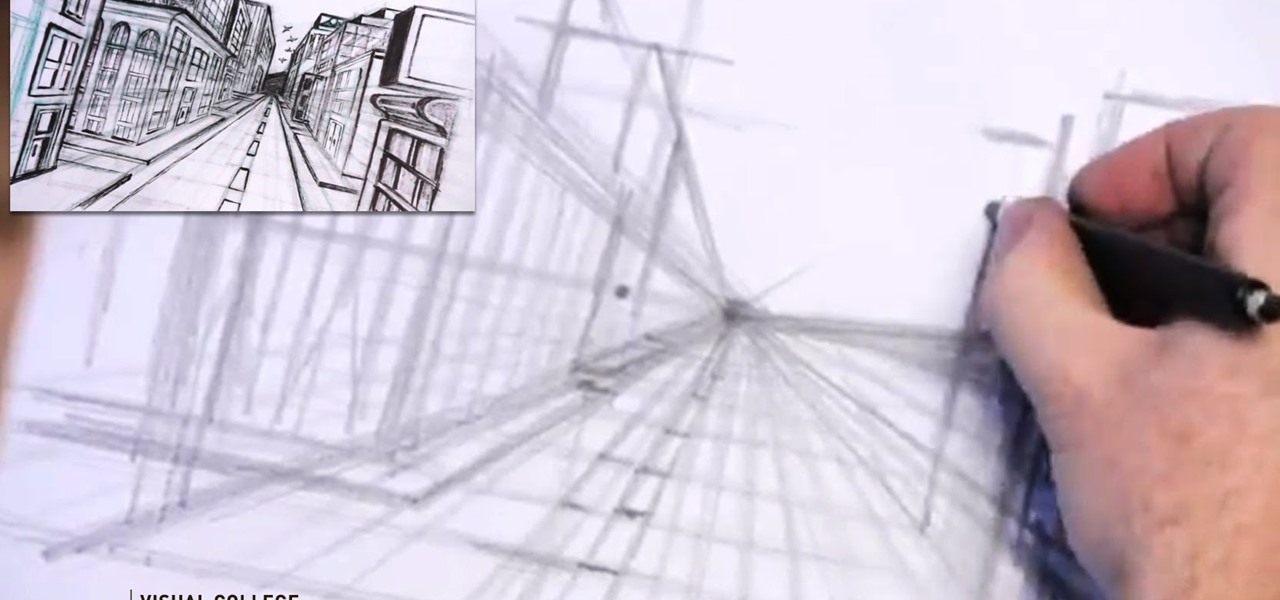
Video: . Step 1: Today We Are Going to Draw a City in One Point Perspective -- Buildings in the City Going into One Point Perspective. Let's Start Our Drawing with the Vanishing Point and Horizon Line. In Order to Get the Feel of the Drawing We Need to Determine Where Vanishing Point Will Be. Feel Free to Improvise and Change It Depending on What You Want to Achieve. Start Mapping Lines in.

I obviously do a lot of Steampunk projects, but there are a ton of things out there that I haven't tried yet. So, in an effort to broaden my horizons, I recently taught myself how to use Arduinos, which I plan to incorporate into some of my future Steampunk builds.

In this video series, you will get a glimpse of the beautiful town of Budapest, Hungary at night. Tour guide and local expert, Sarah Satmari, offers travel tips, destination ideas, and history. You will learn what do in Budapest if you are single, how to have a romantic evening, where to meet local girls and boys, how to dress, and where to eat.

There are more actions available for the Action button, but only a handful of iPhone models have that button. However, there is another button with new features you can use, and you can access all the fresh features on any iPhone model that can run iOS 18.

No, Jack Dorsey's Cash app isn't about to launch an augmented reality device (er, I don't think...), but its latest outing is about as close as we've come to full confirmation that the wearable AR age is upon us.

Two brands with affinities for augmented reality, Marvel and the NBA, joined forces to inject some AR superpowers into Monday night's matchup of the Golden State Warriors and New Orleans Pelicans.

When it comes to posting to social media from your smartphone, the process is typically the same. Find the app. Open the app. Tap the app's version of the compose button.

