
News: Industry Anxiously Awaits Trump DOT's Revisions to Driverless Guidelines
Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.


Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.

The Massachusetts Department of Public Health (DPH) issued a health alert for a Boston mumps outbreak, on Monday, June 5th, to healthcare providers and local boards of health. There have been 12 reported cases of mumps during the recent outbreak. The affected residents' symptoms occurred between March 24th and May 31st, and 10 of the 12 had symptoms after May 9th. There have been 35 confirmed cases of mumps in 2017 in Massachusetts, and "nearly 300" suspected cases in the continuing outbreak.

The problem with HIV is that it attacks and kills the very cells of the immune system that are supposed to protect us from infections — white blood cells. But a new technique, developed by scientists at The Scripps Research Institute (TSRI) in La Jolla, California, offers a distinct HIV-killing advantage.

As headlines focus on melting glaciers and rising water levels caused by global warming, climate change is quietly taking its toll on the nearly invisible occupants of this planet, the microbes.

The bacteria Klebsiella pneumoniae is a bad actor known for being antibiotic-resistant and causing a variety of serious infections in hospitals, including pneumonia, surgical site wounds, and meningitis. K. pneumoniae is something you do not want to encounter if you have a compromised immune system.

Breastfeeding is the ultimate in farm-to-table dining. It is sustenance prepared just for the baby and delivered with a very personal touch. Along with bonding, breastfeeding provides powerful protection to infants and young children in the form of beneficial bacteria, hormones, vitamins, protein, sugar, and antibodies manufactured on site to support infant health.

Devastating and deadly, land mines are a persistent threat in many areas of the world. Funding to clear regions of land mines has been decreasing, but new research may offer a less dangerous method of locating hidden, underground explosives by using glowing bacteria.

Our quest to find new antibiotics has taken a turn — a turn down the road, that is. A team of scientists from the University of Oklahoma is scooping up roadkill and searching for bacteria on them that might yield the world's next antibiotic.

Every Friday, Next Reality reviews the latest headlines from the financial side of augmented and mixed reality. This Market Reality column covers funding announcements, mergers and acquisitions, market analysis, and the like. This week's column is led by two companies cashing in on visual inputs.

There could be a fresh outbreak of the Zika virus in the Americas as the weather heats up and the mosquito population blooms.

LOOOK, a Seattle-based mixed reality and development studio, can now peer into the future with their new geotechnical engineering visualization application for Microsoft HoloLens.

For regions that experienced a boom in mouse populations last year, scientists say 2017 could see a surge in cases of Lyme disease.

Even as health authorities describe the symptoms of Zika infection in the general population as mild, a new surveillance study finds serious side effects are more common, and serious, than previously thought.

We may not fully appreciate all the important roles wheat plays in our lives until it's gone—or at least, when it's in very short supply. What would a world be like without bread, cakes, cereal, pasta, or wheat beer? If the dire warnings about an impending stem rust fungus come to pass, we may know all too soon.

In the summer of 1976, 4,000 American Legionnaires descended upon the Bellevue-Stratford Hotel in Philadelphia, Pennsylvania, for a four-day convention. Several days later, many of the attendees experienced symptoms of severe pneumonia. By the beginning of August, 22 people had died. The Centers for Disease Control and Prevention (CDC) estimate that about 180 people were sickened and 29 people died before this mysterious outbreak burnt out.

Over 1.2 million people in the US are infected with human immunodeficiency virus (HIV)—and one out of eight of them don't know it. Even after decades of intense research into the virus, there's still no cure for it. One of the big problems is that the virus hides out in certain cells of the body, resisting treatments that kill it.

