Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Kitten Planet, a spin-off company that grew up in Samsung's C-Lab incubator, has developed a connected toothbrush that teaches and motivates children to brush their teeth better via augmented reality while tracking their performance.
When I'm with my friends on the weekend, we always end up Snapping shots of one another, adding in whatever stickers and lenses we've accumulated over the last week. But these filters are fleeting, so it's always a challenge to keep up with the best new ones. If you want to get a leg up on the competition, this is your one-stop-shop.
Based on newly surfaced information, transparent smartphones like those teased in Iron Man 2 and those hand-tracking monitors made famous in Minority Report may eventually end up being "designed by Apple in California."
Within the last week, there have been at least three times when someone asked me to play a good playlist. This is always a tough call. What if I play something that nobody likes? I probably will.

In a race to make self-driven cars mainstream, Intel announced today that they've bought Israeli microchip technology company Mobileye for $15.3 billion, setting the stage for Intel to dominate a large portion of the driverless market.

Most augmented/mixed reality hardware still exists in the development stage, whether that's one of the more robust headsets or a high-powered smartphone. Most everything else isn't widely used or monetized. Snapchat, however, snuck in under the radar and created the foundation for the first social network to focus on augmented reality.

With iOS 8.4 and iTunes 12.2, we got our first look at Apple Music, Apple's new streaming subscription service. While it's a little late to the party, there is definitely an incentive for iOS and Mac OS X users to switch over from competitors due to its heavy integration with the Apple ecosystem.

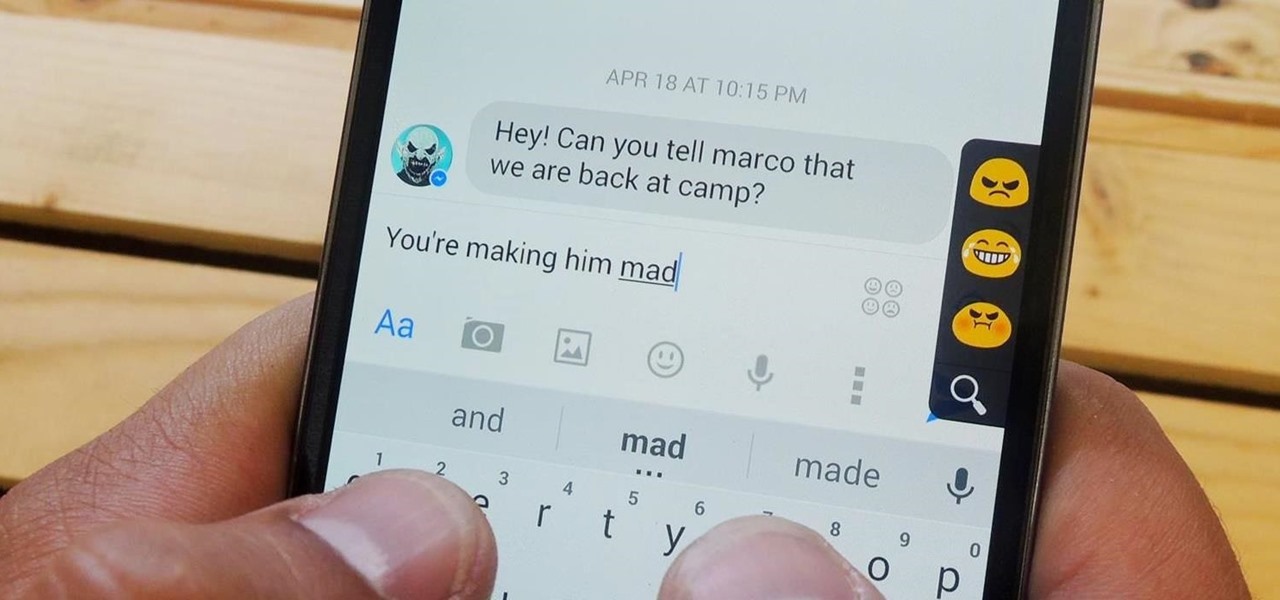
Some third-party keyboards, like SwiftKey for example, include a convenient feature that suggests emojis as your type based on the content of what you're saying. Unfortunately, many keyboards, including most stock ones, don't include this function.

