How To: Write Constructor and Destructor Functions in C
Hey everyone. Only found the site a few days ago but really loving it. Been

Hey everyone. Only found the site a few days ago but really loving it. Been

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.
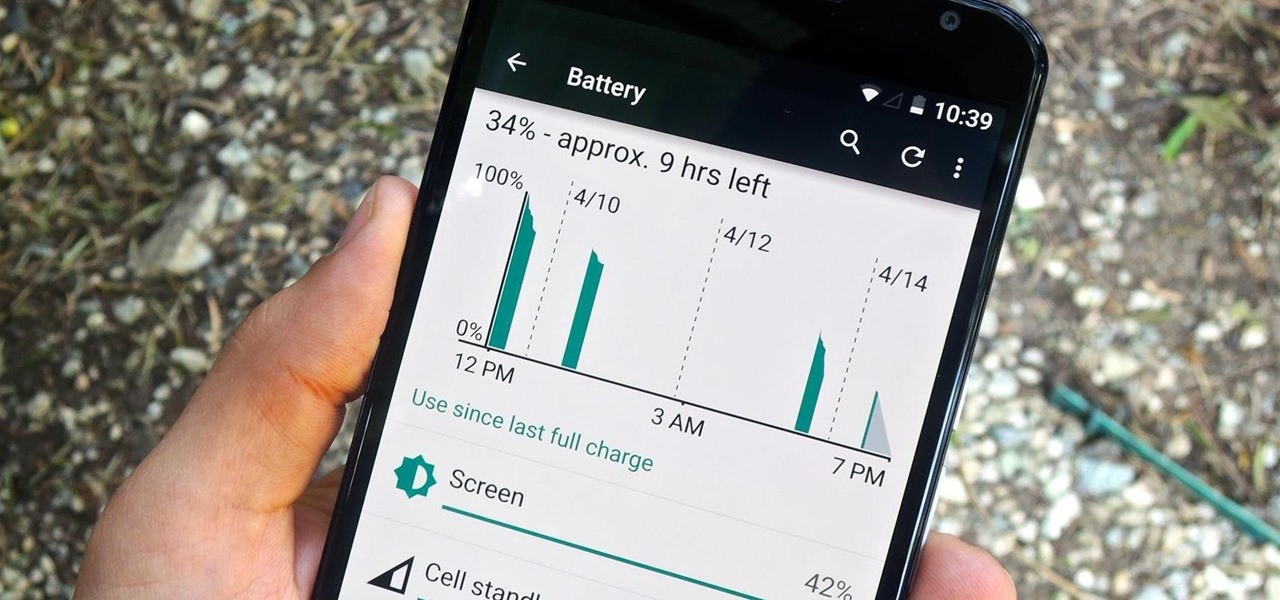
When purchasing a new phone, one of the most vital features to consider is battery life. Everyone wants to know how long they can use their device without needing to hug a wall. Increasingly, more and more manufacturers ship their devices with some variation of a "battery saving" mode, which can help combat dead-phone issues in times of dire need for battery life.
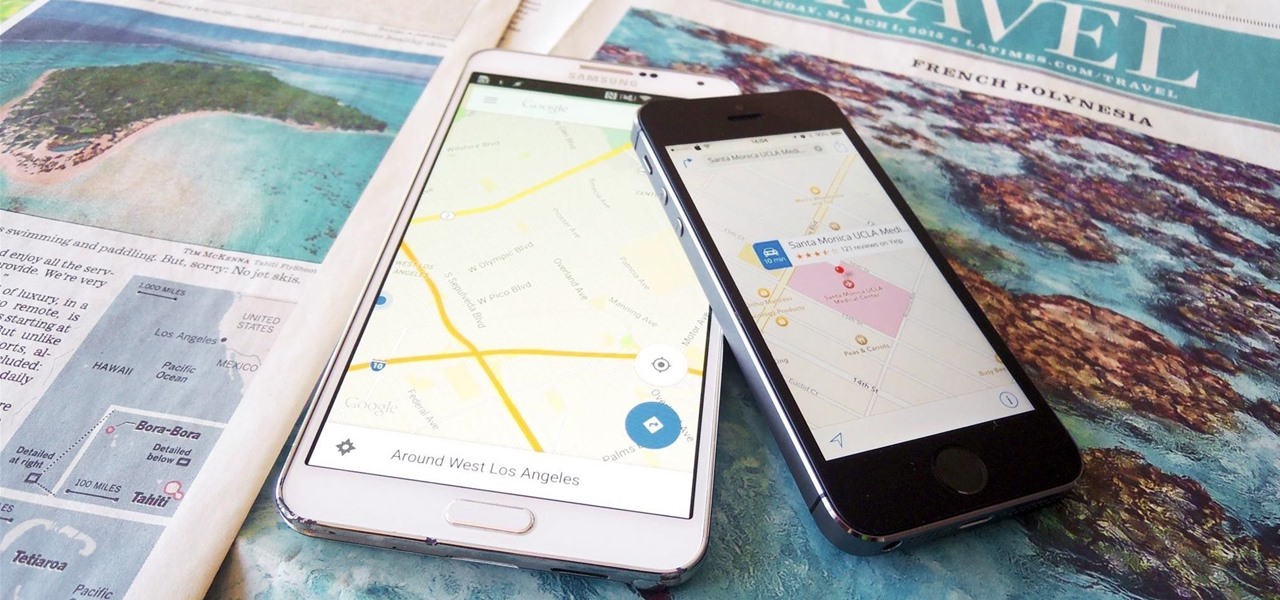
Applications like Apple Maps, Google Maps, and Waze save every location you visit or search for as a way to speed up future searches and to find commonly-frequented places. But what if you go somewhere unsavory and don't want anyone knowing?

