White or light-colored dinnerware is a classic: it looks crisp, clean, and elegant. The only problem is that after you've used it for a few years, the surfaces bear a lot of grey scuff marks from forks, spoons, and knives being dragged across the surface.

Deep in the crevasses of the Songshan mountain range, an Indian dhyana master established the first Shaolin Monastery in 477 AD, seeking to spread the relatively new teachings of Buddha at the time. This monastery then bred the Shaolin monks, who are now popular for their incredible feats with Chinese martial arts, particularly with Shaolin Kung Fu.

I've tried my hand in the past at defining Steampunk, but as anyone else who has made a similar attempt will tell you, there's a significant backlash from the community against working to create a real definition of what Steampunk is. That may sound ridiculous to some, but it's a very serious matter to others. With the recent announcement that TeslaCon 4 will be called the Congress of Steam, I think it's appropriate to talk about why all of this stuff is worth it. In this article, I'm going t...

There are a few significant improvements for your iPhone with the iOS 17.5 software update, released May 13, but my favorite is Apple's enhancements to the Apple News app, which is making its Puzzles section even more fun with Game Center integration and even a new type of word puzzle.

While iOS 14.3 is available to everyone right now, Apple is currently working on iOS 14.4 in its beta programs, and the second iOS 14.4 beta just came out for developers. The public beta version of iOS 14.4 beta 2 was released soon after. But what's in these new betas?

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Whether you're riding the subway on your way home from work, or stuck in the backseat of the car on a long road trip, there are times when you need to entertain yourself without a mobile data connection. A good mobile game would pass the time perfectly, but not every game works without an internet connection.

Today's smartphones and tablets offer a great way for children to learn through interactive sight, sound, and touch, but they can also provide hours of genuine fun. If you have a spare tablet laying around—or at least a nice, durable case—the only thing you need to get your child started in this world of fun and learning is a handful of good apps.

In order to make your food taste good, your favorite restaurant is most likely using way more salt than you think they are (among other pro secrets). Which is why when you ask just about any professional cook what the biggest problem with most home-cooked meals are, they almost always answer that they're "undersalted" or "underseasoned." (In cooking lingo, to "season" food means to salt it.)

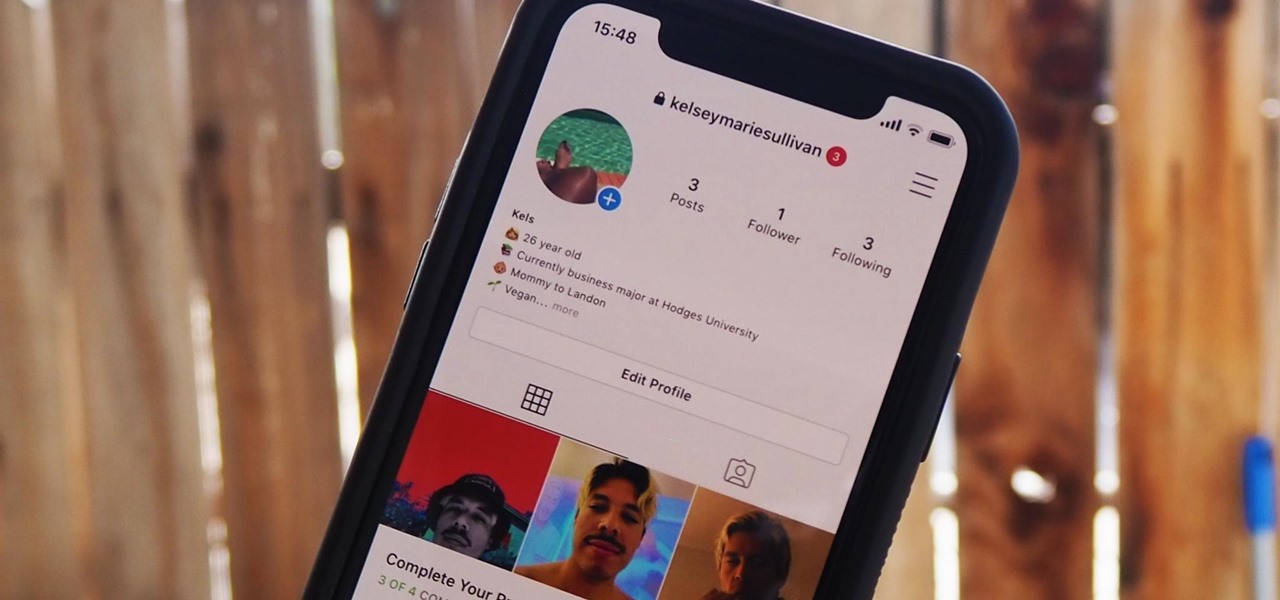
Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools make saving other people's photos and videos easy, and there are always screenshots.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Customization has always been the main draw of Android for me, but Apple has an impressive feature on iOS 16 that lets iPhone users create customized emoji wallpapers for their home and lock screens. While Android doesn't have something like that built-in by default, it's easy enough to make emoji wallpapers for your Android phone.

Buckle up, iPhone users, because it's update time! Apple just released its latest iPhone OS to the public, iOS 14.4. This new edition isn't the company's most ground-breaking, but it doesn't come up short, either — you'll find support for smaller QR codes in Camera, a new "Device Type" setting in Bluetooth, support for a new Apple Watch face, and a major privacy feature, among other new changes.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

Welcome to the first annual Next Reality 30, our list of people who've made the biggest impact on the augmented reality space in the last 12 months — and what a 12-month roller-coaster ride it's been. Apple introduced ARKit-powered apps last fall, Google launched ARCore for Android soon after, Snapchat began monetizing AR, and the Magic Leap One headset finally came out. These are historic times.