Chromecasts can make for some fun nights. Whether you're setting up a collaborative YouTube watch list, letting everyone add to a giant party playlist, or playing games like Cardcast and Big Web Quiz, Google's streaming media stick is a hit by all accounts.

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

When we surf the web, we tend to do it for selfish reasons. Whether it's on Facebook, Twitter, YouTube, Pinterest, or Wikipedia—we're trying to connect with people, voice our opinions, watch funny videos, or do research for that 12-page paper due tomorrow. Whatever it is, it's usually to benefit ourselves. Well, what if you could not only benefit yourself while surfing the web, but benefit others in need, without even having to alter your habits?

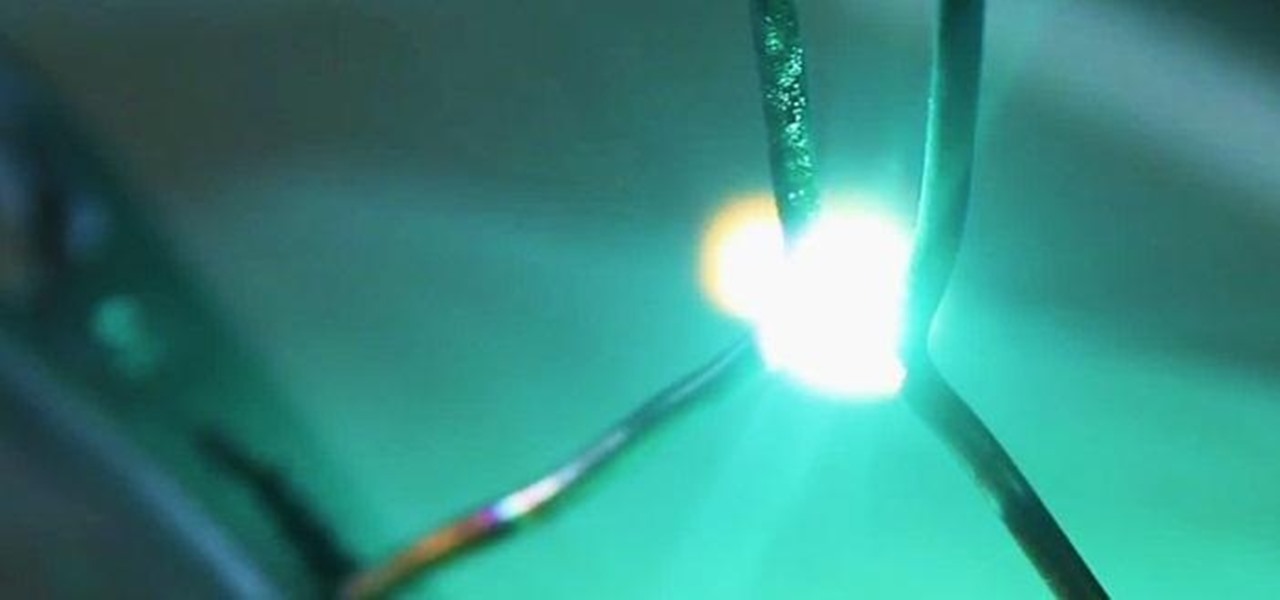
With the microwave oven transformer (M.O.T.) salvaged in a previous project, a simple electrical circuit can be rigged to get high voltage arcs to fly outward and upward along a "V" shaped spark gap.

