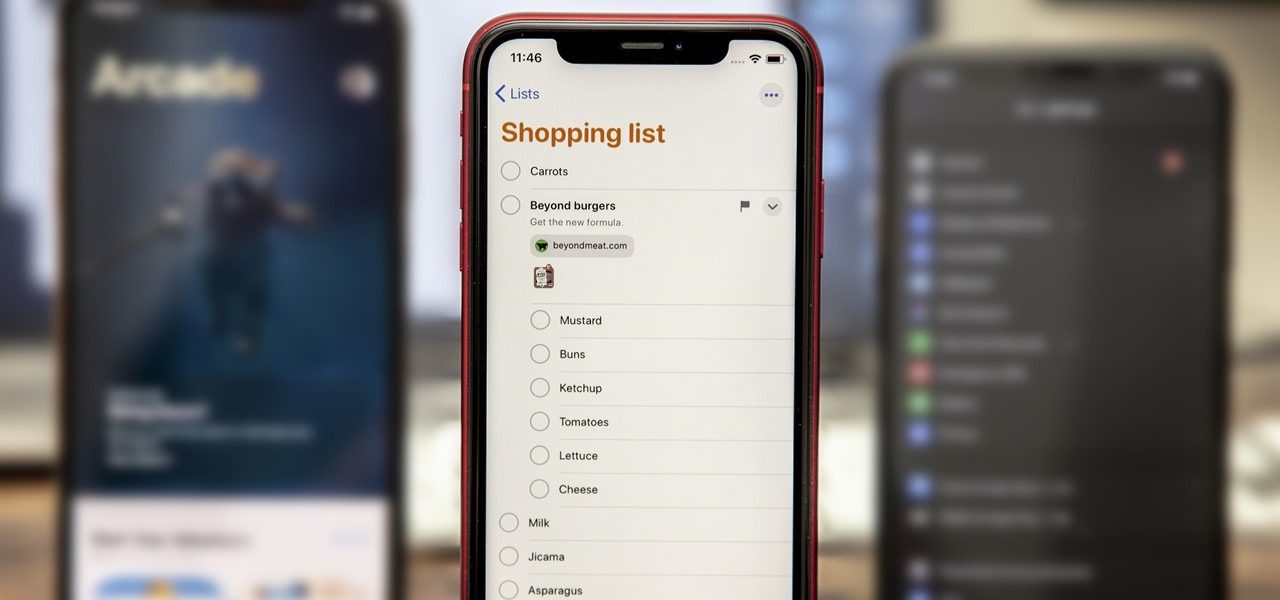
If you're sick of seeing some of your contacts' faces in the sharing menu every time you share photos, apps, webpages, or other content on your iPhone, or if you want to keep nearby eyes from sneaking a peek at the people you frequently share things with, you can make some or all of them disappear.
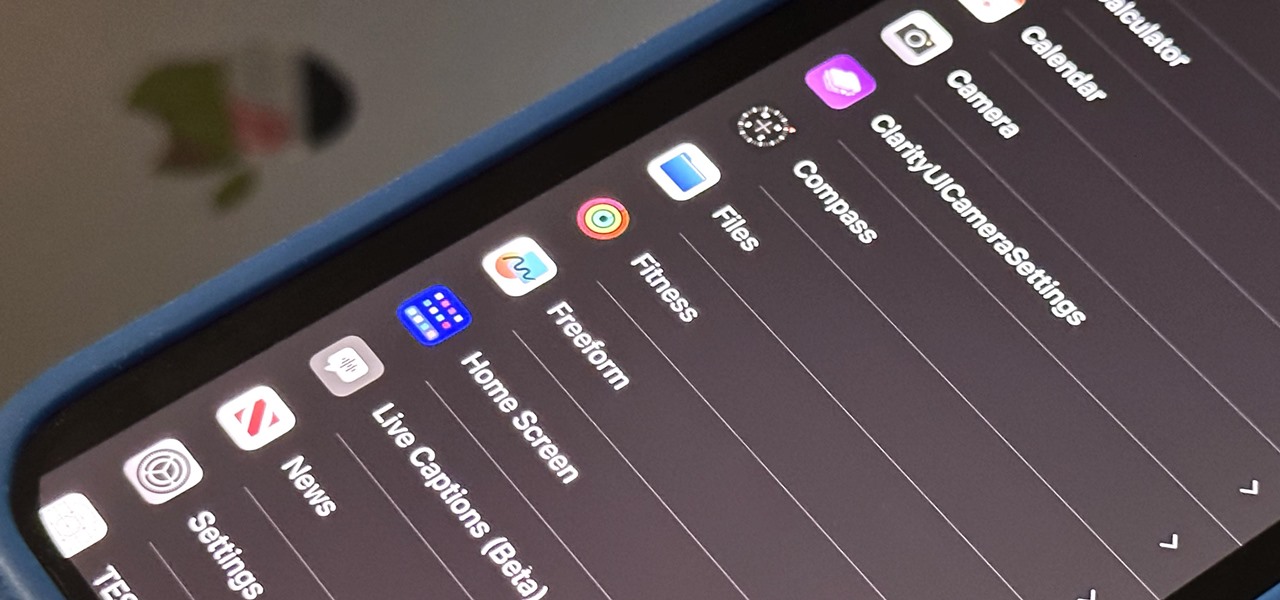
It's not an easy task when it comes to customizing apps on your iPhone. Sure, you can build automations in Shortcuts to add color-related filters, enable Live Captions, or play a background sound specific to each app, but it can be too much work. If you don't mind that, go ahead, but there are also some easier per-app settings hiding on your iPhone that are much easier to assign.