A landmark bill finally went into action this week that will allow American cellular customers to unlock their smartphones for free. The process of unlocking may vary between mobile service providers, but you can rest assured that you are now entitled, by law, to carrier-unlock your smartphone.

At the core of your Galaxy S5's hardware lies the central processing unit, or CPU for short. Practically every piece of data, every binary bit, has to pass through your CPU before it can be used to display a video or execute a game command.

Broccoli is super. Not only is it jam-packed with nutrients like vitamin C, vitamin A, folic acid, calcium and fibre, but it's one veggie that refuses to be just a side-dish. Nobody puts broccoli in the corner.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

One thing I absolutely cannot stand is lag when I'm gaming. Every time I'm about to beat my killstreak record on Call of Duty, my internet connection drops and I'm a goner. It never fails. This usually happens because someone else on my Wi-Fi is streaming a movie or downloading a huge file.

I regularly use iTunes on my home laptop and my work desktop forty-five traffic minutes away. I'm ashamed to admit it, but until recently, I'd been saving my iTunes library on a USB and transferring it back and forth, over and over again, between the two computers.

Long-exposure photography gives us the ability the capture some pretty amazing shots by delicately capturing moving elements in an image while keeping the shutter open at a slow speed. While that's great for things like traffic, scenery, and carnival rides, it can come in especially handy for 4th of July fireworks.

After years of making do with a cheap knife, I finally bought a really good 8" chef's knife—a Henckels, although I was also eyeing a Global santoku. It quietly but literally changed my life.

