Update 1: Evad3ers have released a statement to the jailbreak community, claiming that the safety and security of their users is the most important thing to them and that all speculations about malware being encoded into the jailbreak is simply not true. You can read the full letter over at Evasi0n's site.

Driving in your car can cause a pretty spasmodic GPS connection on your Samsung Galaxy Note 2. Making a lot of turns, speeding past large buildings, and going underneath trees and highway underpasses can all disrupt your GPS signal, making it difficult for the satellites (in the sky) to get a good lock on your location. According to them, you're in that blue circle. Somewhere. Probably.
Written news was first delivered by an elaborate courier service used by the Pharaohs nearly 4,500 years ago. About 2,300 years later, Romans would post public announcements via bulletins carved in metal or stone. Fast forward 1,600 years to the first monthly handwritten gazette published in Venice, the forefather of modern newspapers, which didn't become commonplace until the early 17th century.

Last month, Alexander Heit drifted into oncoming traffic after being distracted from the road. His sudden correction forced his vehicle to roll and flip over. He was pronounced dead at a local hospital shortly thereafter. All because of a freaking text message. He was only 22 years old.

If you've ever listened to your loved ones sing in the shower or watched a few minutes of American Idol, you would think that the majority of the population is tone deaf. In reality, only about 4 percent of the world's population suffers from tone deafness, or the inability to distinguish between different pitches. Che Guerava, Charles Darwin, and Ulysses S. Grant were all tone deaf.

With Google Maps, we can fly from Los Angeles to Tokyo to Paris and New York—all in a matter of seconds. We can zoom in with relative ease and flock around the city of our choice, checking out restaurants, historical landmarks, traffic and scuba divers. Easily the most recognizable and iconic part of Google Maps are the markers that signify all of these locations and point of interests. The iconic markers have already spurred artists to create Google Map inspired art pieces—with one such arti...

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

As Hurricane Sandy barrels towards the East Coast, 50 million people are expected to be affected in the nation's most populated corridor. The behemoth super storm is a cause for concern, evident by the massive evacuations. The picture above is an eerie snap of the mostly crowded Times Square subway station in New York. Government officials have warned over half a million people to evacuate their homes and head to higher grounds. To help prepare for this storm, the internet has provided severa...

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

You know how sometimes you accidentally send a minecart shooting out down your tracks, and you can only watch helplessly as it fades into the distance? And then you know that you have to go find it and break it, so that it doesn't stop up your cart traffic on your tracks.

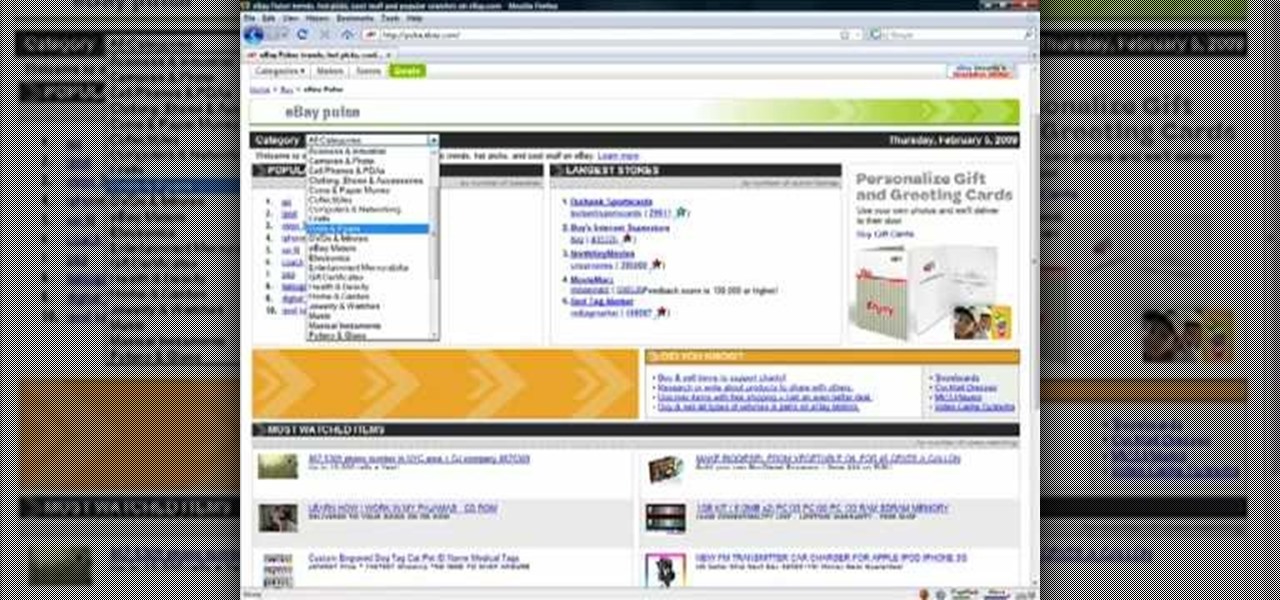
Do some niche research for your eBay affiliate site in these video tutorials, and see how to build an eBay affiliate partner site from scratch. Learn how to drill down into eBay Pulse and search for untapped niches. Finding a niche for your eBay affiliate site might seem daunting, but it's not. Also, learn about the Google Keyword tool and Wordtracker keyword tool along with a basic Google search to determine traffic levels and how easy it is to rank for a given keyword.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus and firewall software is installed.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

