With this video demonstration, you'll learn how to iron a jacket using the Batisella universal ironing board, the technical specifications of which are as follows: board type 50x130cm with automatic steam generator [6,6kW power and 8lt boiler capacity] for 1 iron, board suction and blowing unit 0,37kW, board steaming, board heating power 0,8kW, ironing board height 92cm, heated 0,15kW and vacuum sleeve ironing buck. Equipped with turning iron support, double pedals [enabling work on both side...

Tracing any IP hostname or web address free online is demonstrated in this video. To trace any IP, website and hostname free online firstly go to the websiteGeoLocationWhen the webpage appears you will get a find option. Enter your IP address, website or hostname here. Then click the find option. Your IP hostname or web address is traced. So easy. Quick and simple to use. Your IP address, city, country, continent and time zone will be displayed in a rectangular box in your location in the wor...

The updated Messages app for iOS, iPadOS, and macOS has creative new ways for you to format and send messages, from standard text formatting to fun text effects. But Apple also includes another way to make your messages appear precisely as you want: more control over how links appear for you and your recipients.
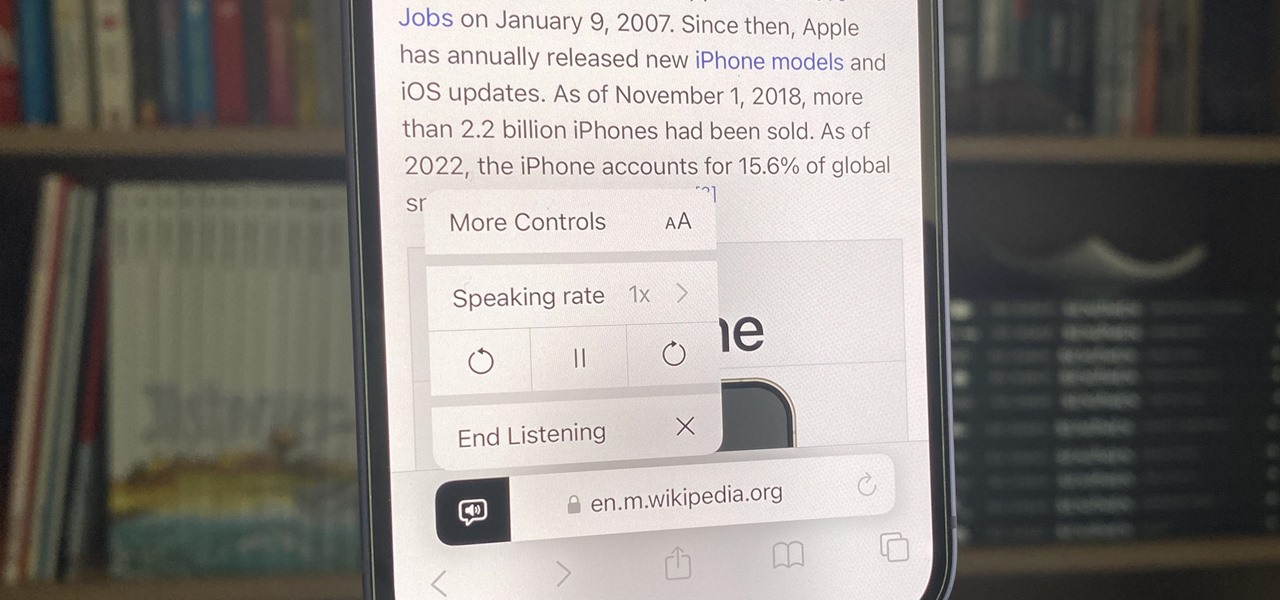
Speech-to-text technology can be seen on your iPhone in various places, from the Dictation tool to Apple's new behind-the-scenes, auto-created transcripts for podcast episodes. Your iPhone also has some pretty impressive text-to-speech capabilities. With them, your iPhone can read webpages, documents, or whatever text is on the screen out loud to you — only some of these tools aren't easy to find.
Apple has a new way to tidy up your favorite bookmarks in Safari, making them easier to access than ever before. This new feature saves space, allowing you to quickly see more of your favorites at the same time.

It was a long time coming, but Android finally has built-in scrolling screenshots, and they come courtesy of Android 12.

