
How To: Prepare Indian moong dal dosa
Watch as Manjula prepares Indian moong dal dosa. This version of dosa is much easier to make since it does not require overnight fermentation.


Watch as Manjula prepares Indian moong dal dosa. This version of dosa is much easier to make since it does not require overnight fermentation.
This two part tutorial for Sony Vegas explains how to use 3D (axis' X Y Z). It will tell you the fundamentals to work in 3D space, and also give examples of using this.

Making rounded corners is literally a cornerstone of learning Photoshop. That's because rounded corners are used in many different applications, from harmonizing pictures in a family photo album to create a fun pamphlet for class to setting up an Indie-style vintage picture for your Flikr.

Have you always wanted to spread your mark on urban society, but were a bit of a scaredy-cat? Well now you have the chance of convincing anyone and everyone you're the next great graffiti artist by creating graffiti in Photoshop. If anyone asks just say the local council came and cleaned it off and it's a good thing you took a picture of your art, isn't it?

Check out this fun version of Rudolph for Solo Guitar. This song is not really for complete beginners because it uses alternating bass patterns - but if you have had some experience with that kind of thing then you will probably find it pretty straight forward!

Check out this solo guitar version of this classic new years eve drinking song "Auld Lang Syne. Aimed at intermediate players, this guitar lesson starts easy and develops a bit.
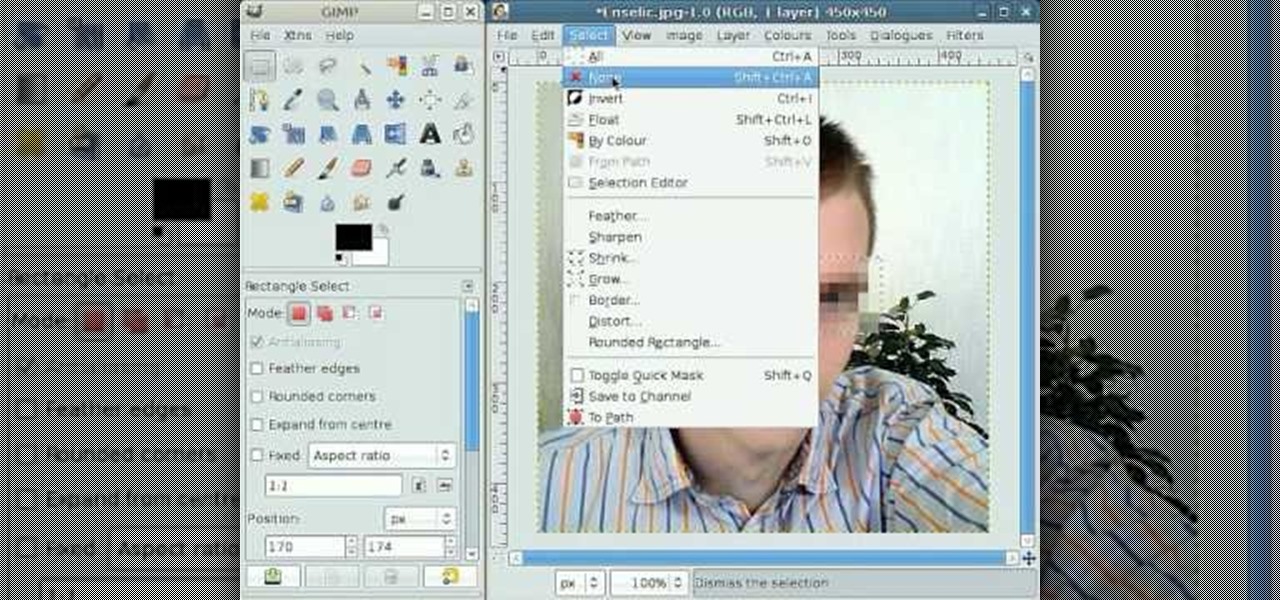
By following this tutorial you will learn the concept of selections in GIMP. Whenever he says "layer mask" he really meant "selection mask".

