You love your bike and it was stolen. Although, this is not a good scenario, you still may be able to retrieve it. Sketch the serial number or means of identification into the bike and then when it is stolen you can really get the word out to all the places that it might turn up.

With NFTs taking the art world by storm, it's a bit refreshing to know that you can enjoy world famous masterpieces in the comfort of your own home via augmented reality without emptying your cryptocurrency wallet.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.
Apple seeded public testers the second beta for iOS 13.3 eight days ago. That update mainly added stability patches to iOS as a whole, as did the public releases of iOS 13.2.2 and iOS 13.2.3. Now, following the release of iOS 13.3 developer beta 3 earlier today, Apple seeded the same beta to public testers.
Just two days ago, on Nov. 18, Apple released iOS 13.2.3 to the general public, which included stability updates for bugs affecting iOS 13.2 and earlier. Today's update isn't for the general public, however. Instead, Apple just pushed out iOS 13.3 developer beta 3 for software testers.

Halloween is barely in the rearview mirror, but Coca-Cola is ready to bypass Thanksgiving altogether to accelerate the arrival of Christmas, and the brand has enlisted augmented reality as an accomplice.

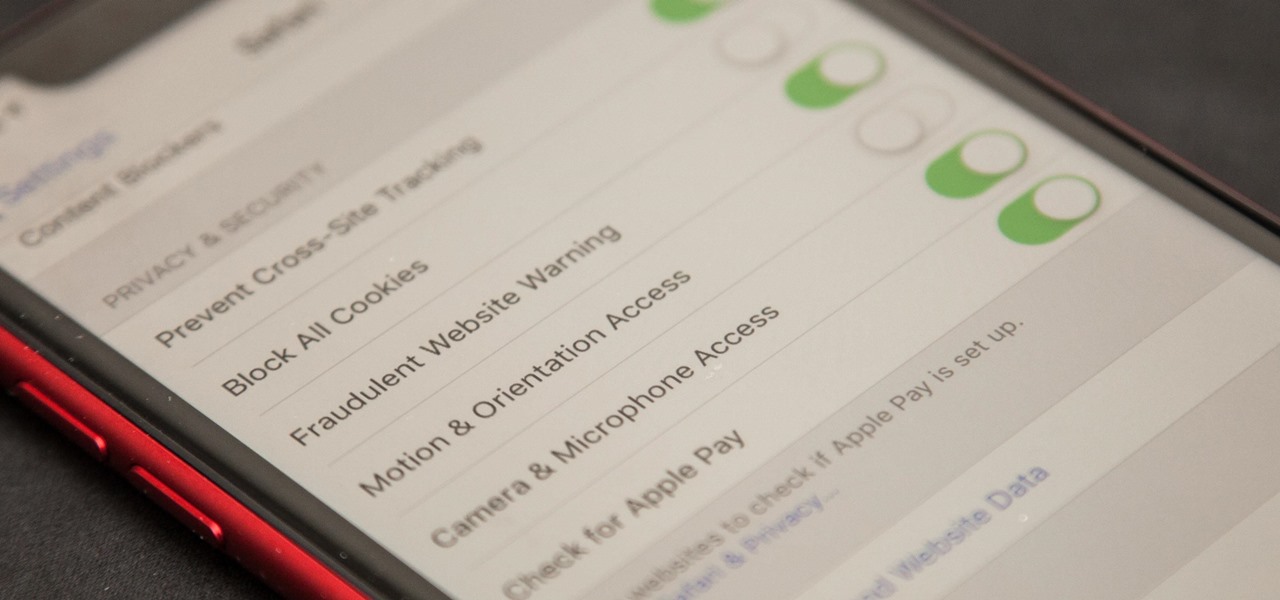
Apple first added the "Do Not Track" option to Safari in iOS 7, which sent a request to site owners and advertisers to not track your browsing activity. By tracking your activity, those third-parties could tailor content to you that you're more likely to interact with. While the feature was always opt-in, it's no longer a feature at all in iOS 12.2 on your iPhone.

After entering the UK's version of bankruptcy last month, Blippar's assets are up for sale, and bidding ended today.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Although the HoloLens is still primarily the domain of developers and researchers, the device is nevertheless on the cutting edge of showing us what will be possible with augmented reality in the coming years. The latest example comes via Microsoft Japan and a new concept video that shows off how the HoloLens will be used in the relatively near future to pilot autonomous ships.

We already know that the connection between virtual and augmented reality is pretty tight, with tools like Unity making porting some apps between the two platforms fairly frictionless. But there are some things currently going in VR that just don't need to come to the world of AR.

