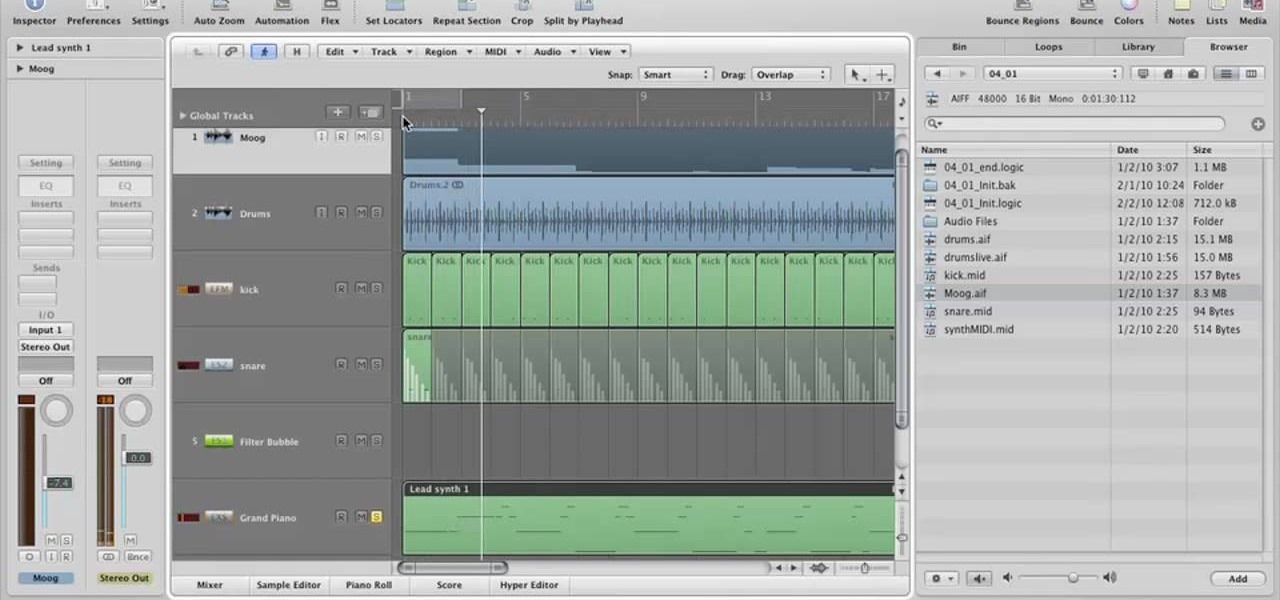
This Lynda tutorial teaches how to use the Logic pro, a songwriting application. Midi sequencing and quantizing is the main focus of this video. Midi is a short name for Musical instrumental digital interface. Midi is not sound. It is a low resolution computer protocol, developed in early 80’s to enable computer to communicate each other. Midi is fast, simple and reliable. It has a intensity stream. In this project, Scot Hirsch explained how a midi file is manipulated in Logic pro. Midi file ...