In this video on Super Smash Bros Brawl (SSBB) for the Nintendo Wii, I showcase how Captain Falcon, Ness, and Lucas work, including their move properties and what I believe will be key strategies to learn with them in the long run. For Falcon/Ness, I show a bit of the differences from their Melee counterparts. Unfortunately, the camera ran out of space as I was doing Wario, so check out my Robot/Wario tutorial video instead for a full demonstration of Wario's moves!

In this ShowMeDo John Montgomery demonstrates how to create a project in Eclipse, then write and run a simple "Hello World" Java application. He also demonstrates the code-completion features of Eclipse, how to use the find and replace functioning and use the CVS version control system.
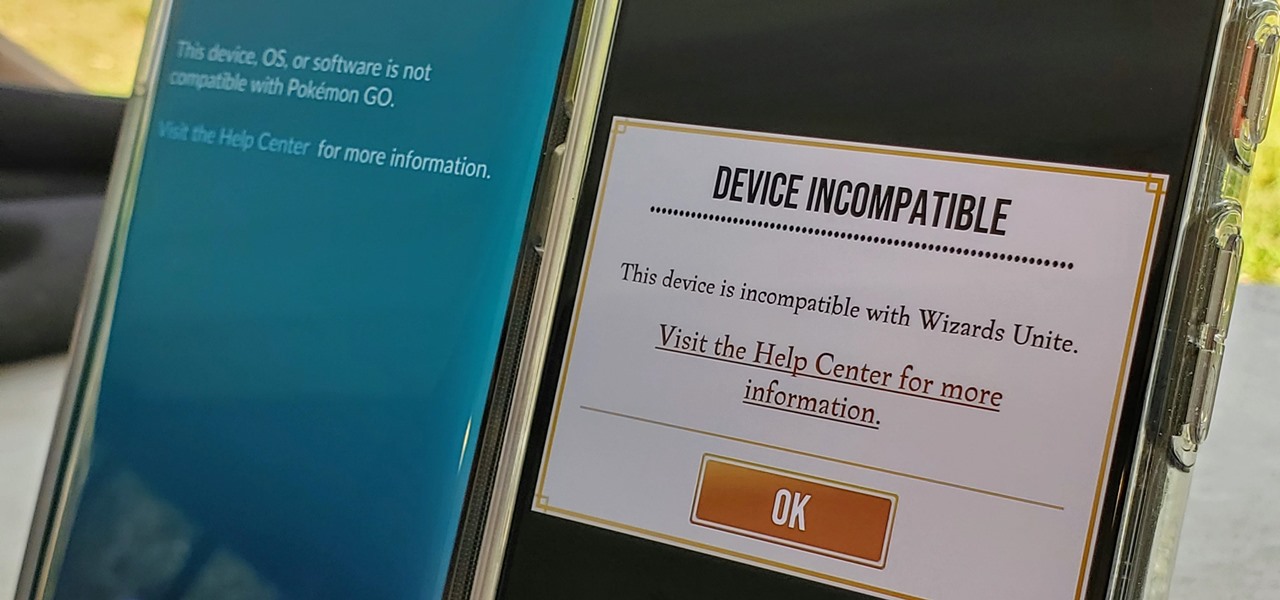
Both Pokémon GO & Harry Potter Wizards Unite are augmented reality games developed by Niantic, and neither needs much introduction. Pokémon GO, all by itself, created a worldwide phenomenon that still carries a strong fan base years later — Wizards Unite is working on doing the same. However, things are not all fun and games, as you might think in the world of monsters and magical creatures.

UPDATE: The OnePlus 8 Pro has been released! Check it out on the official OnePlus website or read through the rumored specs we've left below for posterity.