Integrated rather secretively into iOS 7.1, CarPlay gives a better hands-on experience when driving, working with the car's built-in display to help you find directions, send and receive calls and text messages, control music, and more—without having to fumble around with your small iPhone.
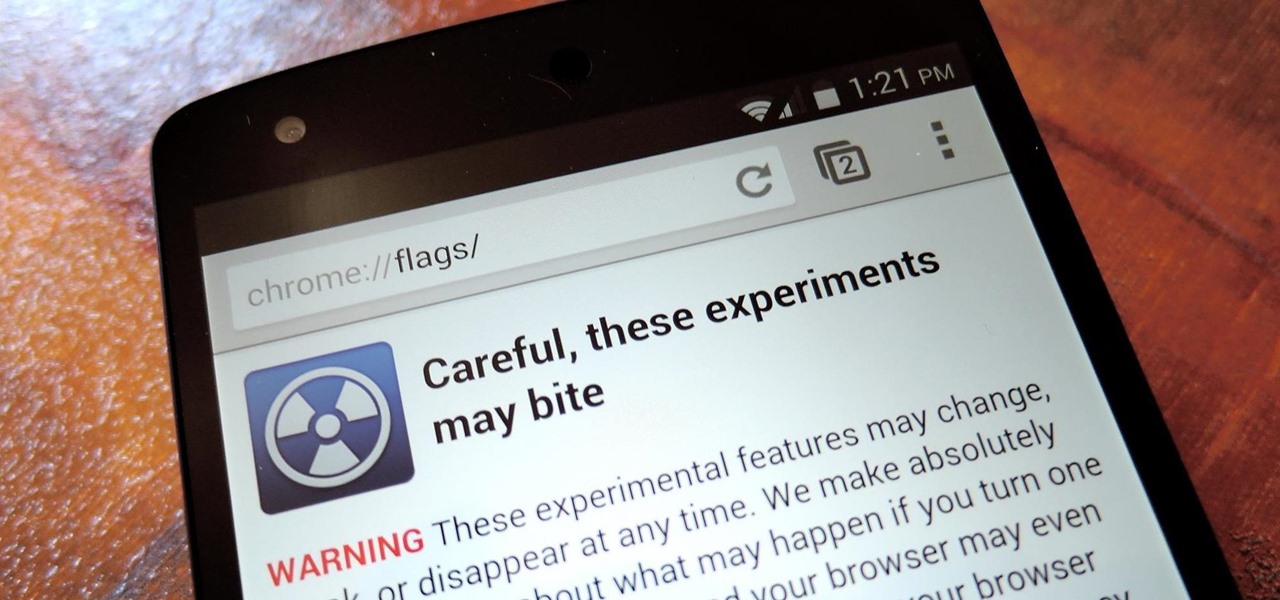
With the release of Jelly Bean, Chrome became the default web browser on Android. The wildly successful desktop browser was now fully entrenched in the world's largest mobile operating system.

As Microsoft unveiled their new Windows Phone 8.1 software update yesterday, undoubtedly the most memorable takeaway was their showcase of Cortana. Competing directly against Apple's Siri and Google's Now, Cortana is Microsoft's entry into the digital voice assistant fray, and the official replacement to their search app.

Seemingly lost in the fanfare of the numerous features and specs of the Nexus 5 were a few highly innovative and handy add-ons—a low-power step detector and step-counting sensor—useful for tracking fitness data.
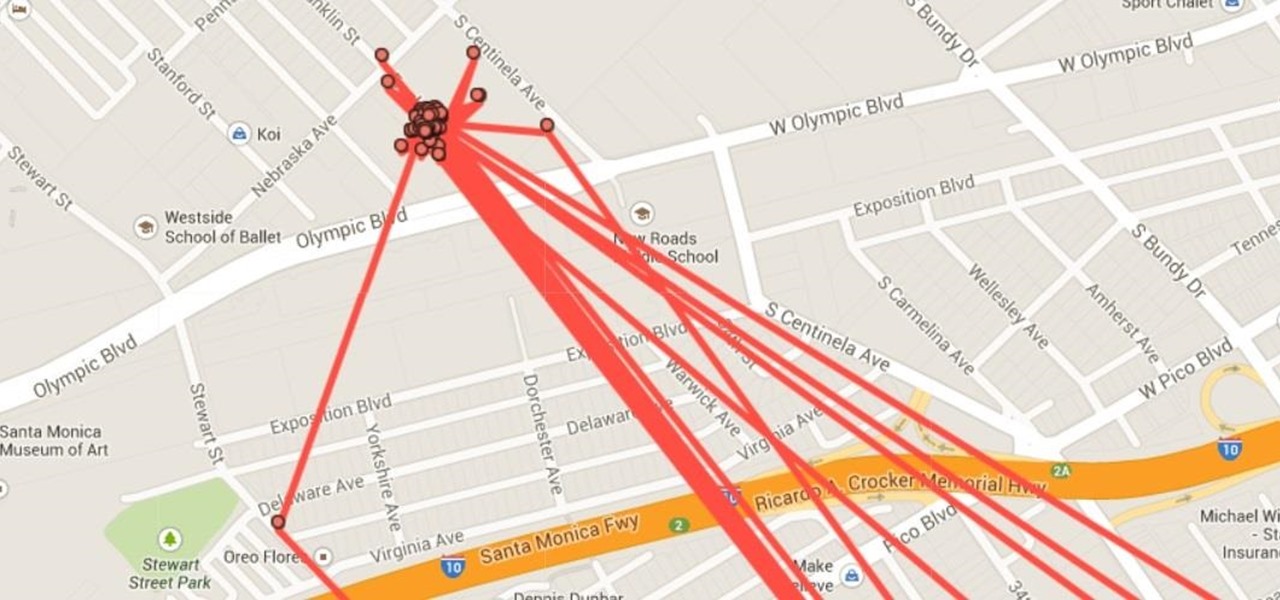
We're only years away from a complete Robot Revolution and Google Inc. will surely be leading the charge.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

Whether you like it or not, certain songs get stuck in your head. You might be driving to work or school when suddenly Cher's 1998 lead single "Believe" plays on the radio.