If you've been getting that "Please update from the iOS 12 beta" alert continuously in iOS 12 public beta 9, Apple just issued a fix for it Friday, Aug. 31, with iOS 12 public beta 10 — just in time for Labor Day weekend. This marks the second update this week as dev beta 11 and public beta 9 were released on Monday. It's also just one day after Apple announced its Sept. 12 event.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

In a surprise twist, Apple released iOS 12 public beta 8 to software testers on Thursday, Aug. 23, right alongside iOS 12 dev beta 10. The release comes as a bit of a shock, as the company released iOS 12 public beta 7 just three days earlier. The official build of iOS 12 now feels closer every day.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

Data for mapping and other applications is the lifeblood of machine-driven cars, and so far, Tesla has taken a definitive lead in information it has gathered ahead of other driverless players, including Waymo.

Hey, all you Instagram lovers, haters, or people who have no choice but to submissively bow down to the social app giant for other reasons, you've come to the right place. Today, I'm going to walk you through a very simple marketing trick to start boosting traffic to your IG account.

Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, from many different backgrounds and skill sets — and Next Reality wants to recognize them for all that they have done and are doing.

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

With the brand new SMS-based ordering service called Magic, anyone with a mobile phone can order whatever they want—really, anything—by sending causal text messages. Who says magic isn't real?

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

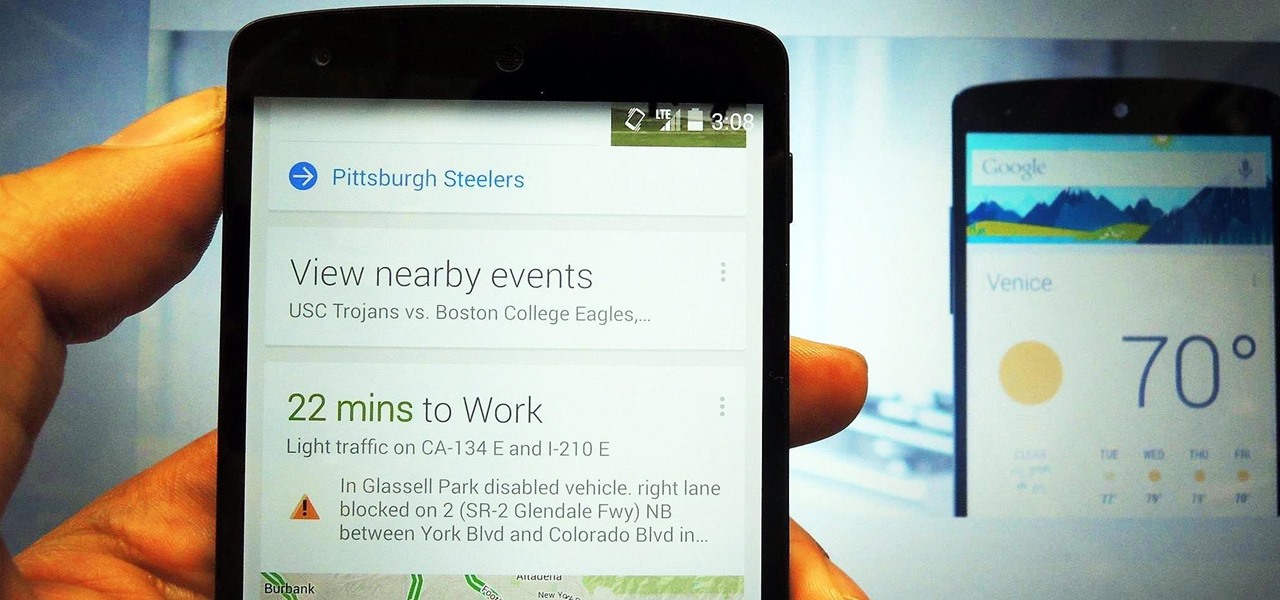
The launch of Android 4.1 Jelly Bean was also the launch of Google Now, a service that was supposed to one-up Siri, the resident personal assistant for iOS devices. Google Now offered enticing features, but its launch went unnoticed by a great many Android users.