With EA chief executive Andrew Wilson stating the official mobile version of Apex Legends won't arrive until the 2021 fiscal year, fans have to wait at least another year to enjoy their favorite battle royale game on the go. But for those who can't wait, there are ways to play the game on iPhone and Android right now.
Many users have reported Android's speech-to-text feature adding an 'Oh' before each comma. How annoying is that? Fortunately, Reddit user Jay-jay1 has found a solution to this pesky problem. This quick-fix should make your 'Oh' so annoying problem disappear.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

In 2019, Sony is mixing up its design, attempting to stand out among the sea of familiarity. Instead of emulating Samsung with punch hole cameras, they decided to target a rare section of the market, content consumers. There's the Xperia 1 for those who want the best, and the Xperia 10 and 10 Plus for the budget crowd.

While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

| Updated Aug. 22, 2019 with new phones. When will my phone get Android Pie? For the first time since Android's inception, this question shouldn't have an answer that lets you down. That's because Android Oreo introduced Project Treble, a new low-level arrangement that makes updating a lot easier. So with Pie, it's not if your phone will get it, but when.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.
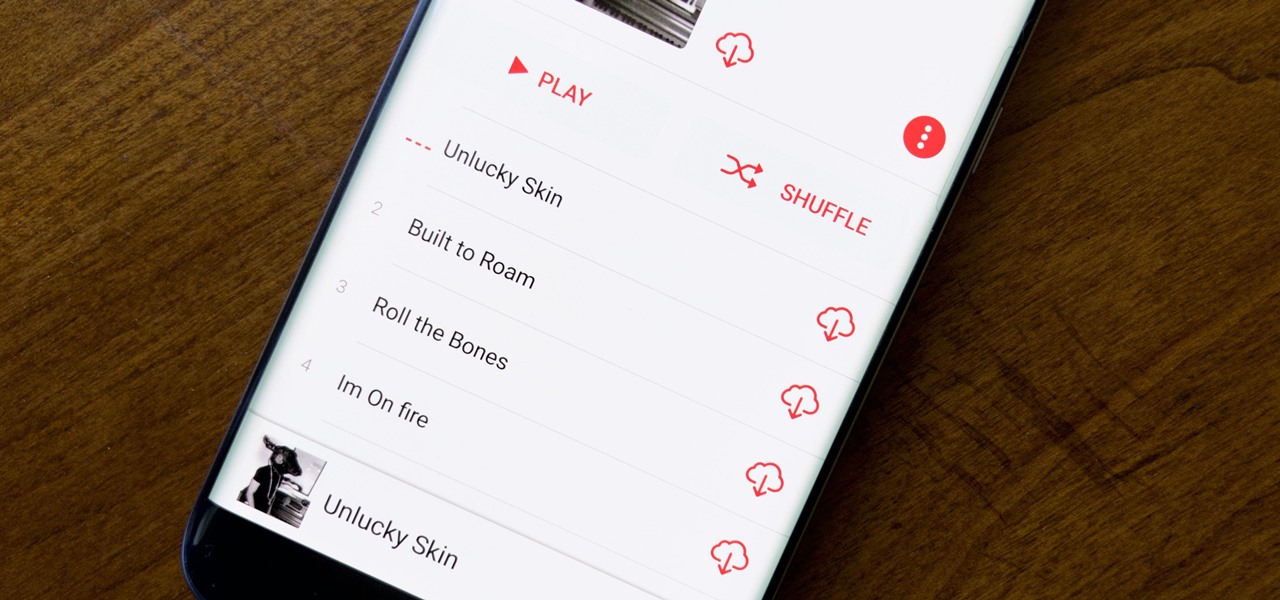
For most carriers, "unlimited" data plans aren't really unlimited, and they still cost more than data limited plans. So while subscribing to music streaming services and storing your own music library in the cloud may be more convenient, it may eat your data up like candy. To keep that from happening, try downloading tracks from Apple Music for offline playback.
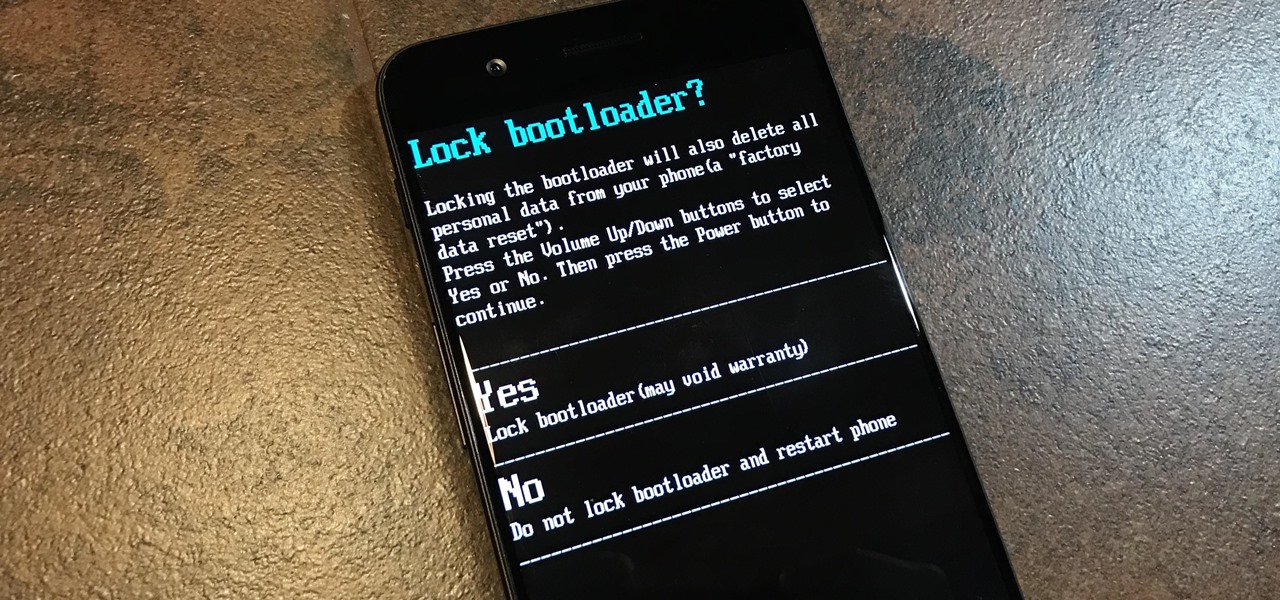
