
GHOST PHISHER : Security Auditing Tool
Hey Everyone! Welcome to my post. We have seen a numerous GUI Tool in kali linux. Armitage, wireshark, Burpsuite etc,. Lets see an another GUI tool.


Hey Everyone! Welcome to my post. We have seen a numerous GUI Tool in kali linux. Armitage, wireshark, Burpsuite etc,. Lets see an another GUI tool.
Getting used to your new Firefox 4 web browser? If so, you might have seen some improvements in the Location Bar. The updated features make browsing the web a cinch, so it's no wonder why more and more Internet junkies are calling it the Awesome Bar. It's faster and easier to use, and there's even some optional tweaks that you can employ to make your Internet experience smooth and effortless.
JavaScript is the language of the internet. It is what allows us to create dynamic, interesting webpages that are fast, web-based applications and so much more. The primary use of JavaScript is to write functions that are embedded in or included from HTML pages and that interact with the Document Object Model (DOM) of the page. This is the magic that allows all of what we see to happen, and for our browser to be manipulated.

Facebook is powerful and affluential, even when it comes down to its applications. But some applications are just downright annoying! With the new layout and other changes affecting Facebook recently, you can take ease in the fact that blocking and unblocking Facebook applications is still as easy as before.

This article is going to cover the basics of link building. Why do we want to build links? First of all, what is a link? A link is a hyperlink, actually. You click on it and it brings you to another webpage. I'm sure you've all clicked on links before. Well, what we want to do is we want to build links from other sites back to our own site. Why do we want to do this? Google’s problem, as I see it, and this is based on thousands of hours of research, reading articles and watching videos and li...

Haven't you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security, because X10 is here.

I'm sure we've all heard about MSN and Yahoo! Messenger, right? They can be useful, but the setup can be quite time consuming for those who need to use it just once or twice—and the privacy statements are a real bother. For example, we must provide our real details. You could use Fake Name Generator, but if you get caught, you will have your account suspended. I don't have a law degree, but to my understanding the United States recently passed legislation that gives the authorities the power ...

Today's tutorial will teach you how to erase data permanently so that it cannot be recovered. Many believe that having a file shredder on the computer means you are up to no good.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Mining obsidian is not only time consuming, but dangerous. Looking for caves with obsidian and risking death by creeper, zombie, or lava just isn't worth it sometimes. Luckily, obsidian can be farmed, just like cobblestone! You'll no longer need to put your life on the line for this most-indestructible of building materials.

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

JavaScript is one of the main programming languages that the Web is built on. It talks directly to your browser and exchanges information with it in ways that HTML simply cannot. With JavaScript, you are able to access browser cookies, website preferences, real-time actions, slideshows, popup dialogs and calculators, or you create entire web-based apps. The list goes on nearly forever.

L4D2: The Port Finale The Third Chapter in The Passing is the Port Finale. It's similar to the Dead Center finale, where you have to gather gas cans spread throughout the map and fuel the generator to lower the bridge.
I will illustrate a simple, yet effective way to stop tracking and third-party cookies without installing any additional software on your computer. Third-party cookies are often used to track your visits and activities on webpages and can slow down your browser and hinder your privacy. They are often the most common detected adware or spyware installed on most computers.

