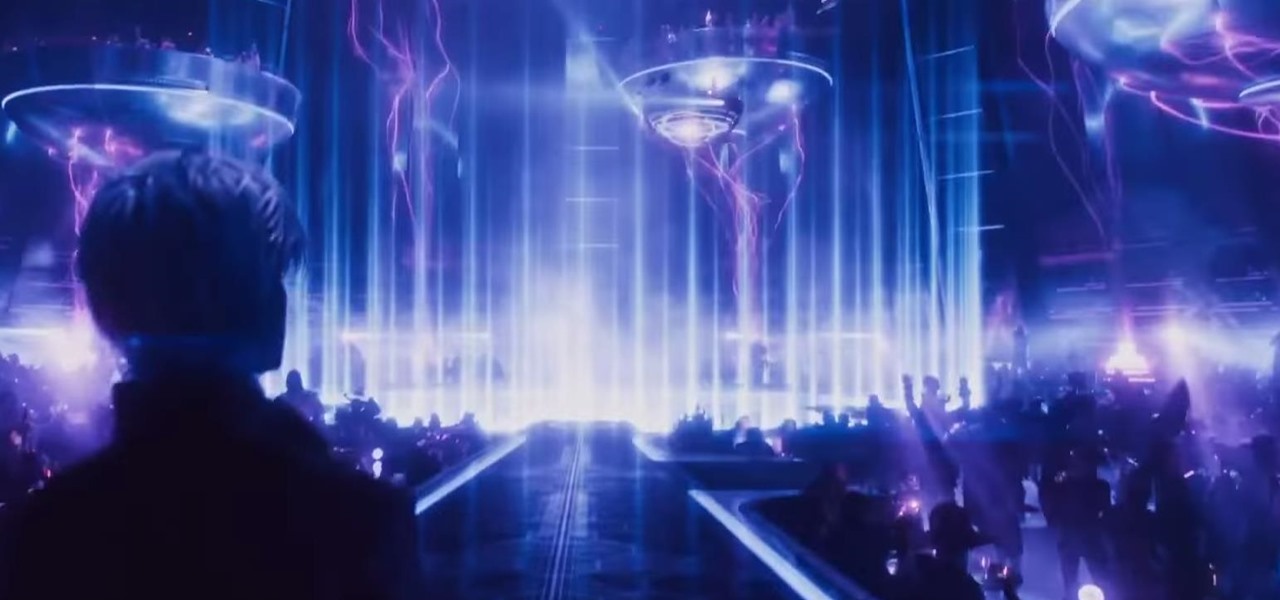
So while it is the weekend of San Diego Comic-Con, and it should not be a complete surprise — without a word of warning hitting my feed — the trailer for the upcoming film, Ready Player One was released today. And wow it looks amazing.

Mobile augmented reality developer Blippar has updated its mobile app for iOS and Android with an augmented reality face profiles feature based on the company's real-time facial recognition engine.
One thing that I got more and more excited about as we got closer and closer to the Microsoft Build 2017 developers conference was finally learning about the new Acer Windows Mixed Reality head-mounted displays (HMD). Brandon Bray, Principal Group Program Manager at Microsoft, had teased us a few weeks earlier at the Vision Summit event in Los Angeles, California, and said there would be a lot more information at Build. Fortunately for us, he was right.

Jostled in the airport, someone is coughing in line. The air looks empty but it is loaded with microbes that make their way into your body. You get sick. You give it to your family, and that's pretty much it. But what if you were so contagious that you spread it to your entire community and beyond?

Virtual reality holds the promise of electronically visiting distant places we'd otherwise struggle to reach, but that teleportation-esque ability isn't possible without the right content. YouVisit created a platform that makes it easy for almost anyone to create immersive 360-degree experiences so we can map our lives and see the world through the eyes of our fellow humans.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Pokémon GO made waves as the first augmented reality game to gain popular adoption. In fact, it was so popular that it only took a few days to uncover some the benefits and serious issues with combining physical and digital worlds.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

Apple just released public beta 2 for iOS 14 today, Thursday, July 9. The good news comes two days after Apple released the second iOS 14 developer beta, and 17 days after the release of the first developer beta. While this is the first public beta for iOS 14, it's called "public beta 2" to keep in line with developer beta numbering.