To please those of us who love to mod and root our Androids, OnePlus has made both the OnePlus 5 and 5T relatively easy to customize — so much so that the 5T topped our list for the best phones for rooting. Unfortunately, unlocking the bootloader and using root to modify the firmware on your OnePlus 5 or 5T makes it hard to update to a new firmware such as Oreo when compared to stock.
The Pixel 2 is a solid upgrade when compared to the 2016 model, but we've reached a point where the latest generation of a smartphone is never leaps and bounds better than the last. It's hard to justify dropping nearly a grand on a phone when it doesn't improve your situation much — especially when a few software tweaks will give you most of the upgrade for free.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

Nintendo's Super NES Classic system, a pint-sized version of the iconic Super NES from the '90s, is highly anticipated in the gaming world. The retro system has already met its fair share of controversies and it's been a long journey to preorder. Finally, the Super NES Classic is officially available for preorder, but it's selling out fast.

If you use the Google Assistant on your Android device, you can easily send a text message to any one of your contacts. But even though that same Assistant is powering the Google Home, you can't use the smart speaker to accomplish the same task — at least, not without some tinkering.

The sheer variety of Android devices on the market is staggering—one report suggests there are well over 24,000 distinct phones and tablets floating around out there. When you consider that each manufacturer adds a few tweaks to the Android code base here and there, that makes for a lot of software variations, which in turn means there needs to be many different root methods to match this variety.

