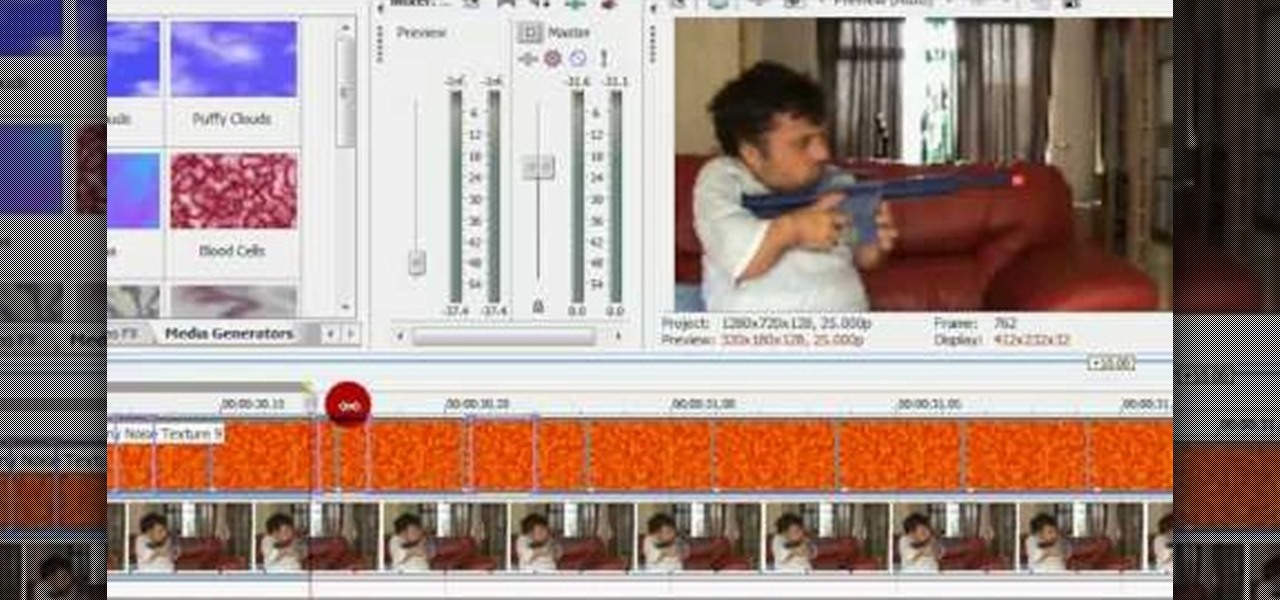
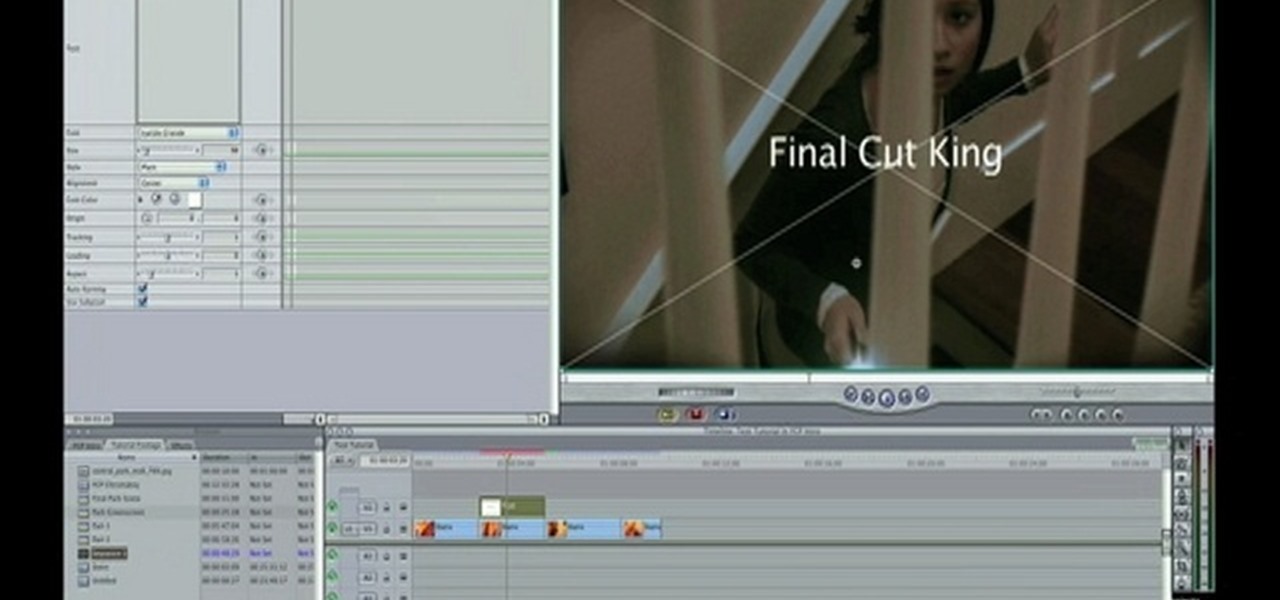
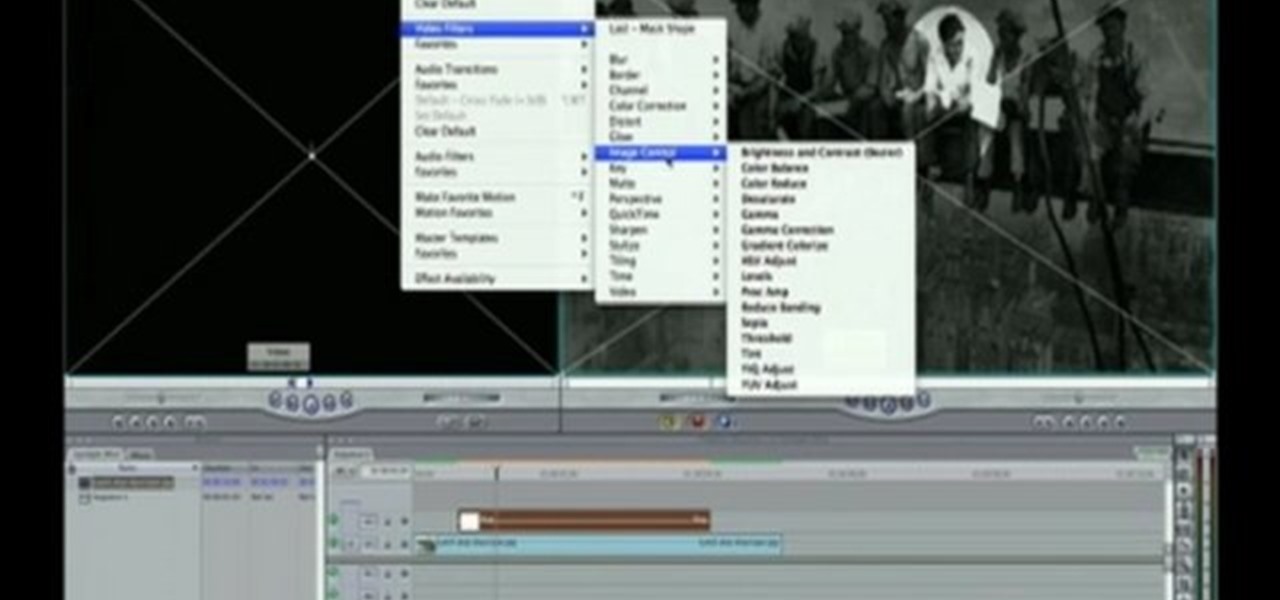
This tutorial shows you how to use transitions and media generators in Sony Vegas. You should have a basic idea of how Sony Vegas works first, and if you don't, you can watch Montagical's other tutorials here first.