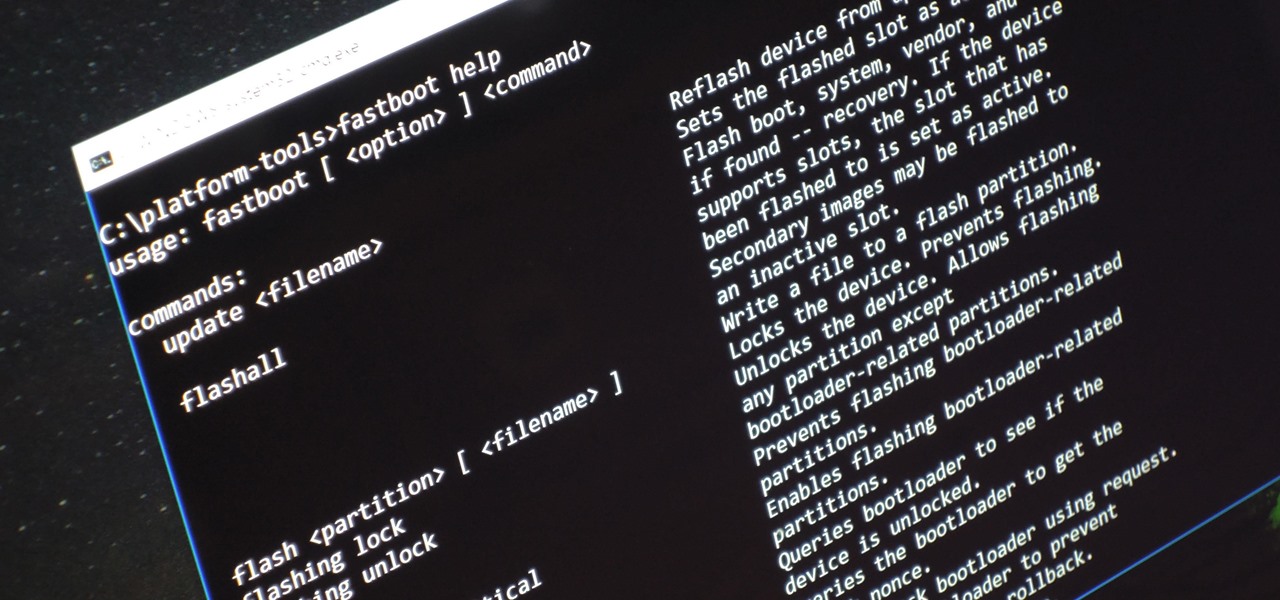
Unless you're experienced using the Linux terminal, running ADB and Fastboot commands can get confusing very fast. The problems often stem from having to hunt for various files — usually IMG or ZIP files that you need to mod your Android phone — and then move them to your platform-tools folder, which, depending on how you installed ADB in the first place, could be anywhere.

Last week, the internet was ablaze with talk about the Galaxy S8's home button, because it subtly changes positions without the phone alerting you. This feature was included to stop burn-in issues with the screen, and the general consensus from tech sites was the screens would not experience any burn-in at all.

Those of us with modern smartphones know that 4G LTE networks have provided us with a phenomenal experience. One light years beyond what we had access to before. For some time, AT&T has been teasing its dive into the next iteration of network speeds, agonizingly doing so without any specific dates for when they would actually deliver. But today, AT&T confirmed what they call the "5G Evolution," and it's available now.

Over the past eight months, ten infants at UC Irvine Medical Center tested positive for the same strand of methicillin-resistant Staphylococcus aureus (MRSA). Despite the danger of this superbug due to its high resistance to most antibiotics, this information was only released to the public on Thursday. Thankfully, all ten babies survived and are currently healthy.

A new app called Roadie now makes life a little easier by connecting users to people who can transport their stuff. The app allows users to transport anything from dogs to getting rid of your ex's things. Furthermore, anyone can register as a sender, or become a driver to make an extra buck. The app is very easy to use: simply download (the app is available on both iOS and Android) and register using an email address or with Facebook. Using the profile you've created, users then select whethe...
This is for those using Kali Linux 2.0 that need to edit the CRDA values to get the increase in Txpower

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Based on OTW's encouragement in his post on "How to Find the Exact Location of Any IP Address", I decided to make a gui(graphical user interface) which would hopefully make the process easier. However, because turning a python script into a standalone executable is a right pain in the nether-regions, particularly for linux, I haven't yet completed this step(I will soon and update this). I did however, make an apk for android(you use a .apk file to install an app on your android device), which...