Let's say you're flush with Google Opinion Rewards credits, or you just got a Google Play gift card for your birthday. This is a perfect opportunity to remove ads and unlock new features by upgrading some of your free apps to their paid counterparts, or to finally purchase that app you've been lusting after that doesn't offer a free version.
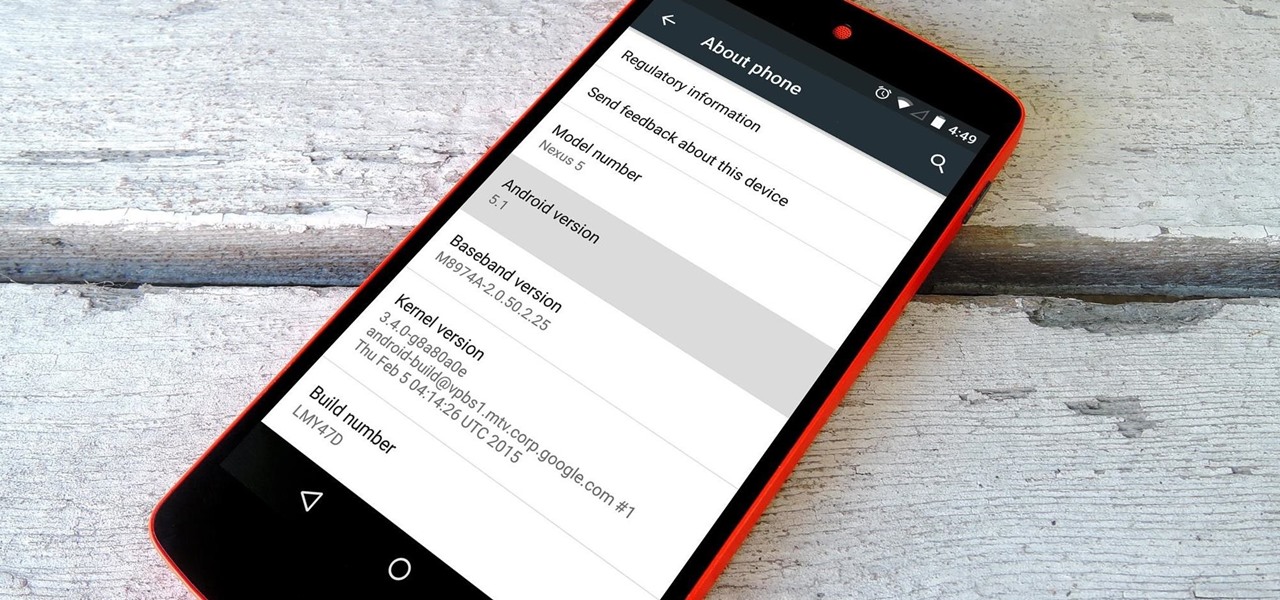
Google inconspicuously announced an Android update yesterday, and while it's not quite the overhaul that the initial Lollipop release was, version 5.1 brings plenty of bug fixes and new features.

Android 5.0 "Lollipop" has only existed for a few months, but a leaked version of Samsung's take on the firmware has already been spotted in the wild. This update came straight from Samsung, and brings with it a plethora of new features, including greatly improved performance and a revamped TouchWiz UI.

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

My phablet has incredible battery life, but that doesn't mean I wouldn't like it to last even longer. Unlike the Samsung Galaxy S5, the Note 3 does not come equipped with Ultra Power Saving Mode, which can keep the phone running for another 24 hours with only 10% power remaining.

It seems like custom Google Now commands are a dime a dozen these days. With Commandr for Google Now giving non-rooted users their first taste of custom voice commands just a couple weeks ago, you may wonder why we're covering this subject again.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

You know what's awesome? You own a Nexus. That means, with Google's blessing, you have easier access and control over your device than other manufacturers allow. You can really dig in and do some interesting things if you root.
If you're tired of the boring old ringtones on your iPhone but don't want to shell out extra dough to buy a new one, here's an easy way to make your own.