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

Time is money, and if your job requires sending out hundreds of generic emails—think "Thank You" notes and sales pitches—you could save days of work by creating templates stored within your Gmail called "canned responses."
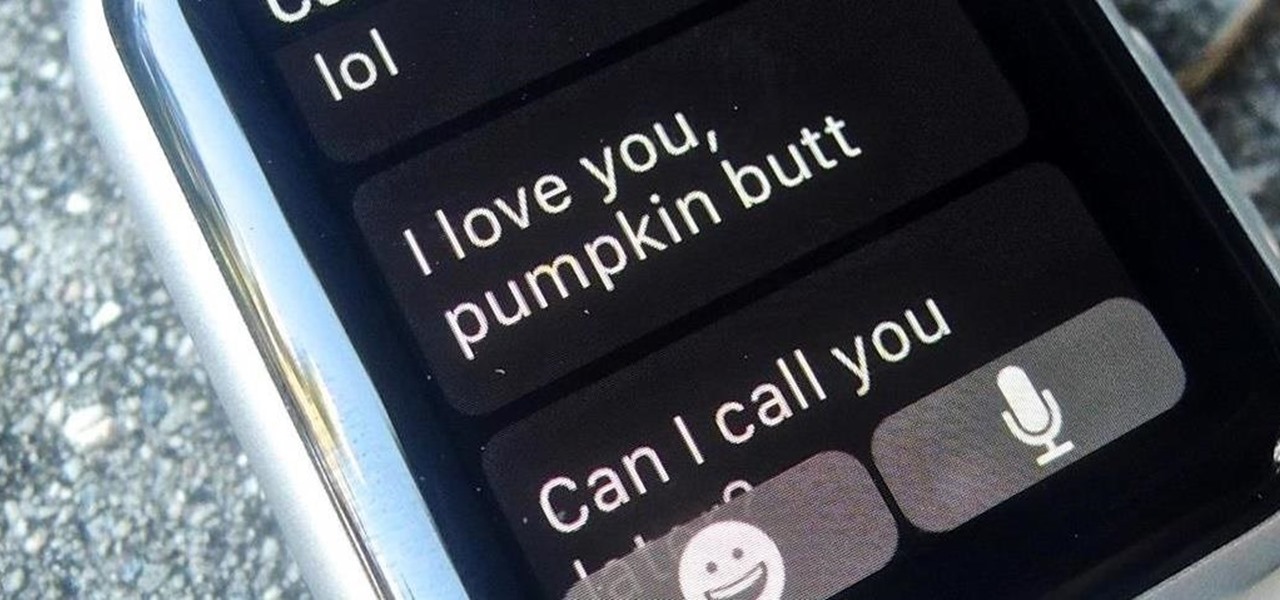
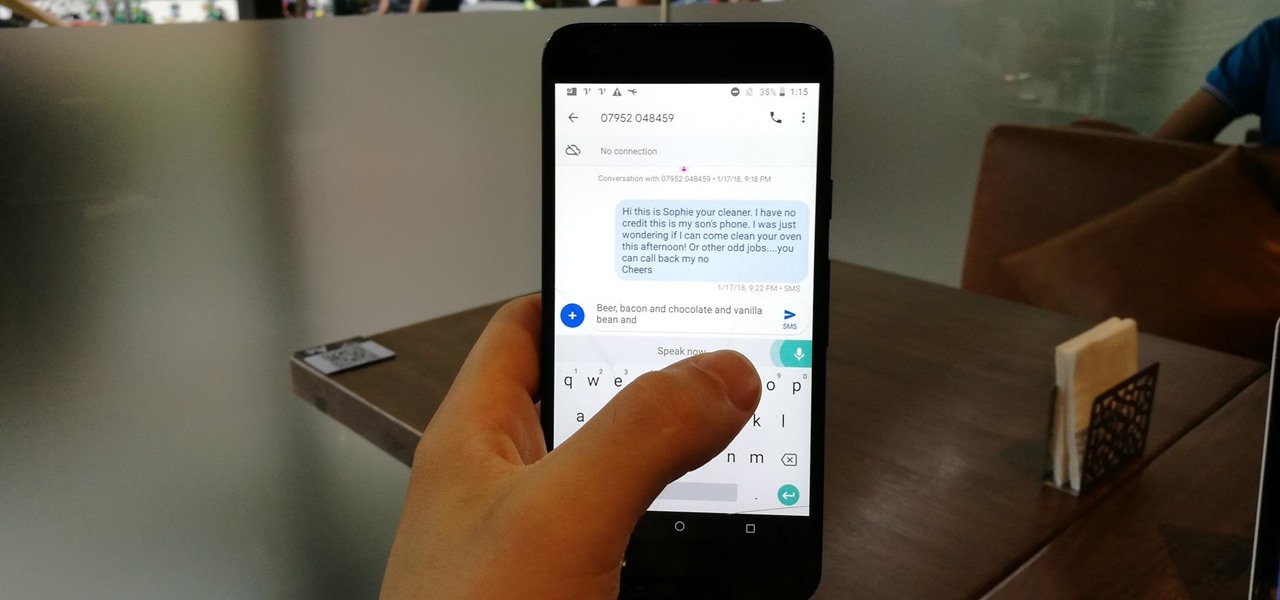
The display on the Apple Watch is way too small to even attempt typing on it, which is why the Messages app only allows for responses using default replies or by speaking a message. But you won't always be able to speak a message, and often the default replies will be too generic to want to use.