Amid rumors of a 6-inch phablet Nexus and the impending release of Android "L", Google posted—then quickly removed—a trio of ads for their industry-leading mobile OS.

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.

With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Social media is where we post our thoughts for the world to see, but sometimes a little more exclusivity is needed. And that's where Scrambls comes in.
The Internet has had a huge influence on many areas of our lives, but, in particular, has resulted in nothing short of a revolution in the way we work. The web has offered the sort of flexibility to the individual that few people would have dreamed of just a couple of decades ago. And where once a global marketplace was available only to a handful of multinational corporations, today thanks to the Internet, we can all access it.

Seventeen years ago, Apple released iPhone, the first mainstream consumer phone with a touchscreen as its main typing input method. Apple has been perfecting its onscreen keyboard for almost two decades, and it's built with some fantastic features that make typing faster and easier. But it's easy to overlook some of these features, so here are some tips and tricks you need to be using if you aren't already.

We're living in the age of Big Data. As the primary force behind everything from targeted marketing campaigns and online search algorithms to self-driving cars and even space exploration, massive sets of complex data stand at the heart of today's most exciting and important innovations.

Now that more and more people are working on their personal computers and smartphones as opposed to their work computers as a result of the coronavirus outbreak, hackers are having a field day. Unencrypted home networks and public WiFi connections make it incredibly easy for cybercriminals and even government agencies to access everything from your browsing history to your banking information, and a Virtual Private Network (VPN) is the only way to stop them.

For a decade, Microsoft Azure has been transforming businesses across the globe. The cloud-computing service is leading the way in software as a service (SaaS), platform as a service (Paas), and infrastructure as a service (IaaS) protocols.

Smartglasses startup Nreal enjoyed some highs and endured some lows this week, as the company landed a product placement with Kevin Bacon but then faced production issues related to the coronavirus outbreak.

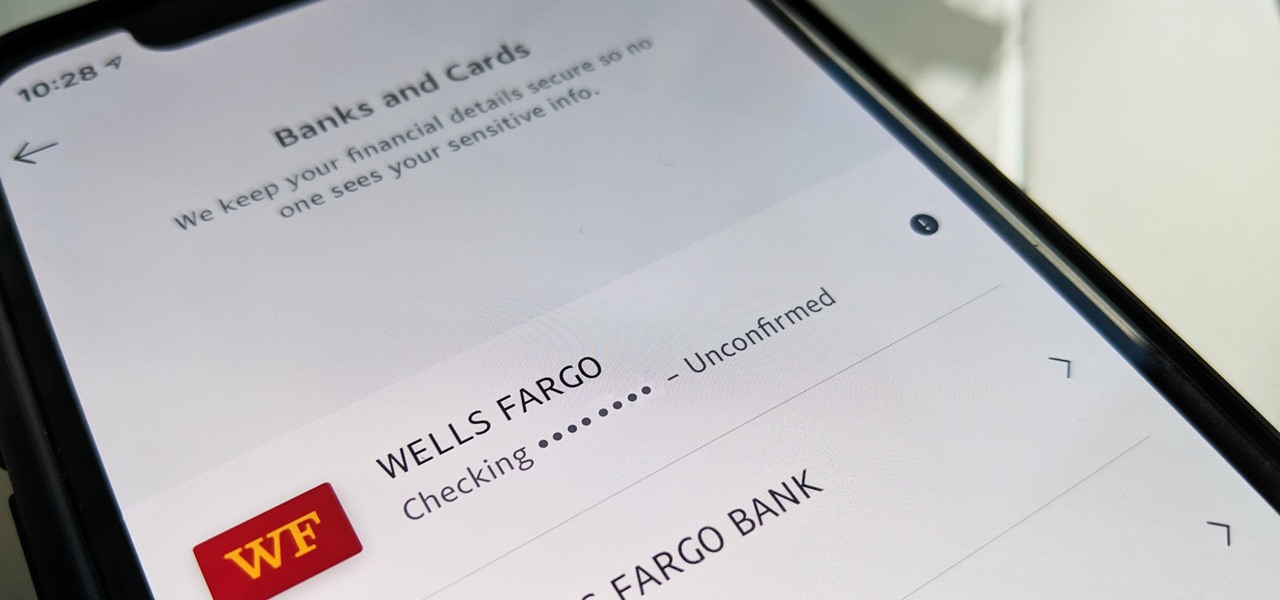
PayPal is one of the most popular payment systems across the globe. It makes payments fast, easy, and secure, and with 250+ million users, it's not going anywhere. If you're new to the online service, one of the first things you should learn is how to add your bank account, credit card, or debit card to PayPal, and make your life easier when it comes to online payments and withdrawals.