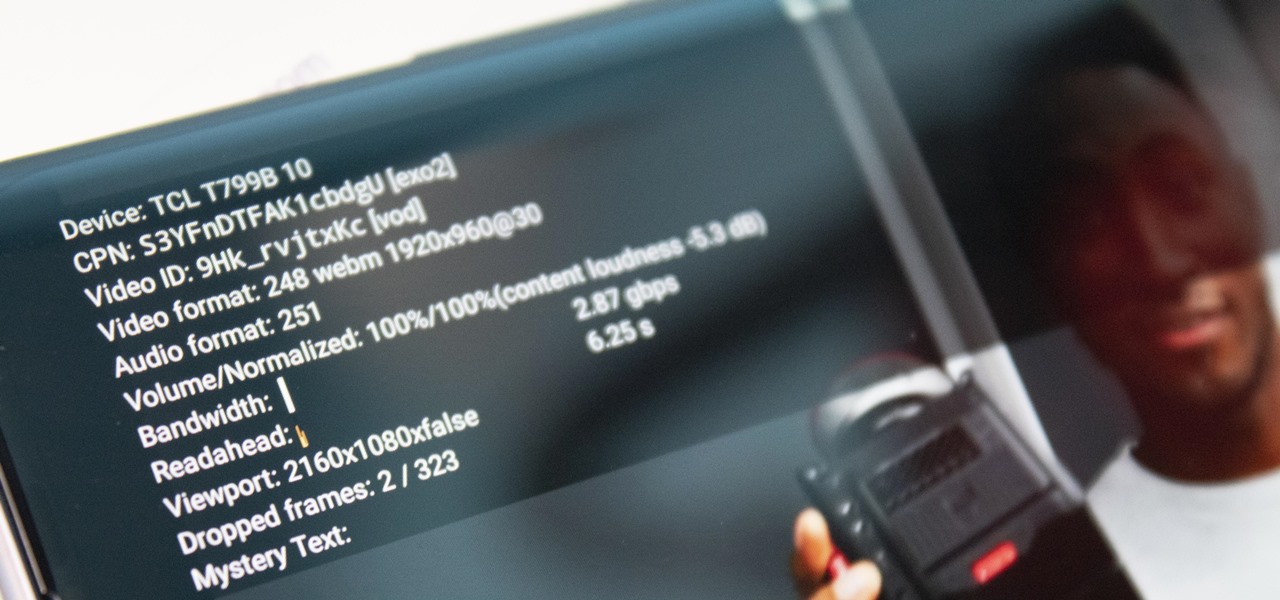
Most streaming platforms have seen a huge viewership increase in the past few months. As a result, wireless carriers and ISPs are struggling to provide the necessary bandwidth for everyone, resulting in some customers being limited to DVD quality. The same applies to YouTube, YouTube Music, and YouTube TV, but you can see the resolution being used and change it to something better.

After an Instagram creator created a viral sensation last holiday season with the Which Disney camera effect, Disney followed it up with a Sponsored Lens playing a similar roulette with programming from Hulu.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