There’s nothing more special than a beautiful pearl necklace. But how do you know if they are real? Knowing some qualities that pearls have should help you determine when there is an obvious fake in your presence. It might ultimately be necessary to leave it to a professional to authenticate those pretty little presents from the sea.

Is the guy hitting on you playing or genuine? Learn to tell the difference between a player and a gentleman in this free dating video.

It's somewhat funny that the HTC ThunderBolt smartphone would be released around the same time as Apple's new Thunderbolt technology. Mainly because HTC's smartphone isn't exactly something I would compare to a flash of lightning, which averages around 60,000 miles per second. But Apple's new interconnect surely deserves the Thunderbolt designation.

There is no fan experience in professional sports quite like watching an NBA game live. Partly, this can be attributed to the combination of fluid teamwork and jaw-dropping athleticism the players exude in the form of size, speed, jumping ability, grace, and strength. What truly differentiates the NBA from the spectators' perspective, though, is the figurative nakedness of the players. While the NFL buries its athletes beneath pads and masks, the NBA presents its talent in shorts and a tank top.

PHONEYS 64 points (14 points without the bingo) Definition: to phony, i.e. alters so as to make appear genuine [v]

NK5 is a genuine wizard with an old monitor. He's hacked together everything from an electric kitty fence to a Halloween hologram using the guts of an old CRT.

This ingenious how-to is a genuine tribute to the designs of inventor Buckminster Fuller. This ice cream cone Buckyball was fabricated and filmed by New England textile artist Alyce Santoro. In stop motion, Alyce illustrates the carbon molecule, self-supporting Fullerene structure.

These are the KGB Agent Guidelines as taken from 542542.com/guidelines. kgb Guidelines

DYVOUR n pl. -S one who is bankrupt Nigel Richards played this word in his very first game in the 2010 National SCRABBLE Championship (NSC) held in Texas, which ended today. Richards won that first game against Lucas Freeman with a 462 to 392 score, but "DYVOUR" was no forewarning for Richards — not at all.

There are many opportunities to make Steampunk clothing. Clothing can be elegant and relate to the aristocrats of the 19th century. But Steampunk also can be rough and dirty, inspired by the adventurer from stories like 2000 miles under the sea or even movies like "Mad Max" or Wild "Wild West".. There are no rules how Steampunk has to look...

Sometimes there's no one around to take a picture of the entire family or group of friends. That means that one unlucky person is chosen to be the photographer and left out from the moment. Sure, you can set up a timer and run, but that's not a viable option during interactive moments. You could always edit yourself into the picture, but who has the time and proper skills to make it look genuine?

Continued from Organize Yo'sef Part One!

Last week I reviewed Kinotopic, the iPhone app that lets you easily create cinemagraphs. While I loved the result, I found the app hugely flawed. Kinotopic forced you to use a Facebook log-in, and didn't store the finished video on your phone itself. Instead, you had to visit the Kinotopic website to see your cinemagraphs or link to your Kinotopic page using Twitter, Facebook or Tumblr.

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...

Video game controllers are our windows into the soul of the machine, our sole means of interacting with them. More often than not, consumers seem displeased by their controllers; it's comforting to blame sticky, poorly laid out buttons for messing up your game than your own lacking skills. The original "fatty" Xbox controller was so large it caused mass consternation and prompted Microsoft to replace it with a smaller version in a matter of months.

Well, The Prophet Blog and Chart Rigger must be squirming in their matching trash bag onesies right now, because their stinky princess K$UX‘s new track is a proper T-U-N-E.

Google+ is nearly complete. We've got hangouts, pages, photos, games, and lots of ways to share what we love and build an audience. But it seems like Google isn't quite done yet. Since most of Google+ has been "shipped", it's now time to "ship the Google" as +Larry Page mentioned in the quarterly report.

Improve your bingo skills with a roundup of this week's Scrabble Bingo of the Days. What exactly is a bingo? It's when a player empties his or her rack in one turn, placing all seven of their letters on the board to create a word that's at least seven letters long.

It's no secret that Apple has retail stores in China, along with a large amount of Premium and Authorized Resellers. But a recent post by blogger BirdAbroad has caused quite a commotion in the world of all things Apple, claiming that in her home city of Kunming, there is another breed of Apple Store locations... "Un"Authorized ones.

Who could resist a retro SCRABBLE board game for two bucks? Suereal definitely couldn't, especially with the challenge of totally revamping a board game into something genuine and creative. Craftster's Craft Challenge #51 last June was meant to bring life back to an old board game with the following expectations:

It could be said that the World Cup really starts during the knock-out stages. What was going on for the last couple of weeks was more like the "World's Soccer Fair." At least I'd like to think of it this way after watching games like Slovenia vs. Algeria, New Zealand vs. Slovakia or Cameroon vs. Netherlands (where Cameroon had no chances at all) and Brazil vs. Portugal with both teams qualified for the next round. I'm not dismissing any of these teams, since after 4 years they all merited to...

The game has undergone many transitions over the years, since its days as LEXIKO (1931) to its briefness as CRISS CROSS WORDS to its current and amalgamated, renowned brand of SCRABBLE. There has been many editions of the word board game along that historic metamorphosis, and SCRABBLE has even given in to pop culture, sports memorabilia, and fanaticism.