A Seattle development team is putting the "ARRRR" in AR with the maiden voyage of Captain Blimey, an augmented reality game for iOS and Android devices that puts a pirate premise on Pokémon GO.

Any parent with a rambunctious child who may have at one point racked up a hefty bill on their Kindle or Android device can now breathe a sigh of relief. One, Jack Black has had it happen to him too, and two, Amazon will be refunding up to $70 million of in-app purchases made by children after downloading apps from the Amazon AppStore.

Since the 1960s, bacteria have been hopping a ride into space on space vehicles and astronauts, and have been cultivated within experiments on space shuttles and the International Space Station (ISS). The extreme growing conditions and the low gravity environment on the Earth-orbiting vehicles offers a stable research platform for looking at bacteria in a different light.

Forget headphone jacks and "Courage." Look past the shiny Jet Black finish and beyond the minimized antenna lines. Sure, quad-LED flash and dual cameras are nice—but dual-SIM would've been much better.

GIFs are awesome, but GIFing from your keyboard is some next-level stuff, and Apple knows this. That's why they've included a way to find and send GIFs in Messages from the stock iOS 10 keyboard. However, iOS 10 is not out for the public just yet, so if you want to easily send GIFs in your messages, you'll have to settle for a third-party keyboard.

You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true.

It seems like Microsoft has finally come to the realization that their Windows Phone mobile operating system is probably never going to compete in today's smartphone market. Why do I say that, you ask? Because they've recently started to embrace the more popular platforms by releasing some quality iOS and Android apps.

Over the course of the past century or so, media consumption has gone from a few readers enjoying their local print publication to billions of users viewing countless hours of video across the globe each day. This was a gradual evolution at first, but recent advancements in mobile connectivity have sent us into a climb the likes of which we have never seen before.

This is a quick and easy method for receiving the backend IP (1) of a server who is hidden behind a proxy (2) or a firewall (3).
Hello I have now asked for help a few times, so I figured I should contribute with what I can offer as of right now, which is many valuable sites if you need to look someone up.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

Yes, emojis are the [insert poop emoji here]. They can help improve your love life and even let you portray emotions in a more diverse and well-rounded way now. But combining emojis with GIFs? Well, that's some next-level [insert poop emoji here] right there, and with a new iOS keyboard from Puppy Ventures, that next level is finally here.

Video: . I made this Tesla Coil using the myRIO and LabVIEW. It uses electricity to play the music, which can be Star Wars, Harry Potter or even Hunger Games! The music is played by the spark heating the surrounding air (causing it to expand) then the spark turning off (causing the air to cool and contract). This expanding and contracting cause's longitudinal waves - or sound waves.

The next time you finish that last pickle spear, don't pour the leftover green juice down the drain. You can use your leftover pickle juice in cooking, in cocktails, and as a post-workout performance shot.

Coffee is one of the world's most popular drinks, and its fans are also usually devoted to a certain method of brewing. Some love the Keurig, others the French press, and still others swear by cold brewing. However, one of the oldest and easiest ways to brew coffee is also one of the best. If you love coffee, you should really think about getting a Turkish ibrik (also known as a cezve).

You wouldn't send your GPS coordinates to a completely random stranger just because he or she asked you for it, right? So why are you constantly sharing your location (and other data) to apps on a daily basis?

As soon as third-party keyboard compatibility was announced for iOS 8, Apple loyalists and the newly curious both looked to the popular Android third-party keyboard developer, SwiftKey, to see if they'd be offering their services to iOS.

Not too long after getting a new device, you probably start installing any and all apps that seem fun and interesting. But after having used the device for a considerable period of time, those extraneous apps begin to take their toll.

Rather than just use the stock Apple keyboard, iOS 8 now lets you use keyboards from TouchPal, Fleksy, SwiftKey, Swype, and more. I'll be showing you how to set up a third-party keyboard on your iPad, iPhone, or iPod touch, as well as giving you a firsthand look at TouchPal's keyboard for iOS 8.

Automated tattoos are now a reality, with 3D printers being hacked into tattoo machines. Multiple people have posted videos of their 3D printer that can "print" tattoos, with one of the more impressive ones shown in the two videos below.

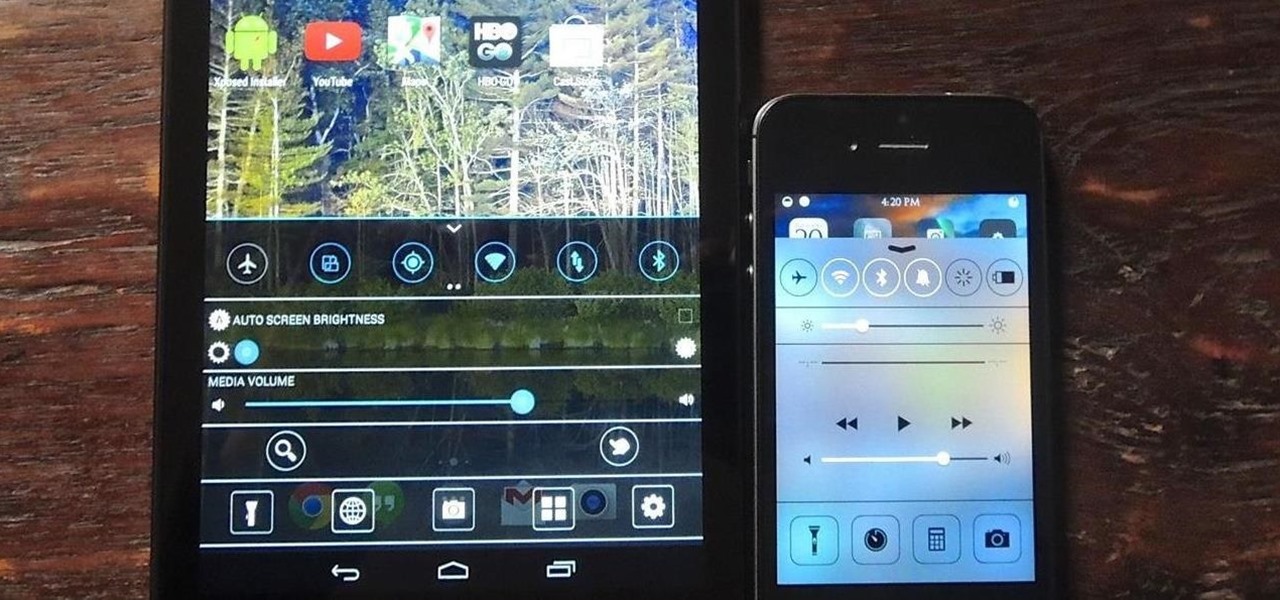
There are two types of tablet users in the world—those who like their quick settings up top, and those who want them on the bottom. I fall into the latter category, and there are a couple of reasons for it.