Imagine… being able to watch television on your PC. And imagine being able to stop, pause and record those television shows. Well, in Windows 7 it's totally possible. This video shows you the possibilities of Windows Media Center.

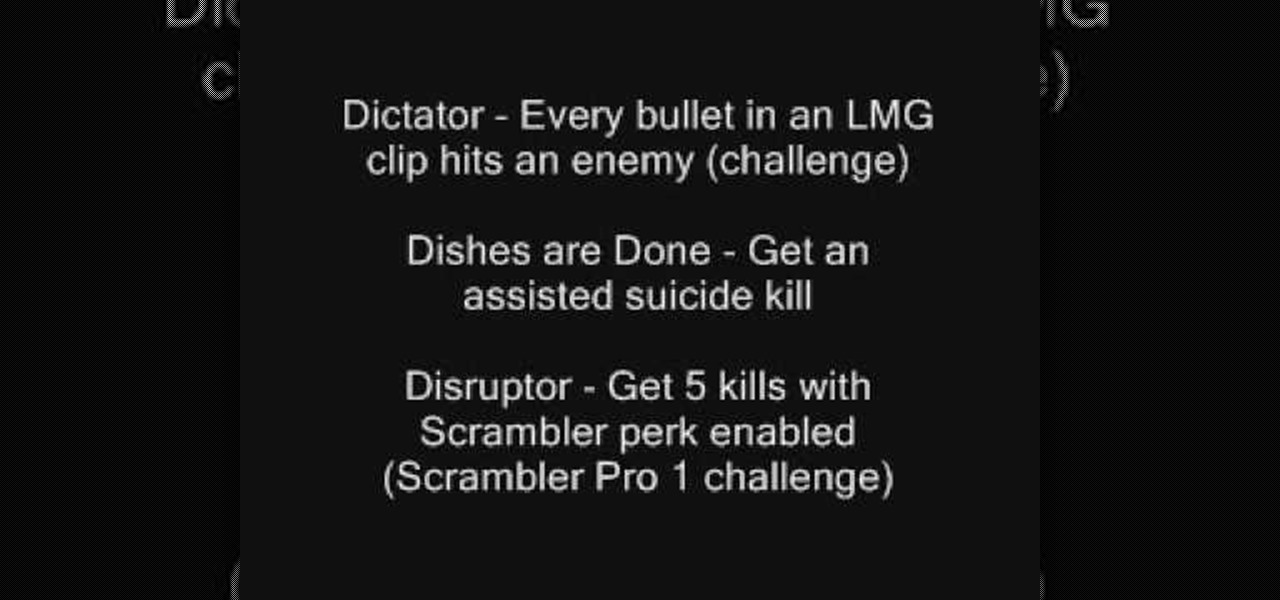
In Call of Duty: Modern Warfare 2 (COD4), there are titles that you can unlock for use on your Callsigns. If you want to know how to unlock all of the titles, this three-part video list them all and how to achieve them.

At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.

The ability to stay connected online regardless of your environment is incredibly valuable. Being able to access the internet during a blackout, check your messages while camping, or get in contact with emergency services while you're out in the middle of nowhere can be the difference between a brief inconvenience and prolonged suffering. The DuoTurbo 4G LTE Mobile Hotspot with Complimentary 9 GB Data can give you that easy, constant connectivity, and right now it's on sale for $152.99 — 10% ...

With the tagline "More Than Meets the Eye," the Transformers franchise was pretty much preordained to have its own augmented reality game, and AR gaming pioneer Niantic has stepped up to fulfill that destiny.

Data analytics is crucial to the operations of every modern business. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics. Experienced professionals that can project manage data initiatives are in high demand.

With over two billion websites floating around cyberspace — only 400 million are estimated to be active — you need every tool you can get to stand out. Great design, fonts that capture attention, and SEO placement are all necessary ingredients to success.

Data analytics is crucial to the operations of any modern business these days. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics.

One of the main goals of Google Wifi (and Nest Wifi after it) is to make managing your internet connections as simple as possible. A great example of this is how easy it is to prioritize one device and allot it more bandwidth when your network is bogged down with other traffic.