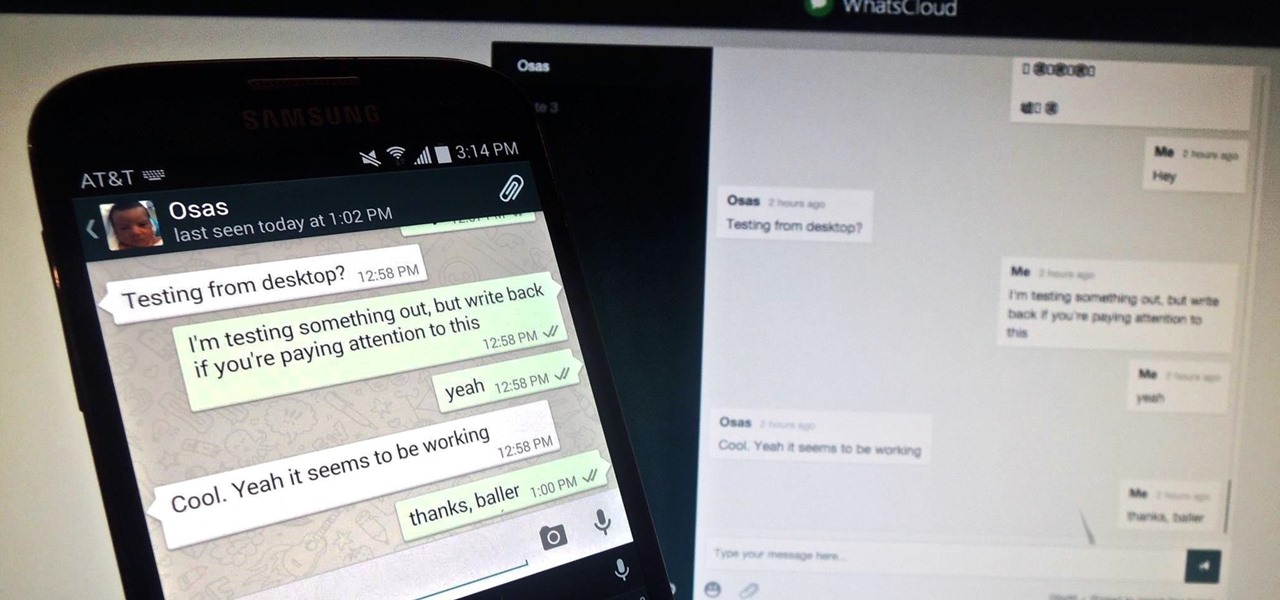
Pretty much my only gripe with computer-side messaging clients like Mighty Text is that they don't allow you to send and receive messages shared through WhatsApp, the popular third-party messaging application, which was purchased earlier this year for $19 billion by Facebook.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

In this how to video, you will learn how to make a tight rope walking magnet. You will need a power supply with currents between 15 to 25 amps. A thick wire from a half to one centimeter is also needed for the tight rope. A small neodymium magnet will also be required. String the wire from one end to another. Place the magnet at one end. Use a pair of pliers and a piece of metal as a switch to run the current through the wire. Once that is done, the magnet should go down the wire. A magnetic ...