Accompanying Snapchat's core features, like editing snaps and applying filters to them, is Bitmojis. These are small avatars that you create in your own likeness and use all throughout Snapchat. Formerly, there were two "styles" that you could pick from to make your Bitmoji: Bitstrips style and Bitmoji style. But Snapchat has a third style now that will redefine the way you use Bitmojis.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

To be twentysomething is an awkward time for entertaining. As we graduate college and begin to work in “the real world,” there is a yearning to transition from keg parties into dinner soirées. However, though the desire is there, often the bank account is not. Here are some ways to do in the kitchen what twentysomethings do best: fake it until you make it. (In other words, host a fabulous dinner party for four and still be able to make rent this month!)

Icebox cakes are some of the most satisfying, easy desserts to put together. This version made out of ice cream sandwiches takes the cake, literally, because the layers are almost pre-made for you. Simple and pretty when cut and served, it will be love at your first creamy bite. Depending on whether you want a layer of chocolate crunchies in your ice cream sandwich cake or not, this could be either a two-ingredient ice cream cake or a four-ingredient one. If you don't need the crunchy layer, ...

The Snapdragon 801 processor inside the OnePlus One puts the device on par with other phones like the HTC One M8 and LG G3 in terms of power and speed. While the OPO is just as fast and responsive as many of the flagships currently available, there's no reason why we can't try to squeeze every last bit of speed and performance out of it.

Plagiarism is a serious offense, even if you are copying from the web. With this tutorial, learn how to cite websites properly using MLA format and avoid any trouble.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

LOOOK, a Seattle-based mixed reality and development studio, can now peer into the future with their new geotechnical engineering visualization application for Microsoft HoloLens.

"Does bottled barbecue sauce even taste that bad?" a friend of mine asked. Well, truthfully, no. But it also doesn't taste that good, especially if you've had truly great barbecue or even your crazy uncle's homemade sauce at a holiday cookout.

Many users have reported Android's speech-to-text feature adding an 'Oh' before each comma. How annoying is that? Fortunately, Reddit user Jay-jay1 has found a solution to this pesky problem. This quick-fix should make your 'Oh' so annoying problem disappear.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

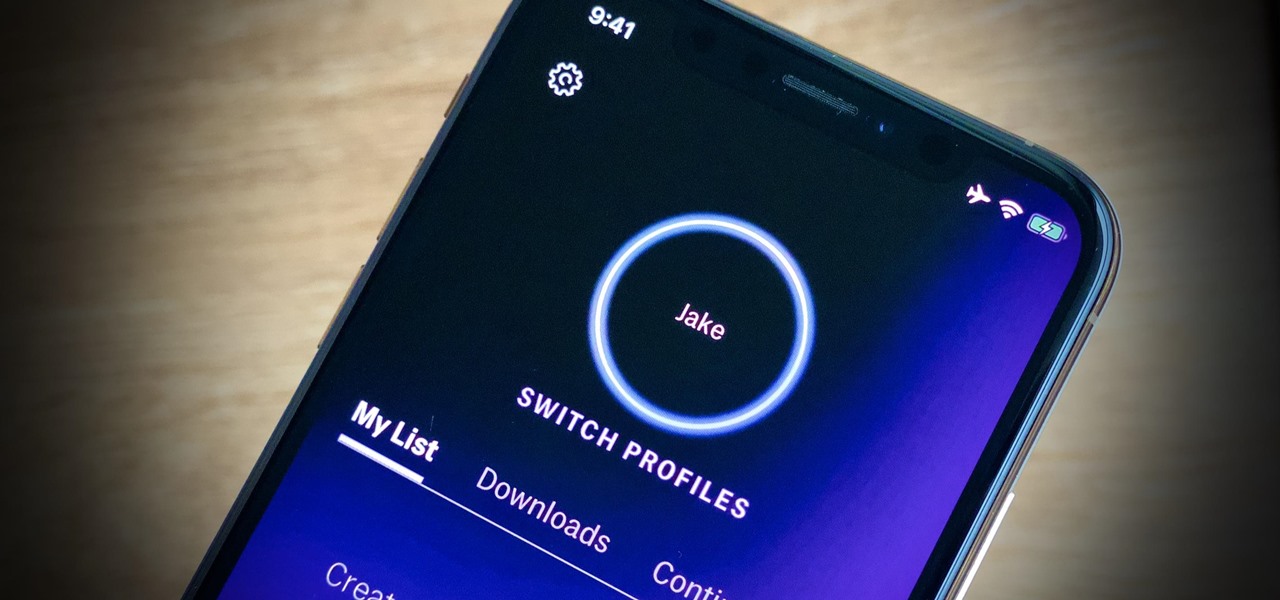
Many streaming services offer user profiles for different people in your household, some of which also include profile images. In most cases, you can set a custom profile image to better differentiate and personalize your account from the others, and HBO Max lets you do the same, albeit, with limited options.