The Xperia Z1, Sony's flagship device, has been extremely popular overseas, so much so that it has made its way into the U.S. market as the Xperia Z1S, a modified version of the original. Known more commonly as the "waterproof smartphone," the Xperia Z1 packs one of the most powerful cameras on the market, with an impressive 20.7 megapixels. Since the device is only available for T-Mobile here in the States, unless you currently have that carrier, the chances of you getting your hands on Sony...

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

In most countries, there is one single emergency telephone number that allows you to contact local emergency services when in need of assistance. In the United States, that number is 911, which most of us know by the time we're able to speak, unless you're Buckwheat and Porky.

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

If you want to start the party out right, you have to impress the crowd with your awesome bartending skills. While lighting cocktails on fire is a nice way to warm up the crowd, it's been done by thousands of bartenders across the globe. Plus, if you're not careful, you could end up like this guy:

Until recently, brainwave-reading devices have pretty much only existed in science fiction. Sure, electroencephalography (EEG), the technology that powers these devices, has been used in medicine and psychiatry since the late 1800s, but diagnosing people's brains and reading their minds are two totally different things. The first EEG headsets available to the public were used mostly in gaming and even in fashion, but in the last few years, they've gotten a little more sophisticated.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and physical barriers to delineate their cultures.

In this video you will see how to select from the various web hosting options to host a domain at GoDaddy.

In this video you will see how to use FTP client to move files to GoDaddy.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

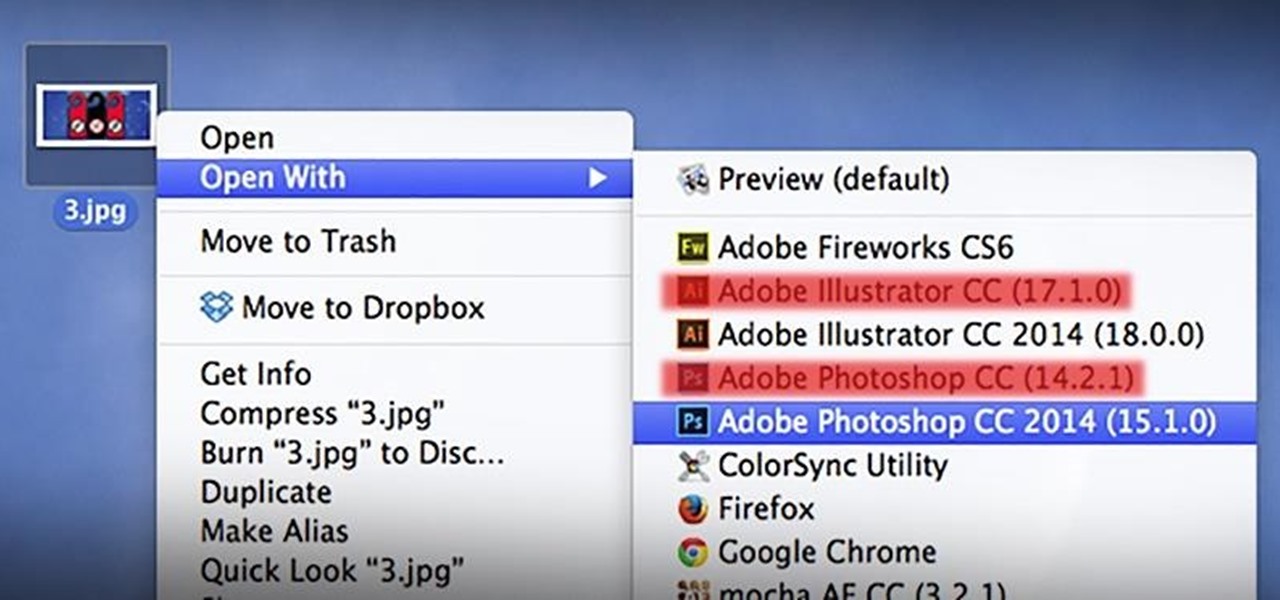
As a regular Mac OS X user, I have a love/hate relationship with the "Open With" contextual menu. Sometimes, it has just what I need. Other times, it's often packed with unnecessary or duplicate items, or missing the app I want to open the file up with the most.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

How to use XAMPP to set up a .com domain name for yourself.