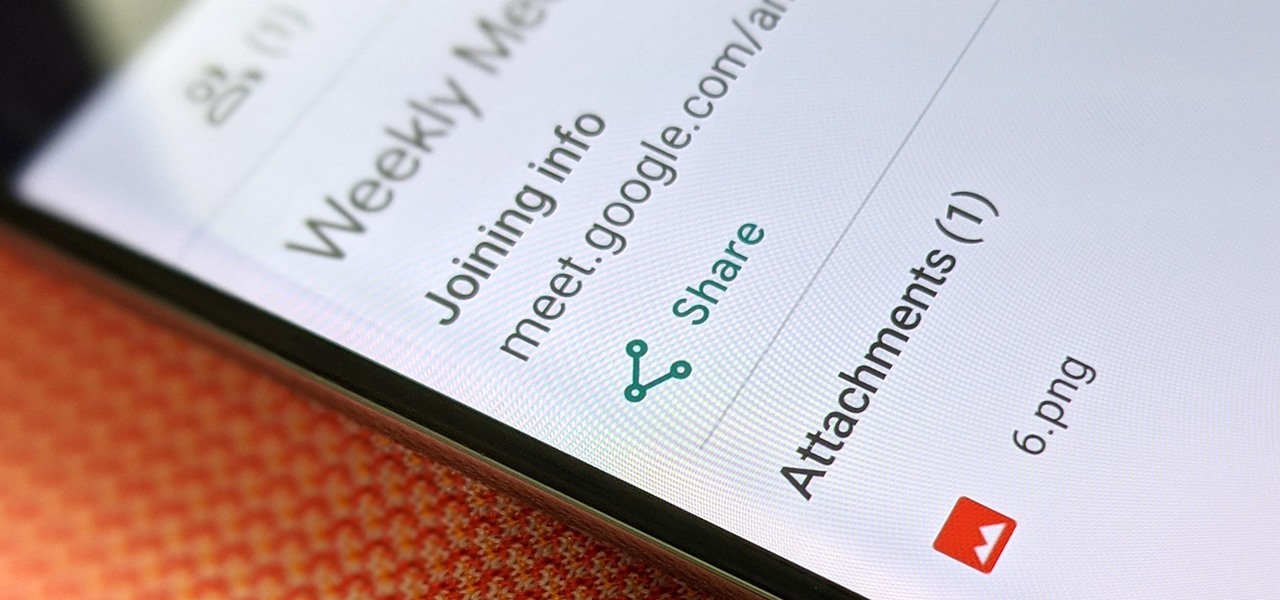
Google Meet might not have virtual backgrounds like Zoom, but it hits all of the other basics, from hosting many multiples of video participants to sharing your screen, that you'd expect from a robust video conferencing platform.

With Google taking on the sidewalks with augmented reality walking navigation for Google Maps, Apple has its sights set on the road.

Smartglasses maker Vuzix has emerged with the first hardware powered by the Snapdragon XR1 chip, roughly nine months after Qualcomm introduced the chipset designed to drive augmented reality wearables at the Augmented World Expo in Santa Clara.

This month, the power of artificial intelligence will be coming to more augmented reality developers as a leader in the game and 3D software development space and a major force behind the current school of cloud-based AI have officially announced a new partnership.

Transparent display maker Lumus has reached a deal to license its augmented reality optical engine models to Quanta Computers for mass production of displays for consumer smartglasses.

NextReality will be giving readers a rundown of the augmented and mixed reality news briefs from the preceding week that we didn't cover already. This way, you'll never miss anything of importance in the NextReality landscape, and will always know what's going on with new augmented and mixed reality tech and applications. The first one starts right now, and you can enjoy future ones every Tuesday going forward, so stay tuned.

Pokémon GO, the biggest augmented reality sensation ever, broke app store records this opening weekend. But it also did something even more important: it gamified physical activity.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

Video: . Being one of the most popular DIY/maker projects around, Musical Floppy Drives are nothing new. However, myFloppyDriveOrchestra includes a few unique features, which separate it from the crowd.