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

The iOS App Store is a big place, offering over two million applications in total. However, there are actually some apps you can and should install on your iPhone that the iOS App Store doesn't include. And no, these apps do not require any difficult jailbreaking or complicated sideloading techniques — they are really simple to install.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

Running diagnostics on your Android phone can be a very tedious process. More often than not, you need to key in dialer codes to see if your device's hardware is functioning properly, though you can also download apps — but these are often hard to understand for a layperson. When a smaller component like a proximity sensor fails, you're often left with no other choice but to take it to a professional.

At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.

Safari's private browsing mode on your iPhone won't sync to other Apple devices or remember your search history, AutoFill data, or visited webpages. Still, it doesn't stop anyone who accesses your iPhone from opening your private tabs. If you don't want anyone snooping through your private tabs, use Chrome instead so you can lock the tabs behind biometric authentication.

Did you know that you could learn all the fundamentals of web development for less than $35? Set yourself up for your new coding career in 2021 with The Ultimate 2021 Web Developer & Designer Super Bundle, which is on sale for just $34.99 right now — a huge 98% off the regular price of $1,886.

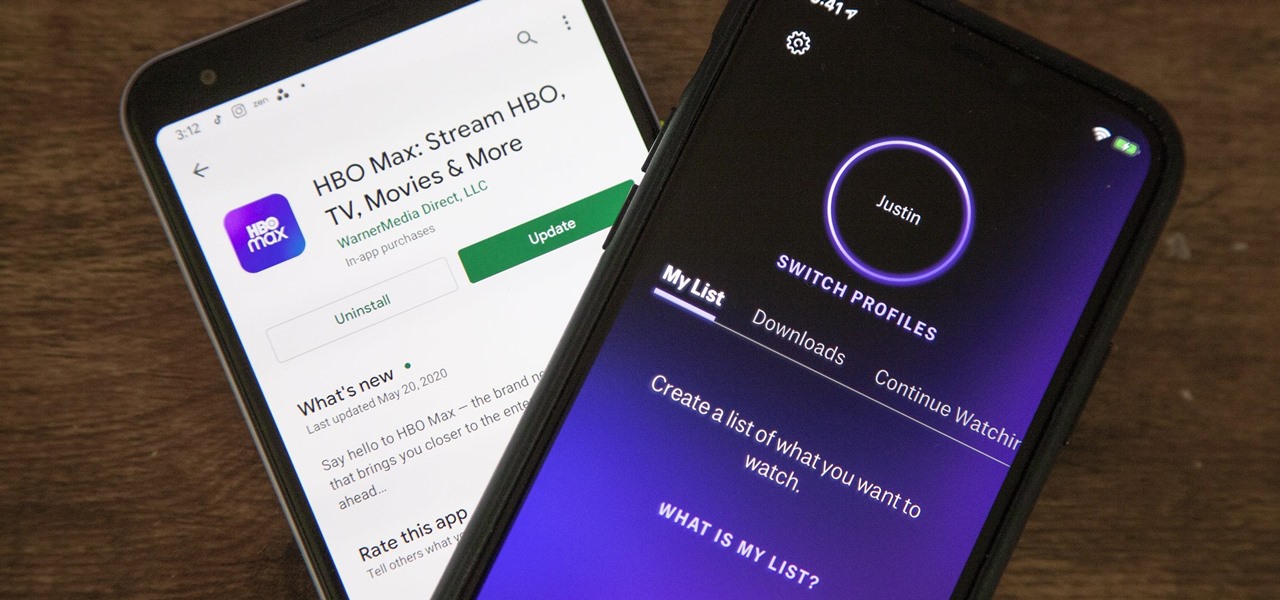
As of May 27, HBO Max is taking over your HBO Now or HBO Go account. If you have your devices set up to auto-install new app updates, you should pause it right now if your HBO app hasn't been updated yet. There's one thing you'll want to do before you make the leap. However, you're not out of luck if you already upgraded.

If you thought the news coming from China about the coronavirus might not affect your daily life in Europe and in the Americas, think again.

In iOS 13, Safari has become even more powerful, especially when it comes to privacy. The browser will warn you when you create a weak password for a new account. Your history and synced tabs in iCloud are end-to-end encrypted now. And there are per-site settings that let you choose which domains can and can't have permission to use particular device hardware or sensors.