It's easy to copy text from webpages, messages, documents, and other views on your Android device — except when it isn't. Many apps block or prohibit text selection, forcing you to take screenshots or write out the whole excerpt manually. But you don't have to resort to those methods since there's a simple workaround to selecting and copying text from uncooperative apps.

Customization has always been the main draw of Android for me, but Apple has an impressive feature on iOS 16 that lets iPhone users create customized emoji wallpapers for their home and lock screens. While Android doesn't have something like that built-in by default, it's easy enough to make emoji wallpapers for your Android phone.
If you've ever wanted or needed to use an app in a different language than your phone's primary language, your Android phone now makes it a simple process.

If you use the Apple TV Remote found in your iPhone's Control Center, there's a hidden surprise you'll like on iOS 16 and later — one that lets you use the remote without ever having to open Control Center.

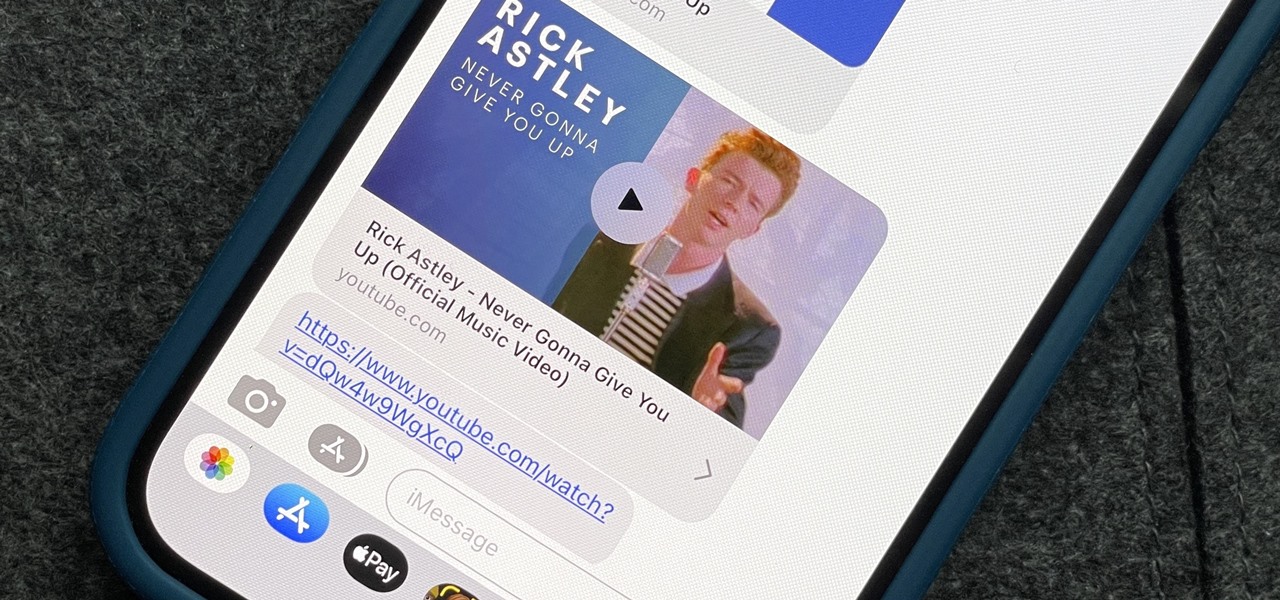
Apple automatically converts most URLs in the Messages app into rich link previews, but they aren't always pretty, and sometimes you just want to see the full URL instead. While there is no setting on iOS, iPadOS, or macOS that disables rich link previews in the Messages app, there is an easy way to show the URL complete with the scheme, domain name, and path.