We've all been there. Your phone's either dead or barely hanging on with a few minutes of life left, and you only have a small window of time to charge it before you need to head out. Sure, you can charge it for the few minutes you have, but what's the point if your device is going to die again in several minutes?

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

Your iPhone has seen a lot of new features in a very short amount of time. For starters, iOS 13 introduced over 200 of them, including, among many others, system-wide Dark Mode. Before you even had a chance to breathe, however, iOS 13.1 came along and dumped an additional 22 features in your lap. For us beta testers, now its time to explore new features all over again with the first public beta for iOS 13.2.

Beta testing Apple's mobile OS has never been more interesting. After eight seeds of iOS 13.0, Apple unexpectedly released the first beta for iOS 13.1, a whopping 23 days before iOS 13.0 made its public debut. Since 13.1, however, we haven't had any betas to sink our teeth into. That is, until now, as Apple just released the first developer beta for iOS 13.2 today, Wednesday, Oct. 2.

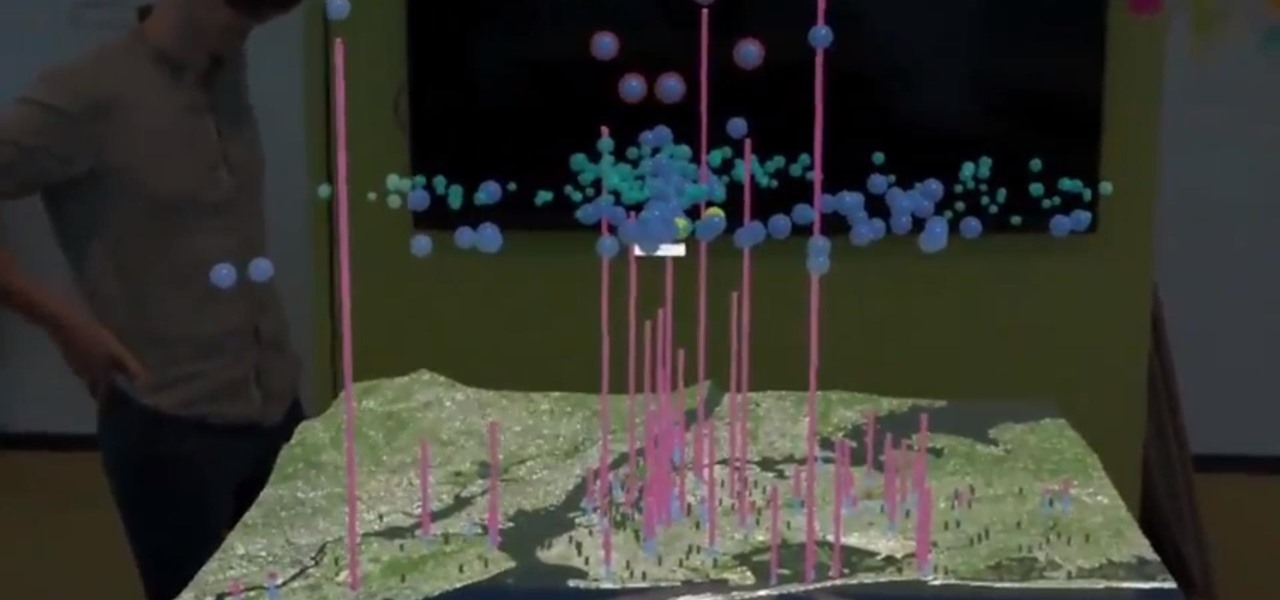
While ARKit and ARCore are poised to bring AR experiences to millions of mobile devices, one company is poised to anchor those experiences anywhere in the world with just a set of geographic coordinates.

Mixed reality display manufacturer Realfiction has developed a 64-inch display capable of delivering 3D holograms without a headset.