Like clockwork, Apple has unveiled the latest additions to its ARKit tookit at the annual Worldwide Developers Conference, where ARKit first said hello to the world in 2017, as well as some new tools that take a direct shot at Unity, Unreal Engine, and others.

Location-based gaming company Niantic knows its business model is inextricably tied to the outdoors, so it is in its best interest to help preserve that environment to give players a place to play.

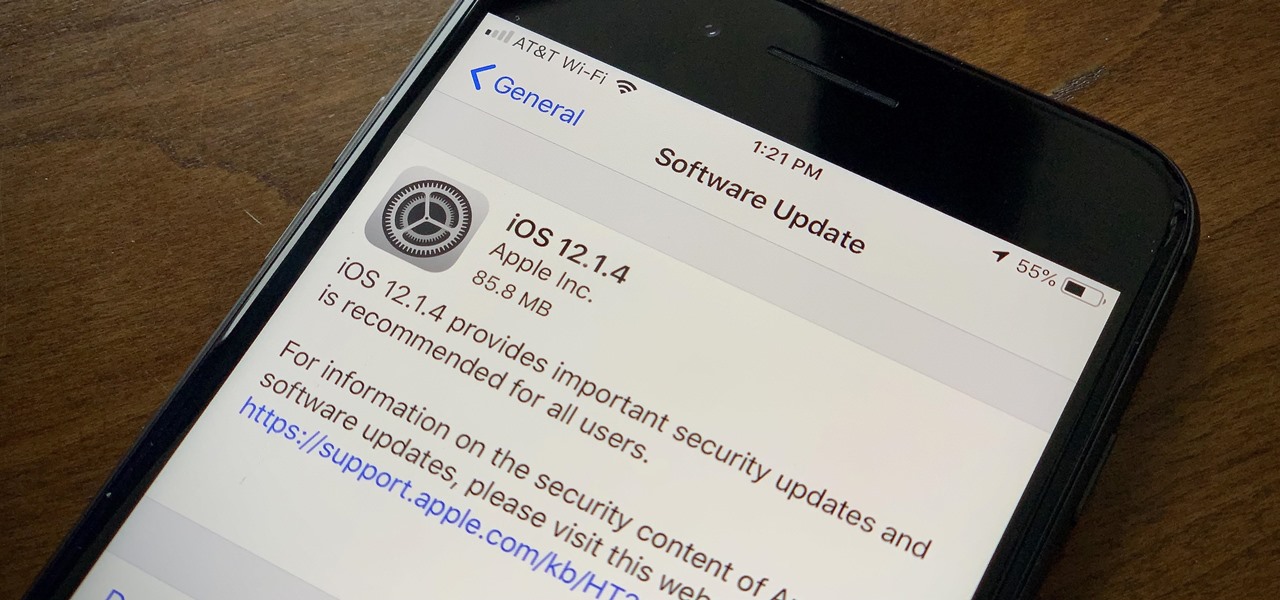
Apple found itself in serious trouble last week when a teenager discovered a critical FaceTime bug that threatened the security of nearly every iPhone user. The bug enabled a user using Group FaceTime to access either the microphone or the camera of a recipient before they answered the call. According to Apple, the issues have been fixed in an iOS 12.1.4 update released Thursday, Feb. 7.