Few things are more important than search engine optimization when it comes to increasing a brand's visibility online. Regardless of whether you're launching a new business from scratch or working as a marketing professional at a major corporation, you need to ensure that you're drawing the most people to your website and affiliate links by utilizing the latest and most powerful SEO tools and methods.

Let's face it: standing out in the digital world is challenging. Graphics platforms are either cumbersome to learn or produce generic stock art. A better solution is needed.

I already know what you're thinking: this guide is blasphemy. I am showing you how to turn a Galaxy Note 10 or 10+ into an iPhone 11 Pro Max. And while I'd usually agree with you, hear me out. How can you know you don't like something until you try it? So here is your way of trying out an iPhone using your Galaxy Note 10.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

Lately, any subject in the realm of politics is a figurative powderkeg primed to explode on the nearest social media channel. Now, one app wants to use your iPhone and AR to strike a match.

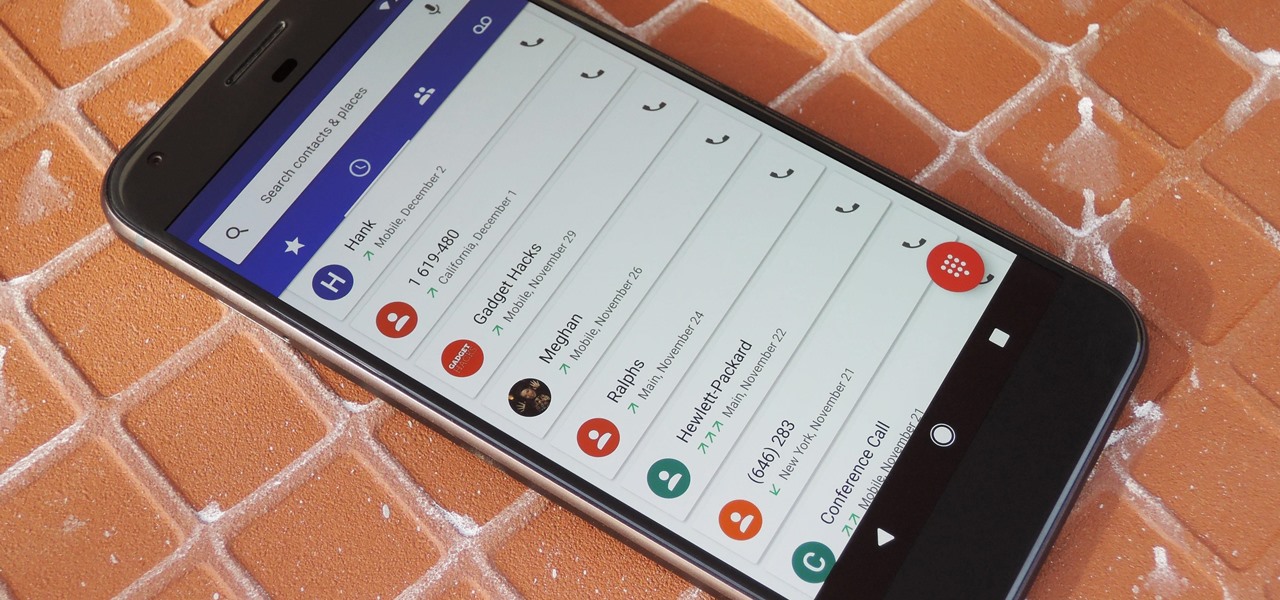
By default, Android limits your call history to the last 500 incoming, outgoing, or missed calls. When you reach this limit, older entries get trimmed off the bottom of the list and deleted forever. This isn't an issue with storage space, because even the biggest call logs only occupy mere kilobytes, so it's really just an artificial limit.