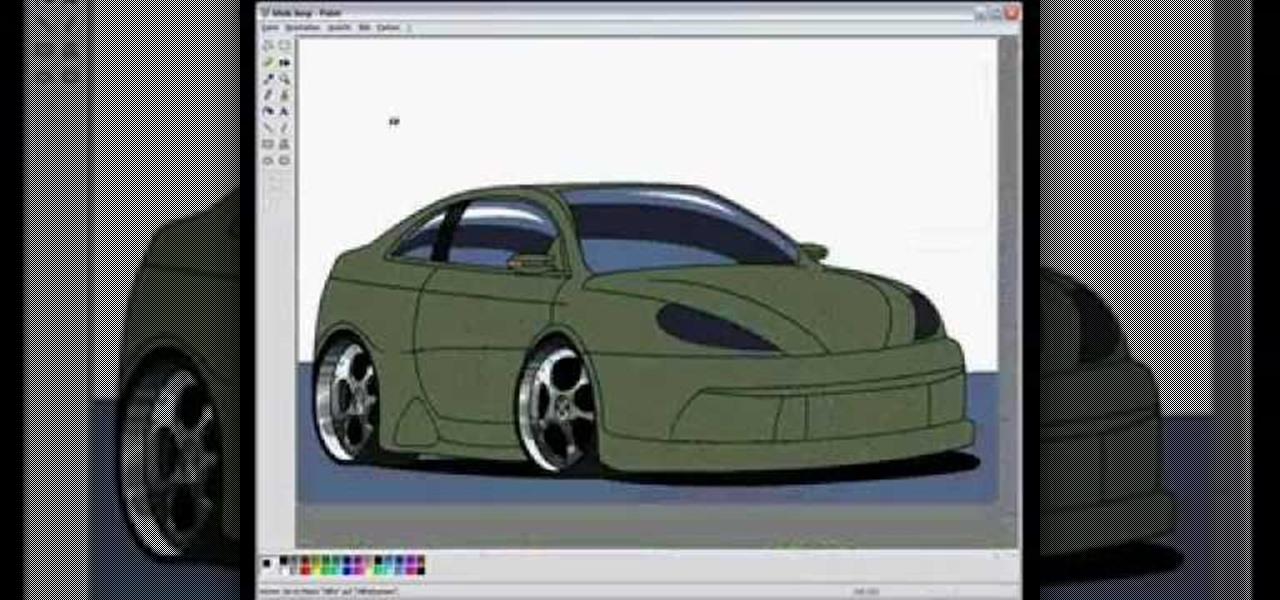
Ever wonder why Windows comes with MS Paint? Well, from this video v=ElrldD02if0], it's amazing how that tiny, little program so often overlooked by most people can, in the right hands, be used to create stunning computed generated drawings. In this video, the author records himself drawing a concept car from scratch. There are no audio or text comments, but rather the video teaches by example. The author time-compressed his work, so don't expect to make a similar work in only five minutes!

The wait wasn't so long this time. Apple released public beta 3 for iOS 13 on Thursday, July 18, just one day after the release of developer beta 4. For context, Apple took five days to seed public beta 2 after releasing dev beta 3, so it's a pleasant surprise that the latest public beta dropped so soon.

We're pumped for iOS 13 and all of the fresh features and changes that come with it. Developer beta 3 came with new features in the double digits, including AR eye contact in FaceTime and mouse cursor size customization. Developer beta 4, released today, has a few more additions and changes as well.

The third developer beta for iOS 13 has been out since July 3, and while devs have had fun exploring all the new features, those of us on the public beta have sat on the sidelines running the public version of dev beta 2. But we don't need to wait any longer, as Apple just released iOS 13 public beta 2 and all the goodies that come with it.

On July 3, Apple pushed out iOS 13 developer beta 3 for iPhone, and there's a lot found hidden within. A new FaceTime setting, more Arcade details, full-page scrolling screenshots everywhere, a noise cancellation option in the Control Center, and a new markup tool — and that's just a few of the new features.

There's no doubt iOS 13 has dominated the talk around the Apple community this month. Since the announcement and release of the first developer beta, we iPhone users have had a treasure trove of new features and changes to explore and discuss. Now the fun continues with iOS 13 dev beta 2. Who's ready to start up the conversation all over again?

The first developer beta for iOS 13 is available to install on iPhone models, but the process for doing so may be a bumpy ride. Apple has not included configuration profiles for the developer beta yet, and many developers are having issues installing iOS 13 even with macOS 10.15 Catalina installed. Plus, since this is the first beta, there are a lot of problems with old and new features to work the kinks out of.

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

After dipping its toes into the AR cloud arena last year, Ubiquity6 is now jumping in with both feet this year.

Former soccer star and current celebrity David Beckham has the augmented reality abilities of Facebook and Instagram as allies in the effort to eradicate malaria from the world.

Just days after Bose did its best to frame a pair of glasses frames with spatial audio as "augmented reality," a patent application from Magic Leap, surfaced on Thursday, March 15, offers a similar idea, but with real AR included.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.