The launch of the Audi A8 marks the world's first Level 3 car on offer in retail channels, except there is one catch: it can only take full control of driving at speeds of 37.3 mph or less.
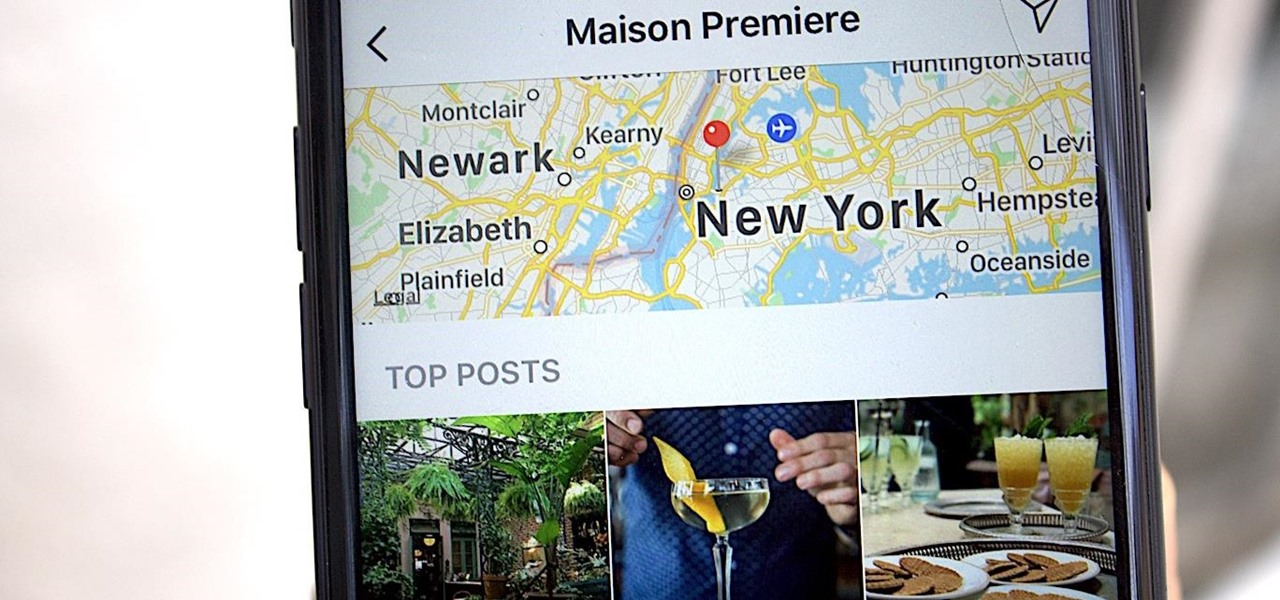
Geotagging your location on Instagram is one of the most undervalued ways to generate traffic to your profile. The beauty about adding your location to your IG posts is that it allows you to be seen by other users than the ones that already follow you.

In the driverless race, technological advances can sometimes just add more tension to an already heated competition, if Waymo suing Uber over their allegedly stolen LiDAR technology is any indication. Now, Sony is offering a new camera sensor, one that should help self-driving cars "see" the road with much more accuracy than any other camera sensors available for vehicles currently.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

If you thought the news coming from China about the coronavirus might not affect your daily life in Europe and in the Americas, think again.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

Amazon Web Services (AWS) opened its re:INVENT developers expo with a bang by launching Amazon Sumerian, a new tool that could become the dominant platform for building cross-platform augmented and virtual reality applications.

Baidu's self-driving car unit has had a tough week. Today, the company's leading artificial intelligence (AI) expert, Andrew Ng, announced in an optimistic blog post that he would be leaving the Chinese search engine company to pursue AI research on his own.

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

Tired of your PC pestering you to check this or fix that? Are you sick of all those pop-up balloons? Well, Windows 7 now has a feature called Action Center, and it lets you decide which alerts you see and which ones you don’t. See it in action!