Hey guys, gals, and everyone in-between! This week's WTFoto Challenge is a real humdinger. For the first time ever, we're asking you to ply your image macro skills and make us belly laugh like a drunken hillbilly at a corn festival. We've created our very own image macro for you to memify—Hobo Advice! Check out the full instructions below to get started.
In this article, I'll show you how to make an awesome "Death Ray" using the large magnifying lens from an old projection TV. The lens is called a Fresnel lens; a device that employs several ridges to focus light, rather than a complete curve.
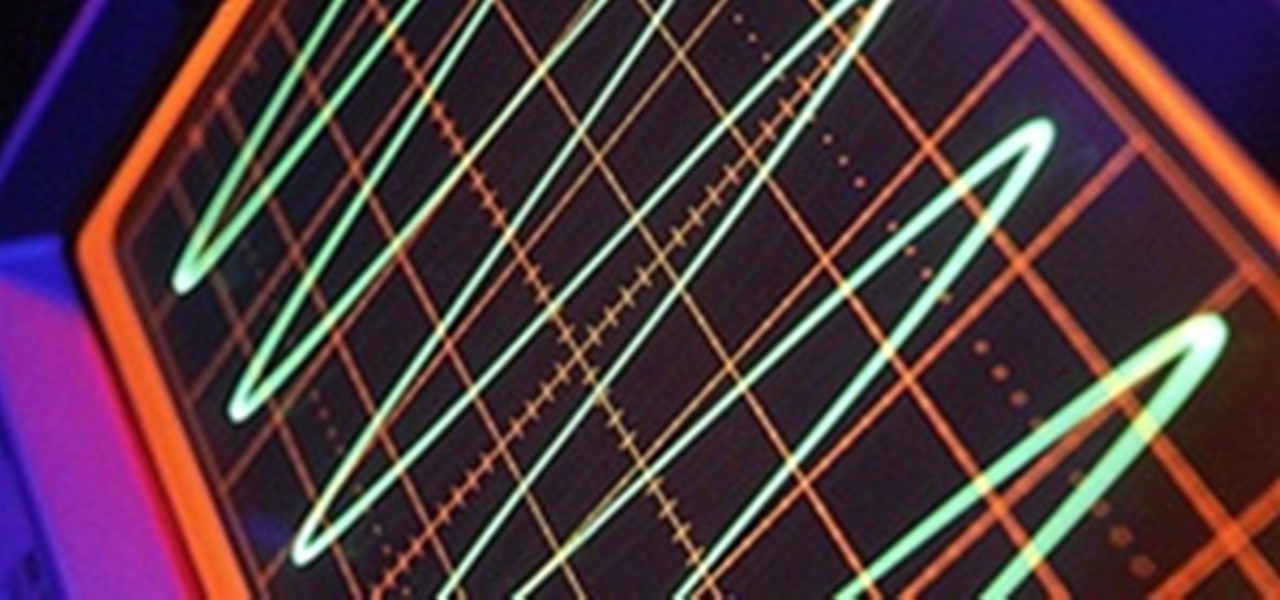
In this article, I'll be showing you how to make a cool visual representation of sound using an old cathode ray tube (CRT) television, a stereo, and a sound source. You'll also need a pair of wire cutters, and a few screwdrivers. To properly understand this project, it's a good idea to learn a little bit about how CRT TVs work. Check out this article on how they work.

It's the most wonderful time of the year. Christmas lights are up, stores are crowded, tacky knit sweaters are making an appearance, and there's the constant smell of something delicious baking in the oven. In this week's Phone Snap Challenge, spread some holiday cheer by showing us your holiday-themed cell phone photos. Post your image to the corkboard by Monday, December 26th at 11:59 pm PST for a chance to win a set of fun Photobooth Props from Etsy store LittleRetreats just in time for th...

The technique of creating double exposure images allows viewers to peer into a unique world, away from reality. The results of combining multiple images into one can really be quite amazing. In this week’s Phone Snap Challenge, we want to see your own take on the double exposure effect. Create your image with your cell phone and post it to the corkboard by Monday, December 12th at 11:59 pm PST for a chance to win a paper pinhole camera kit.

Been hacked once? Twice? Maybe more? You thought abc123 was the only password that is both 6 characters wide and easy to remember? I have some suggestions in store for you. Just read on...

Have an old-school tabula recta lying around? No? Then just print out the chart below. Nothing ensures better password security than this centuries-old cipher technique. Here's how it works, via Wikipedia:

The Job Board is a weekly entry of the most ridiculous Cinematography related jobs posted online. Note: This posting was from a year ago.

When I stumble upon something interesting on YouTube, sometimes I just want to share a few seconds of it with friends. That's where GIFs come in handy: they're small in size, easy to share, and they can be viewed directly in most messaging apps.

Sick of losing quarters to machines that promise you toys? Wanna win the stuffed piggy once and for all?

Watch out Macs. Flashback is back. Variations of the trojan have reportedly infected 600,000 Mac computers around the globe, with about 57 percent in the U.S. and another 20 percent in Canada.

As of today (January 18, 2012) many websites have "blacked" out their content for the day, one of the more notable websites is Wikipedia.org. As this can be a small compromise as an act of protesting against the heinous bills going through the United States' Congress. A lot of these websites are using a type of Java-Script or JS for short, and others are using simple little Pop-Ups to block the sites. Through the use of some clever addons everyone that cares about their online security should...

Web-spying technologies like FaceNiff, Firesheep and Newstweek are out there showing the world just how easy it is to see what you're doing online, but they're amateurish in comparison to what real hackers could do to you if they catch you browsing unsecured websites.

Google's sociable equivalent to the Facebook Like button is finally here, and it works very similar to your favorite social network's recommendation system, except it shows up directly in Google search results. Whenever your Google friend gives a website or webpage the +1, you'll see it in your search results, as long as you're signed into your Google Account.

Can you really make an explosive from salt, sugar and weed killer? Does glycerol and water actually recover text from burnt paper? Is it possible to develop film with a first aid kit and some orange juice? MacGyver says yes.