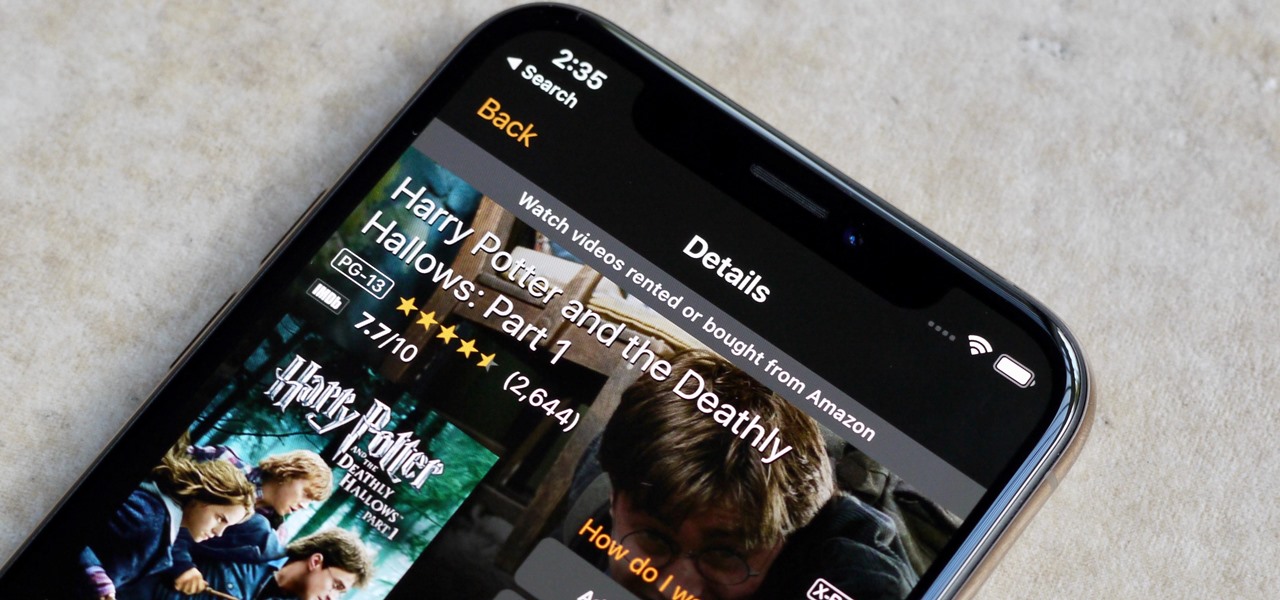
Amazon Prime Video is undoubtedly one of the best services out there for streaming and downloading movies and TV shows to your iPhone. If you try to buy or rent a movie or show in any of Amazon's iOS apps, however, you'll notice that there's no apparent way to do so. No buttons, no links, nada. What gives, and how can you buy and rent content from Amazon on your iOS device?

Apple's dedication to iPhone security is one of the company's biggest selling points. It's no surprise then that iOS 12 offers users a simple yet powerful way to make, save, and auto-fill strong passwords to your iCloud Keychain when creating accounts in both Safari and in apps. The best part? You hardly need to do a thing.

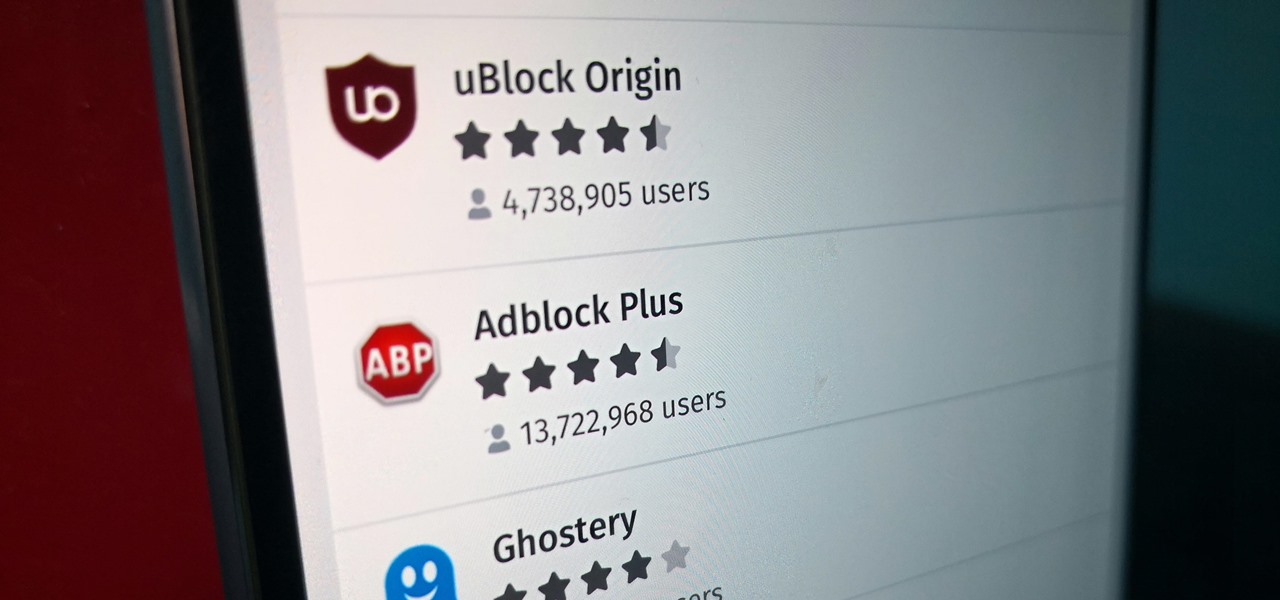
Ads can detract from your mobile browsing experience, especially if they appear out of nowhere as popups or large annoying banners that take up almost all of your screen. If those weren't bad enough, some ads appear as extremely loud videos that can even disrupt others around you. In fact, ads have gotten so obnoxious that even Google itself was forced to act.