Welcome back! Sorry for the dry spell, but I've been rather busy setting up some side projects! If you remember back to a few training sessions ago, we covered basic file I/O. This is a very important step in making our scripts applicable in a real life scenario, and today we're going to further these concepts.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

There's a whole world of wallpapers out there. Apple always includes a selection of stock wallpapers, some unique to every iPhone model you have. Of course, sometimes, stock wallpapers don't cut it. Sometimes, you want to add your own style to your home screen and lock screen. In these cases, using an app to find the best wallpapers out there can be just what you need.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

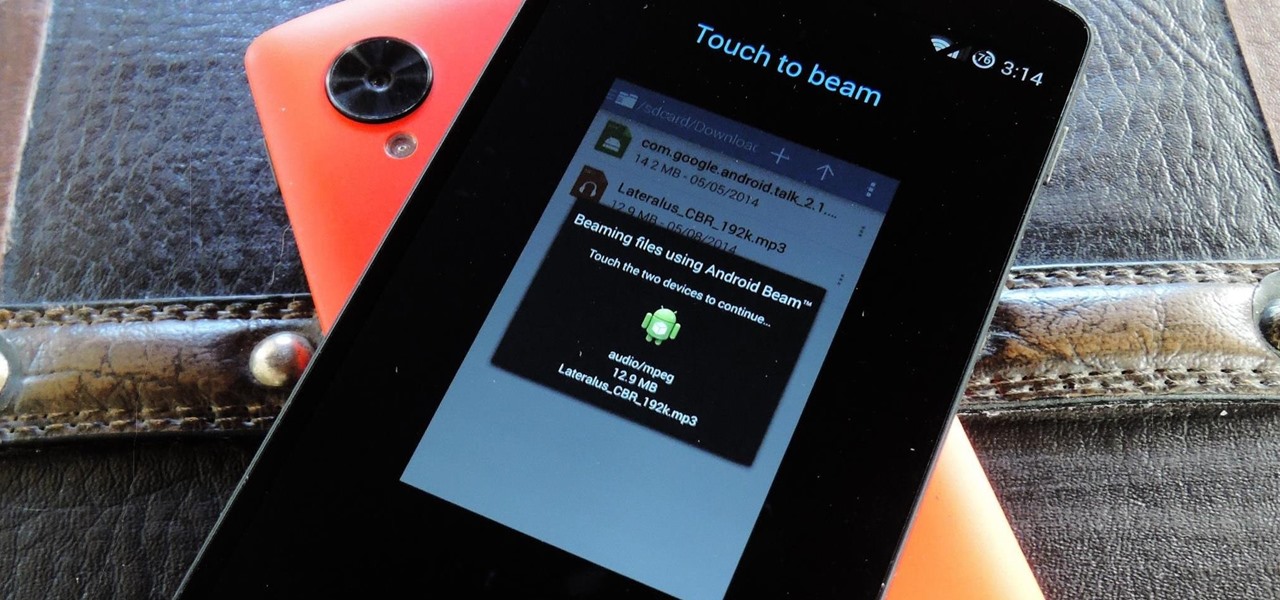
Your Nexus 5 comes with a pretty cool feature baked in called Android Beam. Using NFC, or Near Field Communication, this functionality allows you to send information to another compatible device by simply touching the two together. Most flagship devices have NFC built into them these days, so there is a broad range of devices that your Nexus 5 is capable of sharing information with wirelessly.

With so many competing outlets to reach people, accessing inboxes remains one of the most effective forms of communication. Yet newsletter creators run into a constant problem: bounced emails.

It's not hard to let the new SARS-CoV-2 strain of coronavirus put pressure on our minds. Fear of catching COVID-19 is never far from the topic of conversation. But it doesn't have to be that way. If you're struggling with anxiety, stress, depression, or any negative emotions due to the virus's effect on our lives right now, you might find some solace in meditation.

You may soon add feigning eye contact to the list of ways that augmented reality is improving our lives.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.