Use Fruity Loops generators to create a variety of sounds. Learn how to use the sound generator features of FL Studio in this free digital audio workstation tutorial from our music recording expert.

This is the third part of my electromagnetic pulse series (see Part One and Part Two). By now, I've covered the hardware and general concept of electromagnetic pulse generators, but how exactly do they disable electronics? How can an invisible field of energy have such a catastrophic effect on computers, cell phones, and most any other electronics? I'll be answering all these questions in part three of Making Electromagnetic Weapons.

Build this ultra-simple AC electric generator from magnets, wire, and cardboard. (And a big nail!) Light a small lightbulb, or flash a red LED.

At the end of the Sacrifice, you'll need need to turn on three generators at the same time, so you'll need two friends to help you get this. Once the generators are hit at the same time, you'll get the Chaos Generator achievement.

This video details how to set up a generator to provide back-up power for a home or business. Generators are the ideal emergency power solution for a home or business, generators can automatically transfer the power load from the utility power line to the generator when an outage occurs. To make sure the generator is always ready, generators can self run weekly and perform self diagnostics so maintenance issues are minimized or eliminated. When planning to use a portable generator, it should ...

Danny Lipford gives us tips on setting up and maintaining a portable generator. Set-up usually includes assembly of things like wheels and handle kits. Most portable generators come without oil so you will need to add it. Be sure to check the owner’s manual for the proper type of fuel to use.

Muzzle flashes are basically firing and explosive effects that come out of the pistol or barrel of a gun. These firing effects can be created on Sony Vegas using a masking technique.

For this Final Cut Studio video tutorial, Zach King will teach you how to create and manage text in Final Cut Pro. To create and manage text, just go to the Video Generators Tab in the Viewer window, go to Text, and choose your favorite option, or just the plain old Text. Check out the rest of the process in Final Cut. Let the Final Cut King show you how!

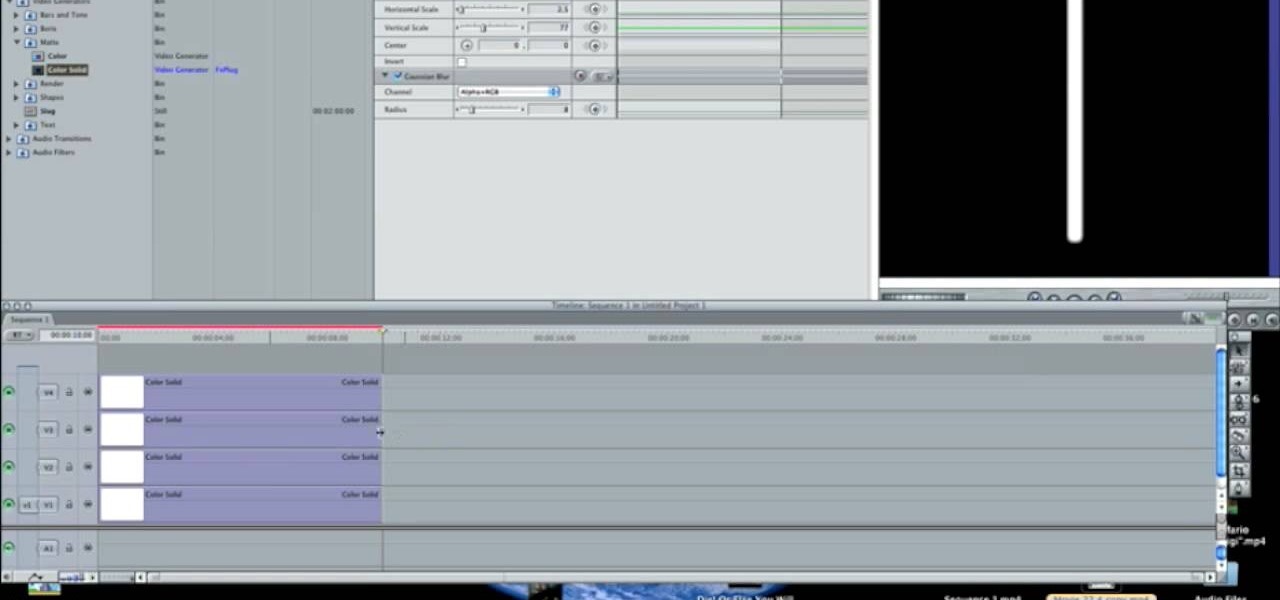
To create a green screen, open up the program Sony Vegas. Now go to media generators. On the left hand side of your screen there should be a list with the link solid color right in the middle. Click on that and a menu with a variety of different colored boxes will appear. Double click on green. A menu will pop up so that you can adjust the shade of green just by moving the vertical line to the left or right. After choosing the appropriate shade, save the green box as either a video or picture...