Like driving a car during rush hour traffic or sitting unmoving at your desk, your body is not designed to sit in one position for a long time, which means that if you ride a horse you may encounter back problems.

Long-time packeteer Bob Bruninga, WB4APR, developed the Automatic Packet Reporting System (APRS), which allows packet radio to track real-time events. It deviates markedly from the usual message- and text-transfer activity. Instead, APRS concentrates on the graphic display of station and object locations and movements.

Settling a new planet will decrease your pride ratio, because your population will increase when you're settling a new planet. If you're not sure how to even settle planets...

In order to spy and gain intelligence on your Conrohl enemies, you need to make an intelligence agency. Then you recruit your spies to perform simple espionage.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to work with layers in Photoshop.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

Although not quite as common today with the always-connected world we live in, you still might be having bandwidth wars in your home right now. If the internet connection in your area is mediocre, you know the feeling well. Google Stadia recommends having a 25 Mbps connection for playing in 4K, so you can expect to need at least that much to maintain a smooth, high-quality gaming session.

Smartphone videos get better and better each year. Seven or eight years ago, who would have thought iPhone and Android phones could support 4K video recording. Some phones can even shoot slow-motion at 960 fps. But no matter the resolution or frame rate, a phone's rolling shutter can make quick movements in front of the camera appear wobbly, distorted, or with artifacts.

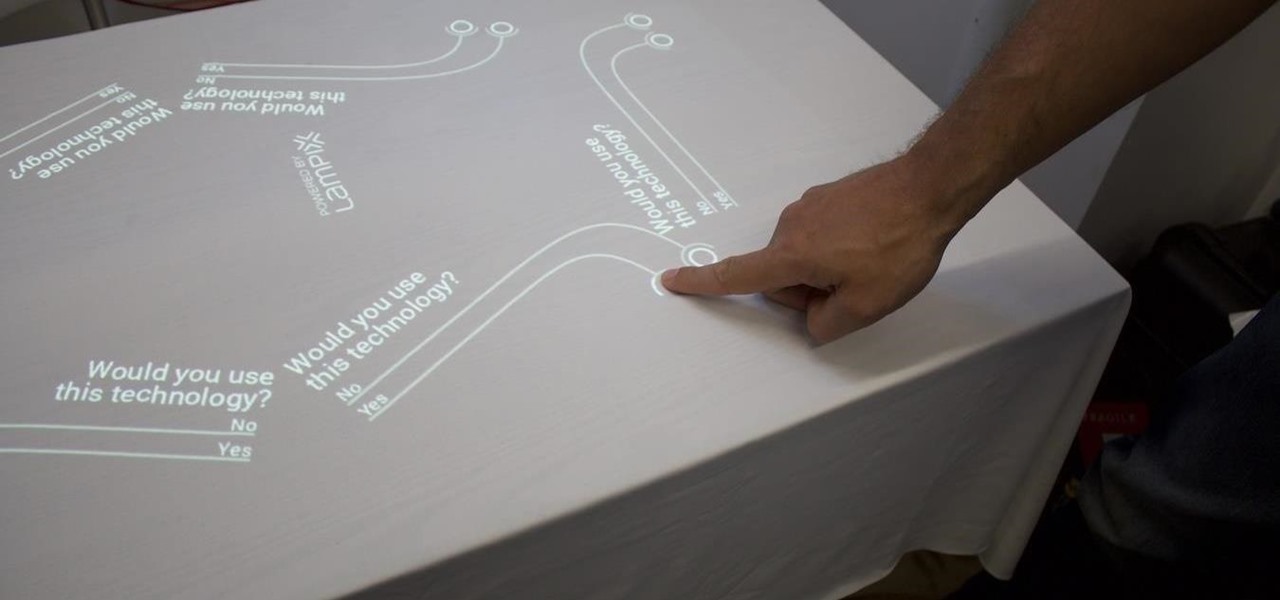
Over the past week, companies took a variety of approaches to investing in augmented reality. Lampix is backing its own effort to build an ecosystem for augmented reality platforms. Nokia and Xiaomi are teaming up on numerous fronts, potentially including augmented reality.