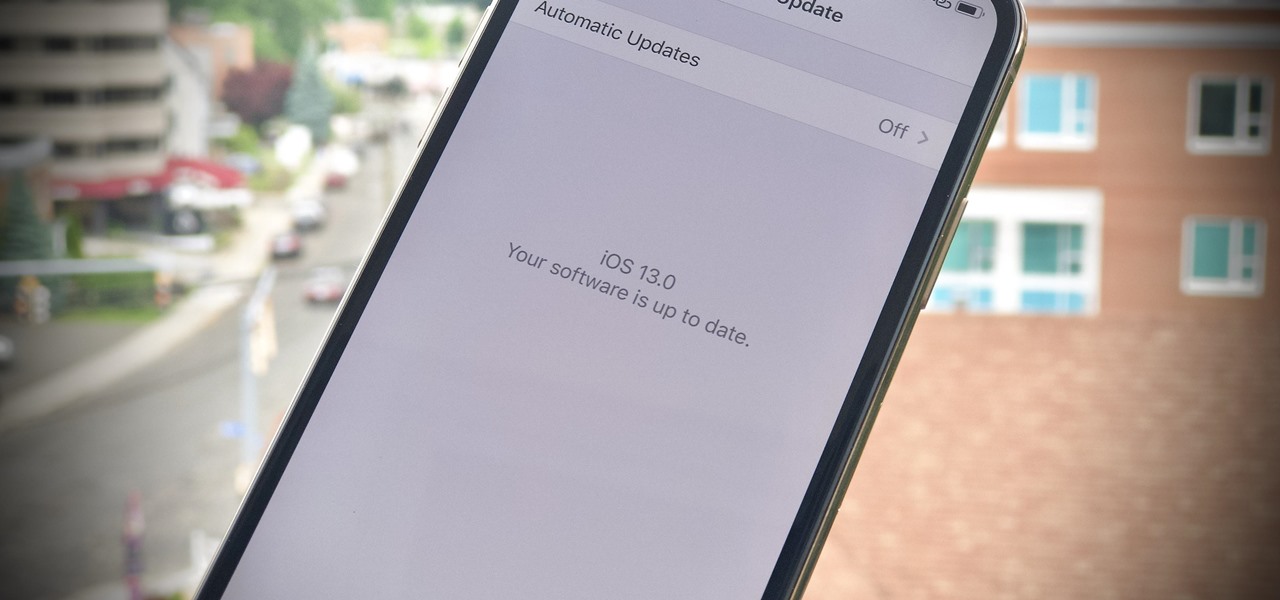
So far, iOS 13's major point updates have all been pretty exciting for iPhone. We've seen iOS 13.1, 13.2, and 13.3 come and go, offering more than 60 new features and changes combined to that very first version of iOS 13. While iOS 13.3.1 was a minor update, its successor, iOS 13.4, is a return to form.

It's safe to say that we can call the annual ranking of AR investments a holiday tradition at Next Reality.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

September is nearly here, which means new iPhones are, too. We're looking forward to iPhone 11 Pro and 11 Pro Max, as well as the more affordable iPhone 11R. All three iPhones will run iOS 13, so Apple's entrusting beta testers to ensure its new OS is ready. The latest update, developer beta 8, is now here for us to test.

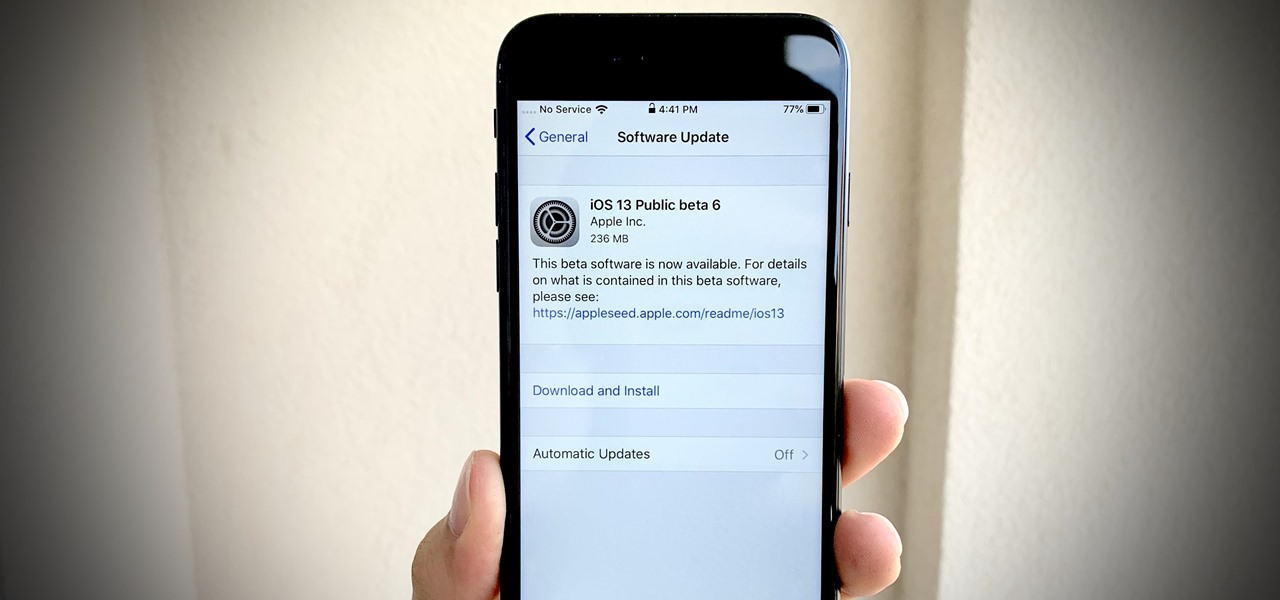
Apple dropped the sixth public beta for iOS 13 today, Aug. 15. This public update comes just hours after the release of developer beta 7, an interesting move for Apple. The company has recently stuck to a schedule of seeding the public beta at least one day after the developer beta, presumably to weed out any debilitating bugs that might have gone unnoticed.