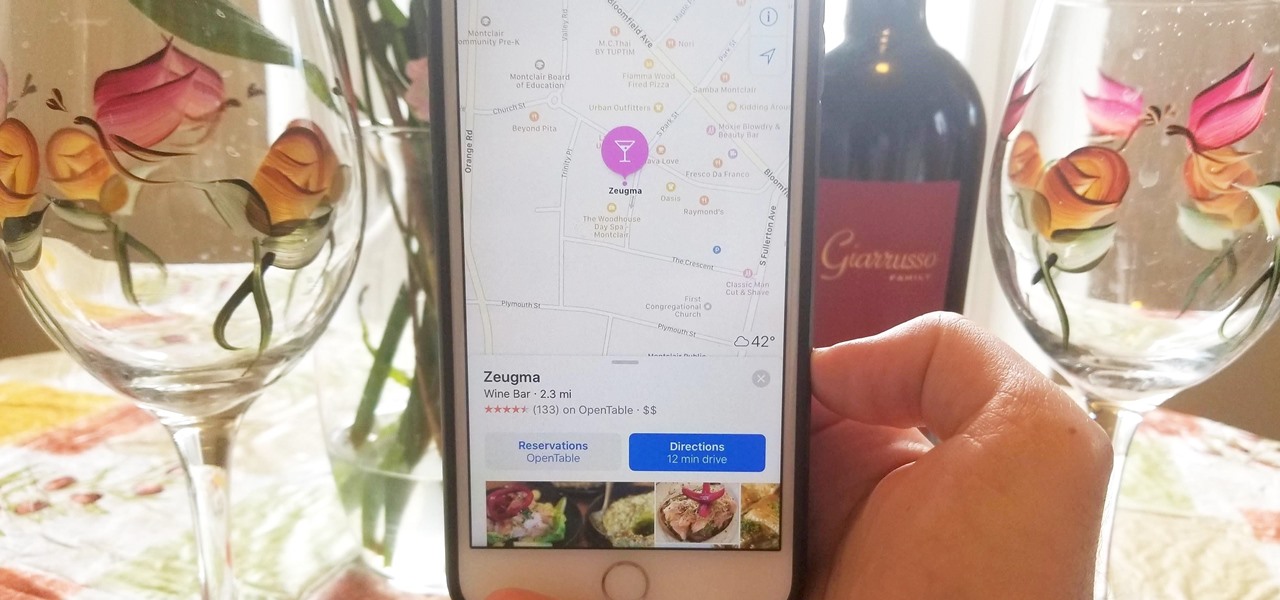
Apple has taken great strides to ensure that iPhone users are having an Apple Maps experience on par or even better than Google Maps can provide. One of the factors powering this is extensions, which adds functionality to certain apps by giving them permission to interact. Among all the possibilities, one extension will let you reserve dinner tables right from inside Apple Maps.

While TouchWiz as an Android skin isn't a favorite among many, Samsung Internet is a fantastic web browser that S9 owners should be happy to have preinstalled out of the box. But you don't need to buy Samsung's latest flagship to try their browser — Samsung Internet is available to all compatible Android phones.

Stop me if you've heard this one before: scan an image with your iPhone's camera and augmented reality content shows up.

Features like themes and a tab queue make Firefox an extremely versatile mobile browser. Mozilla is constantly adding bonus functionality like this to Firefox, but a long-time staple is perhaps the most powerful feature: Extensions. This system gives you the ability to add features without having to upgrade the entire app.

Between Renault Truck's testing of the HoloLens in factories and BMW promoting its newest model through Snapchat, the auto industry is hot for augmented reality to improve internal operations and engage consumers.