Download the P2 Step-by-Step Reference Guide. With Avid, editing footage captured with the Panasonic HVX200 camera is fast and easy. Avids system uses the same native file format as Panasonic P2 memory cards, so theres no need for any transcode, capture or file conversion process at all. You can edit directly and immediately from the P2 cards if you like or have Avid Media Composer create a rapid backup of your files. Nothing could be simpler or more immediate.

So you need to find the p-value for your hypothesis test. To do so, employ the spreadsheet program Microsoft Excel. Using a simple formula, you can easily determine the p-value for your tests and thereby conclude strong or weak support of the null hypothesis.
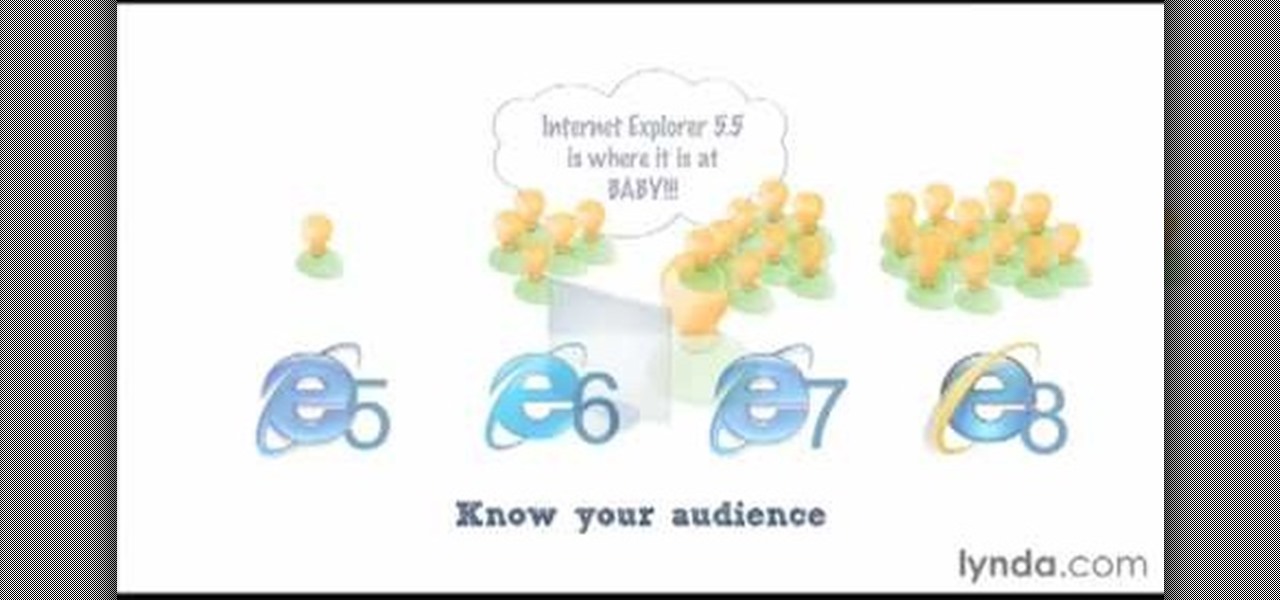
James Williamson for Lynda demonstrates designing for multiple browsers. The most frustrating aspects of web design is constantly dealing with the settle and some times not so settle differences in browser rendering. While they moved to a standard spaced, CSS control presentations has made life infinitely easier for web designs. Dealing with bad browser behavior is one of most unfortunate side effects. All browsers render our pages same because each browser reads and renders the HTML and CSS ...

Learn how to play hide-and-seek. If you need a rainy day activity for the kids, or just want to relive your childhood, hide-and-seek is a great game for everyone.