While its competitors are concentrating on building out AR cloud platforms to give advanced AR capabilities to mobile apps, Ubiquity6 is taking a step in a different direction.

For all its faults, you can't say that Facebook hasn't been instrumental in connecting friends and family together, no matter where in the world everyone is. That's why one of its upcoming features — watching videos together with Facebook friends directly in Messenger — is so novel. It's just another example of the internet bridging gaps that couldn't be bridged just a short while ago.

Giphy has had a few apps for iOS over the years. Giphy Keys was a keyboard built specifically for GIFs. Giphy Cam lets you create your GIFs complete with stickers. Giphy World is for adding augmented reality stickers to the real world. But now, Giphy has combined elements of all of these into its main app, so you can create, find, and share GIFs and stickers right from your keyboard.

The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

Most of us have probably used a GIF at least once or twice to respond to a message, and that's why a lot of messaging services and keyboards have GIF search tools readily available to use. Now, Google wants to take GIF responses to a more personal level, by allowing you to create your own selfies GIFs to instantly sent to family and friends.

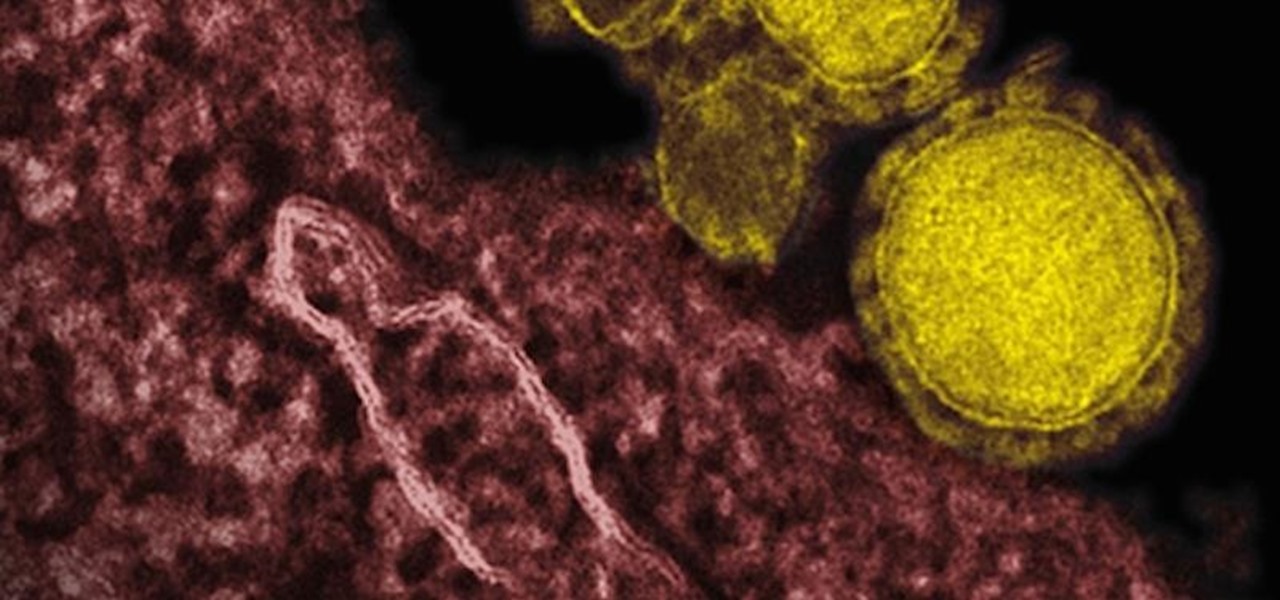
Coronaviruses are common viruses, and most of us catch one at some point — they cause about 30% of all common colds. A new accidental discovery could help fight these viruses, even the deadlier, emerging ones.

The bacteria Klebsiella pneumoniae is a bad actor known for being antibiotic-resistant and causing a variety of serious infections in hospitals, including pneumonia, surgical site wounds, and meningitis. K. pneumoniae is something you do not want to encounter if you have a compromised immune system.

Fighting fire with fire, scientists are harnessing the adaptability of helpful microbes to challenge the adaptability of deadly microbes. What are we talking about? Hunting with phages — viruses that attack and kill bacteria.