Scanning important paperwork on smartphones is a tedious process, often relying on either external scanners or third-party apps that had to be either purchased or were loaded with annoying ads just to get the job done. Thankfully, iOS 11 now lets you easily scan documents using your iPhone, and finally does away with the need for third-party apps or machines.

We all know the internet isn't exactly a safe place. While plenty of its users are innocent and kind, you won't last long unless you treat every new screen name like a criminal (we're all this cynical while surfing the web, right?). Well, that cynicism is proven correct today, a post on Medium uncovered a group of scammers on the iOS App Store that are costing victims up to $400 a month.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

Intel, the company which is mostly known for creating computer processors, once again showed off their Project Alloy "merged reality" experience, this time during their CES 2017 press conference. Intel's Chief Executive Officer, Brian Krzanich, stated that they will be "productizing" this tech with their partners in the fourth quarter of 2017.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

When you're browsing the internet on a computer, you just need to hit Ctrl F (or Command F) and type something out to find all instances of that word in the webpage. It's a handy feature baked into most browsers (nearly all mobile browsers have a "find" feature, too), but unfortunately, it doesn't work with real-world documents, signs, and menus—or at least it hasn't, up until now.

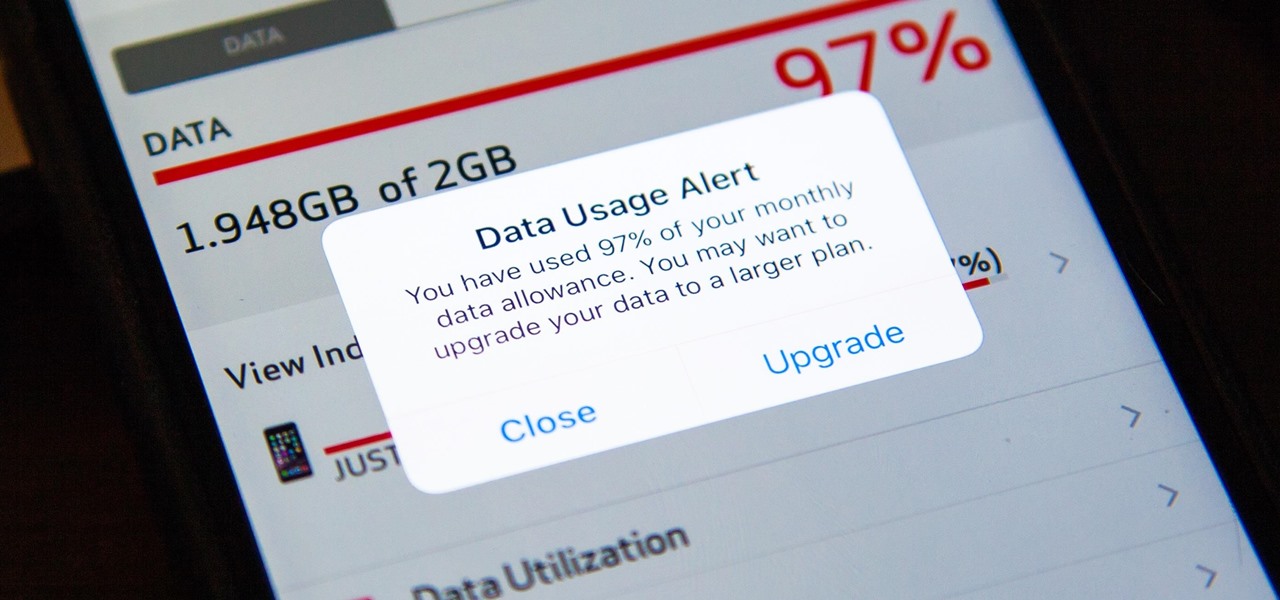
I was one of the first to install the iOS 10 developer beta, and I remember thinking that everything was working insanely well compared to the first iOS 9 developer beta—but then I got a warning that I used 90% of my data 11 days into my following cycle—one day before I updated to beta 2.

I often read ebooks on my iPhone while I walk, but being glued to my screen is a good way to get run over or cursed at. To save my physical and social hide, I use this trick to get my iPhone to read ebooks and articles out loud, turning my whole text library into de facto audiobooks.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.