By default, your iPhone's share sheet will have a row of contacts iOS thinks you'll want to share the content with. Those suggestions are handy if you frequently share things with the same people, but they also clutter the share sheet, invade contacts' privacy in screenshots, and tell nosy people in eyeshot who you share with the most. Thankfully, you can remove or hide them whenever needed.

Some of the new features in iOS 15 take some getting used to, and the biggest one of those is Safari's relocated search bar, aka address bar. There are more than a few reasons why it's a jarring change, but the good news is that you can return Safari's search bar to its pre-iOS 15 position at the top of the screen.

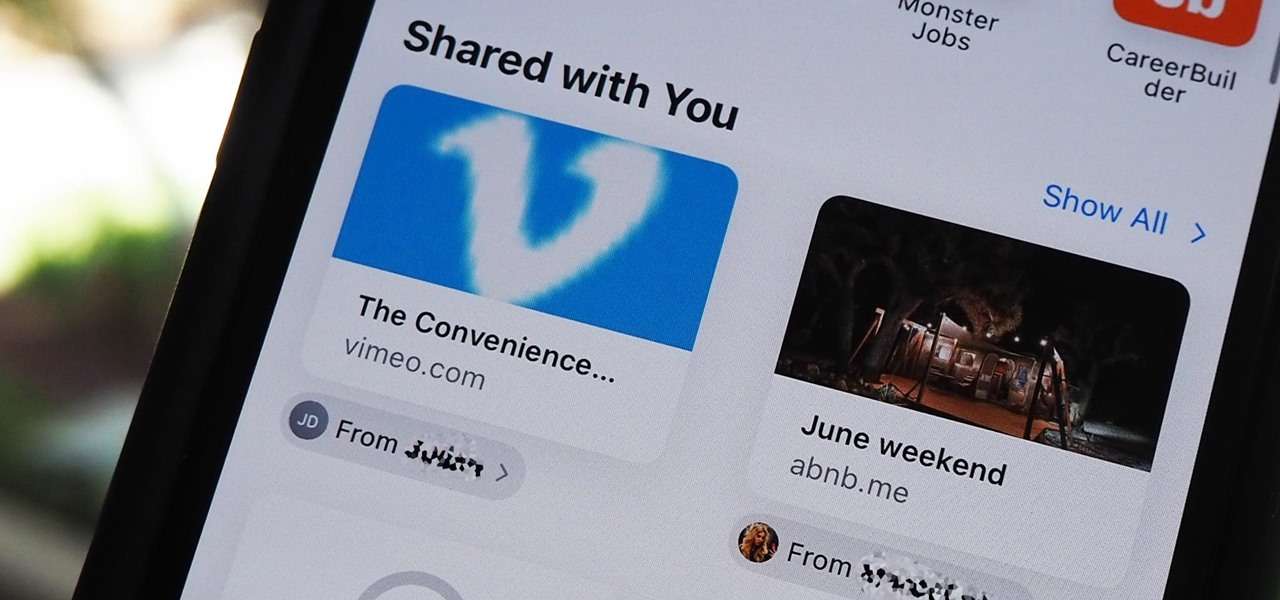
After updating to iOS 15 or iPadOS 15, you'll notice a new "Shared with You" section in certain Apple apps that contains recent shares from conversations in Messages. If you don't like seeing shared content from specific contacts or groups, there's a way to block them from Shared with You on your iPhone or iPad.

I am constantly hitting Apple's limit of 500 open tabs in Safari on my iPhone, so it's safe to say that I have way too many tabs to sort through. With that many tabs open in the browser, it can be impossible to track down the one needed at any given moment. If that sounds like you, stop browsing tab after tab to locate the right one because there are hidden tricks to searching those tabs that make it easy.

Have you ever wondered where you'd come out if you drilled to the other side of the world? Now, if you have an Android device and Chrome web browser, you can find out.