LEDs have slowly become the standard for DIY lighting projects because they consume less power and last way longer than regular light bulbs do. Light-emitting diodes have no filament, meaning they generate their light solely by the movement of electrons in a semiconductor material.

Walking the streets at night can be uncomfortably dangerous. In 2010, there were 32,885 motor vehicle deaths in the United States. Of those, roughly 13%, or 4,280, were pedestrians. Two-thirds of those pedestrian deaths occurred at nighttime. Along with darkness, drivers also have to deal with rain and other harsh weather conditions. Combined, all of these factors can be very dangerous for anyone taking a walk at night. As it happens, pedestrian deaths are on the rise since 2009.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

There's a cool little plugin for your WordPress blog that will help you get more traffic from people searching the web on mobile devices. It's called MobilePress. Your visibility will become greater on mobile phones and other mobile devices when activating this plugin on your blog.

Now that you know the power of the music, in this video series, learn how to use a Korg Triton Studio synthesizer to create songs and melodies of your own. Our synth expert, RT Ouk, will explain many of the basic functions in detail, including how to use the different modes on the Triton keyboard, such as the Combination Mode, the Program Mode, the Sequencer, the S. Play Mode, the Sampling Mode, and the Global Mode. Also get tips on often used buttons like Disk, Compare and Menu, which allow ...
You may not realize it, but most of your apps include third-party tracking services that monitor your activity in other apps and websites to serve highly-targeted ads to you. But now you can stop the creepy behavior on an iPhone and Android phone.

