Audiobooks are great because they require little-to-no effort on your behalf. When driving in traffic, why not listen to George R.R. Martin's lengthy A Feast for Crows instead of repetitive, commercial-laden radio? Maybe it harks back to prepubescent bedtime readings, but having things read to me is a very satisfying experience.

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.
When the Google Maps web app got a massive redesign earlier this year, I was pretty excited to try it out, but it was a fairly disappointing update for me. The slower load times, confusing street view, and bicyclist neglect are just a few of the reasons I don't enjoy it over the old classic Google Maps. The brand new drag-and-drop measuring tool released this week is actually pretty useful, but not enough to change my mind.

Facebook will let you do pretty much anything via a text message, but unless you still have a flip phone, it's more of a novelty than actually useful.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

Facebook just released its new "home on Android" last Friday, appropriately called Facebook Home. Taking a cue from Amazon's Kindle, Home serves as an "operating system" that runs over Android.

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

Video: . Optimize your Marketing with a Mobile Website

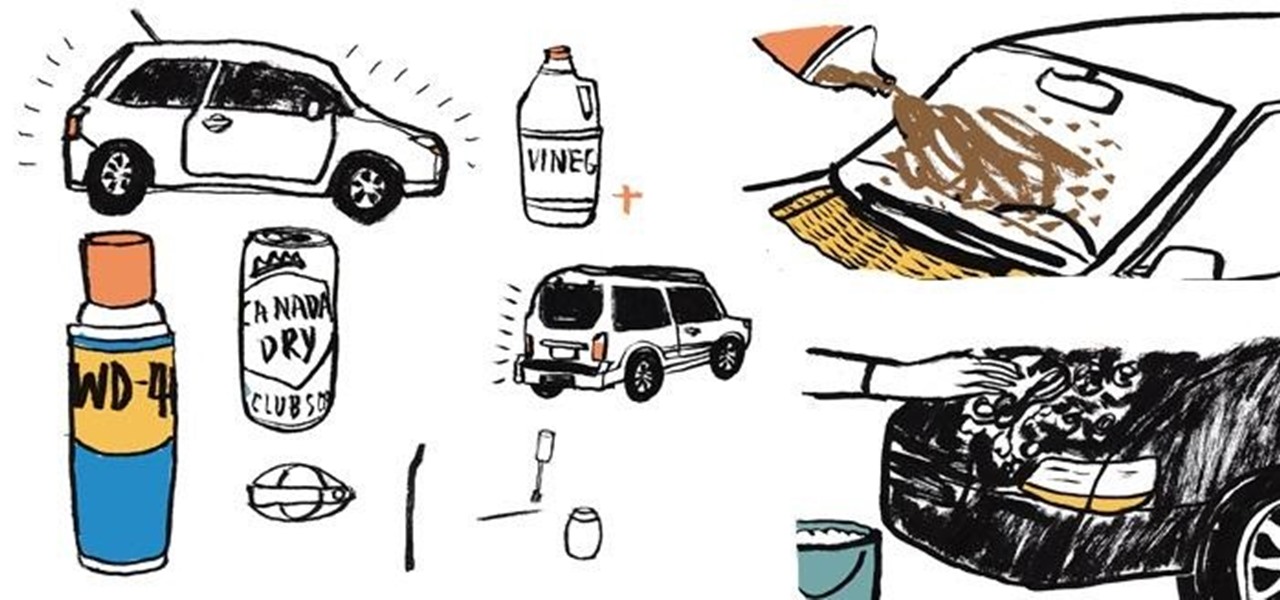
Ever see those cars so covered in dirt, dust, and grime that someone writes "Wash me" on it using their finger? Well, for those cars' sakes, as well as cases less extreme, a word of advice: procrastination is not a solution — it can only compound the problem. Self-cleaning cars are the stuff of the future, not the present, and your car needs attention now.

Caller ID is great to have, but there are certain situations where you don't want the person you're calling to have your number. People who sometimes use their personal phones for work may not want clients knowing where to reach them outside of work, and anytime you're dealing with Craigslist, it's better to be safe than sorry.

Not that long ago I wrote an article discussing what it would be like, realistically, if you were to accidentally travel back in time to the Victorian era. At the end of that article, I mentioned that the best thing you could bring with you on a time-traveling adventure is a Kindle, or similar e-reader, stuffed full of the knowledge of the 21st century. Why a Kindle? Well, I own a Kindle, and I love it. However, there's far more to it than that.

Living in Los Angeles has taught me one thing—parking is a luxury. If you are lucky enough to find street parking anywhere near your desired location, do not pass it up thinking you will get an even closer one. It does not exist. Looking for free parking? Get real. You can't even park at a busted meter in Los Angeles, despite state law saying otherwise. Now, finding a good parking spot is not just relevant for Los Angeles, but for other large cities and any other crowded areas, be it a shoppi...

It's September 1st, 1859, and the Earth looks more or less like something out of an apocalyptic movie or Sci-Fi novel. All communications have failed, it's so bright outside at midnight that people are getting up and making breakfast, and people all over the world are seeing auroras. The solar storm that produced the electromagnetic pulse and caused all this mayhem is known as the Carrington Event, and storms like it happen about about once every century.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

On Monday, the social media giant Facebook suffered a massive outage that, as of this writing, is still in effect.

Apple released the fourth beta for iOS 14.7 today, Tuesday, June 29. The update comes 15 days after iOS 14.7 beta 3, and restores battery service messages that may have disappeared after reboot on some iPhone 11 models.

A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attacks, but Xerosploit can automate high-level functions that would normally take more configuration work in Bettercap.

If you rely on Apple Maps to get around over other navigation apps, there's a lot you can do. Look Around lets you tour cities up close, restaurant reservations make dining less frustrating, and 3D view gives a new perspective of a neighborhood. While there are many more where that came from, iOS 14.5 just added six new features and changes you need to know about.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

Apple Maps has had a rough lifecycle. After completely dropping the ball during its inception, Apple has been slowly improving its usability and feature set. After six and a half years, users still prefer third-party apps in iOS 12 over Apple Maps, with Google Maps stealing a large 67% market share. But iOS 13 for iPhone may finally close the gap.

We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all completely free to play.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone are all it takes to start listening in on radio conversations happening around you.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

There's a growing sentiment around the web that when it comes to Android, stock is best. Many people prefer the clean look of Google's vision for Android, but manufacturers like LG will add features and themes on top of this base to differentiate themselves from the pack. But these OEM skins, as they're called, aren't always as overbearing as you might think.

We're all aware that Google collects a notable portion of our data. Thanks to the increasing awareness, Google has added a number of privacy controls to limit data collection. But Google doesn't just collect personal data for no reason — many of your favorite apps will use this info to improve their services and add new features.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

Nova Launcher is one of the most popular apps on the Play Store thanks to its rich features and fluid navigation. But one downside that comes with this abundance of features is that much of Nova's functionality is lost on the masses. Fortunately, I've used Nova for several years and learned a few tricks along the way.

Apple has tools built into iOS to help parents monitor the iPhone habits of their children. However, those same tools can be used by everyday iPhone owners to both hide apps they don't care about, as well as restrict features they don't need or that infringe on privacy. Whether you fit into one category or the other, all iPhone users can benefit from the "Restrictions" feature.