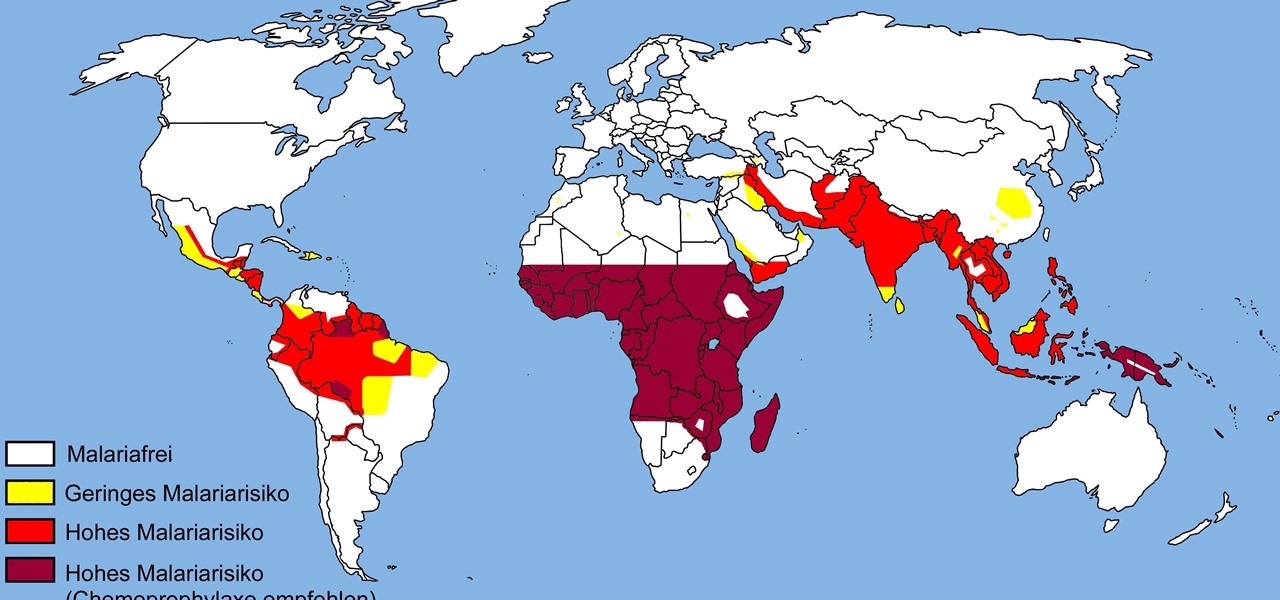
The theme for 2017's World Malaria Day, which is today, April 25, is "End Malaria for Good." For many Americans, this might seem like an odd plea. Especially since Malaria is seemingly an obsolete problem here. However, on World Malaria Day, it's important to remember the danger of malaria is still very much present in the US. And around the world, the disease is at the epicenter of a global crisis.

In Bhopal, India, a place nestled in between the royally pink city of Jaipur and the dry (i.e., alcohol forbidden) state of Gujarat, is a team of developers determined to make a fully driverless car suitable to the complexities of Indian traffic. An algorithm elaborate enough has yet to be made by any other company, but is the fundamental key to handling the intuitive habits of Indian drivers, the often intense and gridlocked traffic, and the country's vast expanse of jarring roads.

Long before Apple and Android became household names, Nokia dominated the mobile industry. The Finnish company was one of the first to develop smartphones, and their classic N95 with 2G "high-speed" internet connectivity was declared the "best smartphone ever" by some in 2007. Outside of the US, before the iPhone became all the rage, owning a Nokia phone was a status symbol akin to wearing a Rolex or Omega watch.

Whether you simply can't stand it or consider it a separate food group (or not food at all), there's no denying that Spam is everywhere. America's favorite canned mystery meat got its humble beginning in Minnesota, but is now used in dishes and found in homes around the globe.

Welcome back, my nascent hackers!

