With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

If you're looking to get started with your training in web development, a natural starting point is learning to code with Python and then saving and sharing your work on Git and GitHub. These are standard tools of the industry, and mastering them will put you one big step closer to succeeding in the professional sphere.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

A cool technique on the guitar is Galloping Harmonics, combining the galloping rhythmic figure with harmonics and making it a little funky with some slap guitar, originally made famous by Regi Wooten! In this video, Jude Gold, head of GIT (Guitar Institute of Technology) at Musician's Institute completely breaks down the entire process of learning how to get the sound, the feel, and the technique down.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

In this three-part accent tutorial, learn how to speak with a Glasgowein, or Glasgow, Scottish accent. Gone over are "typical" everyday phrases such as "awrite mate!" and "watty bounce up n git a booze" in part one, while swear words are taught in part three. As the videomaker states: if you feel strongly against vulgar language, this video may not be for you.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

If you're trying to get your start in the web development and IT field, then one of the best places to begin is by building confidence with your coding by practicing Python and sharing your work on Git & Github. The Learn Python & Django Developer Bundle can help get you up to speed in Python, Django, Git & Github, and more, and right now it's on sale for $29.99.

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

Check out this instructional electric guitar video that shows you how to train your ear to play the electric guitar. This is Season 3, Episode 38 of Dave Weiner's Riff of the Week series titled "An Intro To Ear Training." Dave Weiner is a Favored Nations recording artist, a G.I.T. graduate, and has been playing in Steve Vai's band since 1999. You want to tune your ear so that you can better communicate in music better. A tuned ear will give you better chord choices, better voicings, better no...

Check out this instructional electric guitar video that teaches you about the slap and pop technique and puts it into some chordal work. The slap and pop techniques are commonly used with pull-offs and hammer-ons with the fretting (left) hand, to further increase the rate at which notes may be played. This is Season 3, Episode 35 of Dave Weiner's Riff of the Week series called "Slap & Pop Evolved with Chords." Dave Weiner is a Favored Nations recording artist, a G.I.T. graduate, and has been ...

Check out this instructional electric guitar video that teaches you about the slap and pop technique. The slap and pop techniques are commonly used with pull-offs and hammer-ons with the fretting (left) hand, to further increase the rate at which notes may be played. This is Season 3, Episode 34 of Dave Weiner's Riff of the Week series called "Slap & Pop Evolved For Guitar." Dave Weiner is a Favored Nations recording artist, a G.I.T. graduate, and has been playing in Steve Vai's band since 19...

Check out this instructional electric guitar video that shows you how to simplify complex riffs on the electric guitar. This is Season 3, Episode 26 of Dave Weiner's Riff of the Week series titled "Complex Riffs Made Easy." Dave Weiner is a Favored Nations recording artist, a G.I.T. graduate, and has been playing in Steve Vai's band since 1999. With this lesson and a bit of practice, improve your guitar playing skills by learning to simplify complex riffs and to improvise a little on the elec...

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Hi guys. Hope you all had a good Christmas , today i have a tutorial for you.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

Apps went from a novelty to the main way we control the functionality of our phones and tablets in what felt like an instant. Apps are ubiquitous, and you can find one for virtually every need. However, what's right for someone else isn't always right for you, and what's right for you might be right for more people.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

Dirty, malformed, and outright mischievous text strings have long been the enemy of interactive website developers. Strings contain any combination of letters, numbers, spaces, and punctuation, and are entered into text boxes on websites by users. These strings in particular can do everything from highlighting XSS vulnerabilities to soliciting 404 error pages.

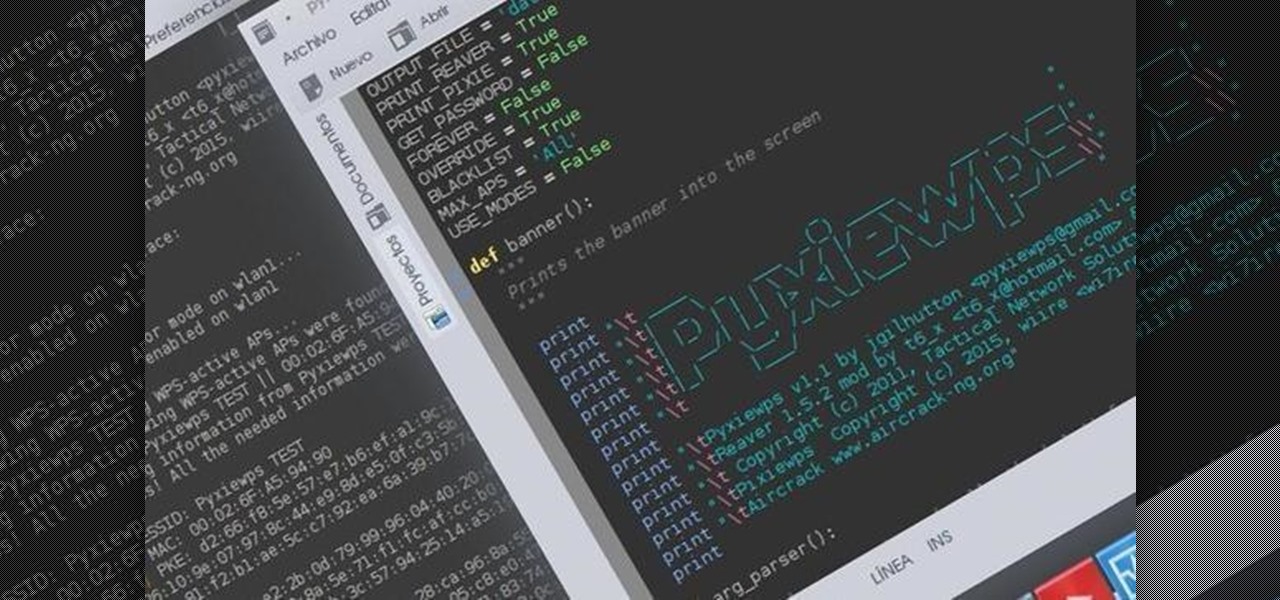
Hello dear friends! I'm jgilhutton and I want to show you guys a Python wrapper I made a few months ago.