In the early days of the internet, if something was there and not password protected, you could see it. In the process of becoming the indispensable work and entertainment resource that it is, the internet also grew the same borders that countries have while also getting less safe for the people using it. If you want to watch something, you have to hope it was available in your country. If you want to keep your information safe, you have to take some extra steps to make sure that happens. The...
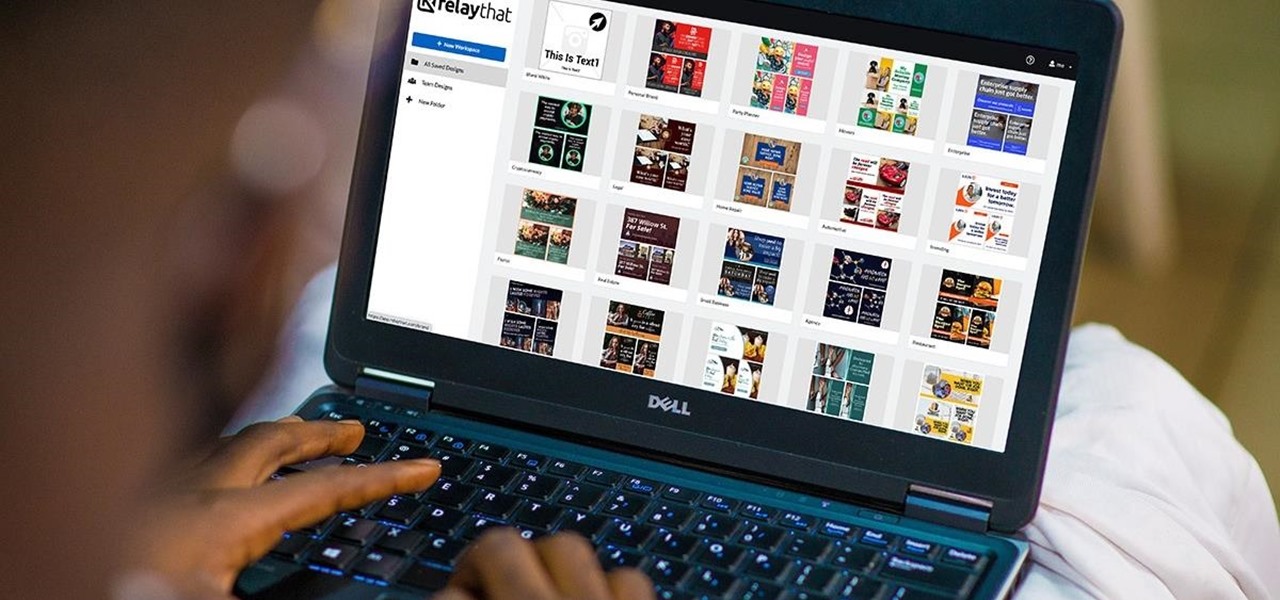
Creating high-quality marketing content for your brand is labor-intensive to the point that it could be a job of its own.
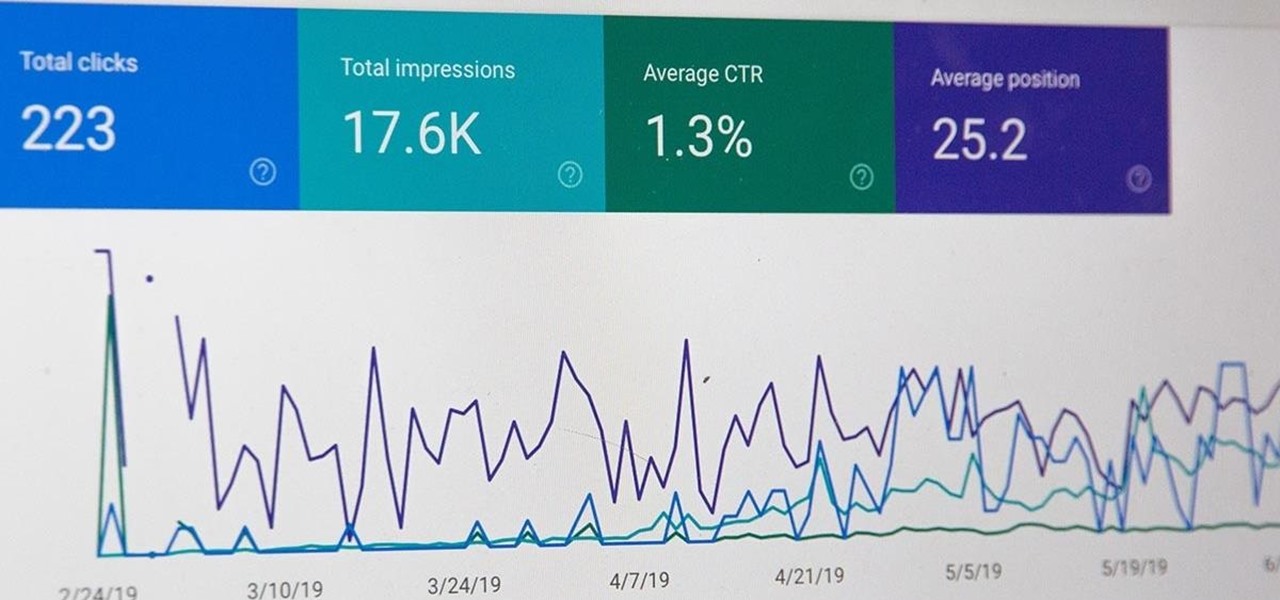