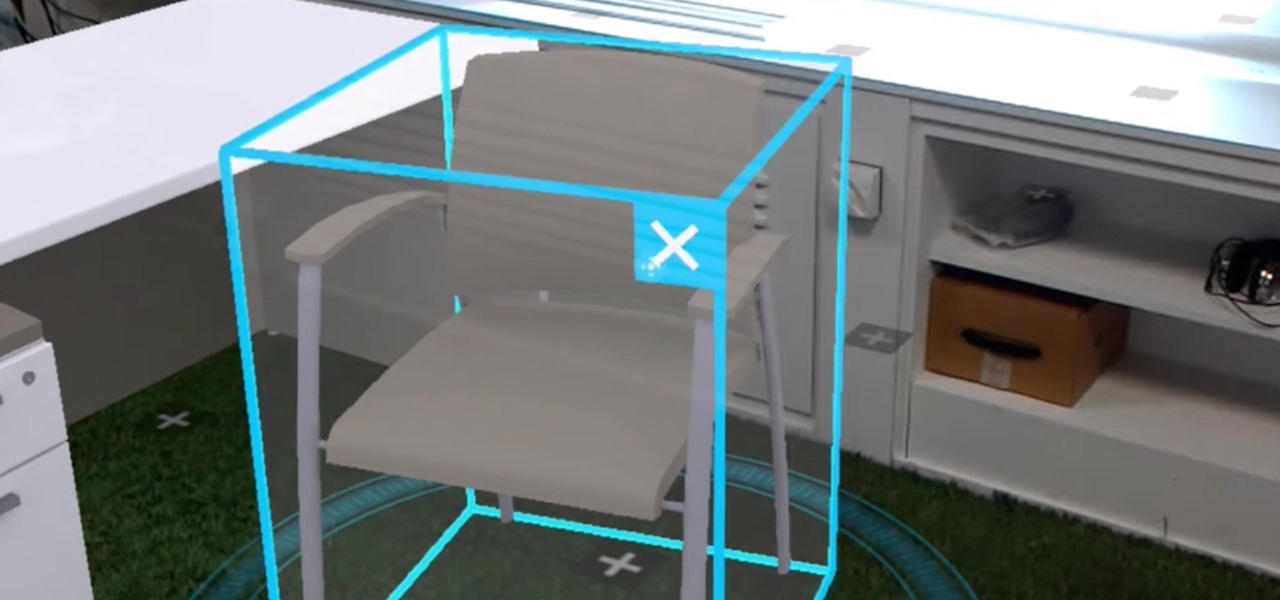
When figuring out how to arrange your furniture in a new room, you traditionally have to measure everything and use your imagination. HoloPlanner has a better idea: just place holographic furniture in the room so the Microsoft HoloLens can imagine it for you.

Google is rolling out an update for Google Drive that streamlines the online file storage/sharing app, and finally gives you access to the Trash folder that had only been available on the desktop version.

Welcome back my friends !! Today we'll go through the second part of this C# series

Throughout history, almost every superstition dealing with evil has had something to do with left hands. In the seventeenth century, it was thought that the Devil himself baptised his followers using his left hand. Today, studies show that left-handed people are more likely to be schizophrenic, alcoholic, delinquent, dyslexic, have Crohn's disease and ulcerative colitis, and a slew of other medical problems. To top it all off, left-handed people have an average lifespan that is 9 years shorte...

Samsung bucked the trend and threw hard keys onto the Galaxy S3 while most manufacturers are going the soft key route. This hack will add on-screen buttons to your TouchWiz-based ROM. You'll need a root file manager with a system writable text editor—I recommend ES File Explorer for this, but feel free to use whatever you want. If using ES, hit Menu, Settings, go down to Root Settings, and check Root Exploerer, Up to Root, and Mount File System.

Doorbells are useful and all, but most of them are boring as hell. They use the same old generic sounds to let you know when guests have arrived, as demonstrated below.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Say whatever you want, but Steampunk is primarily a maker culture. Consider that Steampunk has existed since the 1960s and yet more or less languished in obscurity until approximately 2005, which is when it made the leap to costuming. That costuming was what provided the leap to the tangible, despite the fact that Steampunk art had also existed for years.

The Messages app on iOS features contact photos for every one of your conversations — including group chats. Even if you don't have a picture for a specific contact, their initials will appear instead. For non-contacts, a generic profile avatar appears. These give threads a bit of flare, but if you're looking for extra privacy or don't enjoy the look, you can easily hide those images and icons.