Apple just released the second developer beta for iOS 14 today, Tuesday, July 7. The update comes 15 days after Apple seeded developers the first iOS 14 beta, which introduced home screen widgets, picture-in-picture, and 4K YouTube support, among more than 200 other features.

The US Department of Treasury isn't generally known for being on the very edge of technology innovations (see the current hubbub around crypto), instead usually waiting until certain tools have been battle-tested in the mainstream or enterprise sector.

While Apple introduced new AR features for iOS 15 and Object Capture for Reality Kit 2 during the WWDC 2021 keynote, updates for ARKit were curiously absent in the official presentation.

As brands and content makers create more augmented reality experiences, the demand for tools to create 3D content grows in kind.

Disney Plus shows WandaVision and Falcon and the Winter Soldier are both streaming hits, but the two series could not be more different in terms of giving fans a taste of the Marvel Cinematic Universe.

At the opening of its virtual Lens Fest, taking place Dec. 8-10 and open to the public, Snap is furthering its facilitation of AR development with new tools for Lens Studio version 3.3 and a planned investment into its AR creator community.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

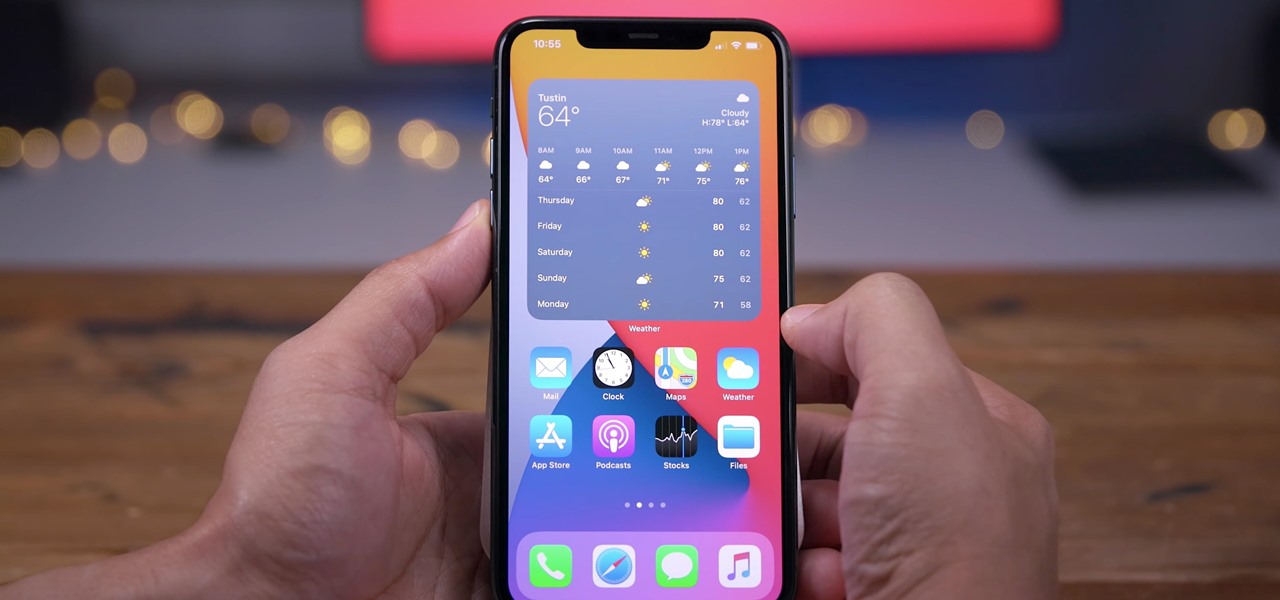
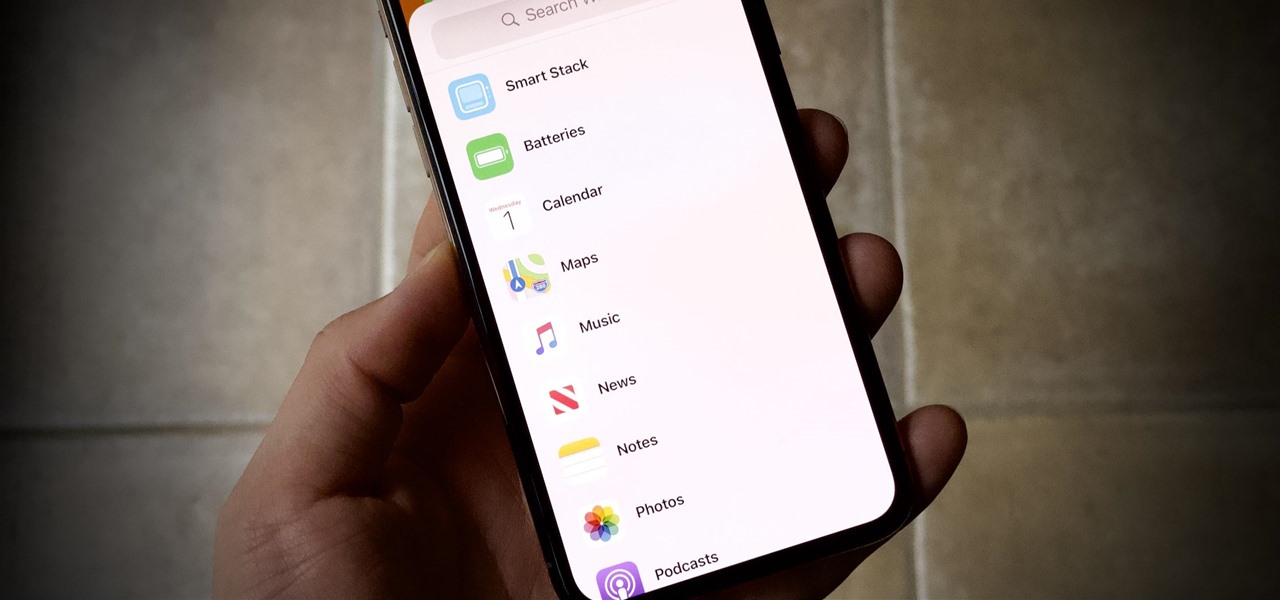
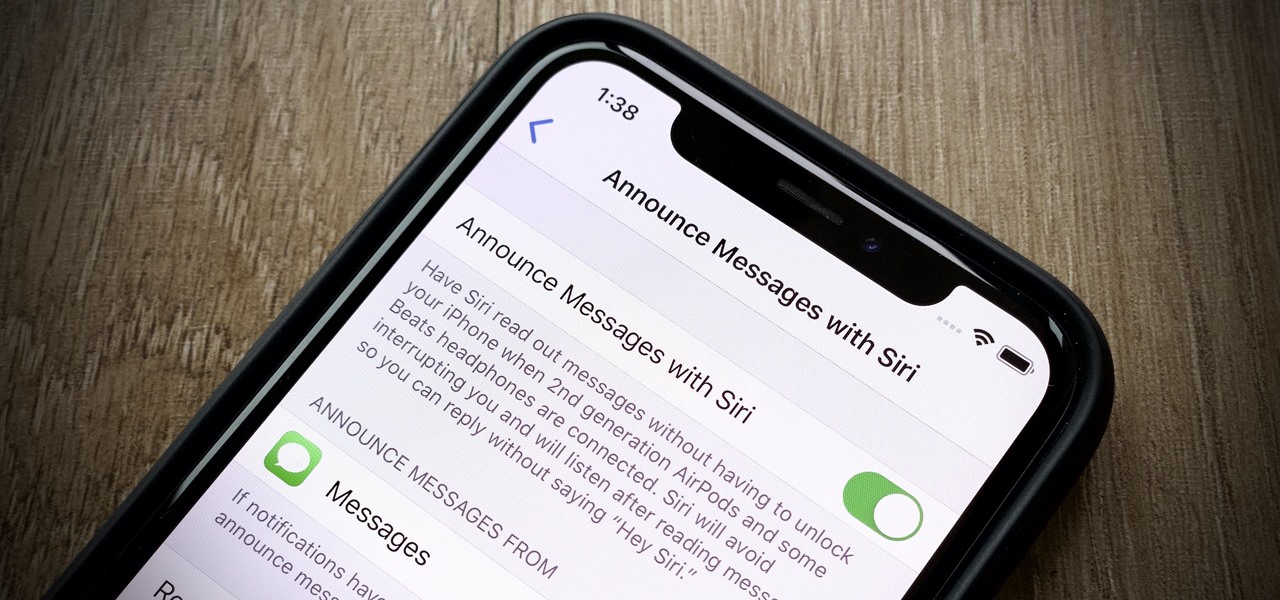
Apple's iOS 13 has been quite the disrupter. The initial update featured over 200 new features and changes, while its successor, iOS 13.1, brought another 22 to the mix. With the company's latest update, iOS 13.2, you'll see an extra 22 amendments on your iPhone, including new emojis, Deep Fusion on iPhone 11, 11 Pro, and 11 Pro Max, and Announce Messages with Siri, just to name a few.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