When an app needs to be absolutely sure it won't be cleared from RAM by Android's memory management system, it posts a persistent, ongoing notification. Another time you'll encounter non-removable alerts is when your phone or carrier really wants you to do something, like apply an update.

The COVID-19 pandemic has increased the demand for virtual and remote collaboration, and Microsoft has a solution that may serve as the catalyst for more such apps for augmented and virtual reality in the near future.

URL tracking codes: you'll see them on almost every link you copy online to share with friends and followers. It could be tens or hundreds of extra characters appended to the end of a URL, which websites and marketers use to tell how you got to the link in the first place. These excess tracking tokens not only make the links you share look sloppy and spammy — they could even invade your privacy.

Instagram isn't as link-friendly as other social media platforms like Twitter and Facebook. Still, when you do find and open a link, whether it's for a petition or a product, you may want to find it again later. That's why Instagram keeps track of every link you've ever opened. That way, if you ever need to revisit a webpage, you don't have to find the original post or account from last time.

Millions of people use YouTube every day, whether it's for trailers, new music, or gameplay walkthroughs. But according to Pew Research Center, over half of U.S. adults use YouTube to figure out how to do things. If you fall into that crowd, adult or not, sometimes it's good to have written instructions to follow along with the video or in lieu of it completely.

You're out and about, and nothing on your iPhone will load. A glance at the settings shows a saved Wi-Fi network with full bars that your iPhone had connected to automatically, but you're not getting any internet. If you've experienced this, you're not alone, and there's something you can do about it. You'll even increase privacy and security on your iPhone in the process.

After an Instagram creator created a viral sensation last holiday season with the Which Disney camera effect, Disney followed it up with a Sponsored Lens playing a similar roulette with programming from Hulu.

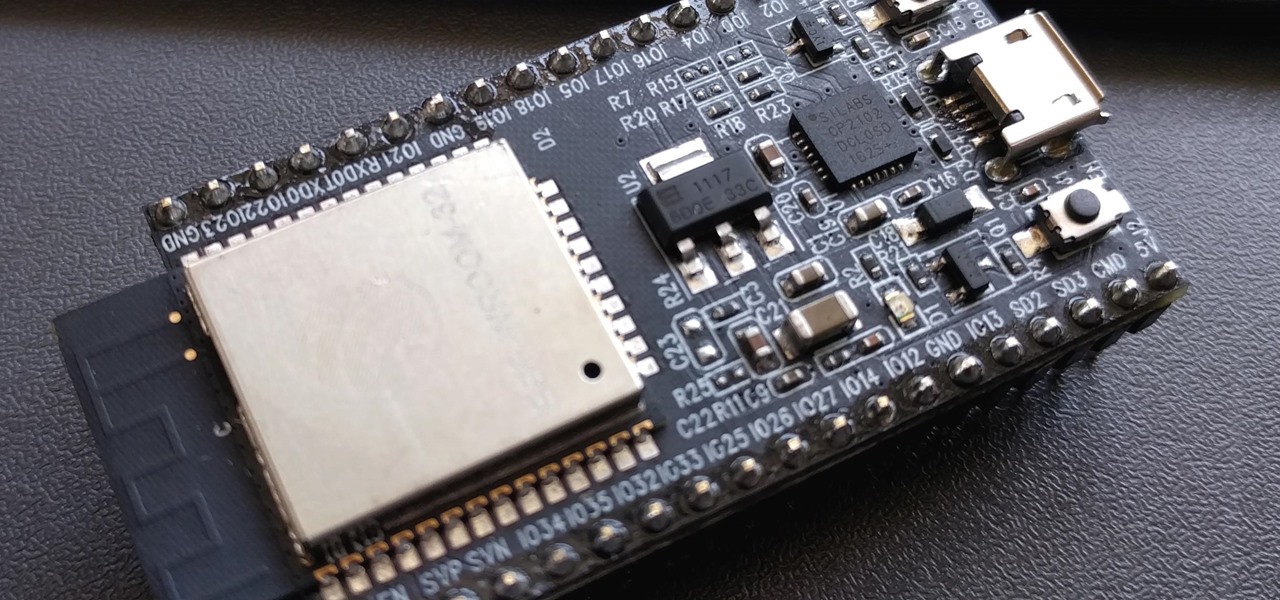
PirateBox is a great way to communicate with others nearby when cellular and Wi-Fi networks aren't available. With it, you can anonymously share any kind of media or document and even talk to one another by voice — without being online. However, it needs a Raspberry Pi, which is more expensive than ESP32 boards, and if you only need a text-based chat, there's a much simpler option.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

To be honest, the Mail app for iPhone had always been somewhat forgettable. It lacked many of the features that made third-party clients like Spark and Edison better, but with iOS 13, the gap between Mail and its competitors is much smaller. Apple updated the layout and added many new features to its native emailing app, and that may be just enough to get you to switch back.