For this Final Cut Studio video tutorial, Zach King will teach you how to create an Apple reflection look in Final Cut Pro. To create an Apple reflection look, just go to the Video Generators tab, go to Render, and then Gradient. Next, go to Controls, click Gradient Type, go to Horizontal Bottom To Top, and also check Gaussian Blur. Check out the rest of the process in Final Cut. Let the Final Cut King show you how!

For this Final Cut Studio video tutorial, Zach King will teach you how to create a spotlight effect in Final Cut Pro. To create a spotlight effect, just drag your photo of choice into the timeline, set and in and out point, go to video generators, and use the slug. Then press the red overwrite button. Next, select the clip, go to the Effects tab, go to Video Filters, Matte, and then Mask Shape. Check out the rest of the process in Final Cut. Let the Final Cut King show you how!

This is an intensive one-day overview video tutorial of the fundamental concepts of the Ruby on Rails Web programming framework, presented by the UC Berkeley RAD Lab. The overview consists of six sections of approximately one hour each. Click through the video chapters to go through the Ruby on Rails programming course.

There are many different things that could contribute to a power or gas outage or accident in your home. To be properly prepared for an emergency or other situations that endanger you, take a look at this video from SDGE on simple tips to keep safe, including discovering gas leaks and using power generators to maintain eletricity in your home during an outage.

Ian uses round magnets, pencil, clay and glass slide to work his magic science experiment. Magentic levitation is said to be a solution for energy costs of trains because it cuts down friction and creates what is mythically regarded as a perpetual energy motor. This is an interesting toy model of how the maglev trains and large scale generators work

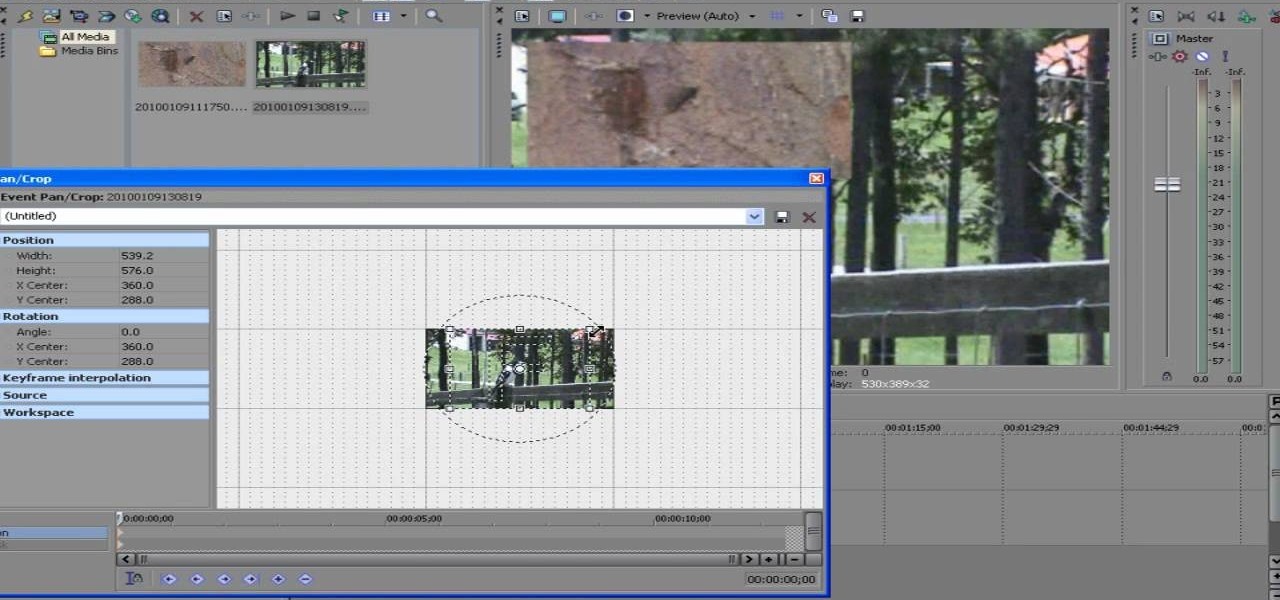
ConnersTutorials, teaches you how to put two videos playing simultaneously in one movie. You use Sony Vegas and drag both movies in the time-line below. Then you press Event pan/crop on the first video. Right click and choose Match output aspect. Then re-size and move the video as you want. Do the same for the other video. Go to Media Generators to choose the background, which can be a solid color, a picture or another video. Just drag that down in the movie time-line when you're pleased. All...