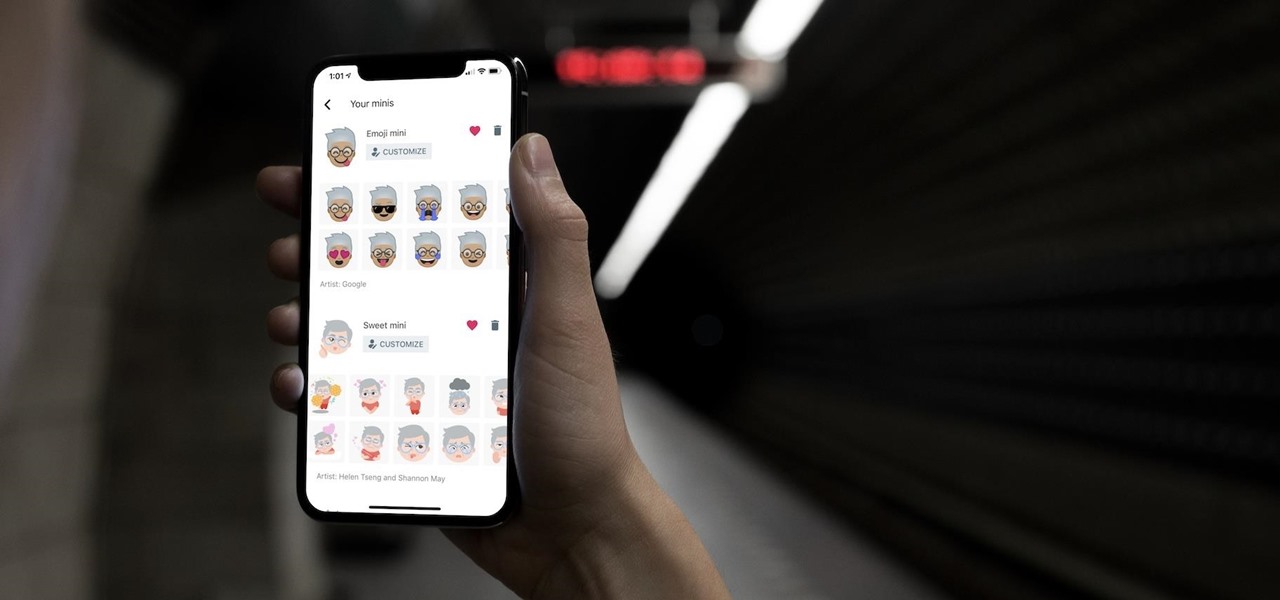
Expressing yourself during chats is much easier these days thanks to the steady rise of emoji. Now, products like emoji Minis for Gboard are taking the craft to an interesting yet familiar new level. With emoji Minis, you can automatically create stickers based off your own face. From there, you can further customize the stickers by adding key features such as glasses, earrings, and facial hair.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Apple released the third beta of iOS 12 for developers on Tuesday, July 3. The update comes exactly two weeks after the release of the second developer beta, which introduced a variety of fixes as well as new issues, and just one week after the release of the public beta. Public beta testers received this iOS 12 update on Thursday, July 5, labeled as public beta 2.