While the Reminders app has been largely ignored by Apple for years, iOS 13 finally makes it a force to be reckoned with. The app has been completely redesigned with easier navigation and more useful features that can compete with other task managers. After giving the new Reminders a shot, you may want to ditch that third-party to-do app you've been using.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

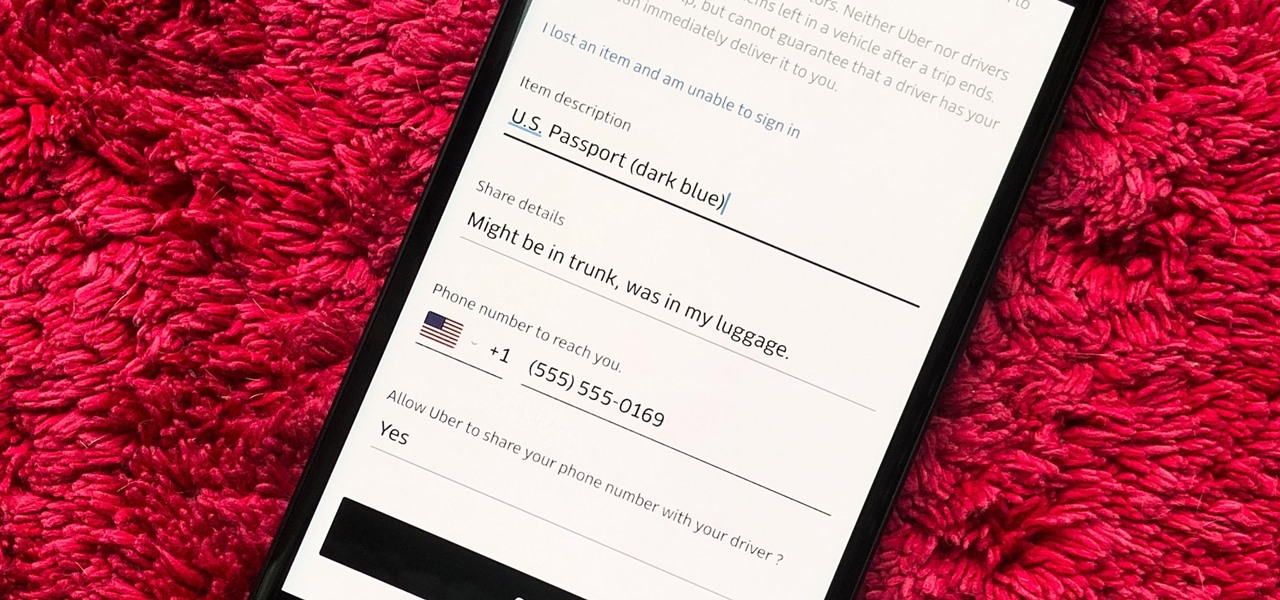
You would think that recovering your smartphone or another important item that you leave behind in an Uber ride would be a simple process, but it can actually be a pain in the ass. You have to find out how to report it to the driver, hope the driver is honest, pay a fee, and contact Uber directly if none of that works. But we're here to help make this process as easy as possible for you.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a thing called "Facebook." But we love grandma, and thanks to this guide, we can definitely make this happen for her.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

Apple's iOS 11 is finally here, and while they showed off several of the new features it brings to your iPhone, iPad, and iPod touch back at WWDC 2017, they've only just touched the surface of what iOS 11 has to offer. There are a lot of cool new (and sometimes secret) features to explore, so we've collected them all here for you.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

I'm an Android user. Over the course of the past seven years, I've owned ten different smartphones—all of them powered by Android. This isn't due to some blind trust in Google or some unfounded hate for Apple, either, because I've always made sure to get my hands on each iPhone iteration along the way to see what it had to offer.

Greetings my fellow hackers.