Apple's sixth iOS 13 developer beta was a welcome update for us beta testers. New options for toggling Dark Mode, a way to hide website previews when peeking links, plus UI changes made for a significant iOS 13 upgrade. We're hoping Apple continues this trend of fun and excitement with the release of iOS 13 dev beta 7.

Life's pretty good for iOS public testers — we get to check out new iPhone features months before the general public even knows they exist. That said, we aren't first to the party. Developers get priority during beta testing, as evidenced by yesterday's iOS 13 dev beta 6 release. It's not all bad though since Apple just released the public version of that software, public beta 5, this afternoon.

If tradition holds, we're roughly one month away from Apple's big iPhone announcement. While we're excited to see what will mainly be a significant camera upgrade, it's not all about the hardware. Apple will also release the official version of iOS 13 to coincide with the iPhone XI. Before then, however, iOS 13 needs beta testing, and developer beta 6 just hit on August 7.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

Apple just seeded the fourth public beta for iOS 13 to software testers today, Tuesday, July 30. AppleSeed participants saw this beta one day early, alongside the release of developer beta 5. Now, developer and public testers alike are up-to-speed with the latest in iOS 13.

Beta testing for Apple's big upcoming iPhone update, iOS 13, is well underway. So far, each of the four beta versions we've seen brought new features and changes to the table, many of which were never even mentioned by Apple during WWDC in June. Now, it's time to do it all over again, as Apple just released the fifth developer beta for iOS 13.

The wait wasn't so long this time. Apple released public beta 3 for iOS 13 on Thursday, July 18, just one day after the release of developer beta 4. For context, Apple took five days to seed public beta 2 after releasing dev beta 3, so it's a pleasant surprise that the latest public beta dropped so soon.

We're pumped for iOS 13 and all of the fresh features and changes that come with it. Developer beta 3 came with new features in the double digits, including AR eye contact in FaceTime and mouse cursor size customization. Developer beta 4, released today, has a few more additions and changes as well.

The third developer beta for iOS 13 has been out since July 3, and while devs have had fun exploring all the new features, those of us on the public beta have sat on the sidelines running the public version of dev beta 2. But we don't need to wait any longer, as Apple just released iOS 13 public beta 2 and all the goodies that come with it.

On July 3, Apple pushed out iOS 13 developer beta 3 for iPhone, and there's a lot found hidden within. A new FaceTime setting, more Arcade details, full-page scrolling screenshots everywhere, a noise cancellation option in the Control Center, and a new markup tool — and that's just a few of the new features.

There's no doubt iOS 13 has dominated the talk around the Apple community this month. Since the announcement and release of the first developer beta, we iPhone users have had a treasure trove of new features and changes to explore and discuss. Now the fun continues with iOS 13 dev beta 2. Who's ready to start up the conversation all over again?

The first developer beta for iOS 13 is available to install on iPhone models, but the process for doing so may be a bumpy ride. Apple has not included configuration profiles for the developer beta yet, and many developers are having issues installing iOS 13 even with macOS 10.15 Catalina installed. Plus, since this is the first beta, there are a lot of problems with old and new features to work the kinks out of.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Your iPhone just went missing, and now you're panicking. You need it for work, to get around, to contact your friends and family, and pretty much everything else in your life. So, what are the chances you might get it back? The odds may be stacked against you unless it's just under a couch cushion, but you can improve your chances of recovering your iPhone by taking certain steps.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

This time last year, we got our first taste of what mobile app developers could do in augmented reality with Apple's ARKit. Most people had never heard of Animojis. Google's AR platform was still Tango. Snapchat introduced its World Lens AR experiences. Most mobile AR experiences existing in the wild were marker-based offerings from the likes of Blippar and Zappar or generic Pokémon GO knock-offs.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.