A young child becomes very thirsty very often and seems tired all the time. A visit to the pediatrician determines she has type 1 diabetes. The onset of type 1 diabetes may seem sudden, and it can be, but the disease may actually have been triggered by common childhood viruses years earlier.
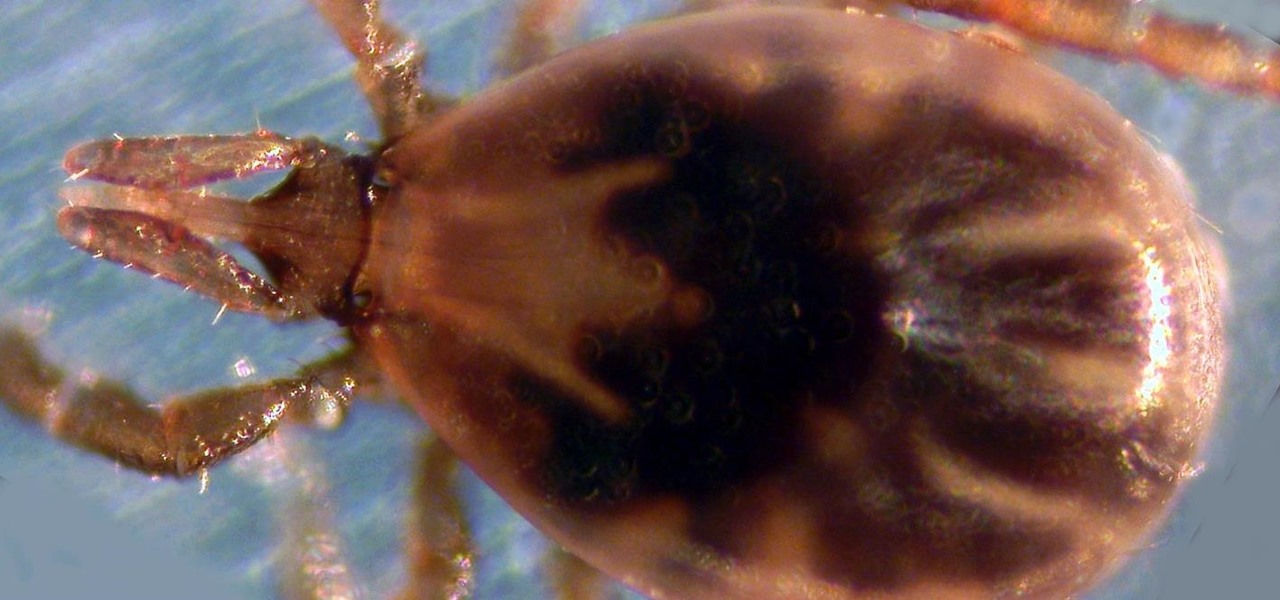
Transmitted by ticks, Lyme disease is a serious infection that is probably headed your way. A recent study confirms the pathogen that causes Lyme disease is now established in nine national parks in the East, including Acadia and Shenandoah National Parks.

If you were a particularly good little girl or boy this year, Santa might have finally brought you that cool new smartphone you've been wanting. Or perhaps you just took advantage of a great sale and treated yourself to a new gadget this holiday season—totally justifiable, and surely a well-deserved gift.

While you can't turn art into a formula, the film industry has managed to come stupidly close. While many storytelling principles still stand across mediums, successfully crafting a compelling, immersive narrative in virtual reality requires a brand new rulebook. Through trial, error, and success, writer/director/editor Adam Cosco figured out the right rules to follow (and break) in "KNIVES"—his latest 360-degree short film. The film tells an old-fashioned tale of a woman, Kelsey Frye, strugg...

Ah, the sensation of that first bite of sorbet in the heat of summertime: icy, refreshing, decadent in flavor and texture. We love sorbet almost as much as we love ice cream, and making it at home is actually pretty simple. Most recipes call for just water, sugar, and a base fruit of some sort (like strawberries or watermelon).

Whether you simply can't stand it or consider it a separate food group (or not food at all), there's no denying that Spam is everywhere. America's favorite canned mystery meat got its humble beginning in Minnesota, but is now used in dishes and found in homes around the globe.
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

On the list of problems with Android, manufacturer tinkering ranks near the top. Slow or nonexistent updates, poor performance, excessive bloatware apps—all of these things can be attributed to manufacturer skins like TouchWiz or Sense, and none of them are issues with unmodified, Vanilla Android devices like the Nexus series.

Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.

Welcome back! In our last training session we covered classes and how OOP can make programming/scripting easier. Today we'll be taking a breather and covering something fairly simple, bitwise operators.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

The digital pen on the Surface Pro 4 and Surface Book is an indispensable tool for serious note-takers and artists alike.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

There are many hacks for increasing productivity, but so many depend on tricking your own mind or behavior. When it comes to motivation in the workplace, though, sometimes the space within which you work dictates how you behave and the work you produce. So if you want to increase your ability to get more done in a single workday while doing a better job, consider changing your surroundings in the following ways.

In response to the success of Apple Pay and an attempt to stave off the appealing Samsung Pay service, Google is completely revamping Android's mobile payments system. Instead of just using Google Wallet as an app to make payments with your phone, a new service called Android Pay, with an extensive underlying framework and API, will soon make its debut—and maybe even sooner than you'd think.

When I was in college, I invited a girl over for a date. It was a glorious spring day, and I thought it would be the perfect time to fire up the unused barbecue that had been sitting on my patio all school year. I prepped all the food, chilled all the beer, and then I realized I had no way of lighting the coals for the barbecue.