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

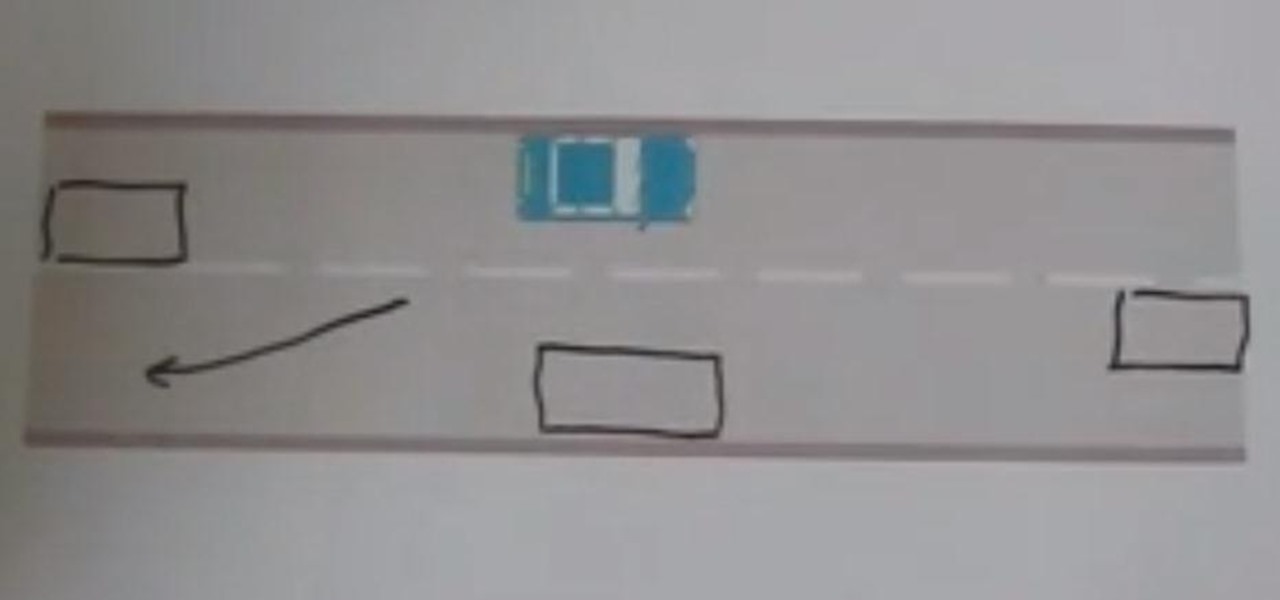
Here is a video all about meeting other vehicles when you're having lessons with driving instructors in Nottingham and the surrounding area. It happens when you are passing parked cars and someone is coming the other way.

With a little bit of planning, you can avoid a lot of blood-pressure-raising traffic messes. You Will Need

Learn how to clean a cassette player. Cassette players may be outdated, but if you've still got tapes, you're going to want to keep them in good condition.

In this video tutorial, Chris Pels shows how to use the ASP.NET IIS Registration Tool to configure ASP.NET. First, see how file extensions are mapped to ASP.NET in the IIS Manager on a global and web-site-by-web site basis. These script maps provide the basis for configuring individual ASP.NET applications to run under a specific version of the .NET Framework. Next, see how aspnet_regiis.exe, the IIS Registration Tool command line utility, is specific to each version of the .NET Framework and...

With the global COVID-19 pandemic preventing Pokémon GO players from venturing into the real world, developer Niantic has adapted the game for trainers to play in a socially-distanced manner.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

For the most part, Google Wifi and Nest Wifi systems take care of themselves. But there are still a few manual features that might come in handy, like being able to check on network activity to see which devices are using the most bandwidth when your connection gets bogged down.

One of the hallmarks of augmented reality's coming of age is that the technology is starting to find a home in business categories that are less obvious compared to typical AR enterprise use cases.

With the consumer edition of its Nreal Light headset, scheduled to ship in 2020, Nreal is prepared to bring the entire Android app ecosystem into augmented reality.