You know just how great your products and services are. Now it's time to let the rest of the world know. Of course, that's easier said than done. You're probably competing with bigger, more established brands that can afford to spend their way to the top. You can make it a fair fight with a little SEO optimization.
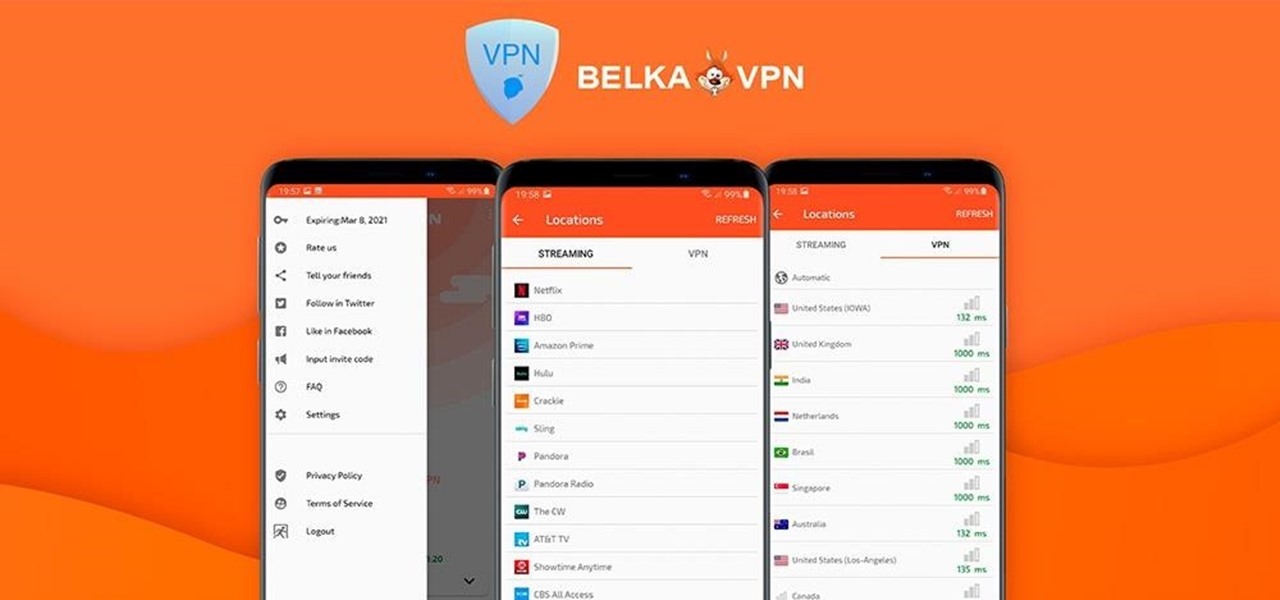
If you're concerned about your data ending up where you don't want it online, then a VPN is something you'll want to consider. A VPN can prevent your bank account information from leaking, your data from being taken directly from your device, and it doesn't come at the cost of any of the convenience we've grown to expect and require from the internet.