Check out this brief video tutorial on using FxFactory the visual effects plug-in package for Final Cut Pro or Final Cut Express and Motion. You'll see the filters, generators, and transitions included, and see how they are grouped inside Final Cut's browser. There are a tones of effects for you here, just watch and see what you can do with it all.

This tutorial helps you utilize the media generators tab to create a short, but still cool looking intro for your videos.

Applying for jobs can be a truly miserable experience. Sending out endless résumés, filling out those janky online applications, and creating cover letters can really wear a person down. So, any suggestions that make that process easier are always welcome.

Open your video in Final Cut Pro. Go to Effects>Video Generators>Boris. Then drag the option called Title 3D over your video. Then select Title 3D and go to your controls. Then click on "Title 3D Click for options". Now a new box should be open. Type your text into it. Then, highlight your text and pick the font size, then hit enter. Next, select the font. After that, go to the bottom test menu, and select Drop Shadow. Make the shadow distance 2. For the shadow opacity, turn it up all the way...

In this how-to video, you will learn how to make a light saber or similar image in the Final Cut Express program. First, go to the effects tab and go to video generators and select color solid. Drag this to the viewer. Go to the control tab and select the blue color. Now drag it to the time line. Double effect the color solid and go to mask shape. Select filters and change the effects settings to 2.5 horizontal scale. For the vertical scale, select 75 to 85. Go to the effects, video effects, ...

What would it be like to have clothing that killed microbes? Or paper that repelled pathogens? A research team from Rutgers University has developed a prototype out of metalized paper to zap the bad guys without being super expensive. Sound good? Read on.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

Use the Soundfont Player and FL Keys feature in Fruity Loops to create a variety of sounds. Learn how to use the sound generators and plug-ins of FL Studio in this free digital audio workstation tutorial from our music recording expert.

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

If you thought the news coming from China about the coronavirus might not affect your daily life in Europe and in the Americas, think again.

Between Renault Truck's testing of the HoloLens in factories and BMW promoting its newest model through Snapchat, the auto industry is hot for augmented reality to improve internal operations and engage consumers.

I rarely receive spam mail, but every now and then I’ll get an email from Cat Fancy Magazine. I’ve never read an issue of Cat Fancy Magazine or been to their website. Actually, I’m allergic to cats. So how did they manage to get my information?

When I see the words "free trial," I know I'm probably going to have to whip out my credit card and enter in the number to "not get charged." Then I end up forgetting about the trial and want to kick myself in the ass when I see my statement at the end of the month.

You probably know Lenovo from their low-cost Windows PCs here in the states, but something you may not be aware of is that they also make smartphones. Right now, their biggest market is in China, but a rumored merger with BlackBerry could make Lenovo a contender in North America, not to mention one of the biggest smartphone manufacturers in the world.

QR codes are so handy. Nowadays, all you have to do to scan one is open your phone's camera app and tap a button. But creating one is a different story — online QR code generators aren't always trustworthy, and most phones don't have a built-in feature for it. Thankfully, Google Chrome now does.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

The fifth annual Amazon Prime Day is upon us. Starting July 15, Amazon will offer thousands of deals on products across its site, kicking off at 3 a.m. EDT. This year, it will only run for 48 hours, so you have even less time to act. To save you some of that time, we made a list of the best deals for smartphone accessories.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

We see Steampunk props all the time and wonder where the maker found all their pieces. In fact, for some people it's almost like a game to examine each prop and see if they can name all of the original parts.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

If you're like me, you don't have time to sit down and leisurely read an entire article from start to finish — but you still want to be informed throughout the day. Instead of just browsing the daily headlines, there's a free service that will summarize any article you throw at it, giving you a better idea of what's going on without committing to reading an entire article.