Now that the iPhone XS is officially available for pre-order, Verizon and Apple are giving Snapchat users the opportunity to win the device through an augmented reality scavenger hunt rather than forking over $1,000 for one.

Will smartphone batteries ever last as long as we need them to? Perhaps not. That's why we rely on external batteries to help us stay connected for hours, even days, longer than usual. But in 2018, you don't want to use just any external battery. Modern Android phones have fast charging — so should your portable charger.

Less than two months since unveiling Project North Star, Leap Motion has released the reference design that will allow developers, makers, and even manufacturers to build their own augmented reality headsets based on Leap Motion's work.

Instagram is no stranger to stealing features from Snapchat. Stories, originally a Snapchat invention, feels more at home with Instagram today. Now, Instagram is attempting to repeat this feat with nametags, a way to quickly add new friends akin to Snapchat's Snapcodes.

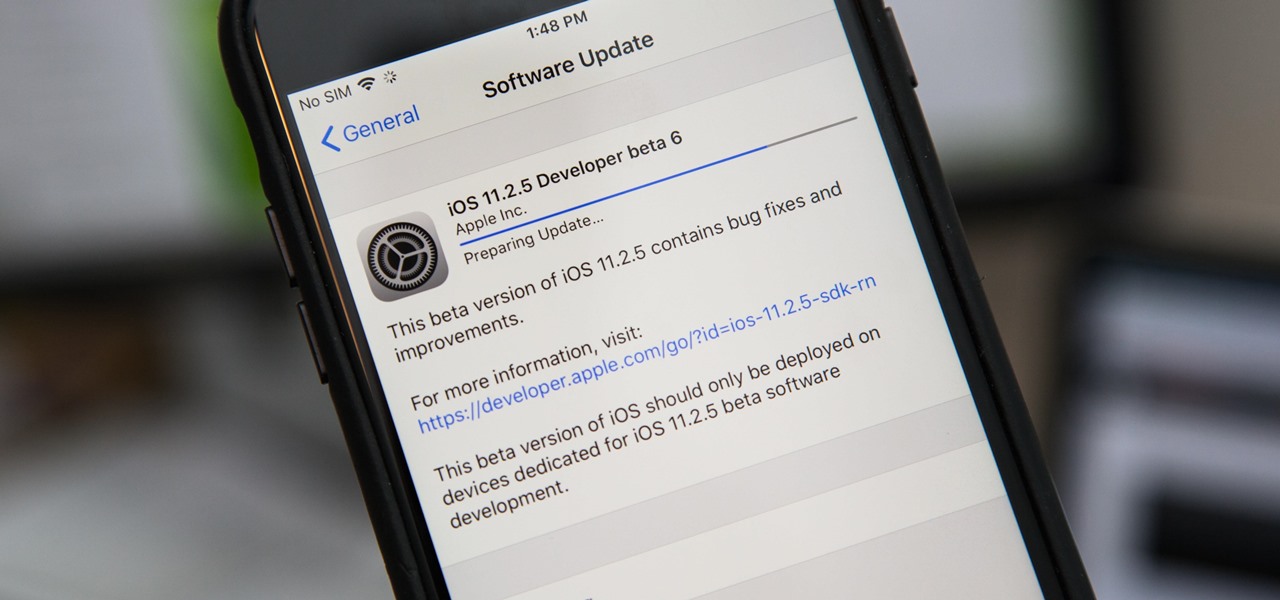
Apple pushed out iOS 11.2.5 beta 6 today for iPad, iPhone, and iPod touch to developers and public beta testers. Last week two beta updates were rolled out, and this fast pace may indicate that iOS 11.2.5 is almost ready for prime time.

While music may not technically be a "universe language," it is the one language listened to by all. There are over 1,500 music genres today—rap, classical, rock, jazz, trap, hip-hop, house, new wave, vaperwave, charred death, nintendocore... and the list goes on. And if you're like most people, you now probably listen to the majority of your music on your phone.

Snapchat has already found a compelling way to create advertisements in augmented reality with their branded filters, but they continue to experiment with new ways to monetize the bridging of the real and digital worlds. Their latest idea, which requires users to "snap" an image to unlock content, could succeed where QR codes haven't.

How do you safely store your augmented, virtual, or mixed reality headset when you're not using it? Cybust hopes you're willing to shell out $89 to display it like a sculpture around your house.