With everything the last year has thrown at us, the odds are good that you've had to start working from home, complete with all-new challenges both for you and the technology you use.

Want to take your productivity to the next level in the new year? Whatever industry you're in, The Complete Google Master Class Bundle will teach you the tips and tricks to become more efficient and highly skilled in its most popular apps. Right now, the entire bundle is on sale for just $39.99 — that's an amazing 97% discount off the regular price of $1,990.

The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113).

In the realm of social media, all roads lead to one destination: cracking the code of continuous partial attention dopamine hits. We learned this back in the days of Vine, before Twitter foolishly killed it. And I pointed my lens at the emerging trend back in 2016 when I highlighted Musical.ly for Mashable, just before it was snapped up by China's Bytedance for $1 billion and merged into what is now TikTok.
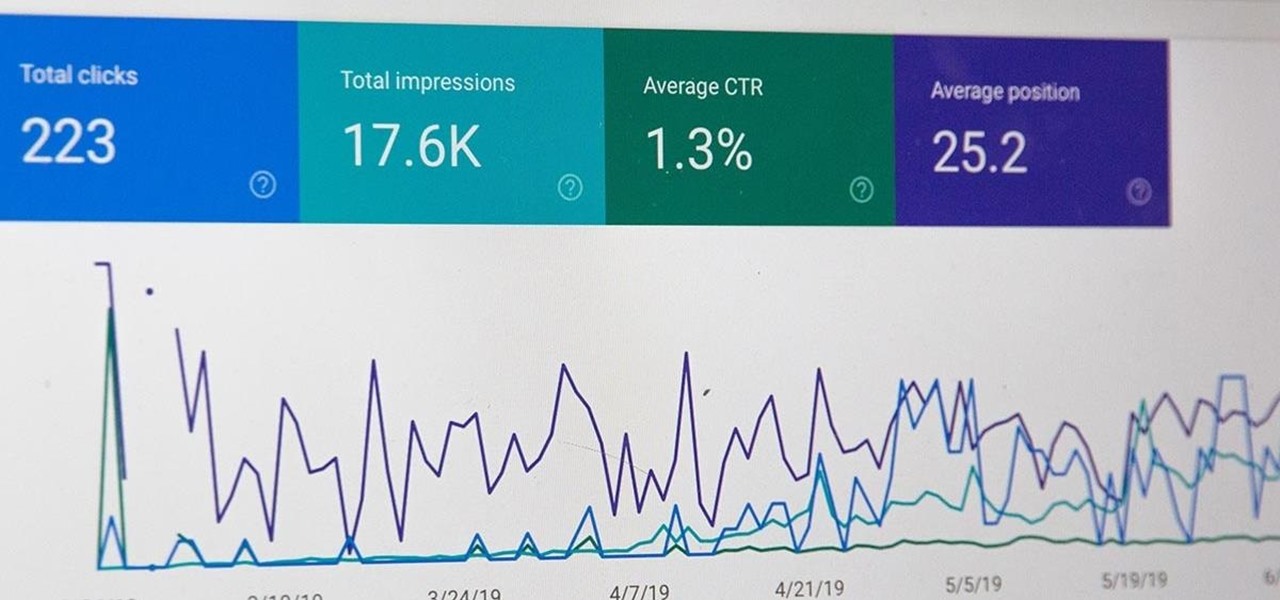
All modern entrepreneurs know that your business is as strong as its SEO. Whether you want to Rank #1 on Google to increase your personal branding, traffic to your online storefront, or to add the skills to your resume, you can now get a Complete SEO Training course for just $14.99, in the Gadget Hacks Shop, 92% off the regular cost of $199.
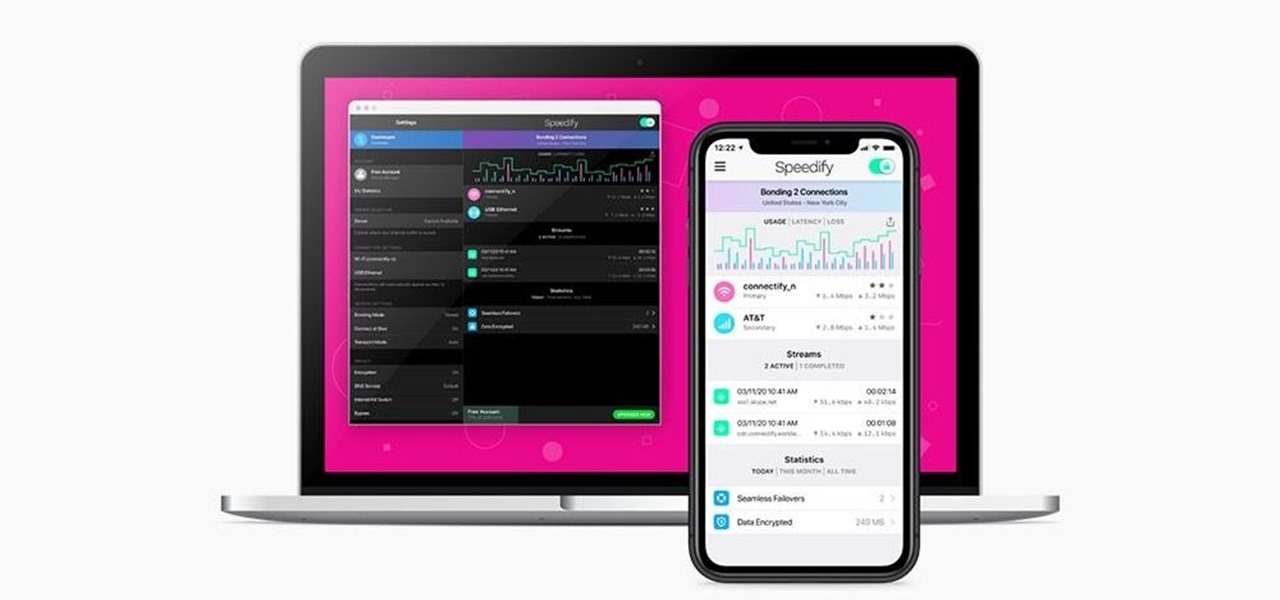
Using a virtual private network (VPN) is one of the safest ways to ensure your identity and data remain secure. Choosing one from the hundreds of services that now exist is another story. How do you tell which VPN truly provides the best protection at a great price?

If you're interested in joining the increasingly popular and lucrative world of ethical or "white hat" hacking, you're far from alone. More and more coding and programming pros are turning to this field thanks to the high pay, countless opportunities, and exciting work environment.

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

There are many considerations to make when choosing a web hosting plan. Storage space, performance, security, and reliability all matter. The cheapest option isn't always the best idea.