Have you ever felt the desire to reach out and touch a galaxy? Or "feel" those stunning nebulas and planets you see in Hubble photos? As alluring as it sounds, it's safe to say the odds of your whim coming true are nonexistent. You'd have to travel about 6 earth years and spend millions of dollars building your own personal spacecraft to get close enough to actually wave your hand through one of Saturn's rings. But in an attempt to help the blind "see" what they're missing, some semblance of ...
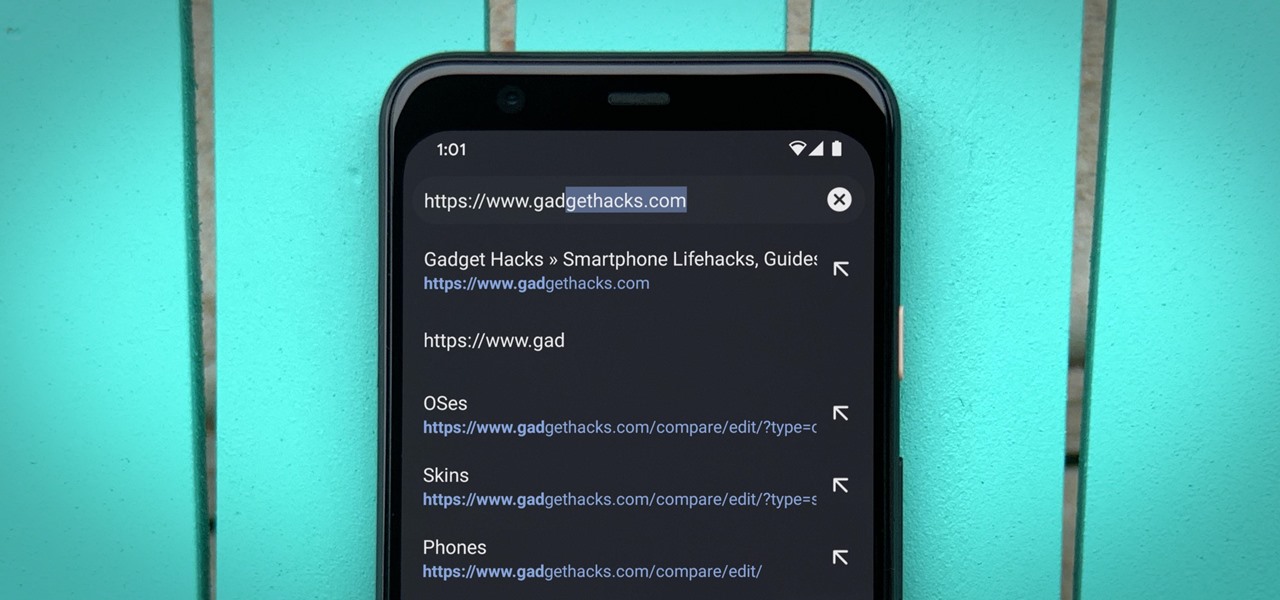
Most Android phones have a Google search bar somewhere on their home screen. But did you know you can replace this with a different widget that actually functions as the address bar in your Chrome browser?

You're scrolling wrong. Kind of a weird accusation, isn't it? But you are. If you're still scrolling through long pages on your iPhone swipe after swipe, you're simply wasting time. There's a much faster way to get to where you want to be, whether that's on a lengthy webpage, long conversation in Messages, or multipage document.

Data restrictions suck, but Google wants to make it suck just a little less. Rolling out is the latest update to their mobile Chrome browser, Chrome 32.
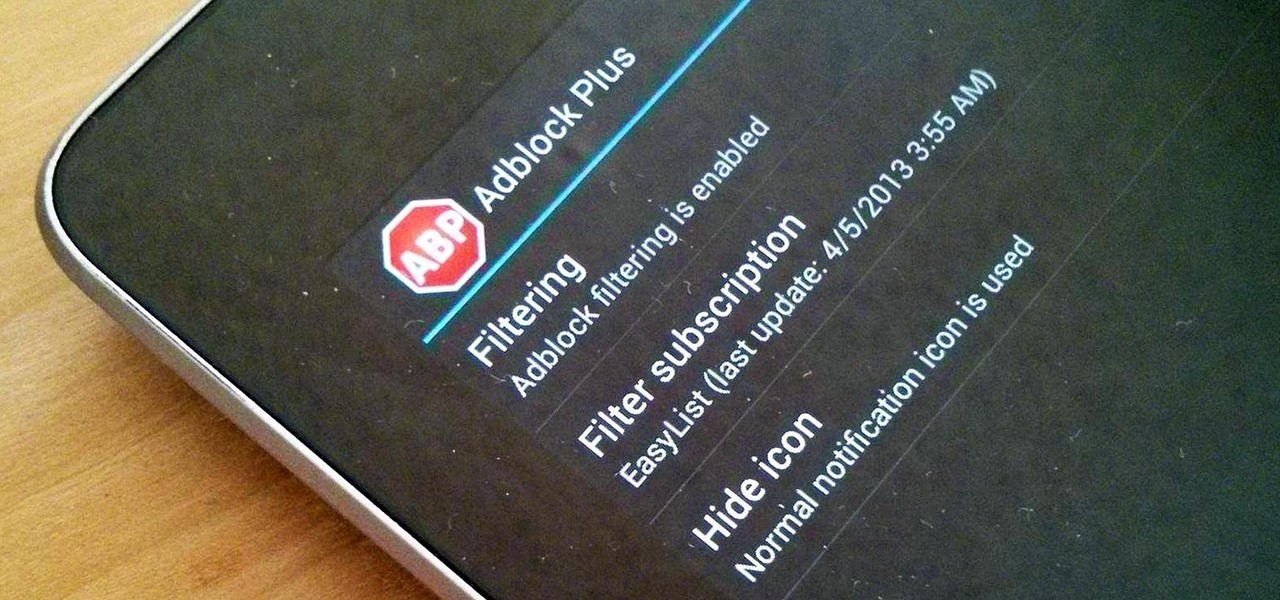
Adblock Plus is a well known add-on for Google Chrome and Firefox that eliminates all of those annoying and obtrusive advertisements on the webpages that you visit.