Have you been noticing SpaceX and its launches lately? Ever imagined how it would feel to launch your own rocket into the sky? Well, imagine no longer!

We're all aware that Google collects a notable portion of our data. Thanks to the increasing awareness, Google has added a number of privacy controls to limit data collection. But Google doesn't just collect personal data for no reason — many of your favorite apps will use this info to improve their services and add new features.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

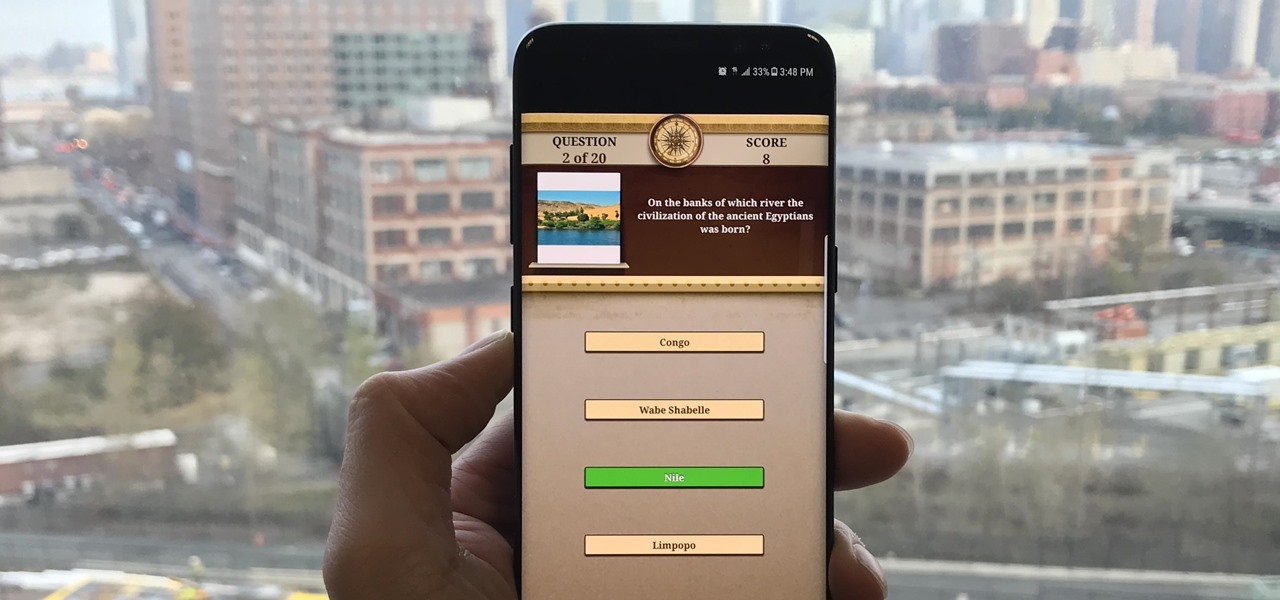
Trivia games are among the most entertaining ways to learn factoids and interesting info you may have never known about before. They're also the perfect genre to enjoy with friends and family, as they're particularly great at breaking the ice to make for a more memorable time together.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.