This may be an old trick, but it is still very useful. Head.js proudly proclaims that it is the only script you need in your head. You can use it to parallel load all your scripts. This is much faster than loading them one by one.

Notes for Gmail now allows you to insert sticky notes directly onto your email threads in Chrome. The browser extension, currently in beta, allows you to annotate your emails as a whole (thread)—or individually. You can add as many sticky notes as you would like and they all appear at the top of the webpage for easy accessibility. To download the application, go to this page and request an invitation. They add users everyday—I was added almost instantly after I applied. Once you've downloaded...
HOW TO CAPTURE STREAMING MEDIA many websites stream songs and videos

Security researcher Ravi Borgaonkar from Berlin has discovered that hackers can hide an 11-digit code in a webpage that can wipe out all of the information on your smartphone—contacts, photographs, music, applications, and anything else of importance. The attack takes no more than a few seconds and nothing can be done about it. NOTHING. This begs the question—are you susceptible?
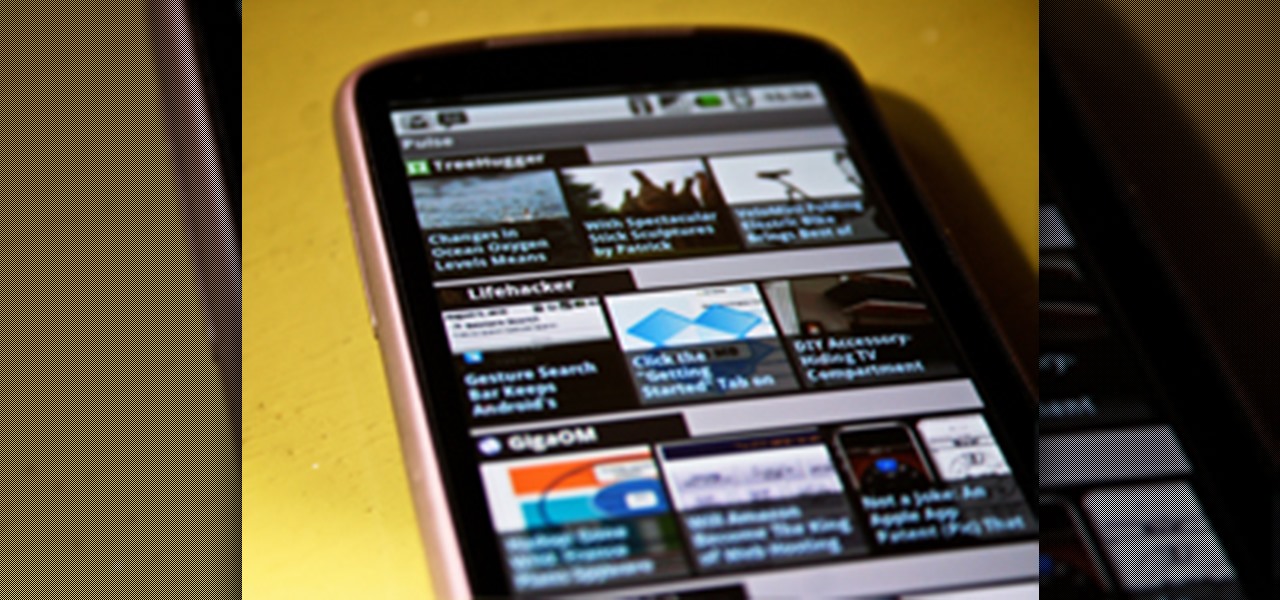
The Android App Market is flooded with tons of new mobile applications each day. But there can't be that many developers out there familiar with the Android OS, so where are all of these apps coming from?

The video gives a step by step tutorial on how to replace the water pump, all belts and the shaft seals on a Porsche 944 S2.